The Rise and Fall of a Mideastern Pasargad
Welcome to Memetic Warfare.
This week, we won’t be focusing on the elections, as I’m kind of over them myself. More importantly, if you’re reading this, you’ve probably read multiple other election-related articles in our niche field, so I’ll save you the time.
Instead, we’ll focus on other, in my opinion more interesting, developments. The first item starts below.
The first has been a long time coming. The FBI, DOT (interestingly enough) and the INCD (Israel National Cyber Directorate) have finally published a report on the hacktivist groups that Memetic Warfare has been screeching about online for months (AnzuTeam, CyberCourt, Zeusistalking/RGUD). The report attributes the operations to Emmenet Pasargard, an IRGC-affiliated front company known for its aggressive and relentless cyber-enabled IO.
I was hoping to be the first to tie all of the above (and more) together at CYBERWARCON, but I’m just happy to share the spotlight here with organizations much more prominent and capable than myself. My talk will provide a different angle and new information though, so it isn’t all a wash! After CYBERWARCON I’ll upload a link to the talk.
Back to the report. Similarly to how the last Open AI report provided unique insight into how Cyb3rAv3ngers works, this report elucidates how Emmenet Pasargard (now operating under the name "Aria Sepehr Ayandehsazan", henceforth ASA) operates at every level - from infra, to reconaissance/OSINT and more.
The first really interesting part of the report is how ASA acquires hosting infrastructure.
Apparently (and I assume here) it was too much of a pain bypassing KYC for Western VPS providers only to then have domains be reported and taken down anyway, so ASA pulled an admittedly Chad move and set up their own resellers to rent their own server space from European providers. This has the dual upsides of not only masking the Iranian origin of their activity, it also makes it harder for domains to be taken down.
One of the server providers, Stark Industries, as has been exposed in the past and written here, is allegedly an unscrupulous provider willing to provide infra for Doppelganger, so no surprise that they’d not check too closely here. ASA seems to be generous as well and is willing to provide hosting support to Iranian AoR allies.
ASA has been busy and seems to love integrating SMSes in their operations. One example below attempted to contact family members of Israeli hostage in clunky Hebrew and an equally clunky translation to English encouraging hostage families to click the link for more information on the hostages.
The use of the link and form on the domain is interesting and also a recurring TTP that we see from ASA in other domains.
From there, the report covers the Cybercourt operation. Memetic Warfare readers were aware of Cybercourt and its motley crew of obvious false flag hacktivist groups months ago, and there isn’t much more here. I’m much more curious to hear more about “Sample”, as I haven’t come across it yet.
The Cybercourt domain was seized a few days ago, and when I came across that I knew something was up and to expect some sort of reporting soon, so nice to see the turnaround be so fast.
There’s also a shoutout for the RGUD operation as well as more information of the compromise of displays during the Olympics:
ASA operators also apparently tried to use Shodan to glean information from Israeli internet-connected cameras:
The real meme moment was the exposure of how ASA carries out reconnaissance. Using knowem and socialcatfish shows a level of expertise roughly on par with say the average senior citizen. Facecheck is fine, I guess, but Pimeyes is known to be better. I’m also surprised that they used data leak aggregators like ghostproject and don’t just collect and aggregate breached data themselves.
The requisite generative AI section is also worth touching on. Remini doesn’t surprise me as everyone uses it, but I’ve never actually bothered to look into voice modulation tools so those are nice firsts.
So, seems that ASA really operates with a shoestring budget and outsourced capabilities. The main takeaway, as per usual with Iran, is that a persistent and not overly technical adversary can still be impactful be with a bit of gumption and risk appetite.
That’s it for this report - I’ll upload a link to the talk on this with more information at Cyberwarcon when it comes out.
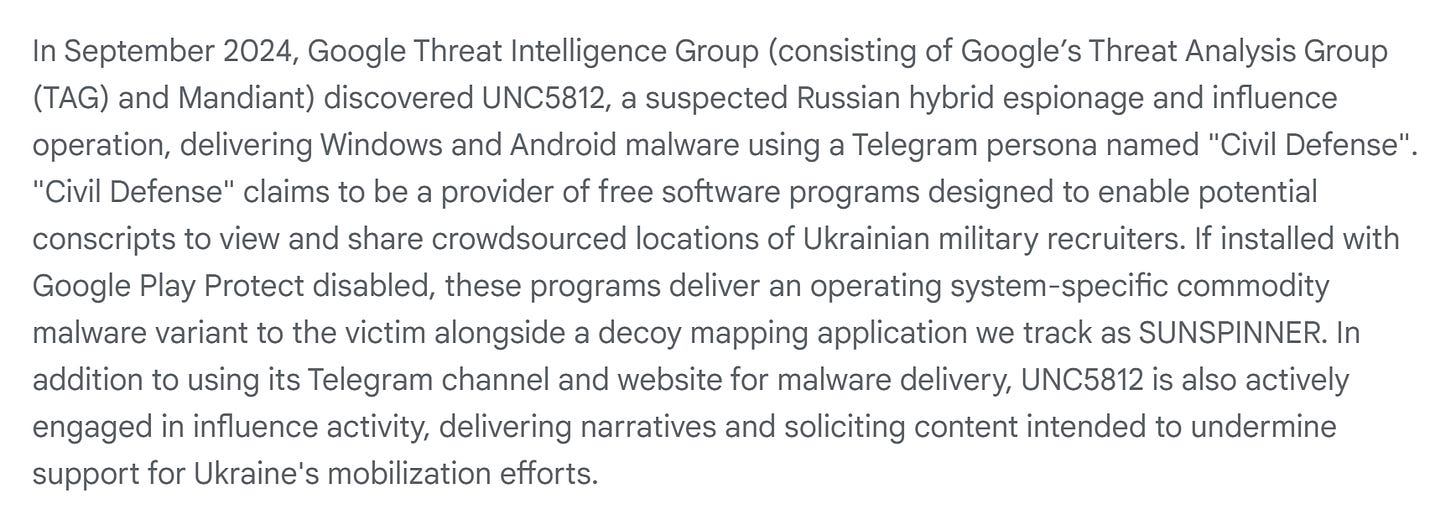
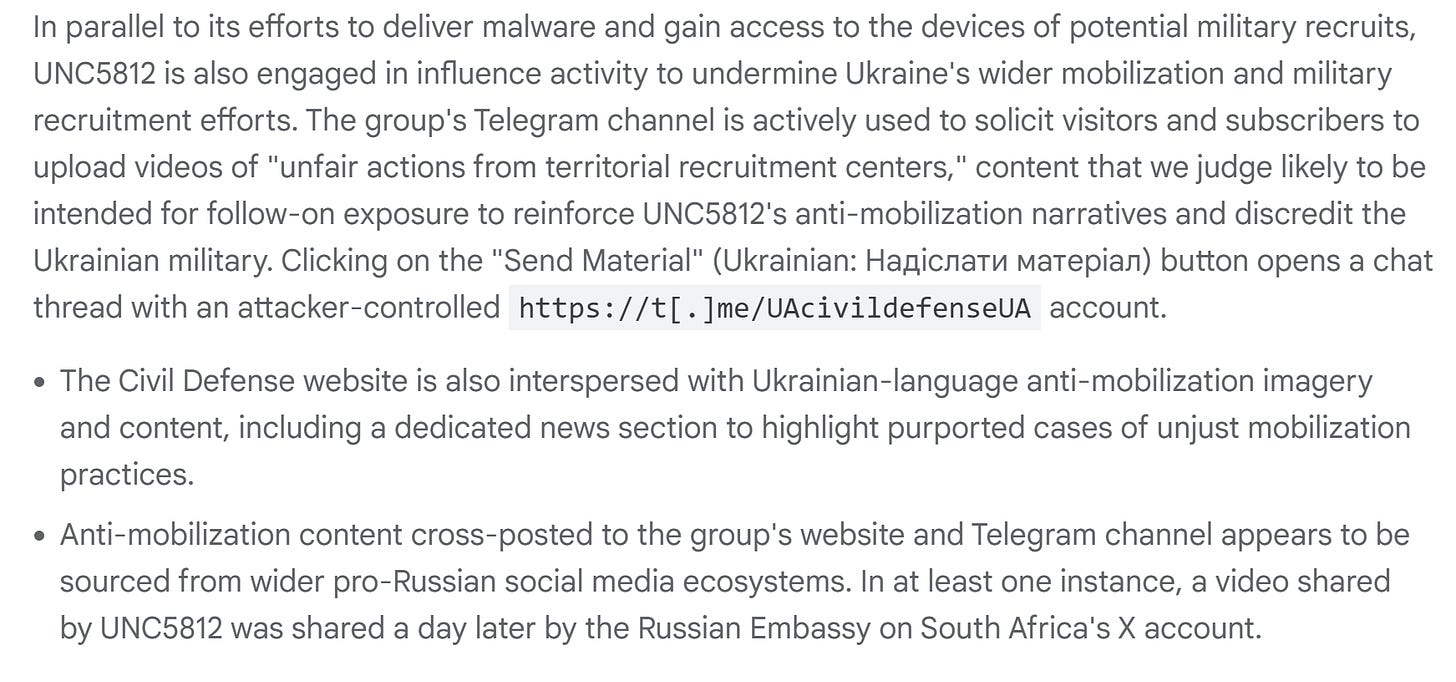
There’re other reports of note as well. Google came out with an interesting Russian operation targeting the Ukrainian military, available here. Check out the summary below:
So we have an interesting hybrid espionage/influence operation operating under the moniker of “Civil Defense”.
The Civil Defense Telegram channel is also fascinating. The group uses paid sponsorships (so Google suspects) to promote their channel on other, legitimate Telegram channels:
Bypassing Play security is also worth calling out. More and more threat actors are calling on people to sideload their apps to bypass protections on app stores, so this is a good use case of that:
IO is also big here. The actor actively solicits content and videos from subscribers of “unfair actions from territorial recruitment centers” to then amplify online to encourage Ukrainians to not join the Ukrainian military. Amplification by the broader Russian ecosystem should go without saying as well:
Overall a great report with a ton of pivotable content in the IoCs (and before you ask, yes, I’ve added the Civil Defense channel to Telemetryapp.io).
We can absolutely expect to see more hybrid activity going forward and this is the kind of stuff that keeps me interested in the IO space - it certainly isn’t Twitter botnets.
I don’t usually cover content from mainstream media as I prefer to bring attention to industry reporting or things that fly under the radar, but I’ll make an exception for Zach Dorfman’s latest article in Wired, available here.
The headline summarizes it well:
To make it even simpler: Trump decided to overthrow Maduro, and utilized an apparently not overly enthusiastic CIA and other USG arms to try to do it. Once Trump decided to do it, a “Venezuela Task Force” was assembled. Personally, were I to write this article, VTF would feature much more prominently in the title. Hopefully they had some commemorative shirts made. The first order of business was expanding hacking efforts.
The first operation of note was a disruptive strike (either a remote-access cyber operation or potentially the result of on-the-ground sabotage) against the state payroll system:
The CIA also ran a covert influence operation to spread “pro-democracy content” online and sponsor civic groups.
Here’s where it gets more interesting. An unnamed administration official decried these efforts as “embarrassing bullshit” not discernable from overt influence efforts meant to promote democratic values.
The next section drives the point home: value-based pro-democracy IO is useless when the average person is actively starving and unemployed. One would think that the sheer number of social science grads in the USG would make USG efforts more understanding of Maslow’s hierarchy.
Interestingly, some officials spoken to by Wired stated that they used the emphasis on democracy as an excuse to not have to actually do anything.
There’s a lot more in the article, and you should read it, but the point I want to linger on is the IO targeting.
The article describes cyber and IO efforts that are in effect siloed.
More effective IO would firstly have amplified that cyber operation to foment internal dissent in the military and government. In these sorts of cases, targeting the military/government and other “legitimate” targets should be the first and most-targeted. Multiple other operations could have been carried out - for example, encouraging military personnel to actively defect, targeted hack and leaks against senior officials to weaken trust in the ranks, and many more.
Other broader, ideally overt operations could have worked to showcase the impotence of Maduro’s government, mismanagement of resources and the economy (and any famine), health issues, violent repression of civilians and more - anything that would the average citizen living in Venezuela would actually care about while not specifically targeting otherwise uninvolved individuals.
Pro-democracy/value-based IO shouldn’t be covert, not due necessarily to any inherent moral issues but rather because it simply wouldn’t be effective.
I normally don’t take statements from political figures at face value, but to paraphrase John Bolton, it seems that the USG, and perhaps CIA in particular, is still scared of its own shadow when it comes to certain types of covert operations. For better or for worse, those times are past, and it’s time to be unburdened by what has been.




















10/10 title! Amazing album.