Host of Operations Past
It's only a TLS certificate if it's from the Grand Est region of France, otherwise it's just an SSL certificate
Welcome to Memetic Warfare.
This week, we’ll:
Investigate the now-exposed Iranian cyber enabled influence operation targeting Sweden
Discuss the DOJ indictment of Iranian cyber operators who hacked the Trump campaign
Review the CISA/FBI bulletin on generative AI and IO
Share a few additional points
Let’s get started.
The Swedish government has accused Iran of being behind an SMS campaign in 2023 meant to stoke civil unrest following the burning of several Qurans in Sweden. The campaign was carried out by, what else, a hacktivist front. The front adopted the moniker of “Anzu team”, potentially using the Sumerian god “Anzu” as inspiration, which makes sense considering the religious tones used by the group.
This operation was pivotal as it came at an especially sensitive time as Sweden was trying to join NATO. Promoting civil unrest and amplifying insults to Islam was probably meant to deter Turkey from approving Sweden’s request to join NATO, as well as of course just making Sweden look bad.
Sweden’s domestic security agency has claimed that IRGC cyber operators successfully compromised a Swedish company that provides “SMS Service” - be it Telecom or SMS marketing, I don’t know.
Iran was a top contender for the operation back when it was first exposed, and all things considered, the timeframe for the case isn’t all that slow.
Unsurprisingly as well the network has had its assets taken down, but we can take a look. Twitter user Swithak has already done the hard work for us:
So, as per usual and foreshadowing future operations in Israel, we see a Telegram channel, two domains (perhaps as backups), and one Onion domain. This is an MO that we’ve seen multiple times up until now with Zeusistalking and other Iranian operations.
Luckily, Telemetryapp.io has the Anzu channel archived, so check it out yourself as well without having to access the channel in app.
The channel’s first post in Swedish and English called for users to send them photos of anyone attacking the “demons” (those burning the Quran in Sweden) to share on the site and receive a “special reward”.
They have one closed group which one can find a link to in Telemetry thanks to it having been archived. Checking that group out also provides us with more context, in this case putting out “Wanted” signs offering a significant financial reward for these alleged “criminals”.
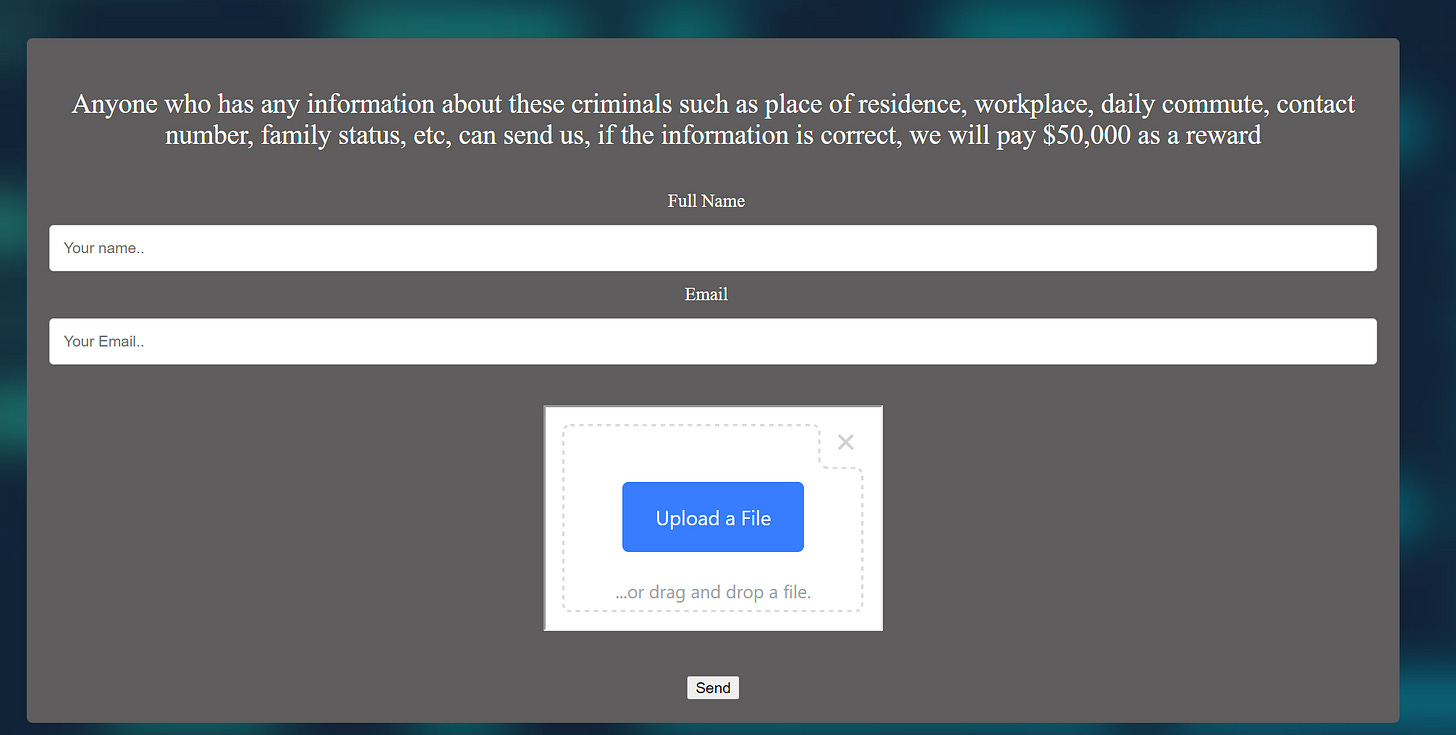
The domain itself (archived) has an upload box for files on these “criminals”:
The domain itself pulls no punches:
The infrastructure for the domain is interesting as well. The main .com domain was hosted on 3 hosts in the past:
One of these was Stark industries, now infamous for ties to Russia and Doppelganger. We also see additional domains that previously were unknown on different TLDs:
One of the past hosts also hosted an odd subdomain, including quite recently. Let’s take a look at it.
The firefighter subdomain has only ever been hosted on that host, but it has additional subdomains on different hosts.
The Havij subdomain is especially noteworthy, as it helps in attribution, not that we needed it. Havij is an Iranian hacking tool tool as exposed by Checkpoint, and it’s possible that the subdomain here is related to some instance or use of the Havij tool, or it could be unrelated. We can’t tell conclusively as the page isn’t accessible or archived from a quick check.
It appears as well that the test7ttt domain was hosted on the server after the Anzu operation, so presumably it was used for additional operations following this one - interesting that they didn’t burn the infrastructure and move on.
I’m not satisfied with the information we have on the root domain though, so let’s check it out in Censys:
Here we have one host. Note that it has SSH running - we can reverse search the public key hash here, although unfortunately there are no other hosts using the same key. Checking out the forward DNS shows that the host resolves currently to cr7cr6[.]test7ttt[.]shop, which is also unavailable.
The host’s SSL certificate is also that of a different domain. Checking it out quickly didn’t bring up much, but that’s another direction to look into and definitely something to monitor.
So here we have some tantalizing opportunities for future pivoting and potential ties to other Iranian cyber operations.
Back to the operation’s core activity. The channel quickly moves to the SMS campaign as well, not only showing the future SMS messages that the operation would later send, but again asking for photos of “demons”.
Swithak shares some examples of the actual SMSes, in this case quoting Hassan Nasrallah of Hizballah apparently:
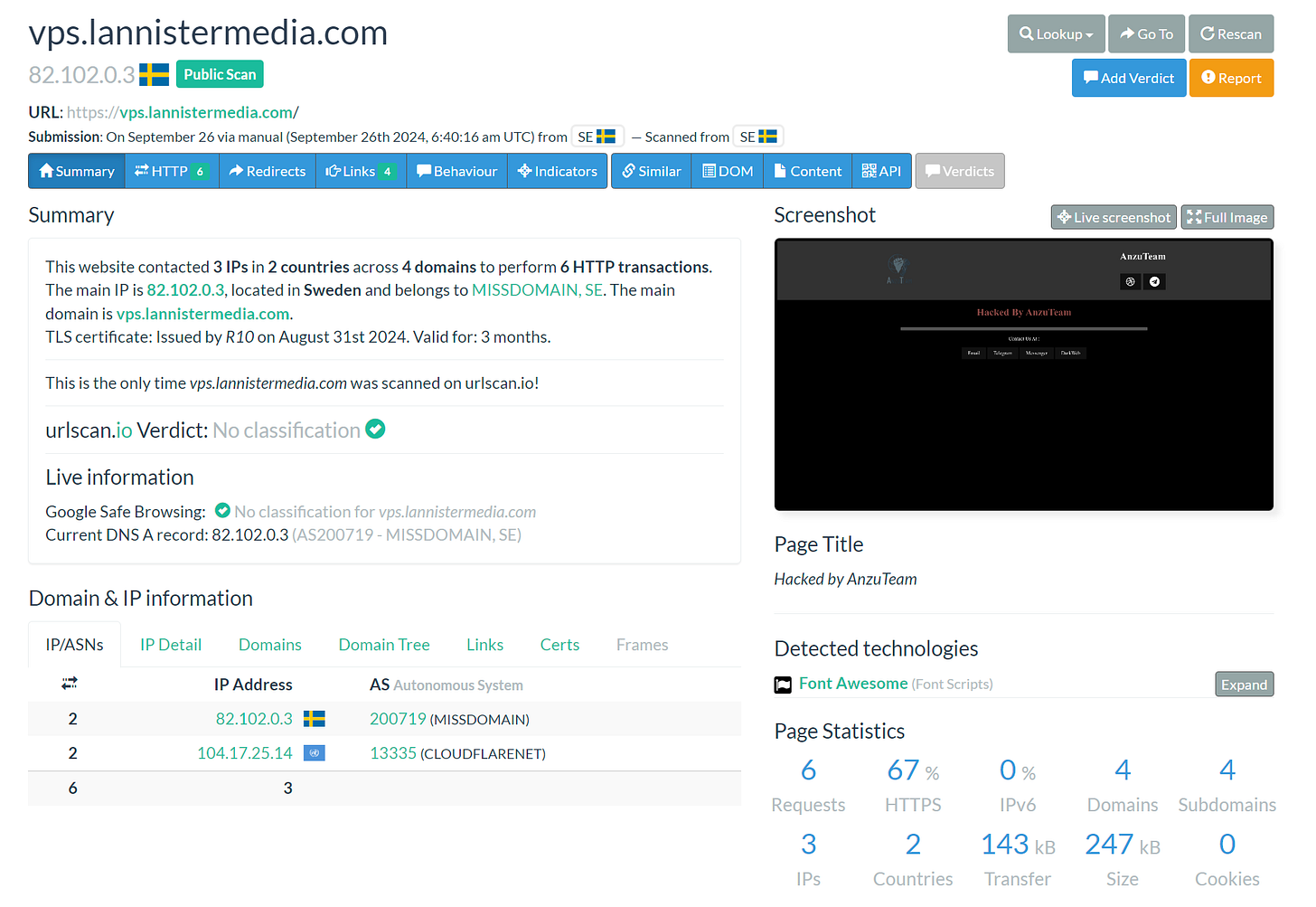
There’s more to their activity though. Looking up Anzuteam(.)com on URLScan.io brings up two domains that refer to it:
Anzuteam has popped and defaced these domains, presumably recently as they’re still up:
This is visible on Google as well:
We have a solid view of this operation, but let’s do one final sweep on its URLScan results to see if we can find other indicators of ties to Iran. The image files are pretty blandly named so they won’t be of much use.
Let’s check out the other Javascript files - Main.js looks interesting.
This response is pretty short, and shows how they integrated their Telegram bot into the domain. Here we can see that the Telegram bot token itself is exposed, alongside the Chat ID, which is a bit less interesting in of itself. However, exposing the token means that anyone could use that token in the Telegram API to mess with the bot itself, which is exactly what a Reddit user did:
Let’s now go back to the URLScan results. Nothing else there stood out to me, so I went to check historical scans, which is often useful for finding previously available data. This approach didn’t fail here, as there was a file in its previous scan that wasn’t available.
This file, titled 1rG0B4, is a .PNG file linking to IPlogger.com to track users that access the domain. This is something we’ve seen Iranian operations use multiple times in the past, see here for one example and the screenshot below from the post:
Quite the operation on the whole. What can we learn from this? Well, a few things. Certain things seemingly remain constant - Iranian operators love hacktivist fronts, doxxing and Onion domains, and the potential overlap with known hacking tools is a rare bonus. SMS operations are not covered enough in IO, despite them happening - look here for a Memetic Warfare look at a Russian operation.
The ROI here is quite high. This operation made the news, and while cyber intrusion of a Swedish company could be expensive, a similar effect could have been had by the IO operators used commercial services.
SMS marketing platforms exist, be they white or black hat, and that could have saved them some time and money, making the ROI reasonably high.
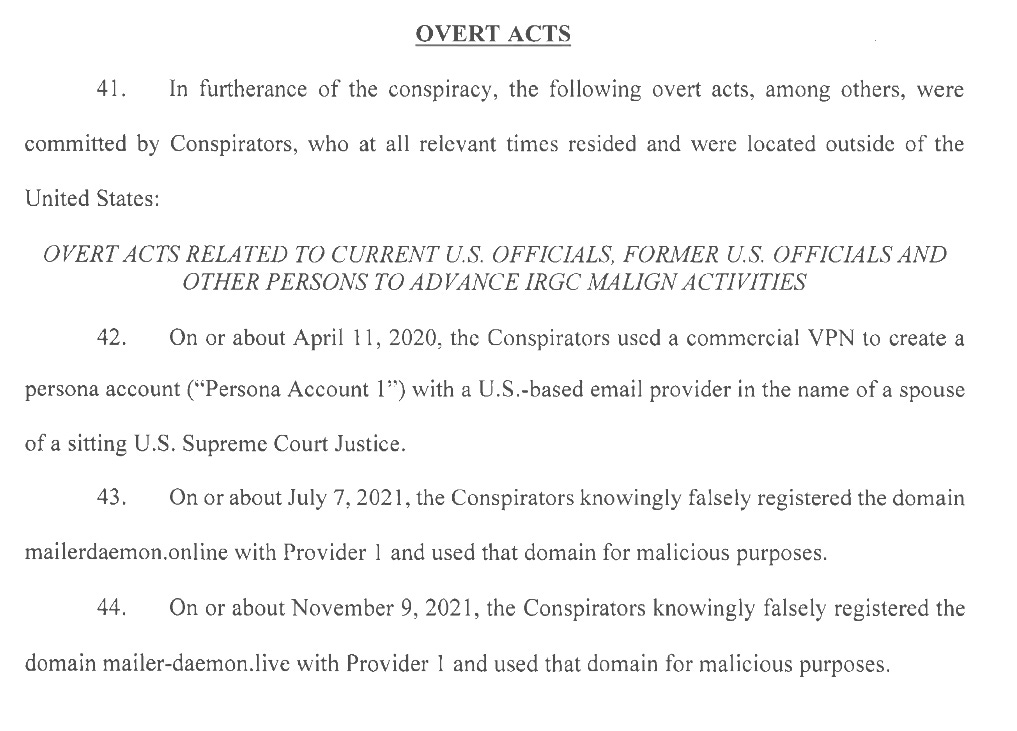
This operation is also sophisticated. While not necessarily highly impressive technically (what IO is nowadays), the operation shows the ability to carry out cyber-enabled IO beyond hack and leaks to operational effect. Overall, pretty impressive and a fun OSINT usecase.
Let’s move on.
The DOJ has unsealed an indictment against 3 Iranians accused of being the operators that carried out a hack and leak operation against the Trump campaign. The indictment is available here.
The indictment confirms what Google and others have already reported, primarily that social engineering and spearphishing were the main attack vectors.
The timeframe is also made specific, with the operation beginning in January 2020 and continuing until September, 2024.
Some specific companies are also called out as being providers for the operators and there are some other interesting specifics, but let’s bring up the domains and IoCs:
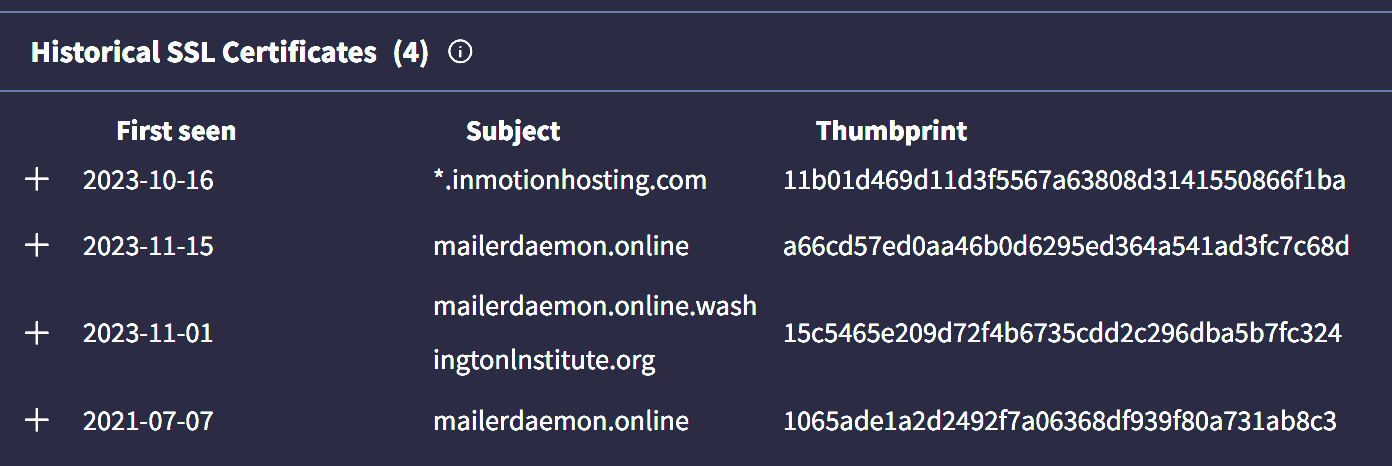
Looking up the mailerdaemon domain exposes which think tank was targeted:
Not much more to this to be honest beyond things we already know or would expect, but good job on part of the DOJ/FBI in getting this out in a timely fashion.
Let’s move on to the ODNI’s latest election security bulletin focusing on foreign use of generative AI and manipulated media.
The bulletin is a page long, so you can read it yourself below. Most noteworthy is the conclusion: AI is useful, but has yet to “revolutionize” influence operations. I agree with the statement also about how the future of AI use in IO will be determined by the ability of nation-states to develop their own models and jailbreak commercial tooling.
We’ll conclude with a potent potable for this week. The Chinese Ministry of State Security (MSS) recently attributed the hacktivist group Anonymous64 to Taiwan, and specifically accused three Taiwanese people of being the key operators.
Oleg Shakirov astutely pointed out that past Chinese attribution of cyber activity has been the domain of private firms and the CVERC (which I’ve written about here).
The CVERC’s domain has been down since their last report on Volt Typhoon (deep dive on this incoming sometime also!) and it may seem that the Chinese government has reached its final form of evolution and will use the MSS to attribute, accurately or not, adversarial cyber activity. This may be a sign of increasing Chinese government maturity, or alternatively a desire to fight fire with fire, so to speak, to combat US government attribution of Chinese activity.
That’s it for this week. Thanks for reading, check out telemetryapp.io and please direct all complaints or concerns to the comments section.