BrAPT Summer
Welcome to Memetic Warfare.
I’m Ari, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
I was going to have this week be a longer post, but unfortunately the topic I wanted to write about still has a gag order on it for some reason! Hopefully that’ll be lifted soon and then we can do a whole thing on that. That threw a wrench in my plans for this week, so this week’s post will be a bit shorter than usual.
Prior to beginning, if anyone wants to hear me ramble on, you can check out the latest episode of Authentic8’s podcast, Needlestack, to hear me talk about IO, marketing tools, and my dog:
I’m also going to (hopefully) publish more and more with the FDD, including short and long-form content, so if you’re interested be sure to check out their site. The team I work with published a quick alert re MuddyWater activity in Israel that may be of interest, available here. As always though - everything I say on this blog or in general is my personal opinion alone.
Alongside that, I’m toying around with doing is a review of recent TTPs from Iranian hack-and-leak threat actors. There’ve been a few trends, such as the use of web3 and Onion networks to avoid takedowns, but something that I didn’t touch upon was the use of the same IP logging tool integrated into most of the recent Iranian hack and leak sites targeting Israel.
Integrating a tracking pixel via services like Grabbify isn’t odd in of itself, but we’ve seen it consistently in the past few operations, including the one that I was planning on writing about but can’t until the gag order is lifted.
We can see it pretty clearly in the Zeusistalking/RGUD operation. Note the Pic_SD1.PNG file linking to “unl(.)one” - that’s the Grabbify pixel on the Zeusistalking domain:
We can see the same thing on the other domain of that operation impersonating a French FRE group - note the 2no(.)co URL hosting a tracking pixel:
We see something similar in other domains. As a TTP it’s comparatively interesting, and while not super strong in of itself, we could use it in conjunction with other indicators to group operations.
I’ll keep thinking about when to start writing up that retrospective of Iranian hack and leaks, and hopefully sometime soon we can get that out.
BrAPT Summer
In other incredibly exciting news, everyone’s favorite hacktivist group/false flag/government front/syndicate or whatever you may believe they are is back. That’s right, Intrusion Truth is now back to posting:
This post reviews what else but the i-Soon leaks, and provides some unique takes. You should read it in its entirety, but because this topic has already been covered to death I won’t do a full deep dive. Let’s extract some key findings:
APT 41 Front Chengdu404 has probably purchased software from i-Soon.
The FBI indictment of APT 41 operators has at least some sort of deterring factor on hiring for Chinese cybersecurity contractors, as i-Soon viewed one ex-Chengdu404 applicant as risky.
The leaks are capable of potentially attributing historical activity and even malware development - see below for some interesting historical work:
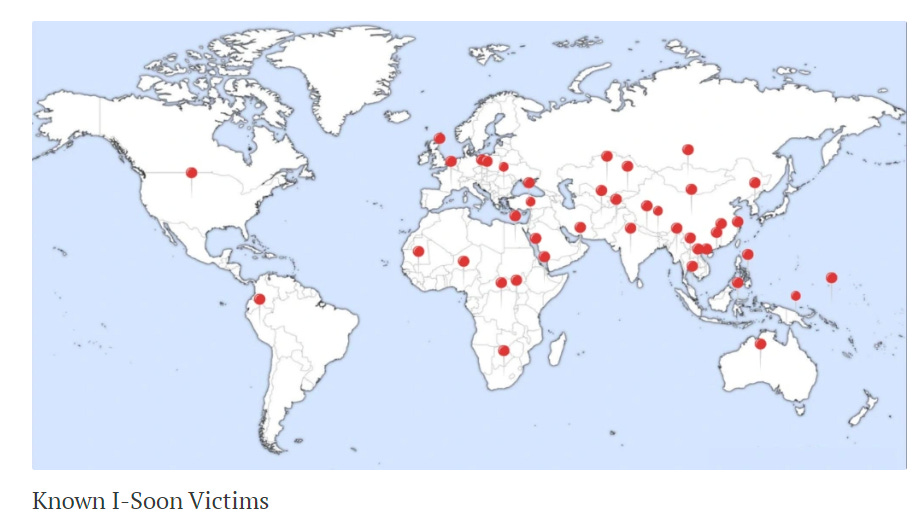
As a Map Guy™ I couldn’t help but share their map of known i-Soon victims:
The post also shouts out Natto Team of Natto Thoughts - check out their blog as well, it’s highly recommended. Most excitingly, this seems to be part one of an upcoming series, so hopefully we’ll see the next sections published soon.
I’ll take points off for the cringe gen AI content but overall, solid stuff if one considers their provenance (many believe Intrusion Truth to be a Western government front, but who knows).
Manila of Heaven
Let’s take a look at the new ASPI report on a new Spamouflage cluster targeting the Philippines.
The network has amplified a disparaging deepfake of Duterte meant to implicate him in drug use.
Most interestingly, the network accounts tweet primarily in English and Tagalog on hot topics such as the recent Reuters expose on American IO activity in PH, the CN-PH maritime dispute and more.
The overall turnaround time from publication of the Reuters report (mid-June) to Tagalog content creation and amplification about a month later here is longer than I’d have expected, so that’s an interesting datapoint for future reference.
One other potent potable - love some metadata from keyboards for attribution:
The same network entities also mentioned Guo Wen Gui, making them by default Spamouflage. I may sound flippant there, but it’s really the case - type in Guo Wengui, Yan Limeng etc into any platform, and you’ll find Spamouflage accounts.
There're some other fun points. Firstly - there’s use of another “unknown freelancer”, one Lin Yuting. Lin’s articles were seeded primarily in legitimate news outlets and only then promoted by Spamouflage - as per ASPI a new TTP, and as far as I’m aware that is still the case, so worth noting!
Those interested in looking at this activity across multiple platforms also should take a look at mentions of Anthony Carty. Just looking around quickly on Reddit and some other platforms I’ve come across some posts that are probably part of this network on Reddit that ASPI seems to have not come across, so that’s always fun and goes to show one of my golden rules: reports are an incredible starting point for further investigation, so take a look at the indicators whenever you get the chance!
We’ll conclude with Harfang Labs’ analysis of recent Doppelganger operations. It’s a solid report but I’ll spare everyone the length as frankly I’m over DG now. We’ll look at two specific sections.
The first is the creative use of LLaMA-3 to analyze 200 articles published by this cluster - see below:
We get the political compass meme which I actually like in this case:
Overall - not a bad usecase for LLMs, if a bit niche, and always fun to see new stuff being used.
That’s it for this week, thanks for reading if you’ve made it this far! Check out Telemetryapp.io and feel free to let me know what you think.