Memetic Warfare Weekly: What's the Frequency, Кеннет Edition
Telemetryapp.io Use Case
Welcome to Memetic Warfare Weekly!
My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
My apologies for the delay in publishing recently, I’ve been quite busy launching Telemetryapp.io, so we hopefully will be returning now to regular programming, at least until I travel for several weeks soon!
I figured that insomuch as this week is all about Telemetry and Telegram, we’d take a look at a Telegram-centric information operation.
What’s the Frequency, Кеннет
A contact of mine recently provided me information about a suspected Russian mass-SMS campaign targeting Ukrainians. I figured that this would be a great case to show some specific OSINT tips - Facebook OCR search, searching Telegram via Telemetryapp.io and so on - even showcasing how we can find evidence of coordinated amplification behind a network.
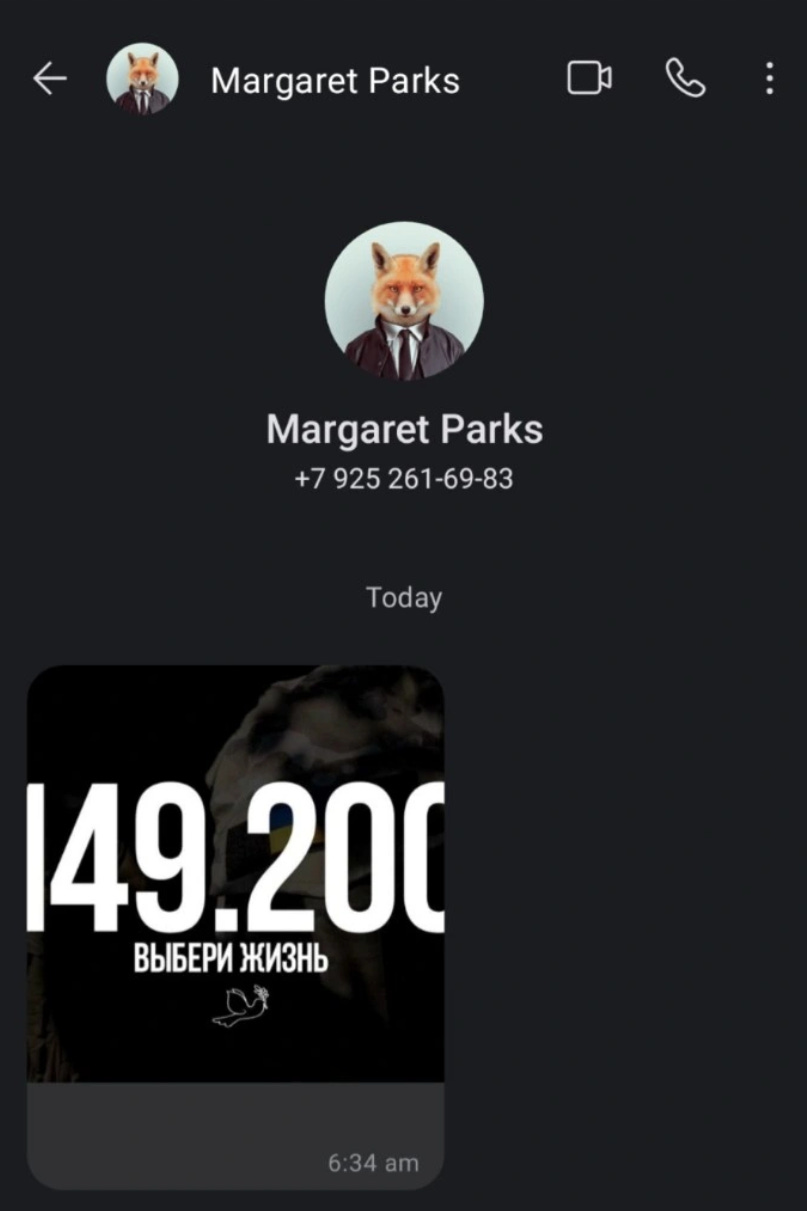
As part of the campaign, many Ukrainians received the below image via messaging apps such as Telegram, WhatsApp and Signal, and social media platforms as well were included, ranging from TikTok to Facebook messenger.
As a tip, one of my favorite uses of Facebook’s search feature is the OCR integration that it has. We can search the below text from the image, and receive public posts of photos that have the same text in the photos themselves:
Doing so has uncovered a number of other accounts sharing examples of messages sent to them. The messages are sent from burner accounts with Russian area codes and, interestingly, fake Western names.
The message refers to a radio frequency, with past Russian posts calling upon Ukrainian soldiers who “wish to stay alive” to radio that frequency and surrender. Past posts and messages referring to this radio frequency from Russian, sources, such as the Perevalsk-Alchevsk Information Center in the Russian-occupied LPR have referred to the same frequency and the Volga river, telling Ukrainians to radio the frequency, surrender by saying “Volga”, and thus make it to Russian lines to “choose life”.
This propaganda video, showing the front and watermarked by Rybar, alleged captured Ukrainian soldiers and so on, is being actively promoted across the Russian internet.
For those curious, I’ll save some text snippets from sent messages:
149.200 "Волга"
Для тех солдат ВСУ, кто хочет жить!
At this point, we can definitely tell that there’s coordinated activity, so let’s try to find the source. Going back as early as possible to find the first seeding of content can often be crucial in uncovering networks and attributing threat actors. Telegram is key to going back as early as possible, as it’s often used to seed content for IO, and is useful for any other kind of investigation.
We can also use Telemetryapp.io to search Telegram. Full disclosure - I am the owner of Telemetry.
Querying “149.200” on Telemetry retrieves hundreds of results from the past few months, with many of them being reshares of the same post.
The earliest mention of the specific narrative in Telemetry (at the time of writing this) is from 25/07/2023:
By using Telemetry, we can identify coordinated activity on Telegram.
Specifically, we see posts on Russian channels calling on members to actively amplify the narrative by:
Searching Ukraine-related keywords on Facebook, Instagram, WhatsApp, Viber and Telegram - see the post for the full list.
Comment on related posts or start new posts by telling “relatives” on the frontlines to radio the frequency 149.200 and say “Volga".”
Thanks to Telemetry’s metadata collection, we can see gauge impact by seeing that one of the posts even has over 300,000 views!
Now that we know for sure that there’s some cross-platform, coordinated activity, it’s time to look more broadly.
We can find other cases of this being shared online as well on dates that correspond with the results on Telegram, and then take those below and pivot upon them going forward to map out the network as completely as possible.
Periodically checking in on the “149.200” query retrieves new attempts by channels to promote the narrative in other languages, including French and German.
From here we have multiple potential directions. We could look more into those accounts promoting the amplification of the narrative, investigate certain entities more deeply and more.
If you’d like to check out Telemetryapp.io, please feel free to do so and let me know what you think!