Chadhaus
Welcome to Memetic Warfare.
I’m Ari, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
Let’s start off this week with a fun and quick investigation into the “Zeusistalking” hack-and-leak network.
Hey, I’m Talking here!
Israeli media broke the news that the Israeli Olympic delegation has had personal data and files breached and posted online by alleged Iranian hackers.
The Israel National Cyber Directorate has attributed the operation to Iran, although at this stage (to my knowledge) without any evidence or reporting. The operation probably is Iranian, but it’d be nice to see some evidence/claims/reporting.
There have been other threats directed towards the Israeli delegation, as well as a flurry of other IO/cyber/physical threats to the Olympics at large that I may discuss in a focused fashion later.
In the meantime, let’s take a look at this operation.
This operation, centered around a domain titled “zeusistalking(.)com”, published alleged hacked and leaked data on various Israeli athletes in the delegation:
The domain was created alongside a Telegram channel (alongside some backup channels), an onion link (TOR page) a Facebook page (now taken down), and a Twitter account. The Telegram channel provides us with some narrative exposition on why Zeus is busy Zeusing:
Nothing unsurprising here other than the use of Zeus as the figure and a surprisingly aesthetically pleasing logo. The Telegram channel also serves as a repository for PII published on individual athletes:
Zeusistalking(.)com, the main domain, was taken down after being up only for a few days. It seems that the network operators themselves took it down as they they set it up again on a .net domain briefly on that domain.
Shortly afterwards, the .net domain was moved to a shared host on Namecheap:
The onion link is still up:
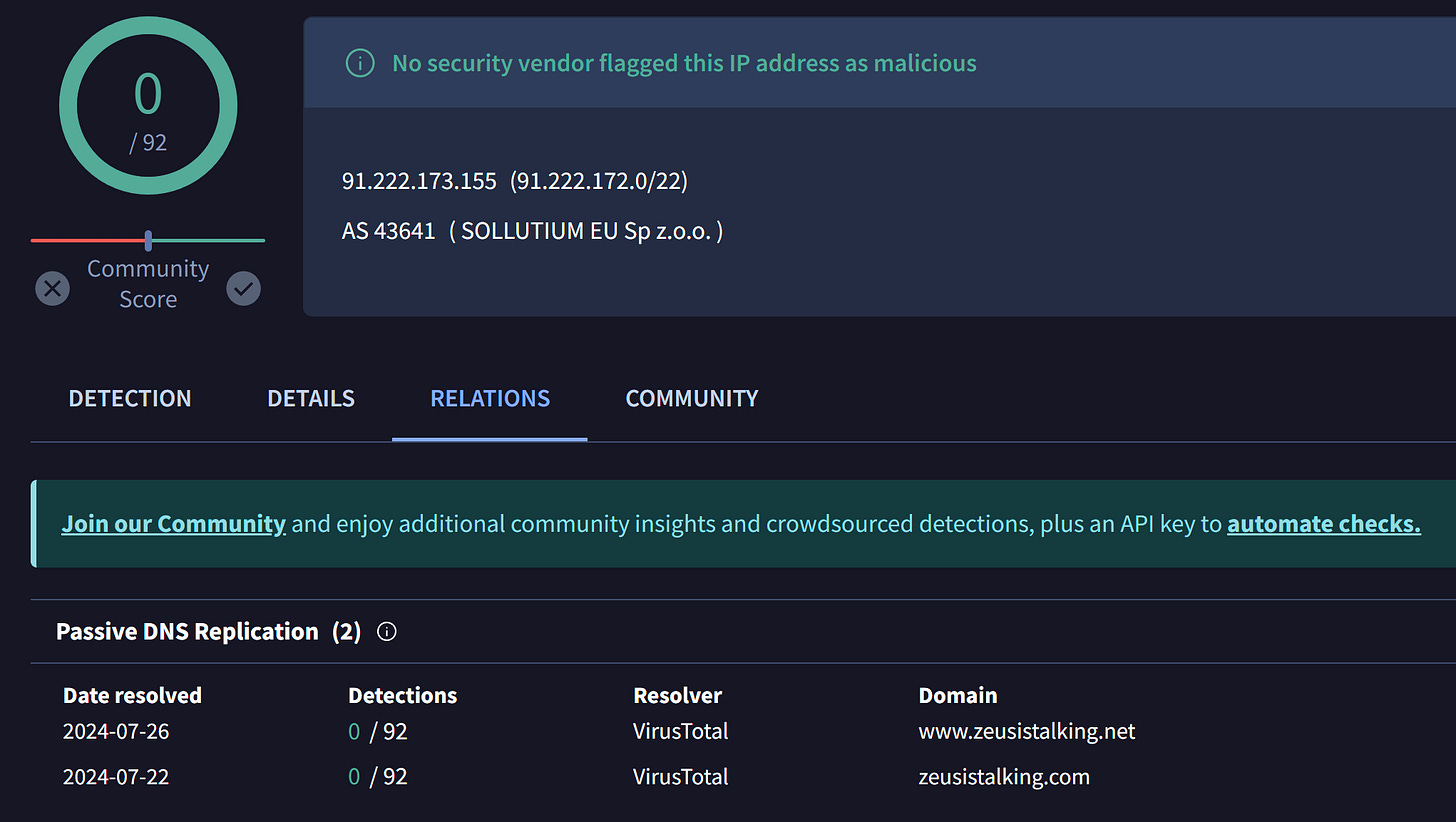
The .net domain appears to be the same as the original domain, so let’s check to see if we can find more hosts via Censys.
Querying both domain names retrieves two separate hosts. One is a typical web server host with ports 80 and 443 open for HTTP and HTTPS, and the second is a Linux host with 80, 2000 and SSH open. This one I would assume is a rented Linux VPS.
So now we can look at both hosts and see what’s up, as Censys doesn’t seem to have caught yet the Namecheap host. The first host is probably the previous web server, the second host is more interesting.
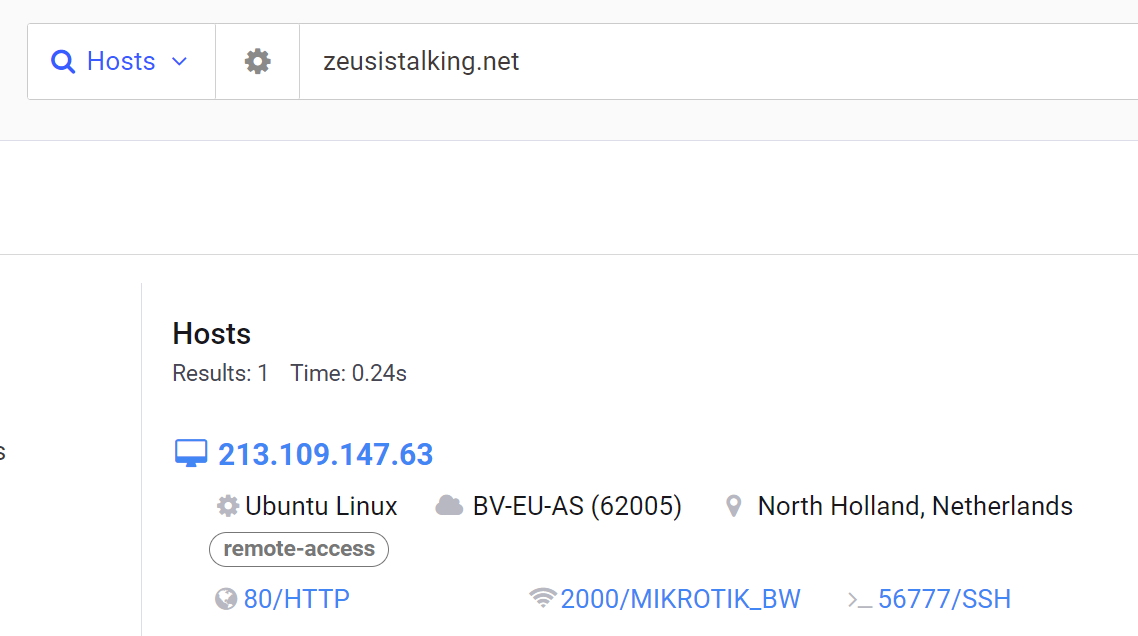
Looking at the second host, we can go to its IP directly and see that it’s the actual host for the Onion domain:
This is critical and searching via Censys is one of the ways that onion domains can be deanonymized.
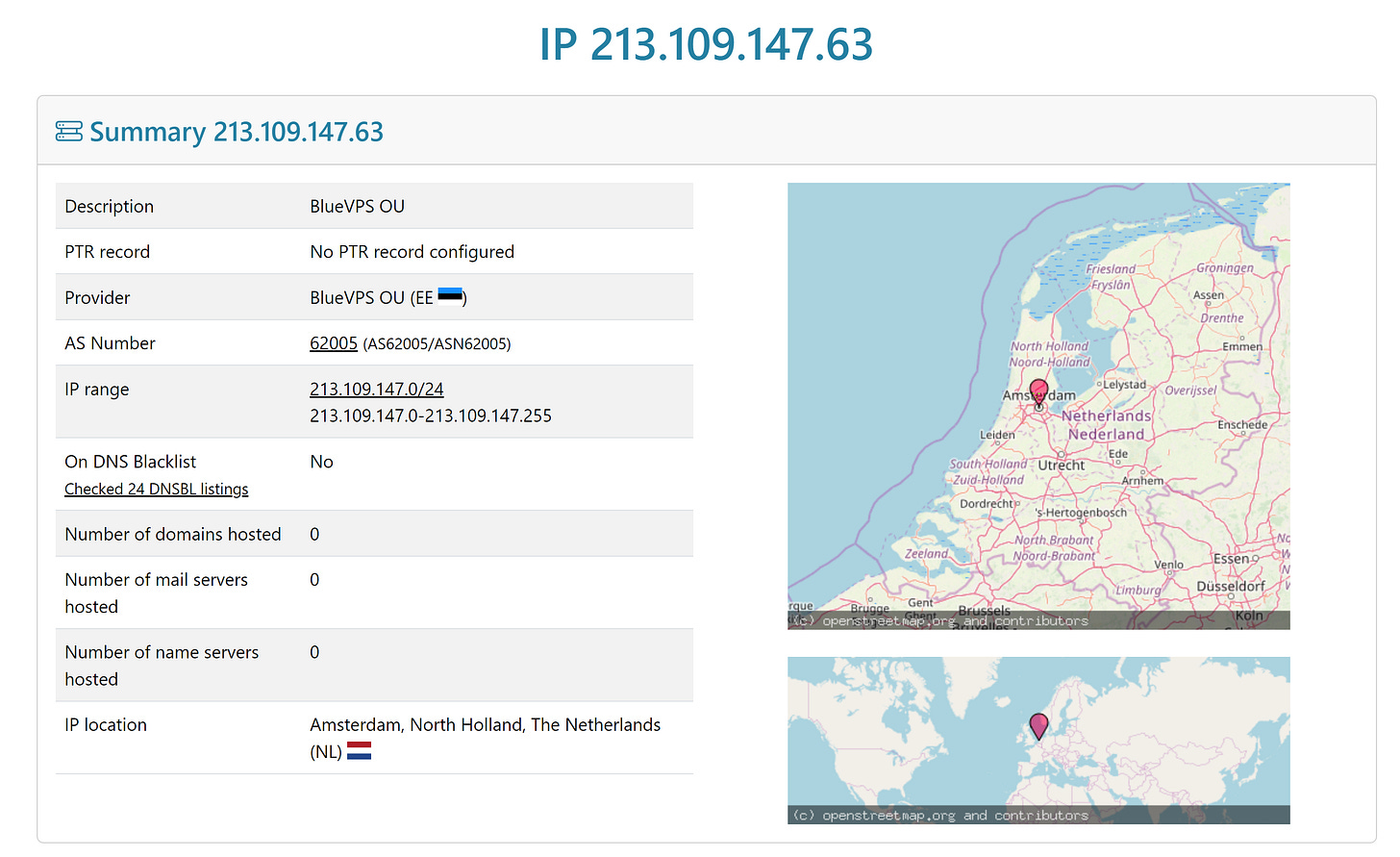
Now that the IP address is known, the hosting provider can be checked out and informed to then take down the host server for the onion domain. Information on those who registered the domain, as well as technical indicators, can be extracted from the host as well.
Validin has it as being part used by Russian and Estonian AS.
DNSLYtics has it listed as being physically in the Netherlands. Chances are it’s a VPS host rented by BlueVPS in Estonia to host the onion domain.
There’s more that we can do in Censys though. The archived HTTP response for the second identified host includes information on entities posted on the site!
You may ask why I even bring this up. When looking at it, the .com domain was down and the .net domain wasn’t yet up, so I needed to find more information. The Censys historical HTTP responses of domains can include that information, as we see here.
We also could have found these by searching variations of “Zeusistalking” on other sites, but it would have taken some more time and this is cooler.
We could also get to these by checking out the “shorturl” link in Zeusistalking pictures, which takes us to a TOR2Web page with links which is still up:
Let’s now look at other entities.
We can also check out the Twitter account, and even the new Telegram channel as well as apparently some other backups. Let’s take a look at those. The Twitter account is now taken down, but I was able to grab one screenshot of it before:
Nothing super interesting, just posting the same content we saw on the domain and on Telegram. The Telegram channel(s) also include multiple links to backup channels and have apparently already had some taken down. Telegram it seems is stepping up.
Let’s see who’s sharing this network and its content. Looking at those who share the domain on Facebook (the Zeusistalking page since having been taken down) shows that one of the first shares was from Nexo Latino - affiliated with HispanTV - an Iranian state media targeting Latin America.
Not only did Nexo Latino get on the bandwagon fast, but the same narrative promoted by the Zeusistalking network was broadcast by Iranian state media on July 23rd, and similar narratives have been promoted by other Iran/Hezbollah affiliated outlets since.
The specific, key talking points being highly similar (all Israeli athletes were in the military, they’re anti-Palestinian fascists and responsible for the ongoing genocide as well and so on):
Rapid or even immediate amplification of a hack and leak by state/grey media outlets is a common TTP, and one used especially frequently by Iran as shown in past, highly-similar cases, including in recent cases as well as covered in this blog. There are some limitations here - Facebook may have taken down even earlier posts that I can’t access now.
Additionally, most of the network entities have since been taken down beyond the clear and onion domains, which are still active. The Facebook page has been taken down, the hashtag #zeusistalking is blocked and posts with the link(s) to the network entities are down as well.
I imagine that the INCD is on this with Meta, but they seem to have missed some, as there’re still plenty of posts that Facebook that can be identified. These can be identified by either searching the new .net domain, or alternatively searching the original .com domain or the shortened URL, as Facebook post/photo search supports OCR - meaning that any text in an image is indexed and searchable as well. Something to consider for next time.
One other thing to note is the use of a web3 hosting service alongside the onion link (presumably IPFS, but I can’t tell for sure as it’s since inactive).
Using a web3 hosting service was also done by the “Cyber Court” network that I wrote about here. There are reasons to do this - it’s a decentralized hosting service that is much harder to take down.
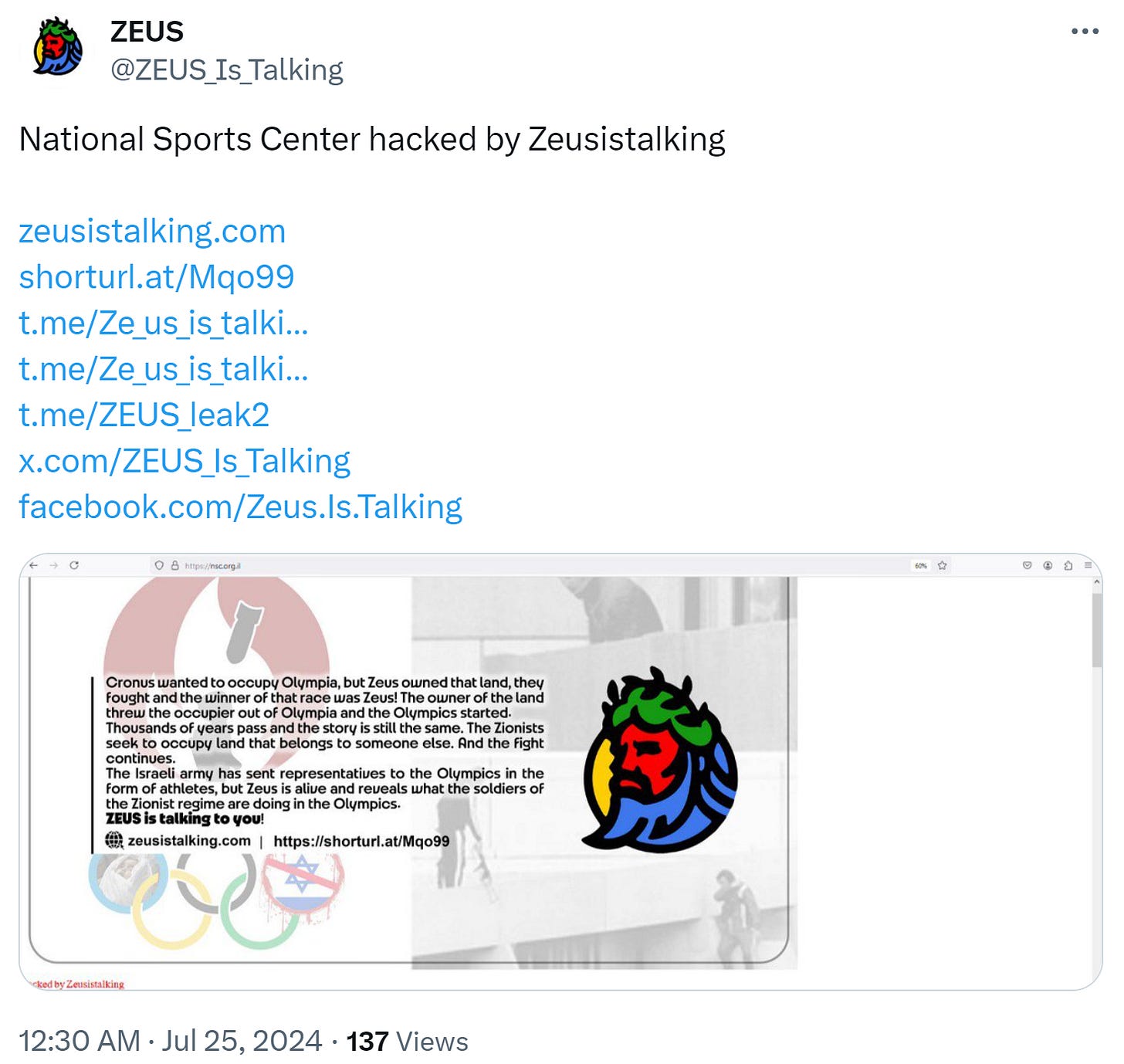
Let’s look at the leaked content. Zeusistalking has claimed to have hacked the National Sports Center of Israel:
This is congruent with the leaked data posted to the Zeusistaking domain. Most of the leaked content are travel documents presumably taken from the National Sports Council:
Beyond the leaked data, some other information on the delegation is available with a heavy emphasis on military service. This information is publicly and easily accessible and doesn’t necessarily indicate that the individual athletes were compromised:
Overall, definitely seems like an Iranian operation based on the INCD attribution (using indicators from the intrusion to the National Sports Council) and the victimology/TTP alignment and more.
The big takeaway here is that when doing a takedown - one has to be thorough. Onion domains can sometimes be deanonymized, social media posts can avoid platform filters by uploading content in images and most importantly - we can catch all of these.
Chadhaus
I’d also like to shout out Correctiv’s English translation of their recent article. Their article contributes to work done by Qurium on Russian bulletproof hosting companies that are critical to hosting Doppelganger domains, and it’s a great read - available here.
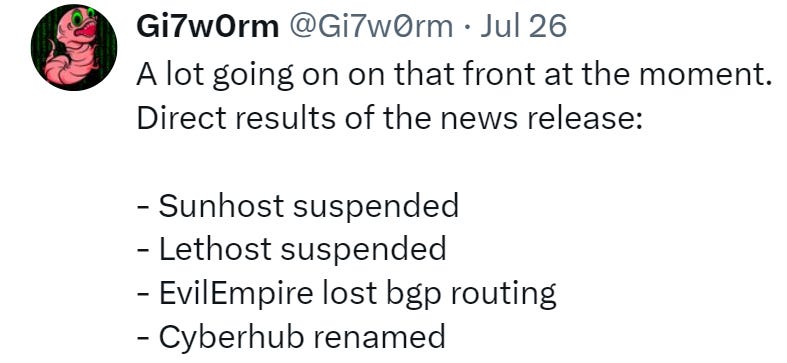
There’s more on that front though from Twitter user Gi7w0rm.
TLDR for the lazy:
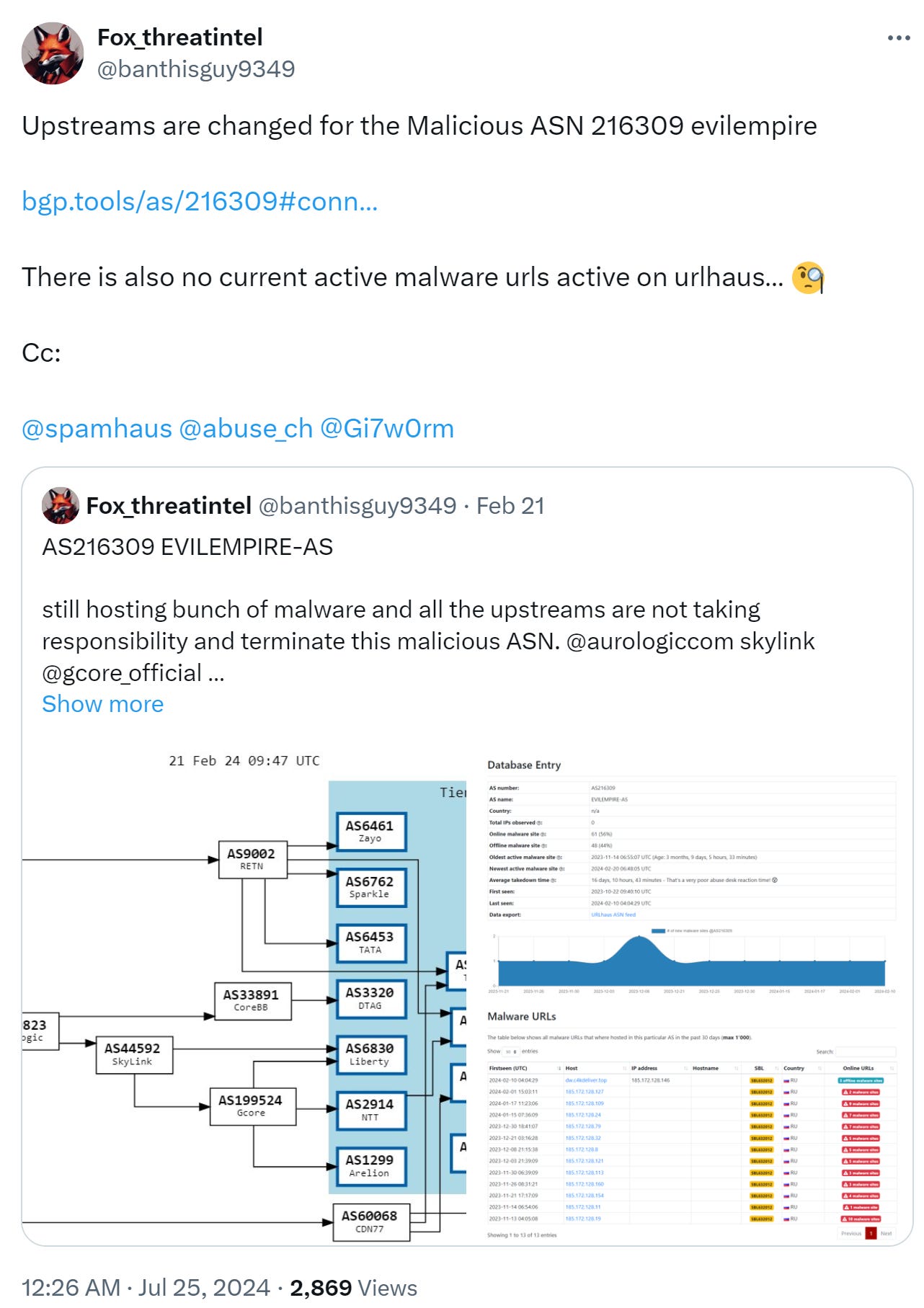
Following Qurium’s report, multiple hosting services that were upstream (meaning provided routing access) of the hosting front companies that were exposed, unsurprisingly, cut off the exposed front companies:
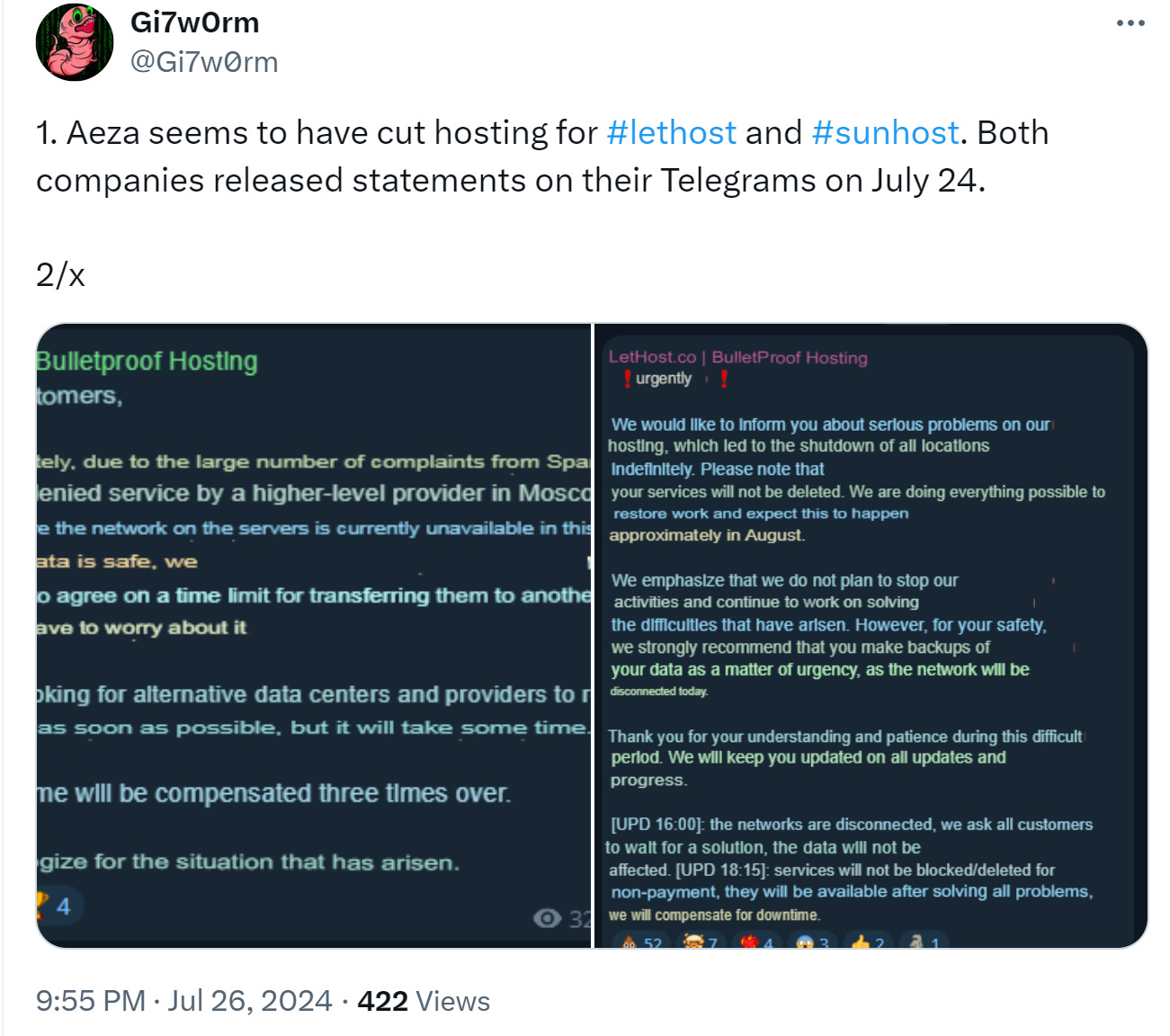
This exposure seems to have forced Aeza, the main hosting company for Evil Empire and other AS, to cut and run from downstream hosting services:
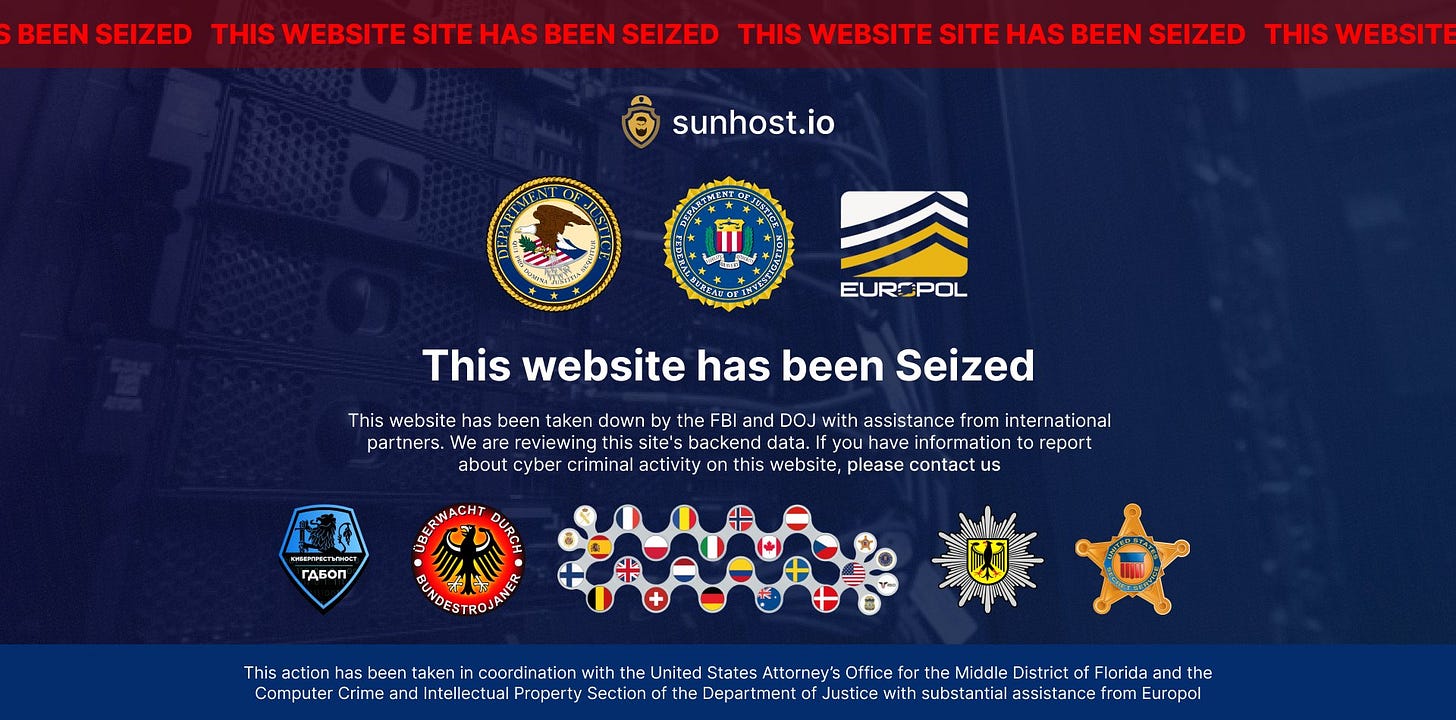
One of the providers, Sunhost,seems to have taken it to an extreme and upload a fake LE Takedown banner:
This takedown notice appears to be fake. There has been no official government/LE announcements on the takedown, and despite overall not looking terrible, there are some logos that don’t exist, weird visual choices, and entities that don’t apparently exist:
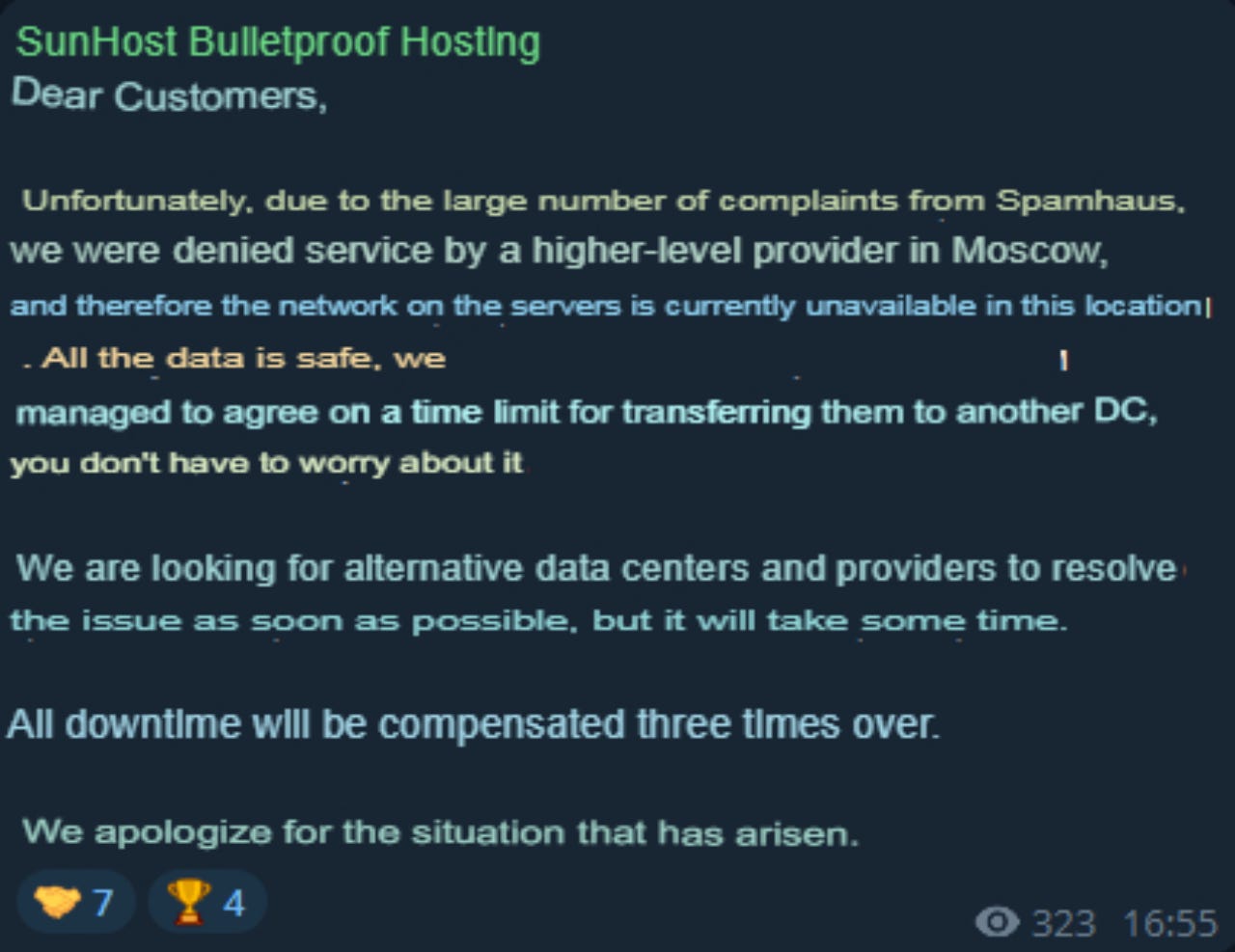
On Telegram, Sunhost (and LetHost as well) explains that apparently multiple complaints came in to Spamhaus re their infrastructure, leaving them to have their service cut off while they look for an new providers:
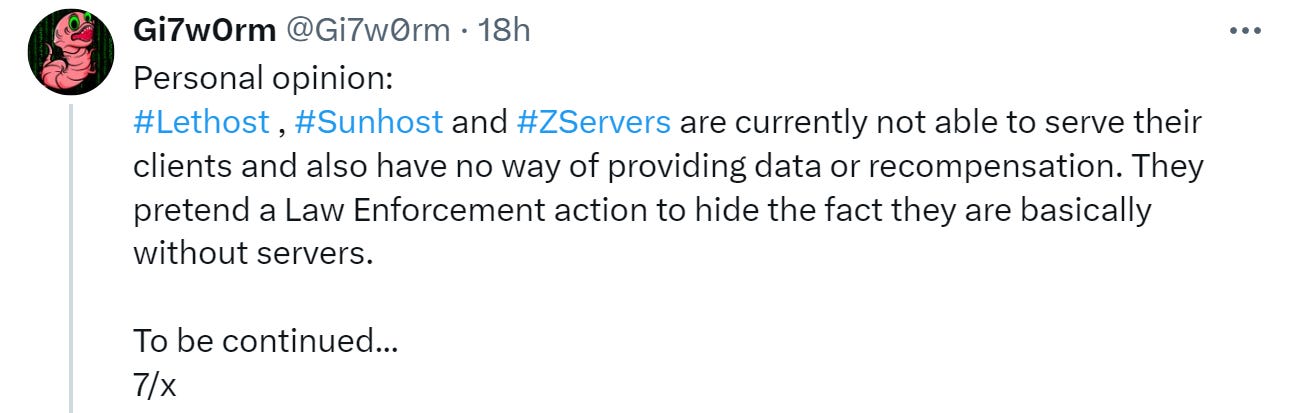
So, why post a fake takedown notice to your site after having upstream access cut off by Aeza? Well, Gi7w0rm provides a very reasonable theory:
So, Spamhaus seems to have played a key role here. In fact, Sunhost actually changed their AS registration for one of their ASNs to denigrate Spamhaus. Bad move on their part, as Spamhaus is extremely online:
That’s it for this week. If you’ve made it this far, I salute you. Check out Telemetryapp.io and let me know what you think below.