In Rruge
Welcome to Memetic Warfare
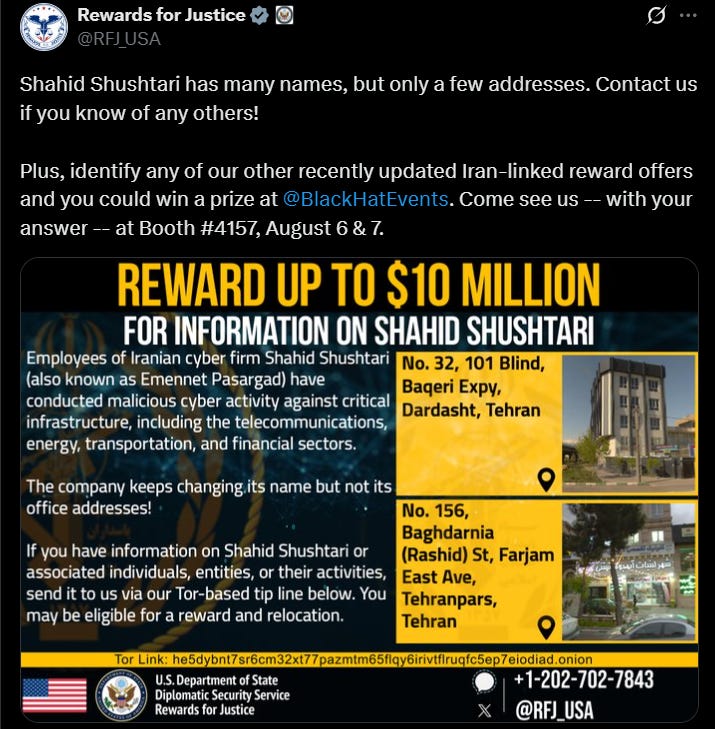
After a short interlude in southeast Asia last week, it’s time to continue looking at Iranian cyber-enabled influence operations, and following the recent renaming of ASA to Shahid Shushtari, I figured why not take a look at some other Iranian activity.
We’ll take this opportunity to look at an old favorite now back at it again: Homeland Justice.
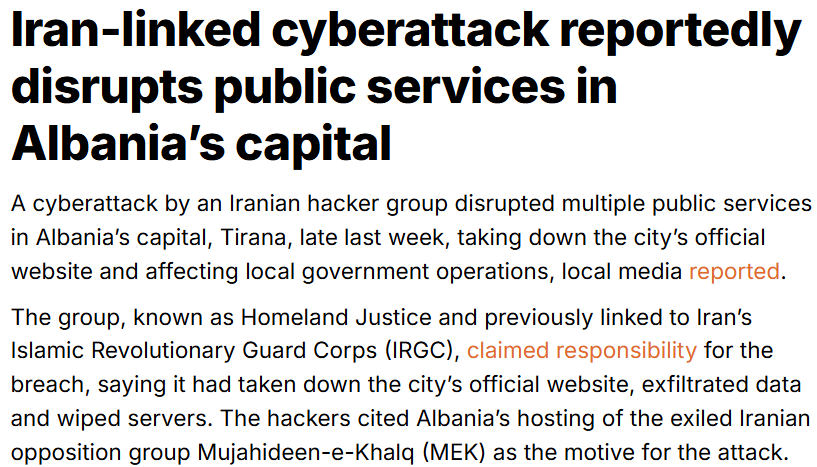
Homeland Justice, the Iranian hacktivist front that famously breached the Albanian ministry of the interior (leading to the severing of ties between Iran and Albania) is back - this time targeting Tirana, the capital of Albania, and is bragging about it on Telegram.
Just to put things into context and to understand why Albania matters to Iran, Albania currently hosts the controversial Iranian opposition group, Mujahedin e-Khalq (MeK), which seeks to overthrow the regime in Iran. The below AI-generated image should make it clear:
Microsoft attributed Homeland Justice to a threat actor group operating under the MOIS, but only with moderate confidence, which Checkpoint backed up:
No one has conclusively attributed the group beyond that, and there are some interesting elements of their latest batch of activity that seems to me to be more similar to ASA (though I’m not attributing this by any means to them, as it’s mostly circumstantial).
Firstly, Homeland Justice began acting up again in late June, close to the date that the Cyber Isnaad Front launched. This doesn’t mean that there necessarily is any relation between the two, but may be indicative of a wider push across Iranian nation-state APT groups at the same time.
Let’s look at their latest activity just for fun.
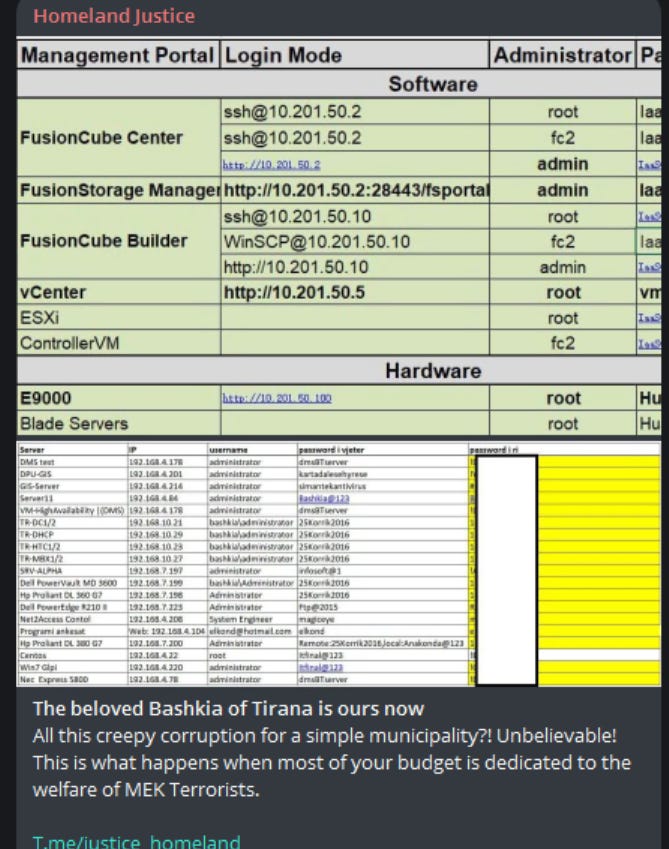
We can see their uploaded evidence of having compromised the city of Tirana on their Telegram channel as well as other related content from the past week or two:
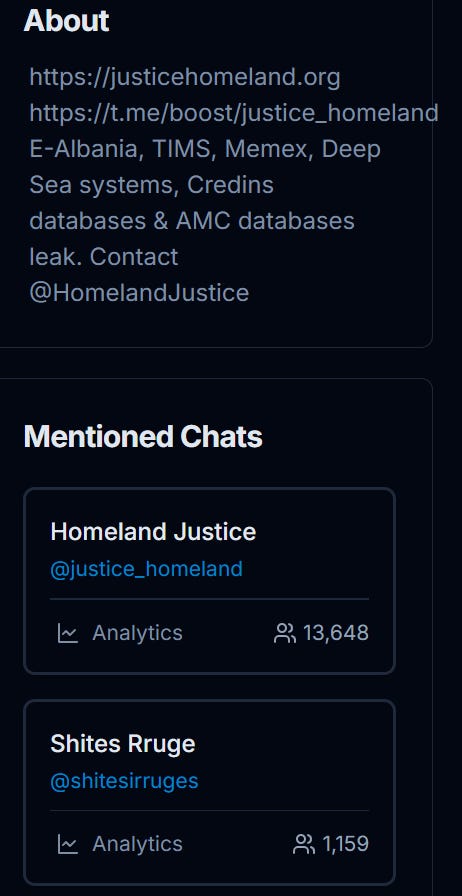
Thanks to Telemetry we can easily see if the channel has forwarded content from any others, and we see in fact that there is only one, apparently named “Street Vendor” in Albanian:
The channel has an obvious AI-generated image of a street vendor with a computer for apparently selling data:
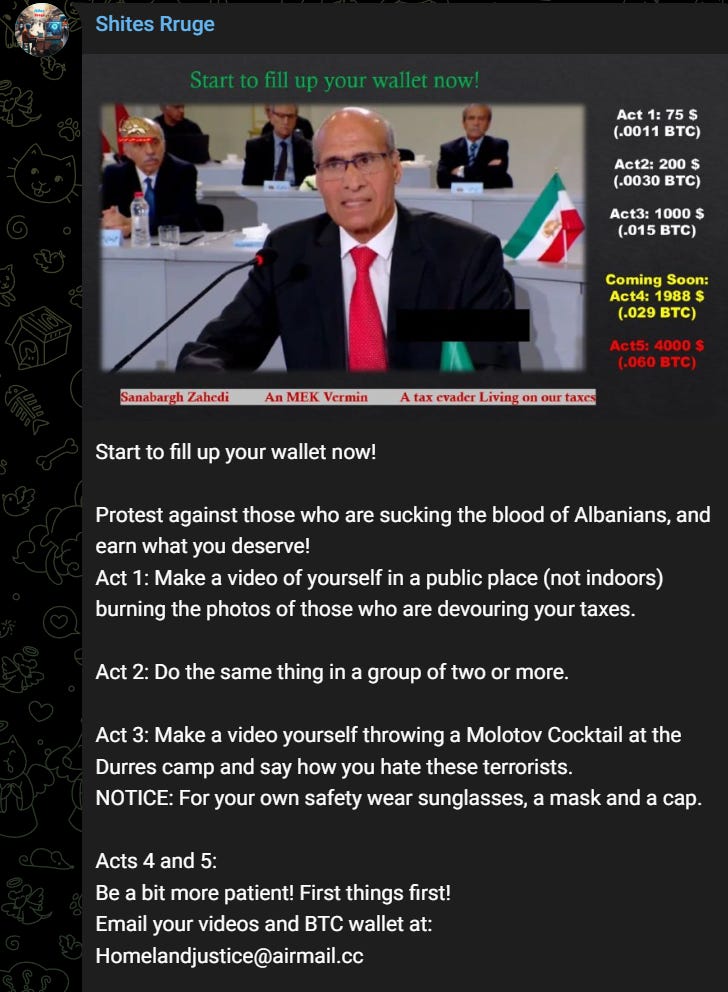
The channel calls on people to send in anti-MeK videos and was mainly active in 2024:
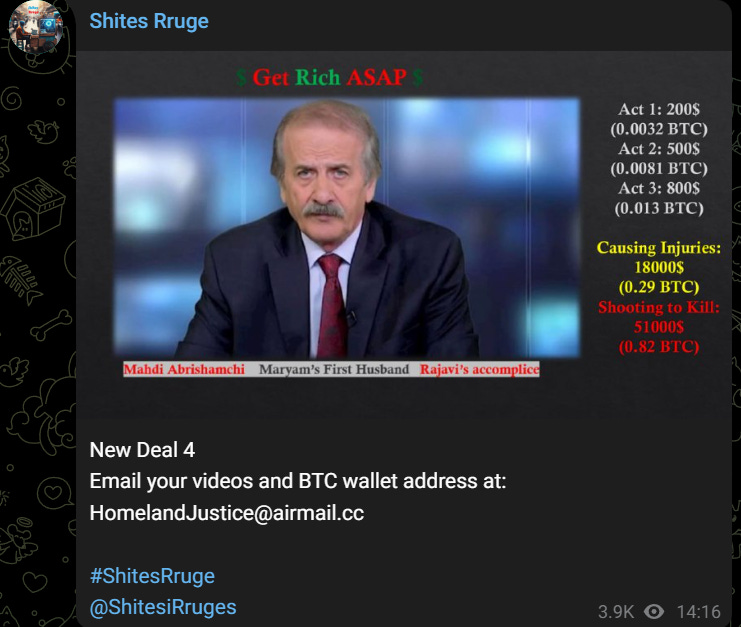
If you look carefully, you’ll see that the videos also call for people to carry out Acts 1-5 for various sums. This then escalates to acts of violence or even “shooting to kill” in exchange for more money in Bitcoin:
So the main Telegram channel is what we’d expect - proof of hacking, politically oriented posts, AI-generated content and data leaks. They also had this IO side channel ready to go calling on people to send in videos/assassinate MeK members.
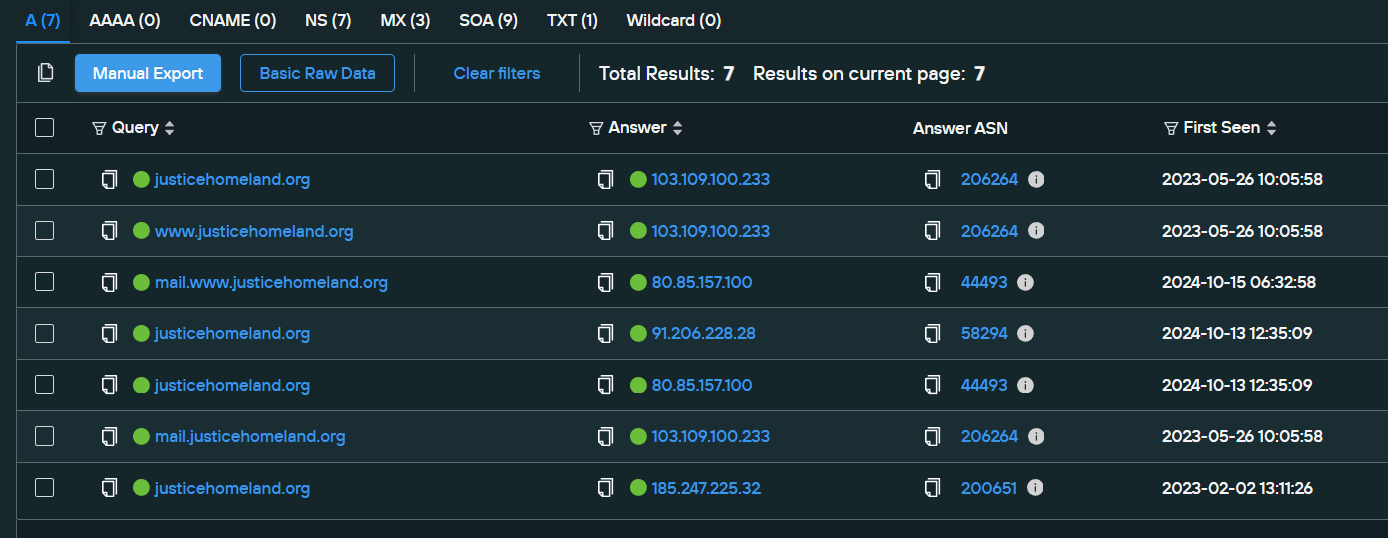
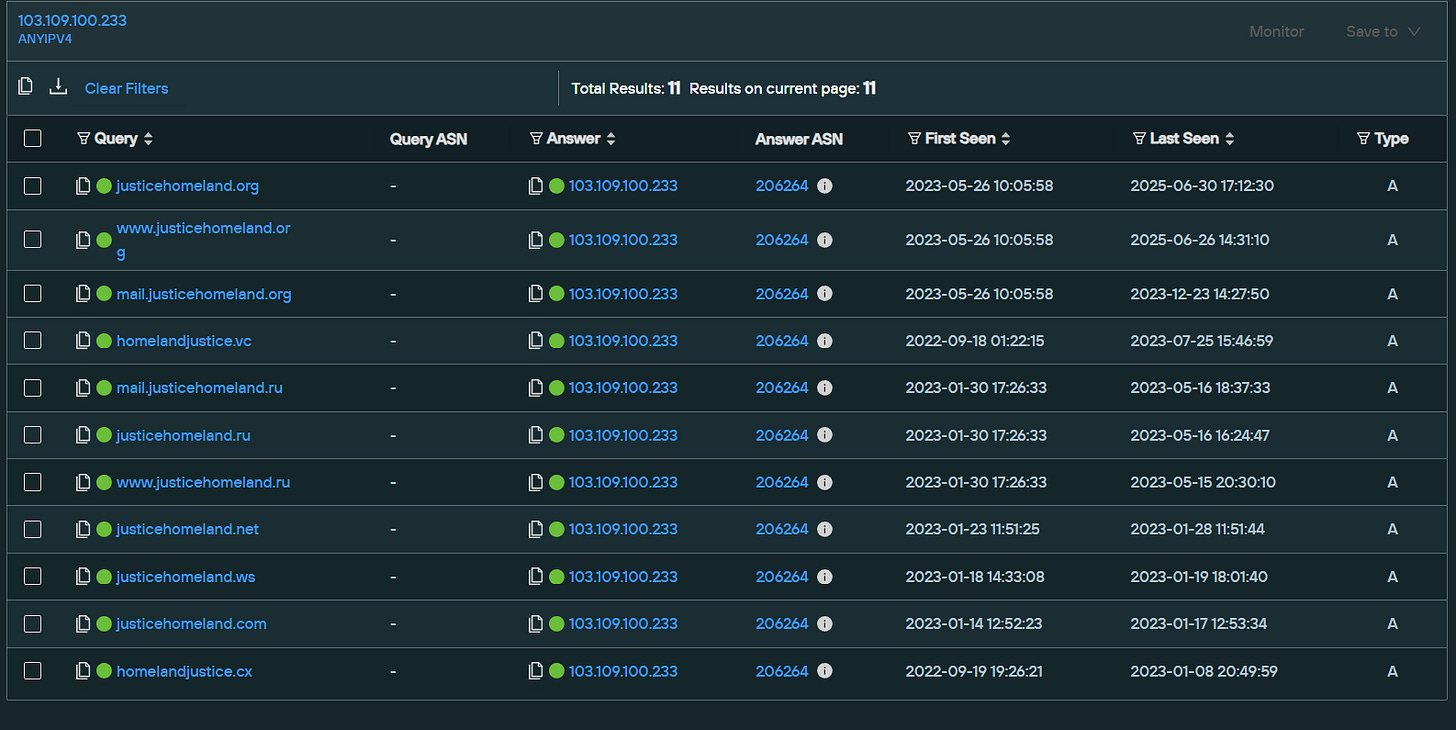
They have a domain also, so let’s take a look at that. The main .org domain has been hosted on a few hosts, mainly on Amarutu (a Hong Kong based provider), a Russian provider and a Bulgarian provider with various ASNs. Some of these have also served as mail servers simultaneously:
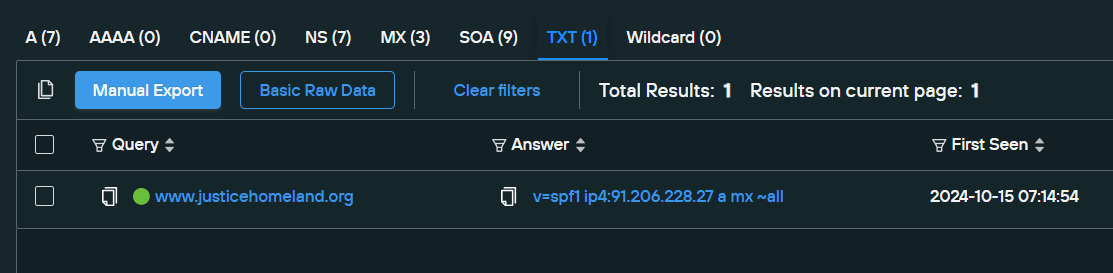
We can also look at the other records here, though unfortunately not much came out of the SOA, NS and other records. The SPF record, though, exposes the one IP address allowed by SPF (sender policy framework) to officially send emails for the domain:
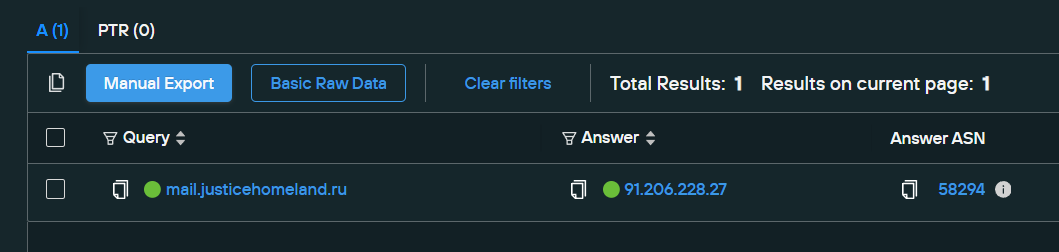
We should note also that this IP, which hosted a mail server for a .ru TLD of the Homeland Justice domain, was sequentially just one down from a previous host of the main domain.
Look at the fourth A record for the .org domain and you’ll see the .28 IP address that I’m referring to. This is common, as people usually rent IP addresses in bulk in a specific range owned by a certain provider.
We can now look into that range specifically ending in 27-29, though in this case there isn’t much point as they aren’t being used anymore - this is the kind of thing that can be incredibly useful in other investigations though.
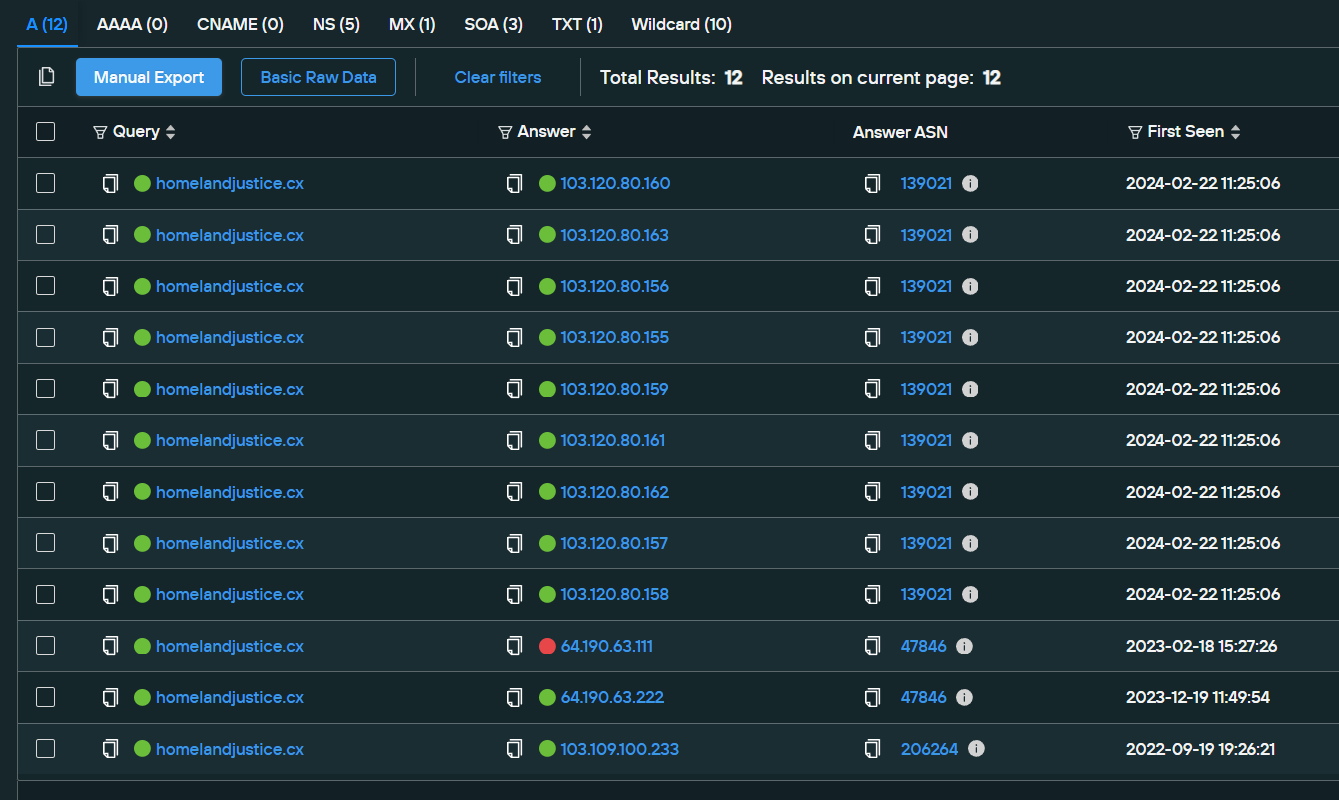
We can see this dynamic become very apparent when looking at the passive DNS records of one of the other affiliated domains. Note how almost all of them are in the same AS:
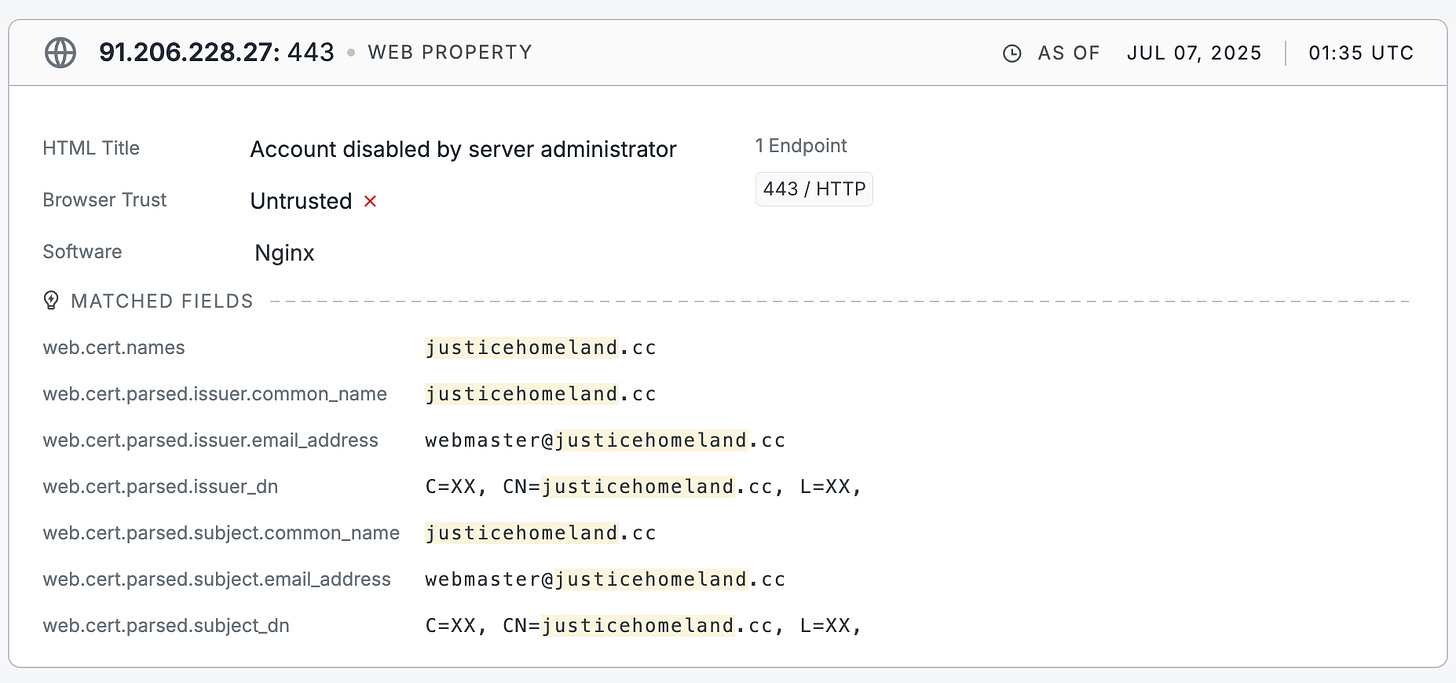
Looking at the current host server’s passive DNS records in Silent Push, we see that on its current host it has also hosted a mail service, as well as multiple historic backup domains on various TLDs - .ru, .vc, .net and even .cx, an uncommon TLD also used by Handala on its backup domains.
The domains are all on the same host, so chances are they did this to avoid blocking of URLs and not because they were concerned about their VPS getting taken down. The domains were registered within a short time frame and seem to be prepositioned backups - also done by ASA and other Iranian threat actors.
Homeland Justice has also historically utilized Russian and Hong Kong-based hosting companies for some of its server rentals, including some even in mainland China.
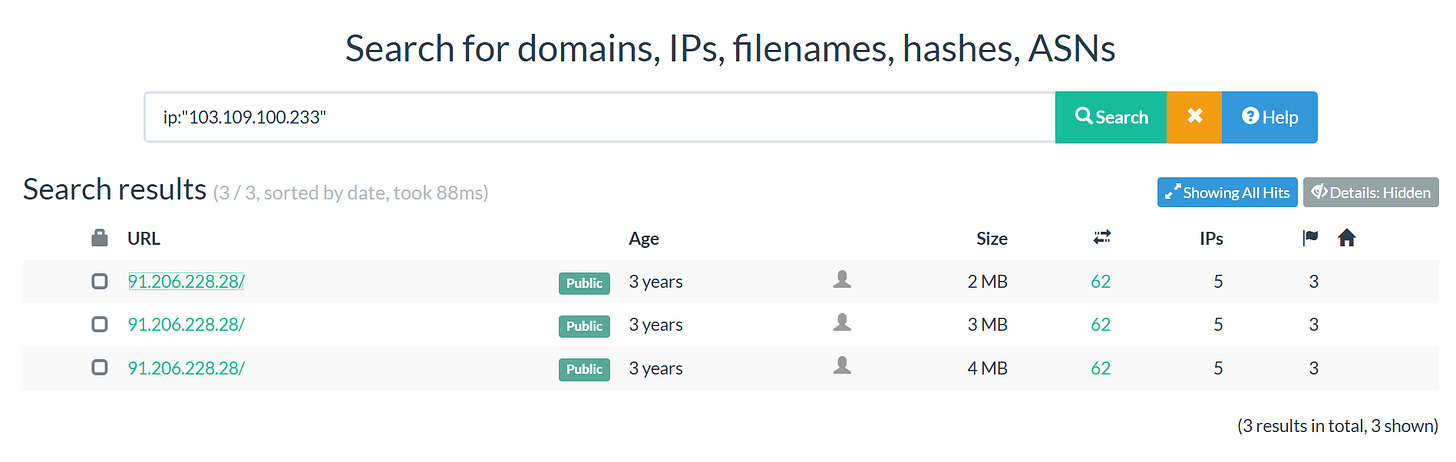
We can find other sites by searching Censys:
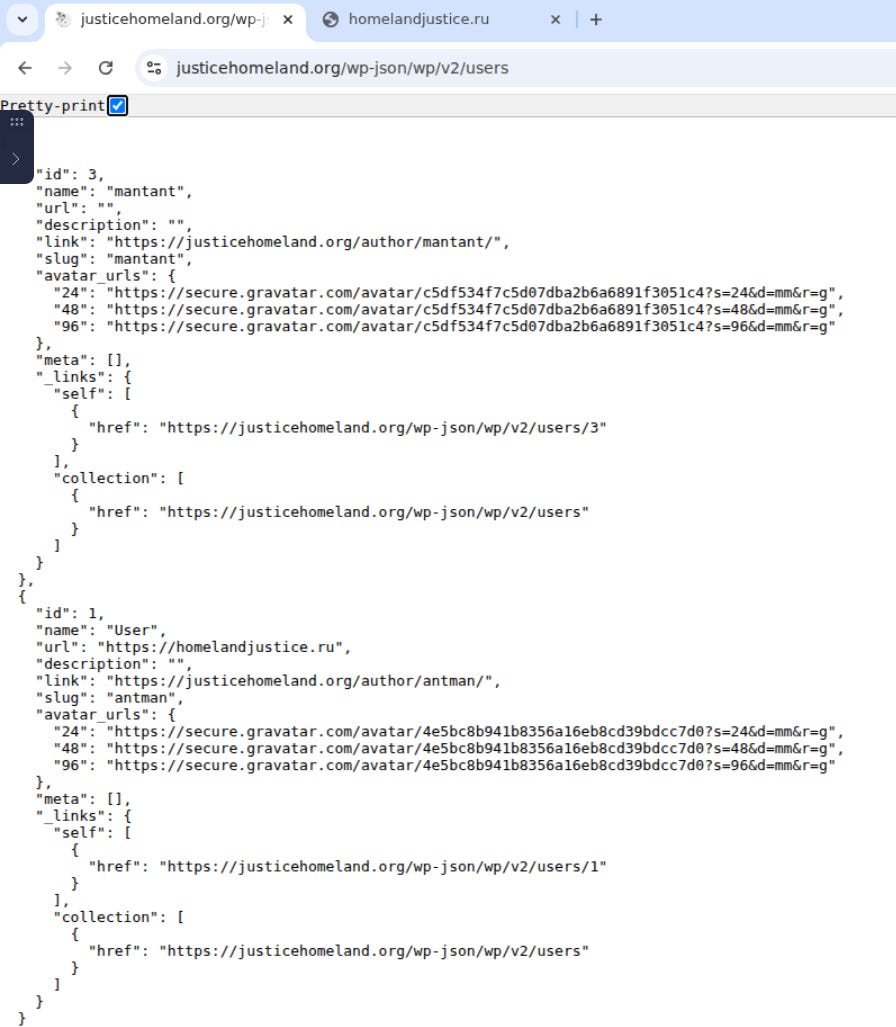
Looking at the exposed JSON of the main site exposes some usernames which unfortunately are too common to pivot off of effectively, but still useful for future comparisons:
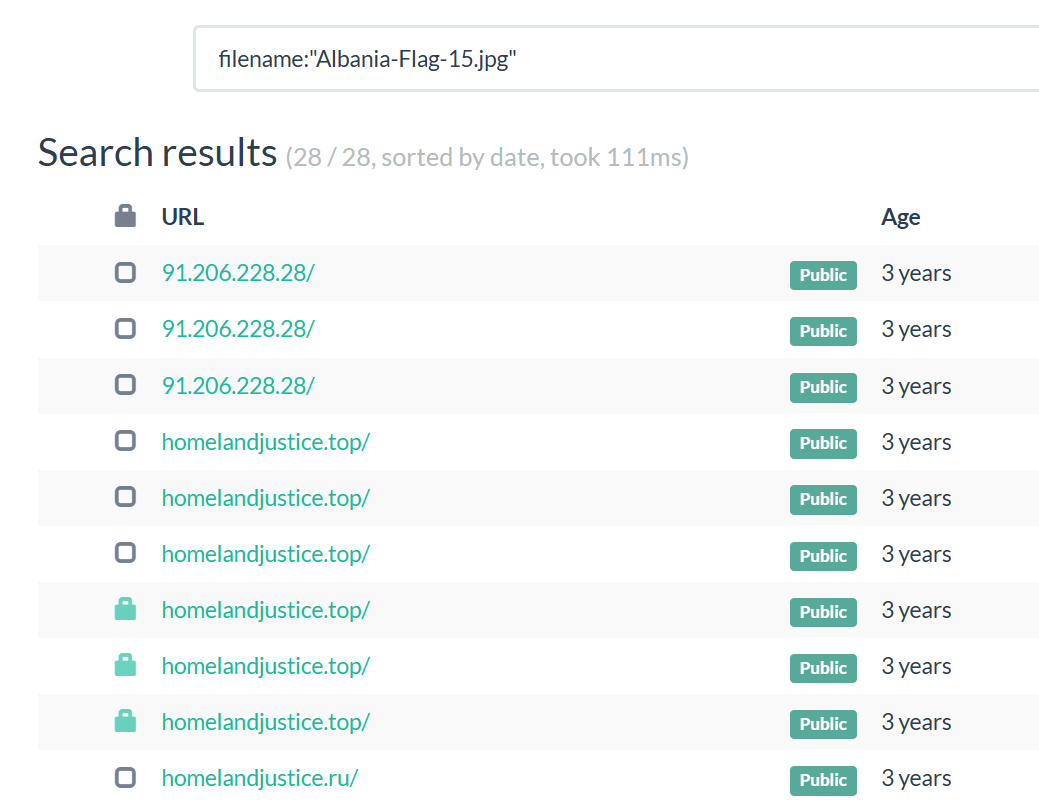
We can also maximize our look at their infra by using URLScan, which unfortunately refuses to scan the whole site. Just querying their current host IP finds that there have been scans of one of the past hosts:
From there we can pivot by filename:
There we go, in this case a new .top TLD domain:
We’ve expanded some of their infrastructure which is good, and a few trends become apparent.
While not ASA and not using many of the common TLDs used by ASA, instead using others such as .top and .cx (as used by Handala e.g.), Homeland Justice still has a LOT of similarity with ASA and other Iranian threat actors, who themselves often share TTPs.
This dynamic makes it difficult to track any operation that isn’t overtly one or the other. This dynamic is by no means unique to Iran - it’s the same with China.
This is in large part due to the same reason: overlapping tooling, infrastructure and TTPs emanating from operators switching groups and moving on in their careers, but also - and perhaps to a larger extent - from different contractors and groups working as providers. Here, for example, we see quite a few as discussed, with the placing of bounties something ASA does as well.
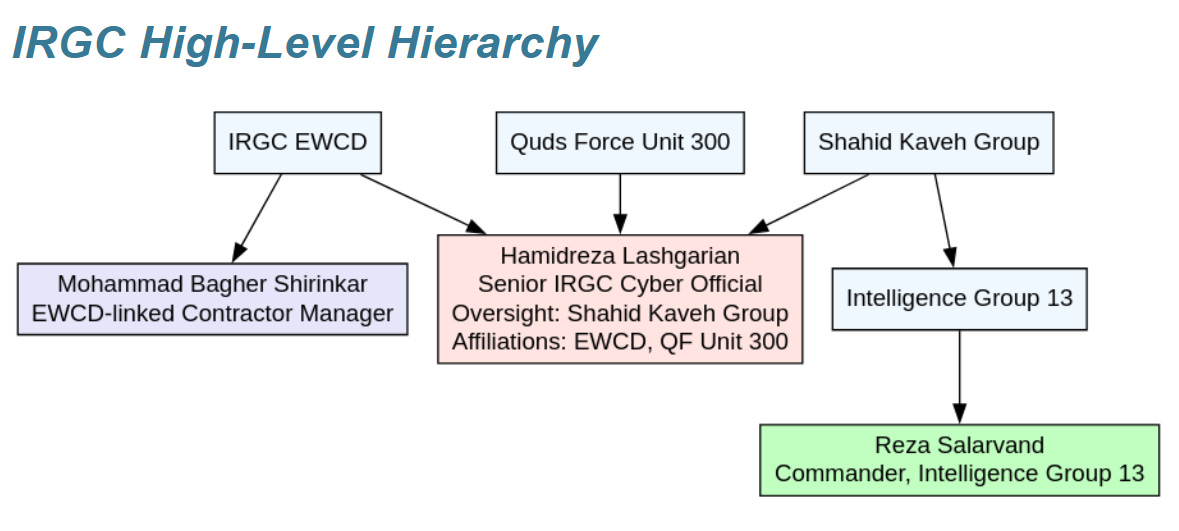
As Domaintools’ threat intelligence team has pointed out in its look at the Iranian Shahid Kaveh group, these groups are often amorphous and function in murky bureaucratic structures - see below from Domaintools a basic graph:
We don’t see much activity referring specifically to Shahid Kaveh other than the odd mention in Microsoft reporting, though as Domaintools has also shown by analyzing leaks, at some point ASA itself turned into a key training and support group for Shahid Kaveh, now sharing a highly similar name - Shahid Shushtari.
There are other shared elements that go back prior to the current operation. Homeland Justice has also historically used a Predatory Sparrow-inspired logo (similarly to APT Iran now adopting a similarly inspired image), showing just how effective Predatory Sparrow was and is at pissing off Iranian actors.
Microsoft also covered some other points showing how Predatory Sparrow inspired later Homeland Justice TTPs:
So, they’ve had birds on the brain to say the least, and that was several years ago. We’ve now seen similar trends move to other Iranian actors.
So, why do I bring this up? Mainly to introduce some open questions. How well do we understand this ecosystem? Is it normal, or possible, to expect coordination or cooperation between these threat actors, or alternatively their highly fluid contractors and front companies? To what degree do shared or similar choices in iconography indicate shared actors or direction?
Perhaps. Or, alternatively, they simply have similar organizational culture and undergo similar or even shared training programs, leading to some MOIS and IRGC operations looking more similar than one would even expect from a shared state.
Anyway, it’s always a good time looking holistically at a specific threat actor to see how they evolve over time.