Smells like Teen Sepeher Ayandehsazan
Welcome to Memetic Warfare.
This week, we’ll take a look at the “Cyber Isnaad Front”, a new operation that I first wrote about at the FDD, available here, with Max Lesser.
We attributed the operation to ASA based on significant overlap in TTPs, behavior and infrastructure, so let’s get to it here.
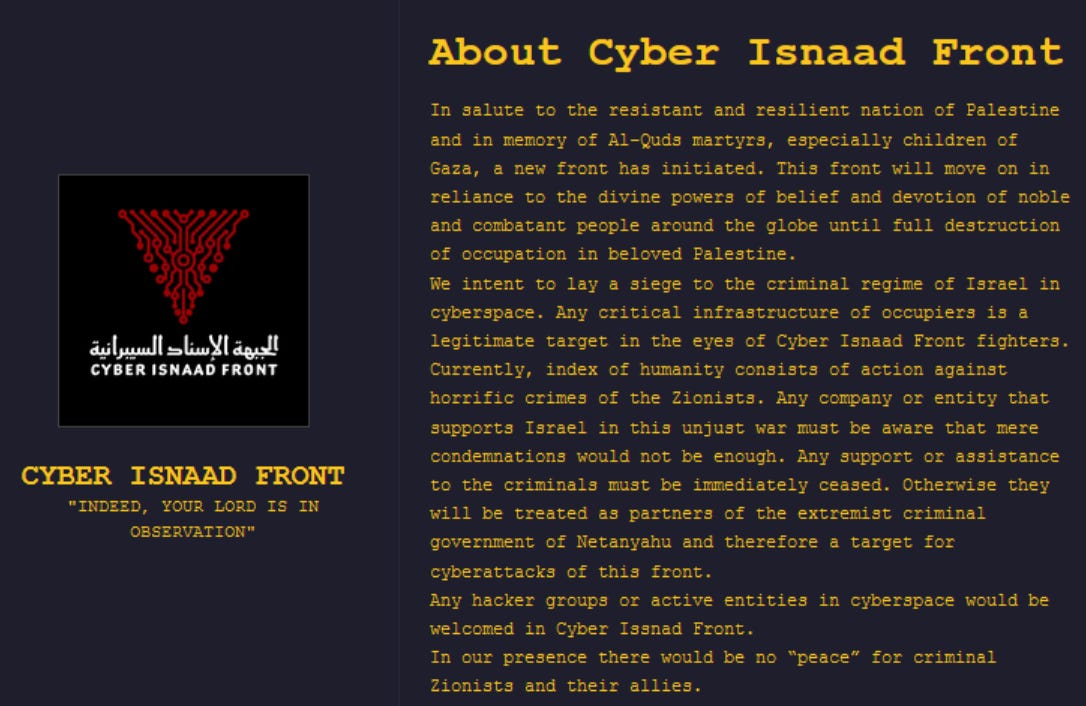
The Cyber Isnaad Front, a hacktivist group (front) targeting Israel, is active on Telegram and an Onion domain, sporting a “tech”-inspired version of the infamous red triangle used to show Israeli targets in Hamas propaganda videos.
The operation is quite new, with its Telegram channel having been created on June 17th:
The Cyber Isnaad Front has multiple similarities with ASA TTPs. Firstly, they move fast, as ASA has shown they can do in the past. The Cyber Isnaad Front has already compromised multiple Israeli companies, the majority of which have some connection to the Israeli defense apparatus - primarily as manufacturers. This is similar to past ASA targeting, which has focused on Israeli critical infrastructure, government agencies and suppliers of the government and military.
Like past ASA operations such as “ZeusisTalking” and the “Cyber Court”, the Isnaad Cyber Front Telegram channel posts high production-quality videos showcasing data hacked from its victims, including the actual act of compromising a network, though these are unconfirmed. The channel also posts videos from hacked CCTV cameras:
Similarly to ASA, it also posts stylized doxxing images and documents of the employees and management of its victims.
The Cyber Isnaad Front isn’t clowning around though, and in a first for Iran-nexus actors (to my knowledge) they decided to use an actor in their videos. This may be a sign of Iranian actors developing independently or alternatively mimicking Russian use of actors in its influence operations.
The Cyber Isnaad’s Onion domain is also a common thing for hacktivists, especially for ASA.
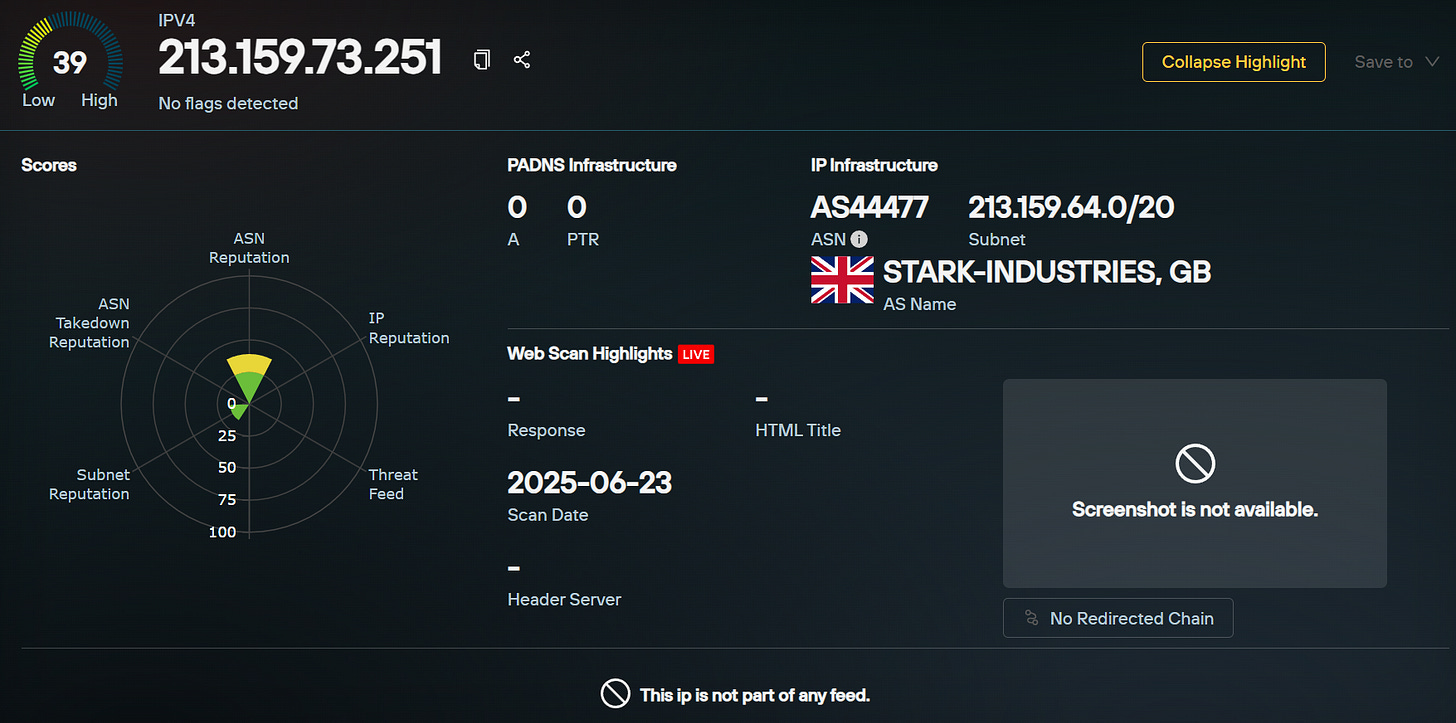
The Onion domain can be easily deanonymized by querying Censys for the word “Isnaad”, which retrieves three results. The first two are irrelevant, but the third host is labelled as a bulletproof host with port 80 exposed. Looking at the host confirms that it is in fact the host of the Onion domain.
The hosting firm listed seems to be a subleasing firm for Stark Industries, the bulletproof hosting firm that powers the Russian influence operation Doppelganger. ASA is known to utilize Russian hosting firms, including Stark Industries, for its operations as of late.
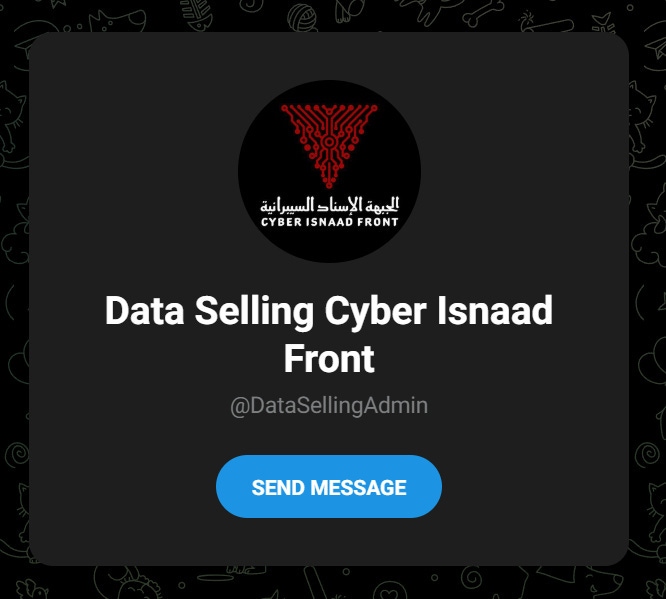
The source code of the site also exposes a Telegram account used for dselling data that isn’t yet linked to on their site.
The onion site itself further explains the goals of the Cyber Isnaad Front, utilizing languages of “war crimes” and justice that are commonly used by Iranian actors, and ASA in particular.
The Onion site also hosts evidence of past Cyber Isnaad Front operations, including a planned “Data Selling” section that is currently filled with placeholder text - another development from Iranian threat actors, which usually simply post the data on forums or open Telegram channels.
The next indicator of the operation being tied to ASA is the coordinated Iranian state media promotion of the Cyber Isnaad Front. Similarly to past ASA operations, Iranian state media works in lockstep with their operations, pushing out similar articles across Iranian outlets - including in Hebrew - to promote the group.
The Cyber Isnaad Front has ties to other Iran-nexus hacktivist groups online such as Gaza Children Hackers.
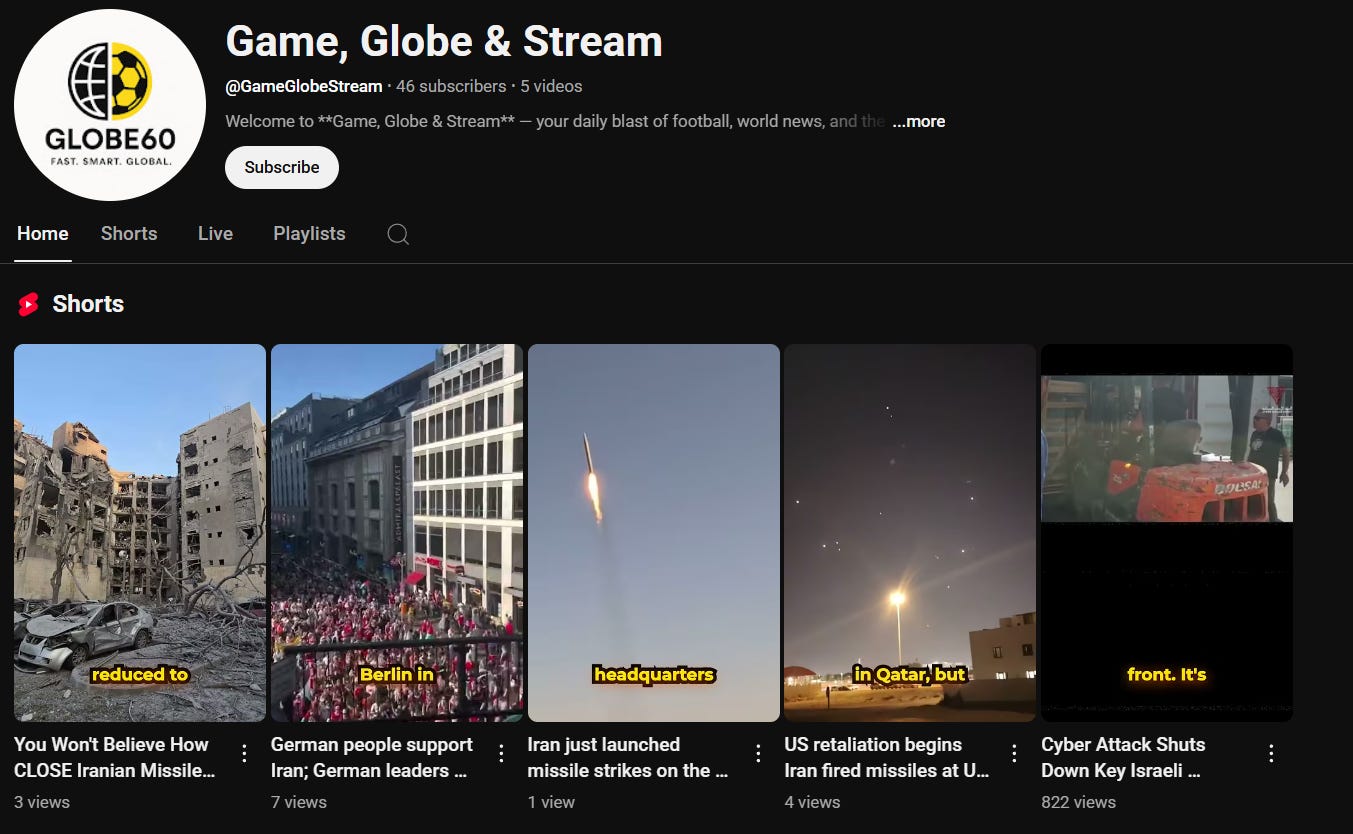
Beyond state media, online amplification has been comparatively minimal. One YouTube channel has shared a video promoting the Cyber Isnaad Front. The channel is repurposed, having been created in 2011 and focusing on sports:
So, on the whole looks like an Iranian operation, but one that has learned (a bit).
Unlike most ASA operations, we don’t have any clearweb domains which makes sense, as those are by far the most vulnerable in terms of opsec.
We do have an onion domain and Telegram account, and the interesting choice to sell data.
We also have a dedicated doxxing section - something often done by ASA and groups like Handala.
Pretty high investment value per operation, common for ASA.
Coordinated state media amplification is also big here, making me inclined to believe that it’s ASA.
Minimal online amplification beyond a few accounts, similarly to past ASA operations which haven’t been big on regular social media.
Infrastructure overlap with past operations - use of same hosting firms
The use of an actor is an interesting jump in investment.
So, seems pretty clear who’s behind it, but there’s always some uncertainty. Anyway, that’s it for this week! Leave any jokes, comments or complaints below and as always, check out telemetryapp.io.