VirusBearSparrow
Welcome to Memetic Warfare. This is a long and special post, so buckle up buckaroos.
This week, we’re going to take a long, hard look at an interesting cluster of Iranian hacktivist fronts. I know - it’s been just Iran as of late, but that’s because of the war. I hope to go back to investigating activity from other countries soon.
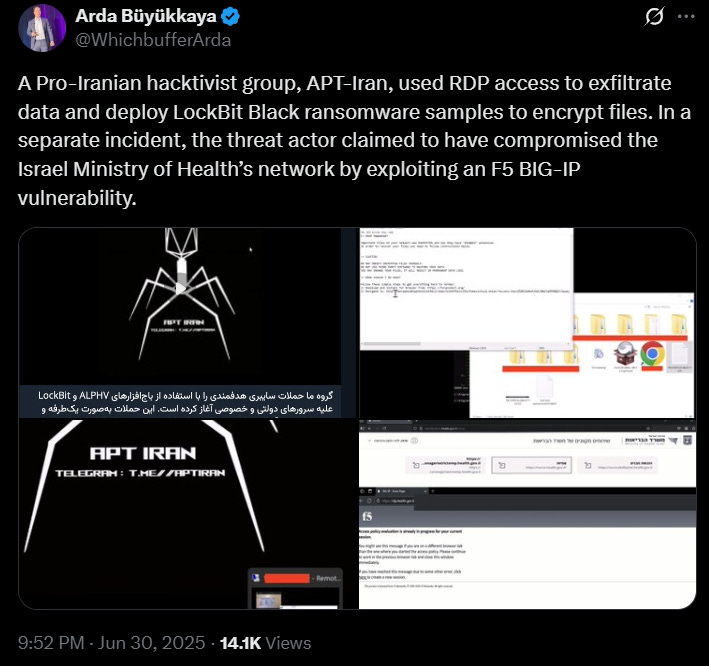
The situation starts with a tweet from security researcher Arda Büyükkaya. He posted that a known hacktivist group, APT-Iran (very creative naming, much wow) had begu nusing Lockbit Black ransomware in its operations. Most recently, the group claimed to have targeted the Israeli Ministry of Health via RDP to access an exposed system. It’s far from clear if they actually did pull this off, as the screenshots aren’t conclusive evidence.
CyberKnow also pointed out that they have been using ALPHV ransomware against Israeli targets:
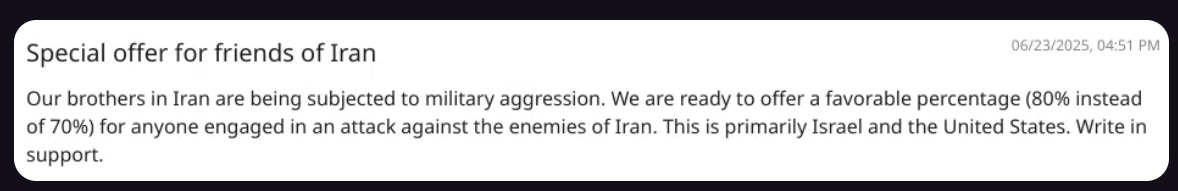
All of this ransomware activity apparently seems to be happening at once, as the Iranian Pay2Key ransomware-for-influence campaign is also back and offering discounts for those that target Israeli victims:
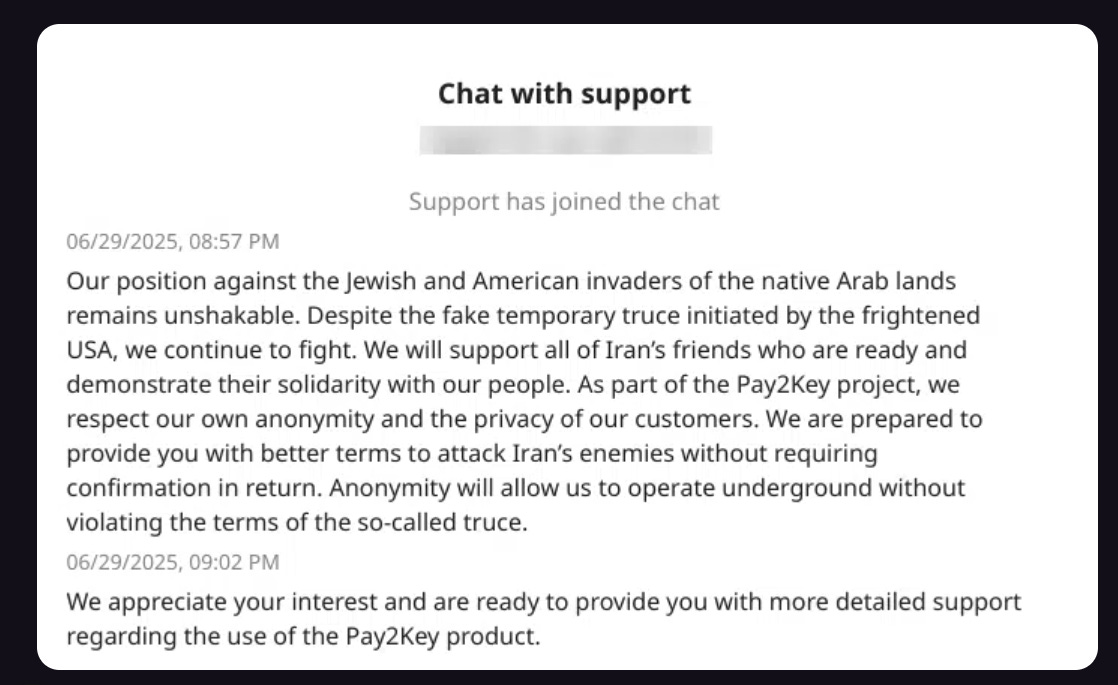
They further expound in their support chat:
So, this is a hot topic and one coming from a group that I hadn’t heard from in a while. APT Iran has been around for a year or two at this point and I’ve come across them before, though they hadn’t done anything of note as of late, so I figured why not take a look.
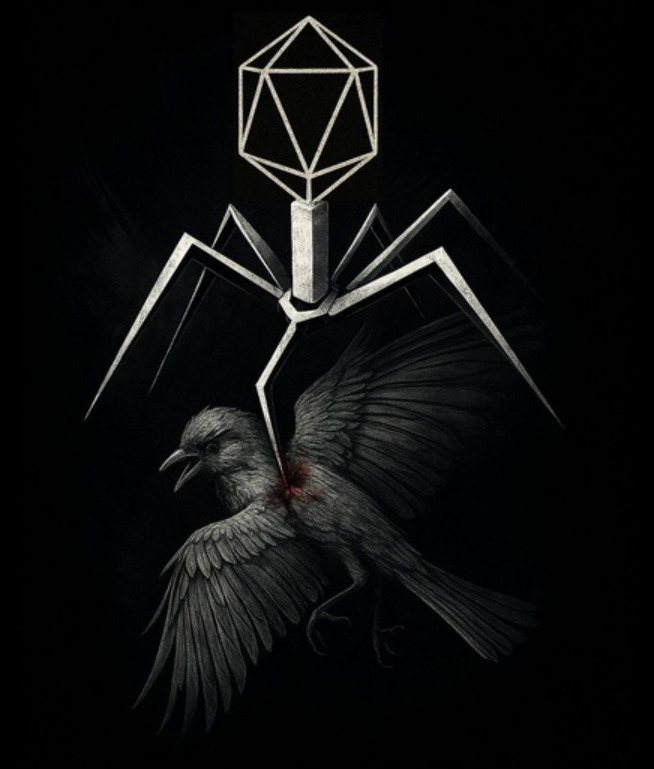
APT-Iran has since taken some interesting action. The first is their obsession with Gonjeshke Darand (Predatory Sparrow) - an anti-Iran hacktivist group that has targeted Iran in the past. This is a big change of pace for a group that not onyl targeted Iranian targets in the past, but mostly talks about infosec in a general sense - sharing CVEs and so on.
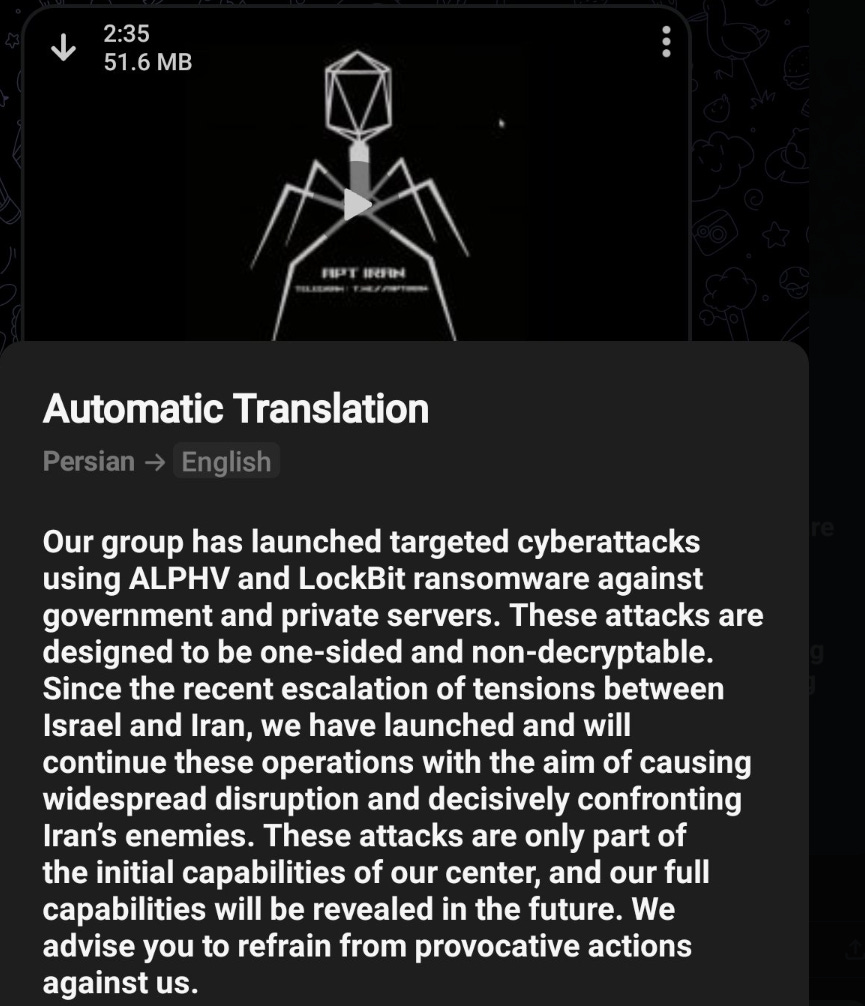
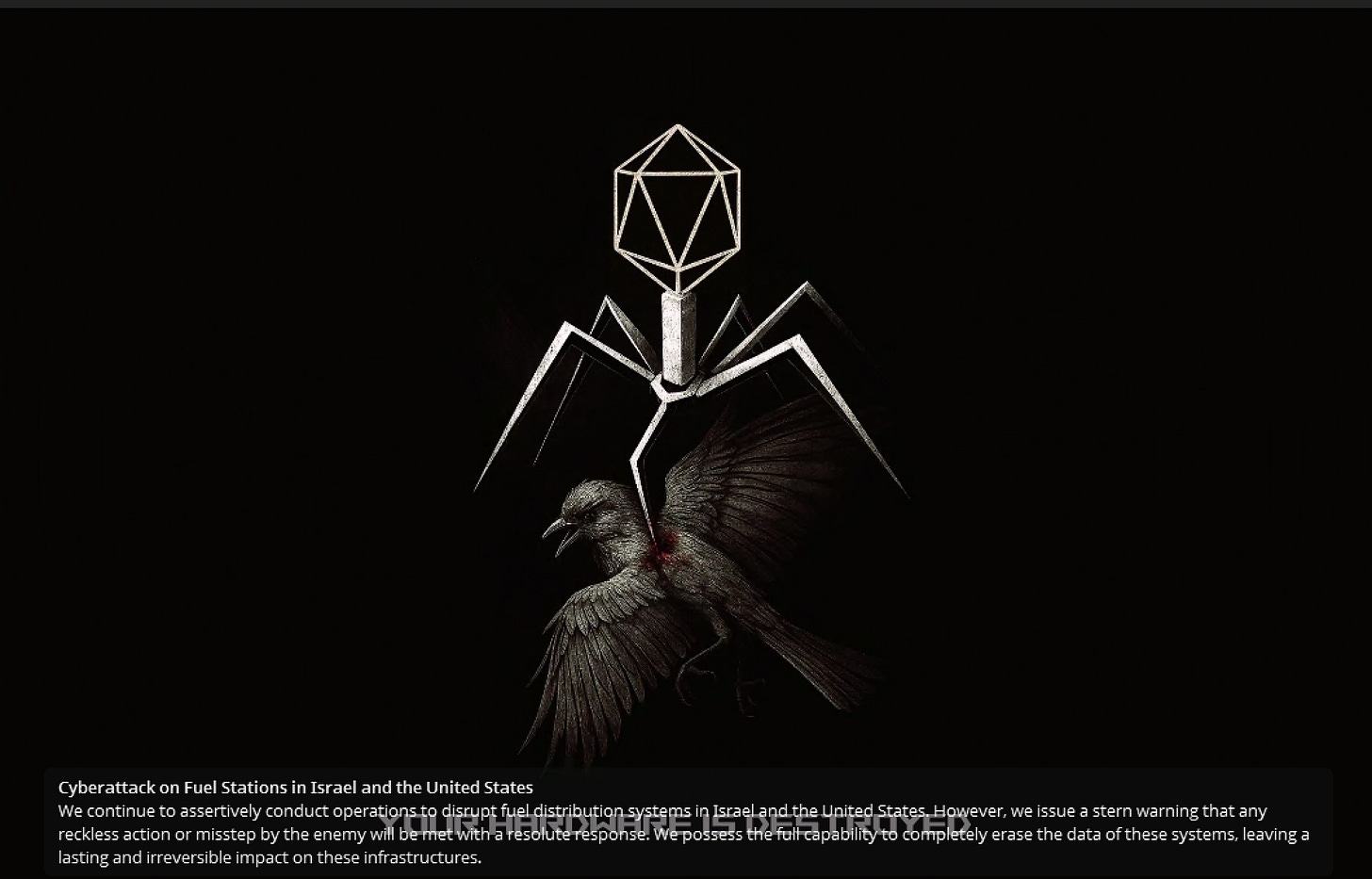
Let’s review their new topic du jour. They’re so obsessed that they changed their logo from a robot spider to a robot virus spider impaling a sparrow:
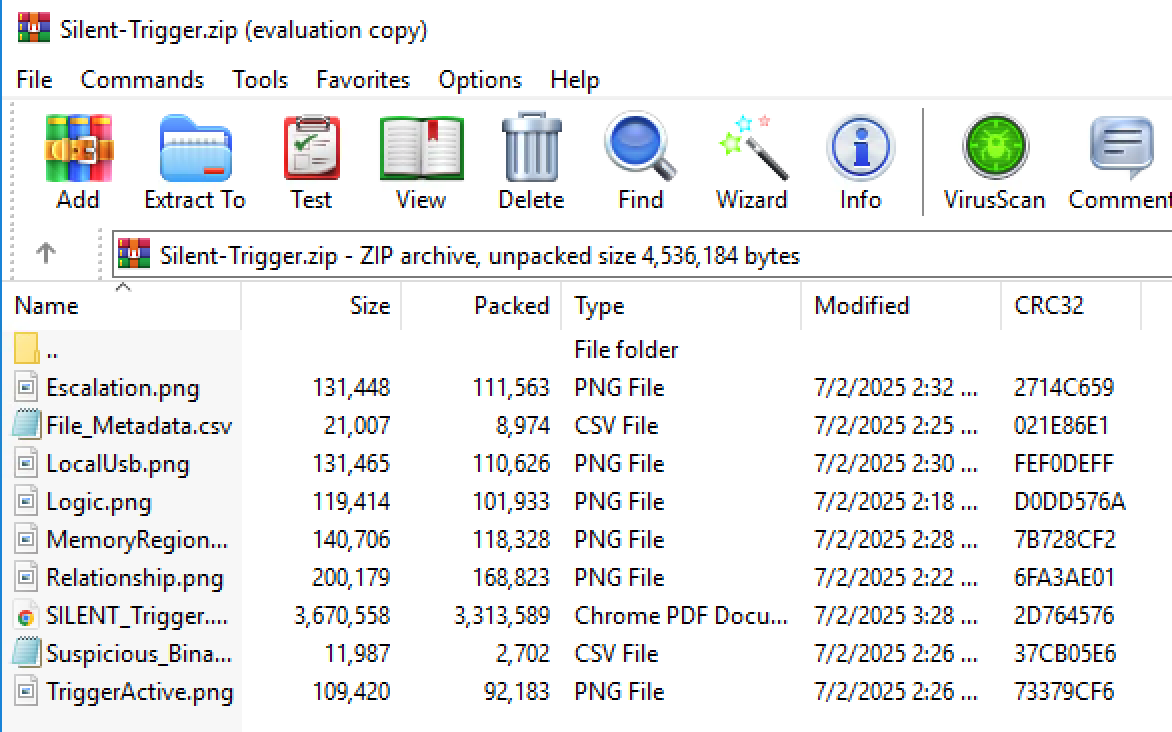
But it gets more interesting from there! They then provided a write-up of some of Gonjeshke Darand’s operations that they named “Silent Trigger”:
The writeup includes a full ZIP file of screenshots, metadata and a report:
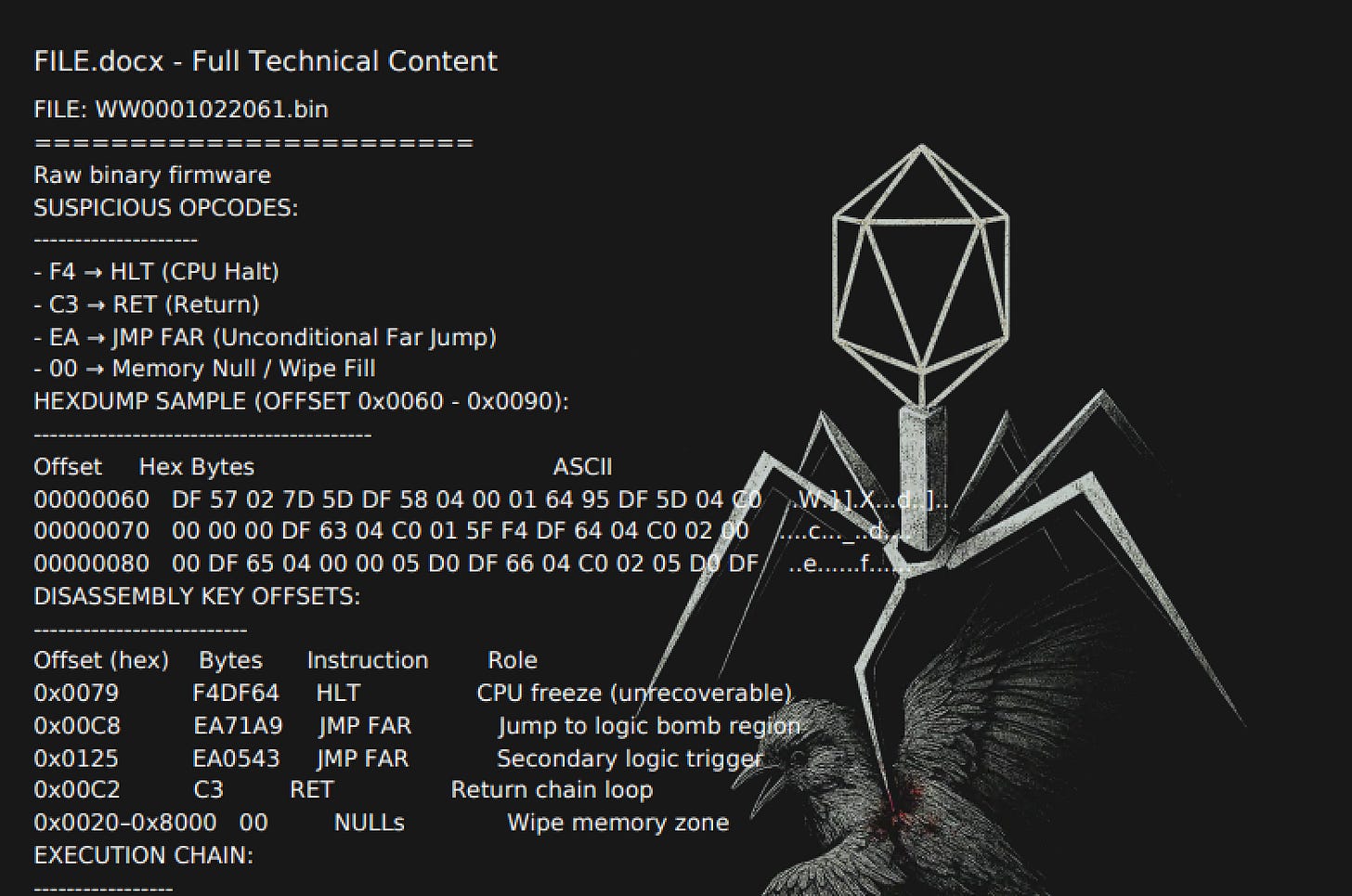
Look at the reverse engineering of a binary file including low level analysis:
This isn’t the kind of thing we usually see from your average hacktivist groups, showing that this is a threat actor with at least an understanding of the basics.
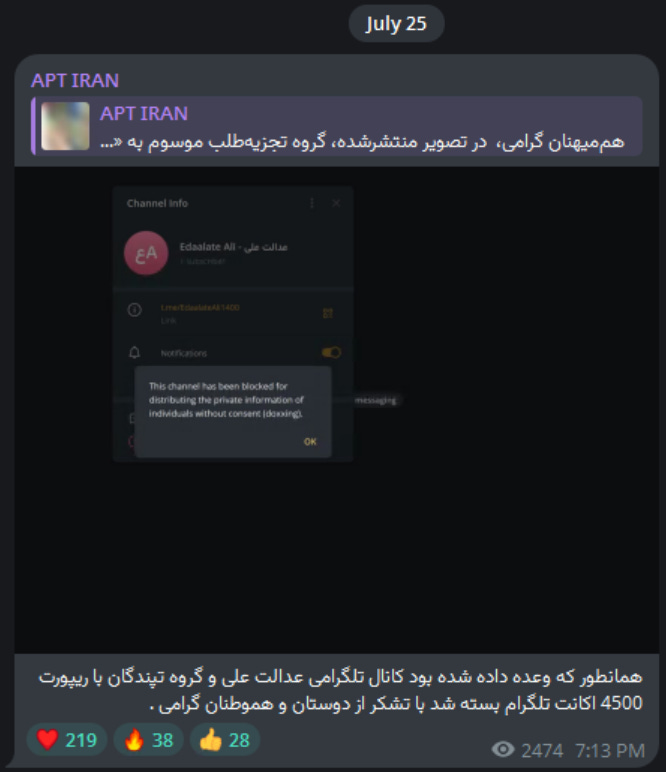
They’re also hostile to other anti-Iran hacktivist groups, such as Edalaate Ali and Tapandegan, whom they have tried to mass report:
They apparently have had some minor success, claiming to have taken them both down by crowdsourcing mass reporting. I’ve checked both. Edalaate Ali is still up, but Tapandegan is in fact suspended by Telegram.
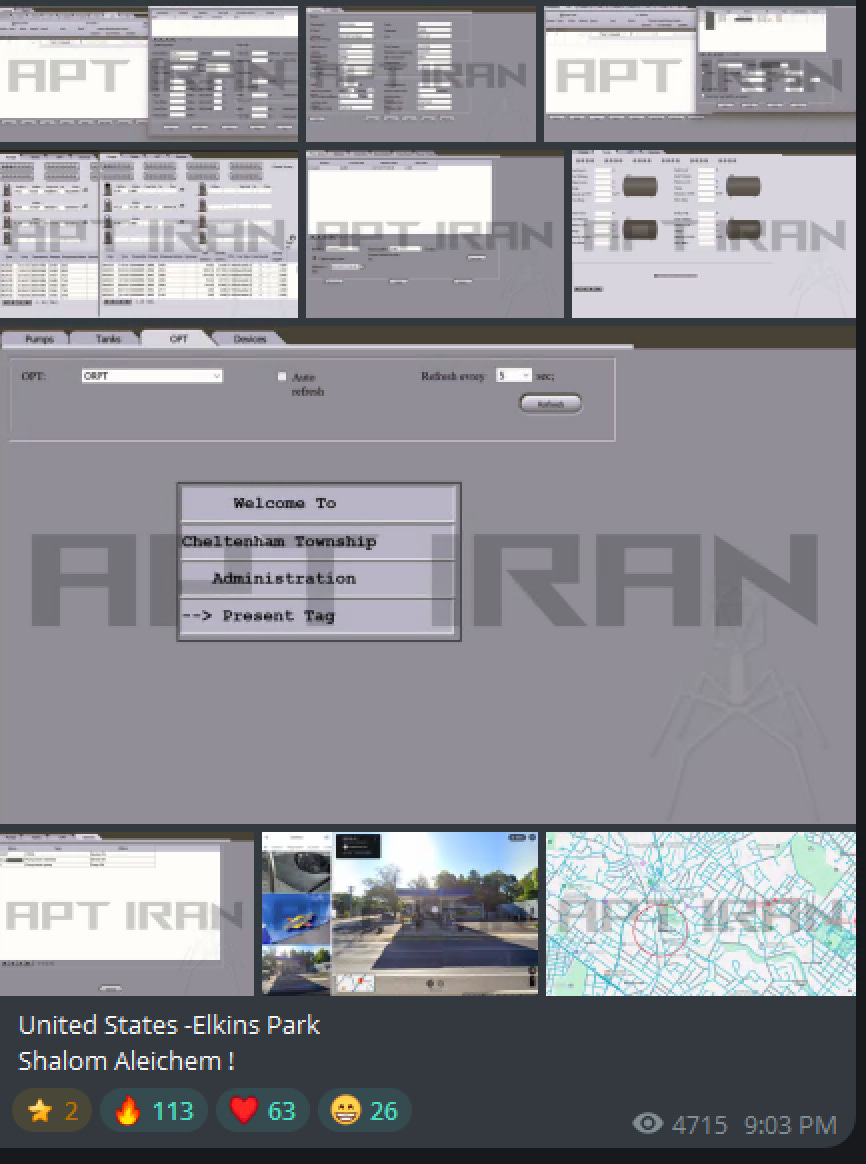
From a channel discussing general information security topics and the occasional bit of hacktivist activity targeting Israeli companies and others, APT Iran has since accelerated their operational tempo, claiming to have targeted critical infrastructure in the US - again, without conclusive proof.
They start off with targeting some gas stations in Israel and the US. This is interesting as it may be a reference to past Gonjeshke Darand operations targeting Iranian gas stations, or it may just be an operation of convenience and opportunity. They did upload a several minute long video of the alleged compromise, showing some dedication.
They also show some apparently compromised panels, although these in of themsleves don’t mean that they were successful - I haven’t seen any confirmation, but they also could have been successful - it’s unclear.
While impressive, this could be sourced from past operations, similar software or otherwise, and the OSINT stuff is of course not confirmation.
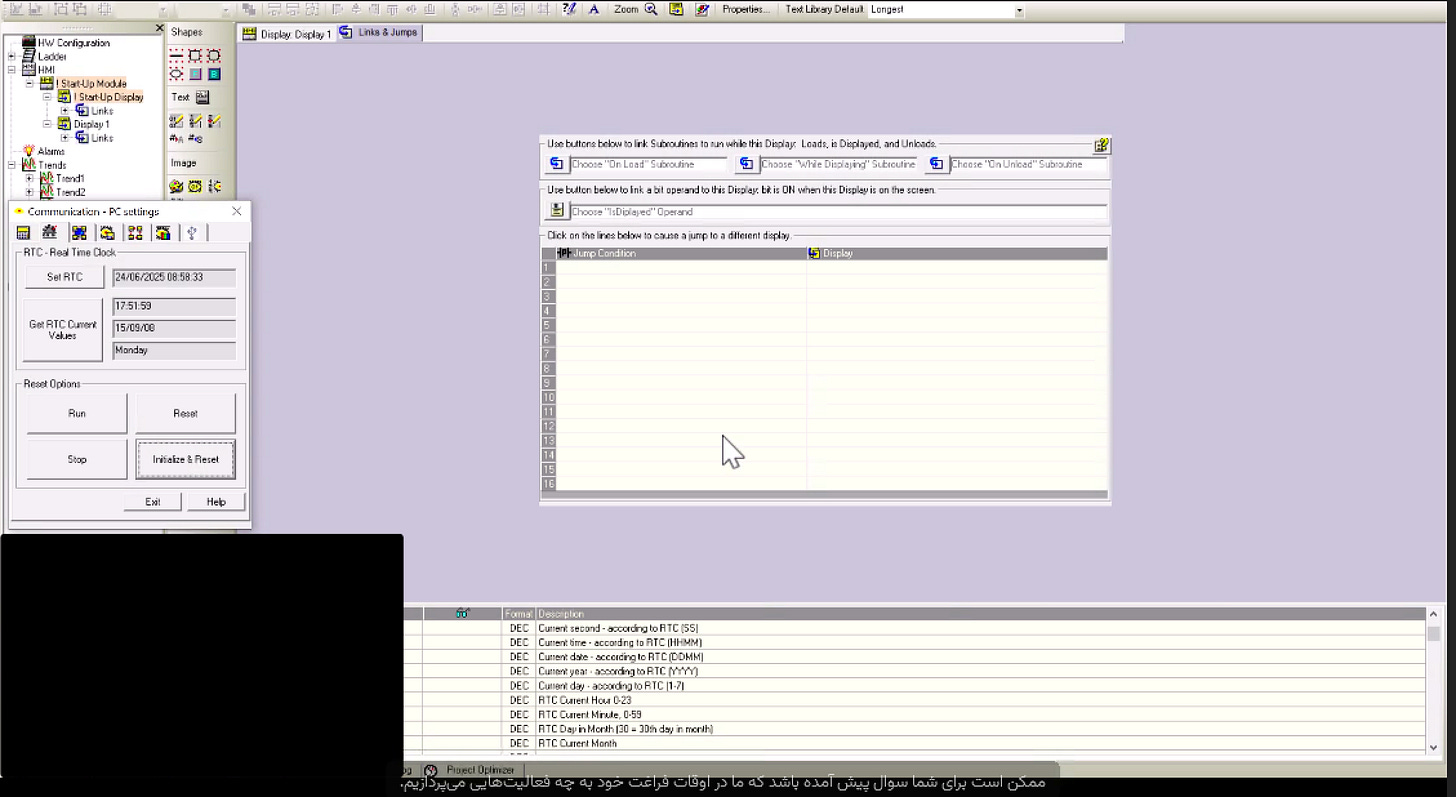
After that apparent unconfirmed operation, they claimed to have targeted some other PLCs - common targets for Iranian threat actors like Cyberav3ngers, Hunt3r Kill3rs and so on.
After this operation it begins to get really interesting. At this point they begin overlapping with Cyberav3ngers (if you don’t know who they are, they’re one of Iran’s leading cyber-enabled IO threat actors, having targeted US water plants and other critical infrastructure). As an aside - this is in fact assuming that this new-ish CyberAv3ngers channel is in fact them. This budding friendship began with them referring to each other on their channels:
To then doing apparent joint operations with shared logos targeting what else but Unitronics PLCs (the number one PLC favored for targeting by Cyberav3ngers):
What an interesting scenario we have found ourselves in! It seems that not only have the two formed a tentative hacktivist alliance - something commonly done in the space - but that they really are operating together in a joint fashion. If they aren’t actually doing operations together, then they certainly want to appear as if they are, which is noteworthy as is. There are a few questions:
Are the two operating together?
If not, why are they appearing to do so?
What may be an increasingly feasible answer is that the two are in fact run by the same operators as different fronts.
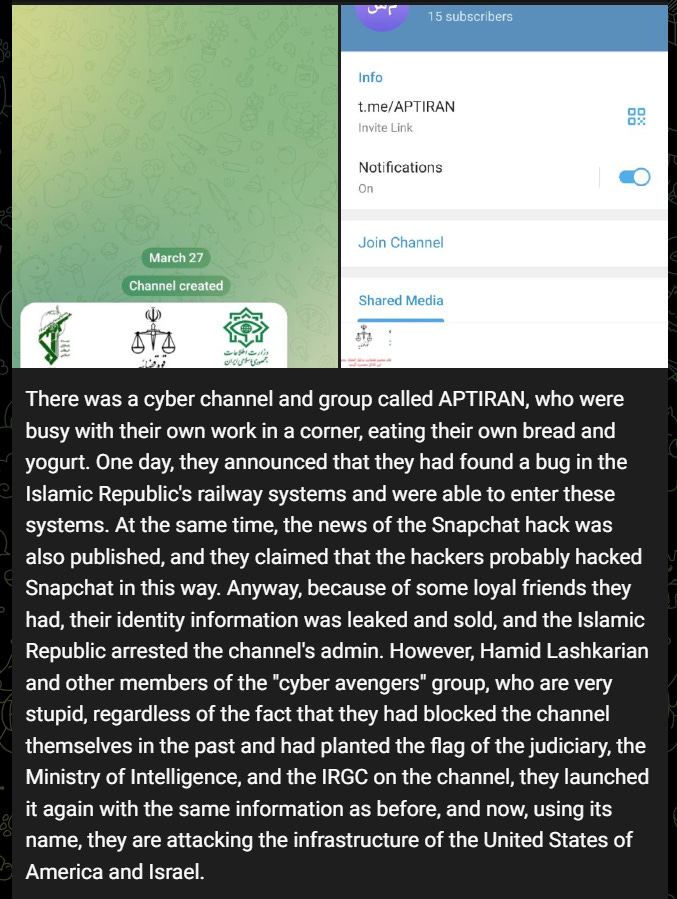
If you Google them enough, you may come across a post from Iranian dissident Nariman Gharib. Gharib claims that APT-Iran used to be (and this is what I remember it as) a hacktivist group that occasionally attacked Iranian targets, until one day they apparently were taken over by members of the notorious IRGC hacktivist front “Cyberav3ngers” in March, 2024:
Is this feasible? Is it possible that the IRGC, and the same unit evne, runs both?
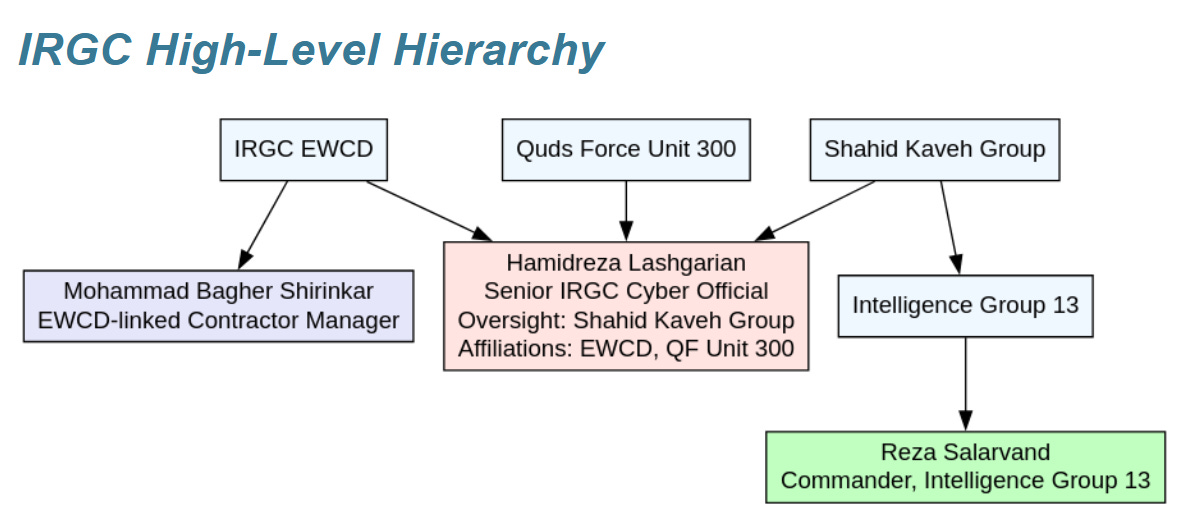
We know that the Cyberav3ngers are run by the IRGC, and in particular a group run by Hamid Reza Lashgarian, the head of the IRGC CEC (Cyber Electronic Command). In what is surely a coincidence and not a sign of nepotism, his son Mahdi Lashgarian is a key figure in the group as pictured below:
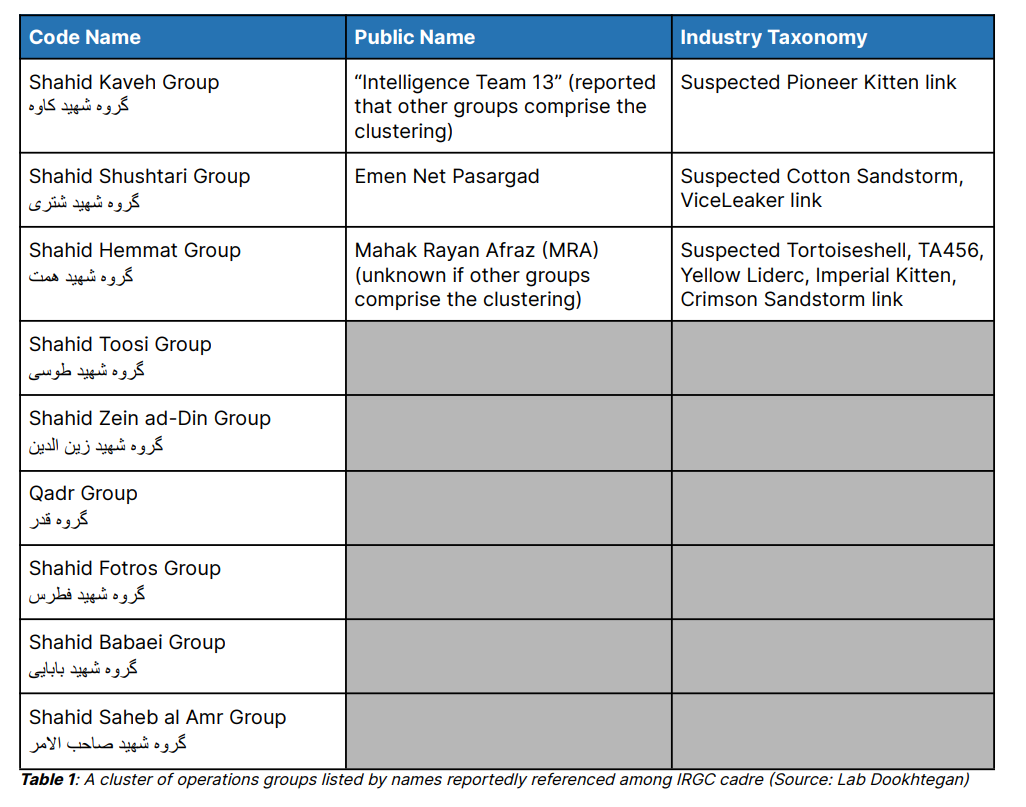
From leaks, we actually know a fair amount about this group. I won’t get overly in-depth here, but to make it clear as per reporting on said leaks on IRGC and MOIS units and the front companies that form them/work for them from Recorded Future, DomainTools and others, we know quite a bit. These groups, interestingly mostly named after martyrs (Shahids) perhaps to stir up religious sentiment, have their public names - apparently Emmmenet Pasargad, now known as ASA, is known as Shahid Shushtari, whereas CyberAv3ngers operates until Intelligence Team 13, otherwise known as Shahid Kaveh.
Domaintools provides us with some graphs as to this as well:
Based on these leaks and org charts, we see as per Domaintools that IG 13 runs CyberAveng3rs, and that many believe apparently that Mahdi Lashgarian is the guy behind Cyberav3ngers in particular, as well as the Cyberav3ngers-adjacent figure Mr. Soul, which we won’t discuss now but feel free to google.
In my opinion, it’s quite possible and even probable that IG 13 runs APT Iran and that they have now decided, for whatever reason, to begin integrating the two operationally. Almost everything lines up - the new targeting style, victimology, the overt activity, and even the potential claims of respsonsibility for fake attacks: CyberAv3ngers has done it before, faking attacks on Israeli critical infrastructure.
It’s also possible that one of the companies and contractors that service IG 13 or other units are doing this and working in collaboration, we don’t know.
In short - it’s a strong “maybe”, or even perhaps a “probably” that both are now run by CyberAv3ngers, and if so that’s a big change in the threat landscape and worth following up on.
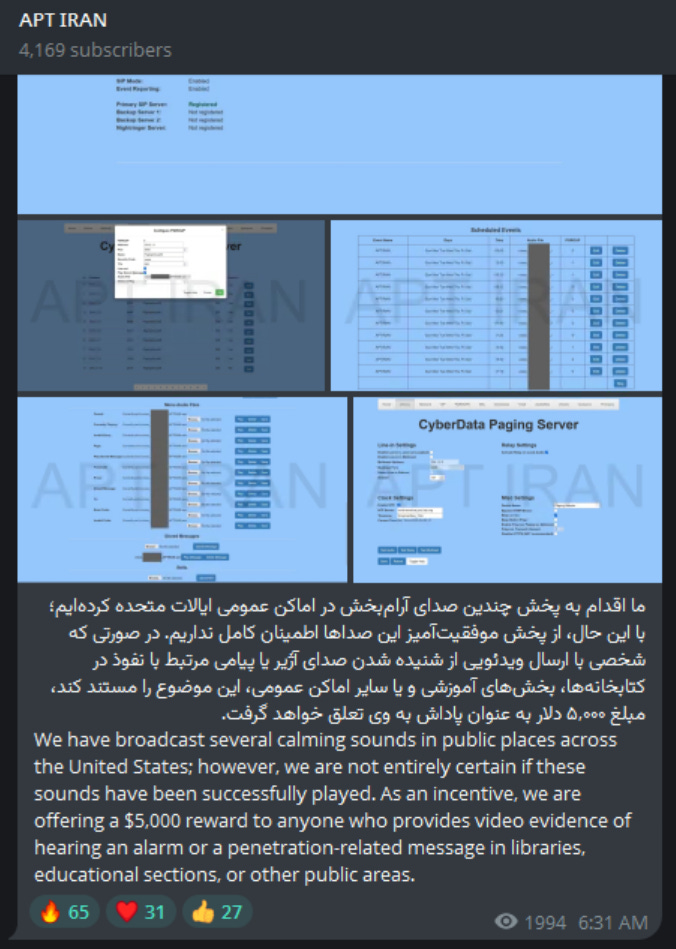
APT Iran has continued to remain active as well independently, most recently claiming to have “broadcasted calming sounds” by compromising speaker systems in America. To confirm that these are successful, they’re offering 5000 USD as a reward to anyone who provides video evidence of one of these being played. I have yet to see any videos of this, so may well also be fake.
That’s it for this week’s overly long-winded post. I hope that you found this niche topic as interesting as I do.