Working 9 to Fars
Welcome to Memetic Warfare.
This week we’ll look at an interesting, presumably Iranian recruitment operation targeting Israel brought to my attention by friend of the blog Milan Czerny.
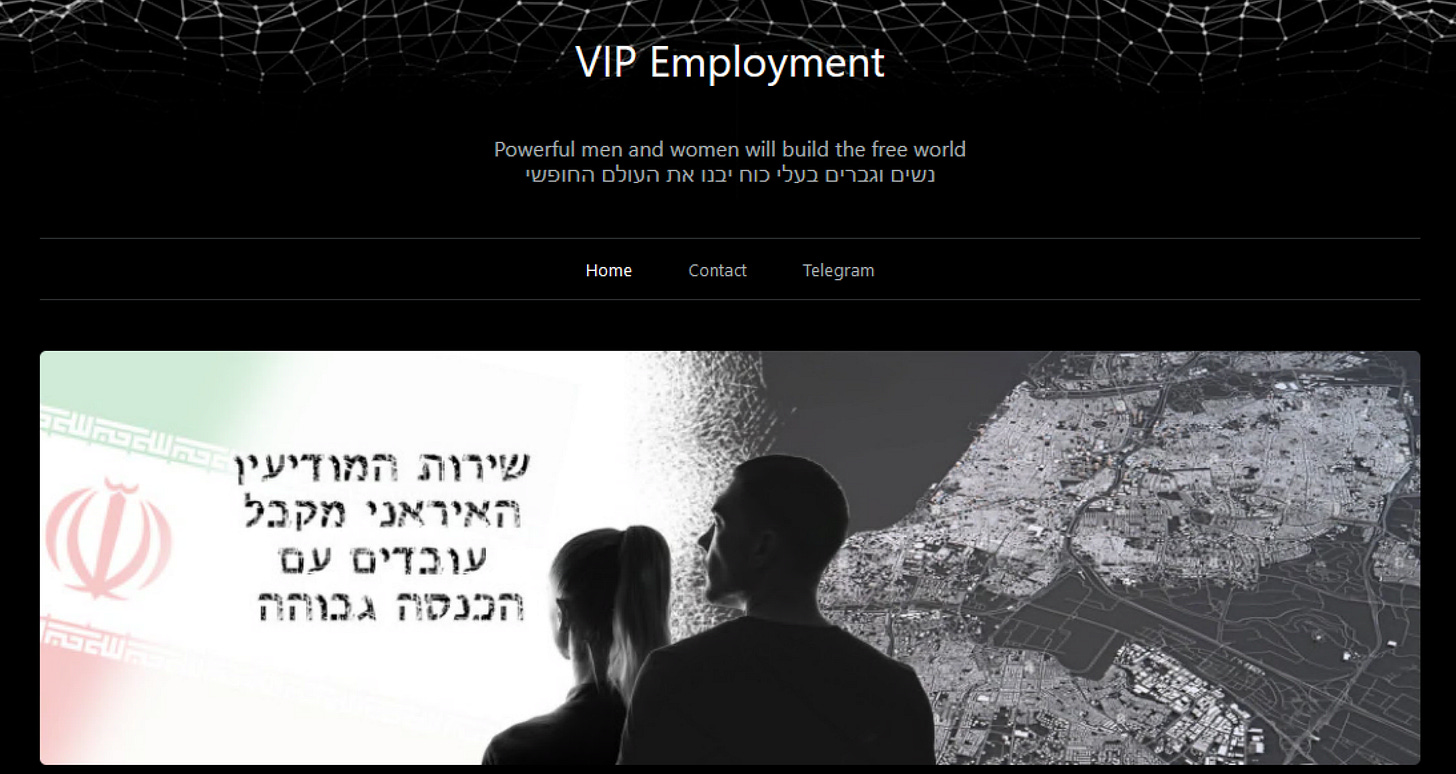
This operation, which became active in August of 2024 (as per what I’m seeing). The operation, overtly attempts to recruit Israelis for the “Iran Intelligence Service” on TikTok, Telegram and an Onion domain.
The TikTok account is barebones, featuring only one video with an abundance of spammy hashtags:
The video, which is a loop of a static image, loops through a map of Iran with some broken Hebrew printed, saying “The Iranian Intelligence Service receives partners for interesting and moving [emotionally, I assume they meant meaningful]… those received will be paid a very high salary.”
I purposefully translated the above text as literally as possible to convey the brokenness of the Hebrew. Below the image, we see a link to the TikTok account, a Telegram recruitment bot and an Onion domain. Let’s take a look at the Onion domain first.
The domain is barebones, and based on a few quick checks in Censys in other tools seems to have been built with operational security in mind, in contrast to past Iranian domains. The domain is straightforward - stating that the “Iranian Intelligence Service Receives Workers with High Income”, a funny misspelling in that it implies that those workers already have high income, not that they’d be offered it per se.
From the homepage, which plays up the ties to Iran with the flag, the domain provides links to a contact page and the Telegram bot.
The contact form is straightforward, explaining in Hebrew, Arabic and English (they don’t discriminate it seems) that they’re looking to recruit “the best ones” to “create a better world”.
The contact form itself jokingly has its fields filled out with the name of the former director of the Mossad.
So the site is barebones but to the point, and the Telegram bot seems to be the same, but is much more effective I’d imagine than an Onion site.
Searching Telemetryapp.io for the username of the bot retrieves over 100 results in past months:
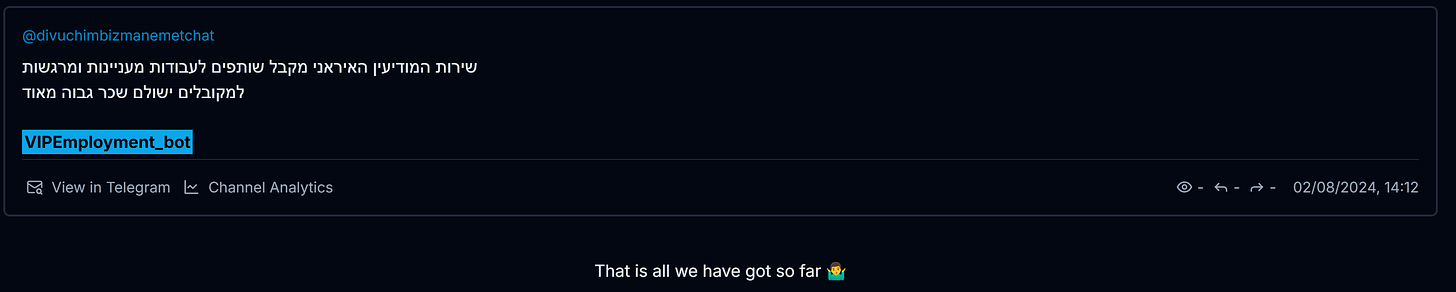
We see multiple posts with links to the bot, including many that are highly similar:
Most of the posts were posted by now deleted accounts, but some are still up.
The earliest message in Telemetry even overtly states the reference to the “Iranian Intelligence Service”:
Let’s look at one in-app from a highly suspicious account (not many Israelis named Stephanie):
The account is, of course, empty:
So, let’s review so far. We have an apparently Iranian recruitment operation active on Telegram, TikTok and an Onion domain, but Telegram seems to be the main focus.
This situation is reminiscent of a suspected Iranian counterintelligence operation that Mandiant exposed here. An inverse of the operation above, this operation utilized, at a larger scale, online accounts to recruit Iranians that expressed interest in working for the Israeli intelligence services to identify potential agents:
See an example of an HR company front below:
For those curious, there are some interesting points of overlap:
Use of the phrase “VIP” in both operations, as well as an emphasis on the “employment” phrasing, which is similar (though not enough for me to say that it’s conclusively the same phrasing)
Some other similar terminology, such as working for a “better world”
Now, this raises the main question: why would anyone be so overt in their recruitment operations?
Well, as a start - everyone is, just look at the below CIA video:
The reason why it makes sense to act overtly is simple - why not?
Not much to lose when targeting states with which you don’t have good relations, or any relations at all.
It also helps clear out some of the chaff - those who would be on the fence about being recruited, and gets right the point for those looking to work for the Iranians.
Perception hacking - just the act of doing this “messes” with Israel and if done right can make headlines, as well as provide extra busy-work for the Israeli government to take down this operation.
The operation could be a false flag, in which another nation-state tries to recruit agents under the guise of a different country, but this is low-probability.
Lastly, some observers may think that this could be a counterintelligence operation to find Israelis that are interested in working for Iran. I don’t think that this is the case (and hope that it isn’t) for a few reasons:
This would arguably be entrapment, and while I’m not a lawyer, it may be difficult to perform legally and ethically.
Similarity to past Iranian operations in style, platform choice and TTPs - there would be no need for this to appeal to the average citizen, who obviously doesn’t follow this sort of stuff closely.
This would be a precedent, as far as I’m aware, for Israeli operations, which have never worked in this way in the past and probably wouldn’t. It’s quite public facing, and arguably not necessary as well.
Let’s move on to our next topic, which this week will be Iran-focused as well. Iran International, an Iranian opposition-aligned outlet (take what they say with a grain of salt), has exposed a number of alleged Iranian cyber/influence operators, including apparently those involved in the famous hack and leak targeting Albania; see the below video:
We’ve seen a significant uptick in entities and accounts exposing alleged Iranian operators, which is an interesting phenomena in of itself. Wonder where they’re all getting their data!
The next item we’ll look at is the Justice Department and FBI’s statement on their recent international operation to delete Chinese malware:
This is a great example of technical disruption of hostile operations with high ROI and lasting impact, so good on the FBI, but even moreso, good on Sekoia, which apparently identified the self-delete capability required to carry out the operation.
This is a welcome change of pace compared to the usual naming and shaming we get in these statements, and I imagine that we’ll see more of this stuff going forward. If you’re interested in diving into this more, listen to the latest Three Buddy Problem episode discussing it here.
The final development to bring up is the recent Treasury announcement of sanctions on a Sichuan-based contractor allegedly affiliated with Salt Typhoon and a Shanghai-based operator responsible for the recent compromise of OFAC, available here.
This has received a ton of media attention, so I don’t want to go super in-depth, but I do want to provide some additional reading for those who want to read more:
For those who want to read more about Chengdu (the capital of Sichuan) and why it seems that almost every Chinese cyber contractor is based there, read Natto Thought’s article here.
The Washington Post checked out the company briefly, finding its total sum of initial capital and some other information, available here.
To me, the main question here is the turnaround time. The investigation and response to the OFAC hack occurred in what seems to me to be an almost unprecedented turnaround.
I’m not sure what this means re USG capabilities - are they capable of doing this most or even every time due to extant collection and sources?
Was this case fast-tracked? Why does it take so long in other cases but so fast here?
Anyway, I’ll leave you with those questions till next week’s post.