The People's Front of Han-dea
Welcome to Memetic Warfare. Let’s get right to it.
Handala is back in the news again after threatening an Israeli scientist, having allegedly left flowers and a letter in his car, claiming to have proved it with a picture and video from his residence which I won’t share here but seems convincing:
This in of itself is pretty impressive in that they were able to recruit an Israeli (or foreigner in Israel) to go successfully carry out this type of operation, which in the past has been less successful or carried out from afar, for example just sending flowers.
The announcement post online included an obviously AI-generated post waxing lyrical about the individual:
They also included some images of control panels that the guy apparently has access to, but those are easily faked.
This is the kind of thing that Iranian actors have done before, but is seemingly a more successful case than usual, having accessed the guy’s car and house and gotten an Israeli (if accurate, which it seems to be) to carry it out.
This is part of a broader push from Handala, similar to other Iranian actors like we covered here last week - ramping up doxxing and threats of violence.
Handala has adopted a new name and domain for its doxxing efforts - highly similar to previous name and typical Iranian tropes - truth, justice, resistance and so on.
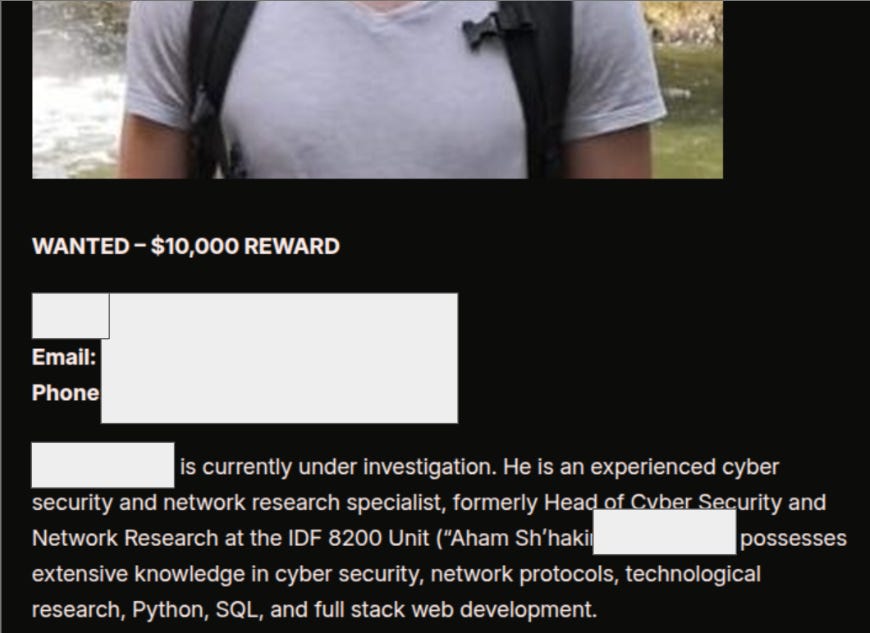
The website - what else - doxxes Israeli employees in defense and tech companies:
They really try to play up the camera attacks, making it appear that they’ve compromised all traffic cameras:
Handala offers a reward for anyone who targets the individuals - a super common Iranian trope as of late:
Based on the text, it seems that they just scrape and summarize data from their LinkedIn profiles, which makes the most sense.
This is part of a broader trend of Iran really ramping up its cyber-enabled IO as well as physical IO and espionage recruitment efforts, which makes sense also in the context of past APT 35 leaks which specifically mentioned this as a goal. I imagine that we’ll see further escalations and investment in this type of activity from other Iranian actors as they see that it’s effective and makes the news (this case, For Justice and many others).
We’ll conclude with a few other pieces of recommended reading. In other Iranian news, Domaintools has put out a detailed look at the recent APT 35 leaks - highly recommended and available here.
The last thing we’ll mention is the final, final look at APT 35 that we’ll have for a while, new KittenBusters leaks aside, is from Nariman Gharib, who published an in-depth review of the operators affiliated with the group itself, available here.