Alas, For Justice, We Hardly knew Thee
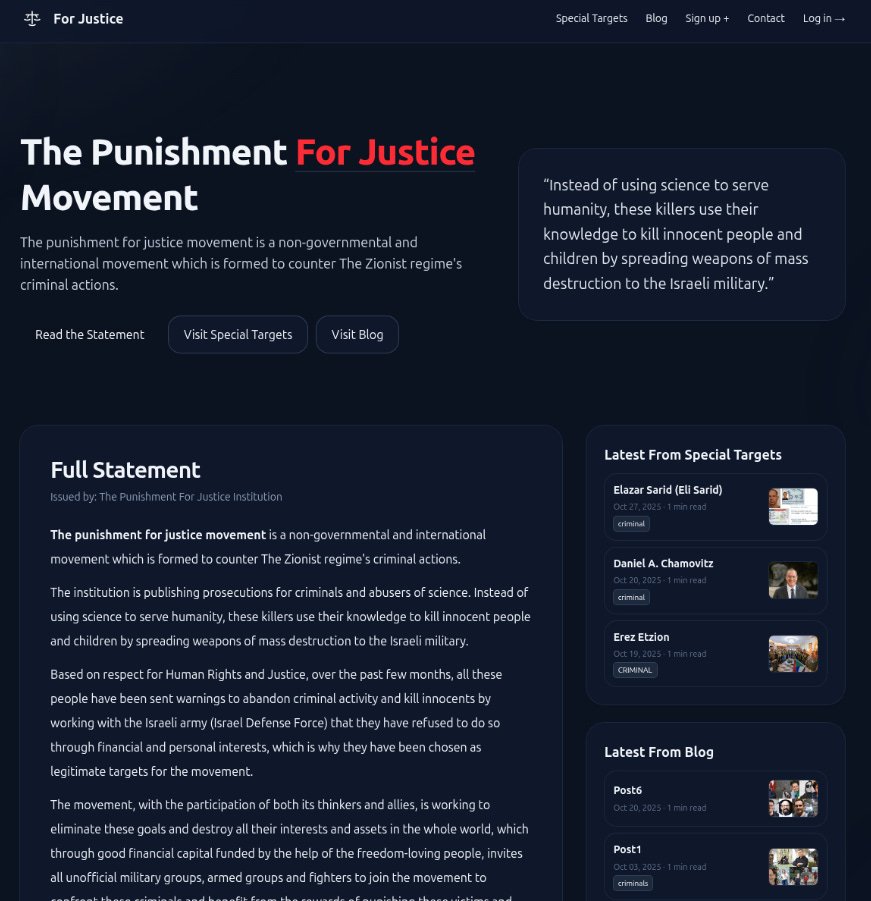
Welcome to Memetic Warfare. We’ll start off this week with a look at a new, almost certainly Iranian operation targeting Israeli academics. The operation features one domain, now since taken down, for the “Punishment for Justice" Movement”, a self-described “non-governmental and international movement which is formed to counter The Zionist regime’s criminal actions”.
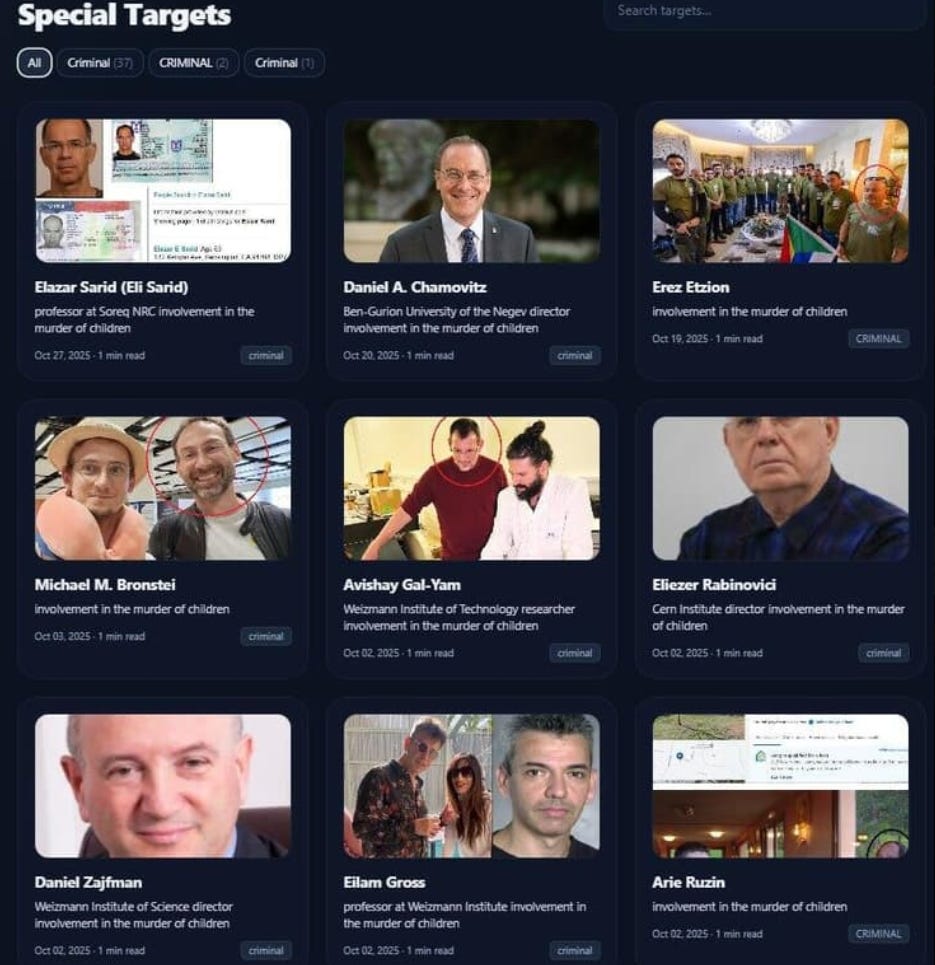
So far par for the course here for Iran, but what makes it interesting is that it’s not just a hack and leak or doxxing website, but rather doxxes Israeli academics (a new target set) and offers up to a hundred thousand dollars as a reward for targeting them.
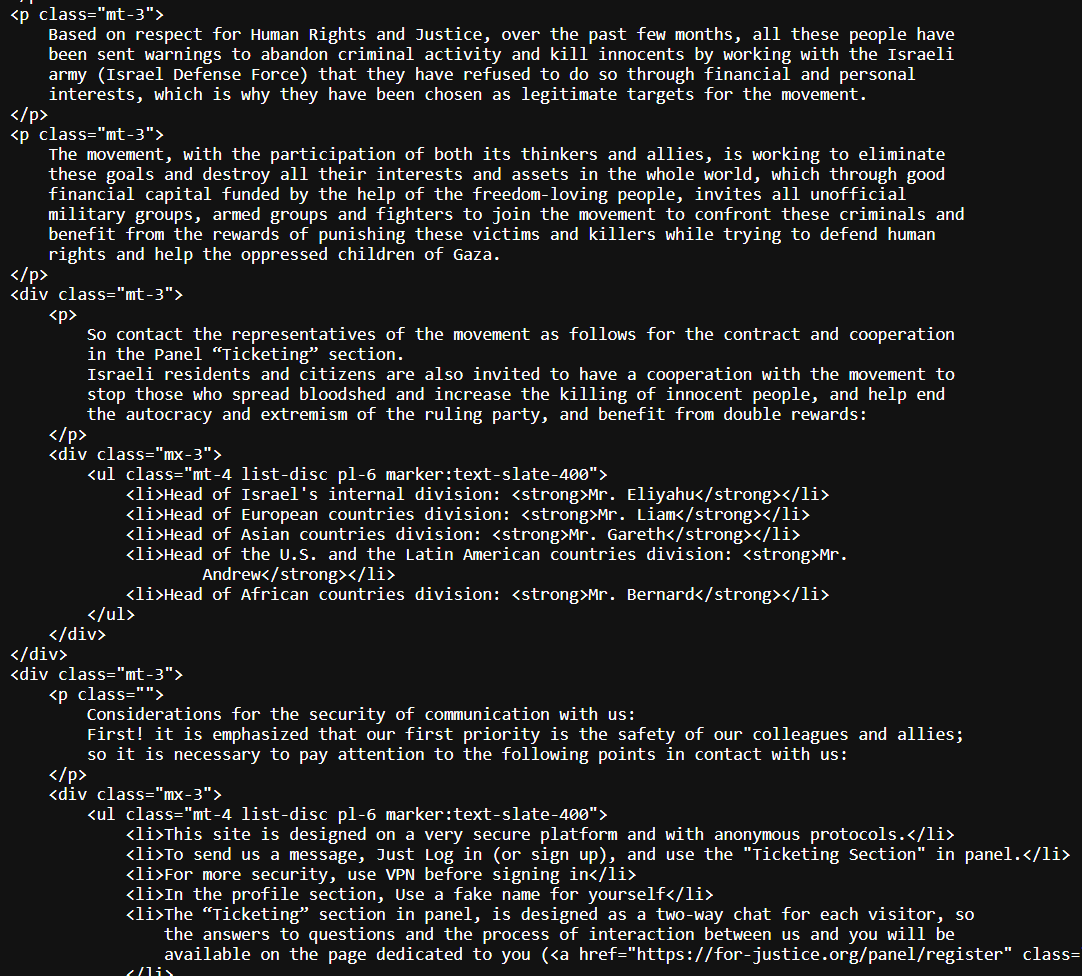
The domain uses typical Iranian style phrasing - emphasizing the “murder of children”, calls for justice and so on (think back to cyber court and mayn others).
This MO is super Iranian - think back to the US-oriented Enemy of the People domain and Iranian operations calling for attacks and offering monetary rewards for attacks against MeK members and Albanian politicians in Albania:
In contrast to other domains, this domain was taken down hours after it went up as it chose to go via Cloudflare, which acted fast. We can only rely on some past URLScans and other historical information, but there’s little forensic data to work with.
One of the few sources we have is URLScan, where luckily it was caught a few times. There we can find a “Contact” page:
What’s interesting here is that not only is this an intimidation effort against academics in typical Iranian fashion, but rather that the contact page alleges to have contacted the people listed and that they refused to stop their alleged work with the Israeli government/military.
I am of course highly skeptical of this, but it’s an interesting note and shows how they attempt to make this more legitimate in the eyes of those who aren’t quite as extreme as they are. Interestingly enough as well the domain actively tries to appeal to Israelis to carry out attacks.
From there, there’s a “ticketing” page to contact the organizers, which are listed as having been split up into regions - Israel, North America and otherwise. From there, and once having connected with a VPN and fake name as they say, they will begin the process and presumably reward individuals that carry out attacks.
While this is almost certainly mainly an intimidation attempt (and a successful one as it has made major headlines in Israel and some outside of it), there’s always an element of possible recruitment for other activity here beyond just carrying out an assassination.
It’s hard to say which actor is behind this, though I’m truly just guessing here due to the lack of further technical information. This seems to me to be more like Homeland Justice/Nemesis Kitten or whatever one wants to call them, but could potentially be ASA as well. Hopefully we’ll get more information from other providers with telemetry sometime.
From there we’ll move on to other Iranian hijinks. AWS’ Security team published a look at Iranian operations that bridge the gap between cyber and kinetic warfare. They spoke about this at Cyberwarcon as well so hopefully we’ll get a YouTube video sometime.
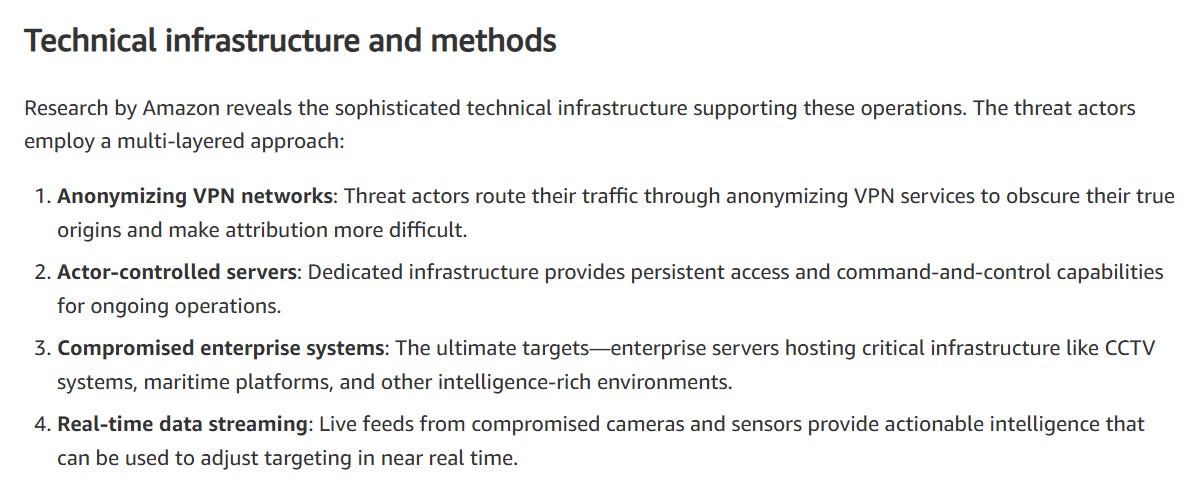
What’s interesting here is the use of cyber warfare to support kinetic operations - Amazon of course came up with a phrase here - “cyber-enabled kinetic targeting”, which is exactly what it sounds like.
The first usecase shows how Iranian actors compromised a ship’s AIS and even cameras to try to aid a Houthi missile strike against that ship:
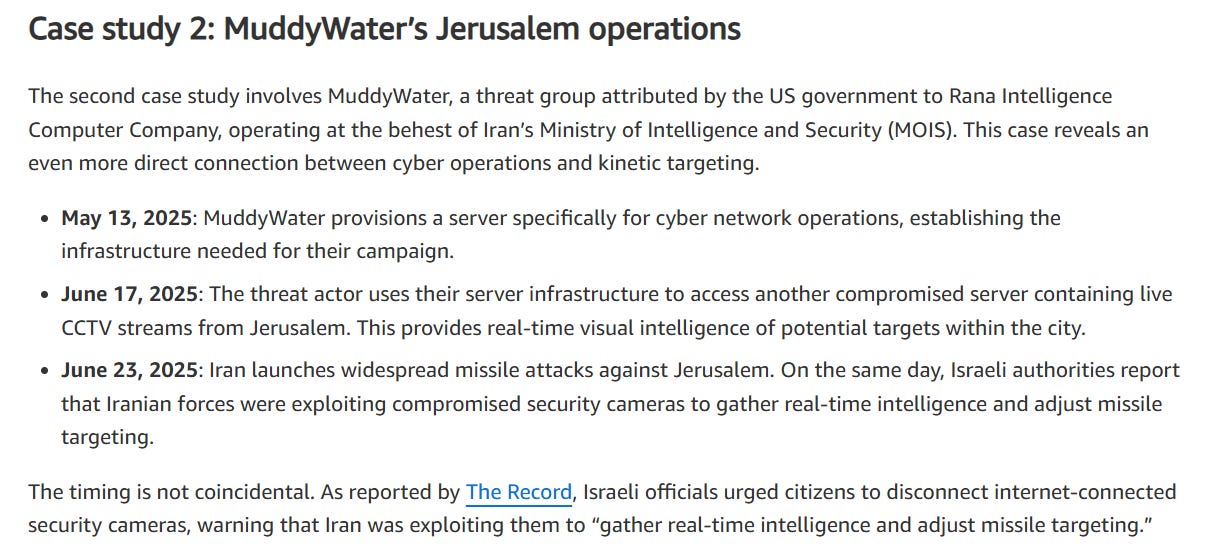
The second is MuddyWater’s operations targeting Israel during the last war. In this case, they targeted a server that had livestreams from CCTV cameras running on it to provide “visual intelligence” in real-time for later targeting via missiles:
The interesting section here IMO isn’t just running servers or anonymizing VPN networks, but rather hitting cameras.
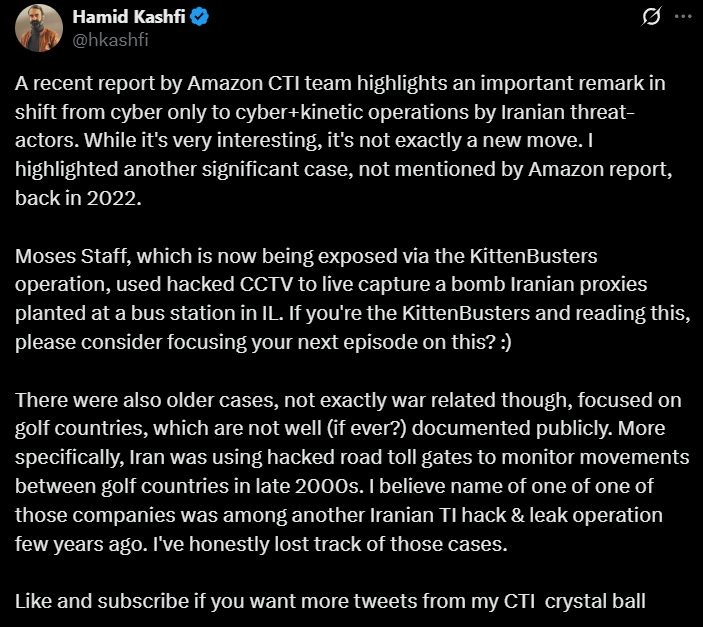
While useful for targeting, compromising cameras and sensors can also be used for IO purposes - to provide visuals of the strike itself, for example. Hamid Kashfi brought this up on Twitter recently, stating that in one case Moses Staff (a different Iranian hacktivist front) used hacked CCTV cameras to film a bomb being planted by a recruited asset at a bus station in Israel, presumably for IO purposes and later distribution (in my opinion):
This is the real interesting part. Controlling sensors isn’t critical for Iran (and other actors in this space) not just for battle damage assessment or to aid in targeting but rather for IO purposes.
Iran has to show that its expensive missile arsenal is scary and intimidating to both domestic audiences as well as foreign, and their efforts in the past war showed this. The same dynamic applies as well to the recruitment and activation of recruited assets in Israel for sabotage - the true impact isn’t the explosion itself, but rather the psychological impact on Israeli society of having been targeted and exploited.