The Inner Machinations of a Threat Actor are an Enigma
Welcome to Memetic Warfare.
We’ll start this week with a look at yet another Github leak of a threat ator.
APT 35 apparently was popped and had their internal data posted on where else but Github, available here. This is the same way that i-Soon was exposed, and we’re lucky to get a deep look into how a threat actor works. For more analysis of their activity, check out Hamid Kashfi’s analysis here and Gemini analysis of the leaks themselves.
The group, which named itself “Department 50”, focuses on counterintelligence and is under the IRGC. Note the logos and iconography:
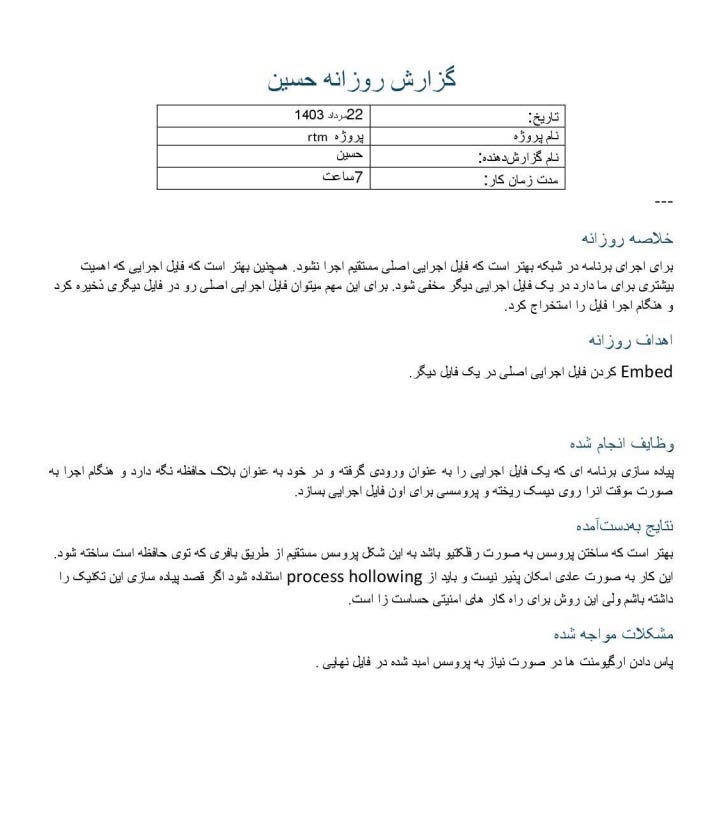
We get a look at the humdrum elements of being a threat actor, including daily work reporting:
We also can see how they use OSINT and other methods for reconaissance:
One of the more interesting documents was a 50-page document on exploiting Ivanti with common CVEs:
The documents also include looks at workflows, including how to exploit the recent SharePoint vulnerability - the kind of thing that you’d expect, but still quite useful. Interesting to see that they use Shodan, Censys, LeakIX and other tools instead of developing in-house (why not, I guess).
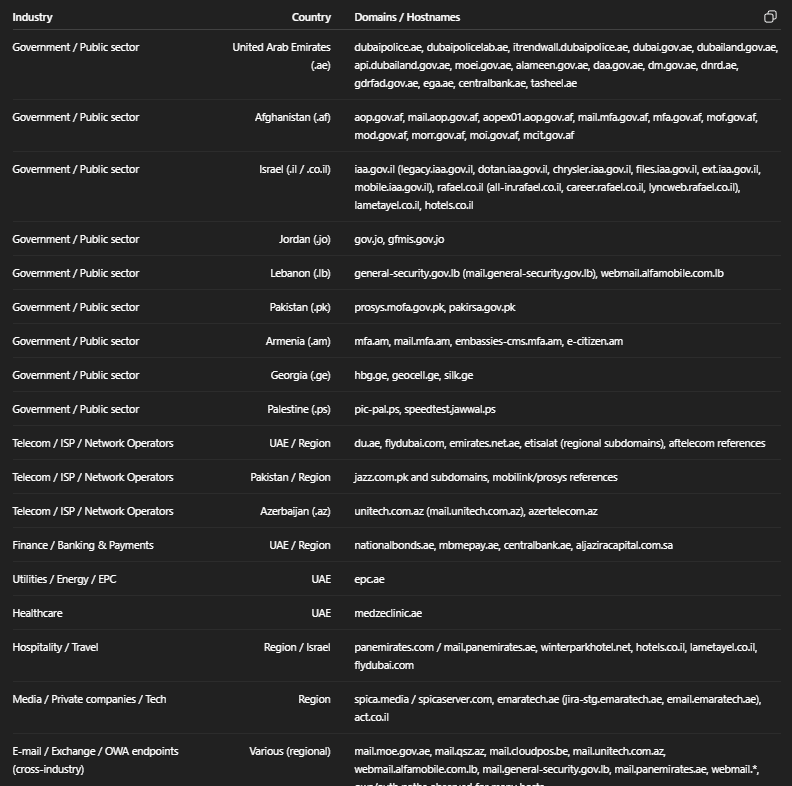
Beyond workflows and TTPs, we also get a look at targeting, including of course countries such as Kuwait, Lebanon, Turkey and Saudi Arabia, but also interestingly enough South Korea:
Insomuch as this group focuses on counterintelligence and threats to the regime, we also see which sites in Iran (and the UAE) they have webshells running on for access:
Chapter 2 of these was uploaded the other day, and I ran some of the new logs through ChatGPT to find more information on targeting:
We also get a look at their OSINT reporting, including their look at Raheel Raza, a prominent Pakistani progressive Islam activist known for her pro-Israel stance. On the whole this is pretty basic and really only includes public identifiers, which is interesting to me in that I’d have expected some more information from surveillance, leaks or so on.
In chapter 2 we also get a look at a monthly progress report:
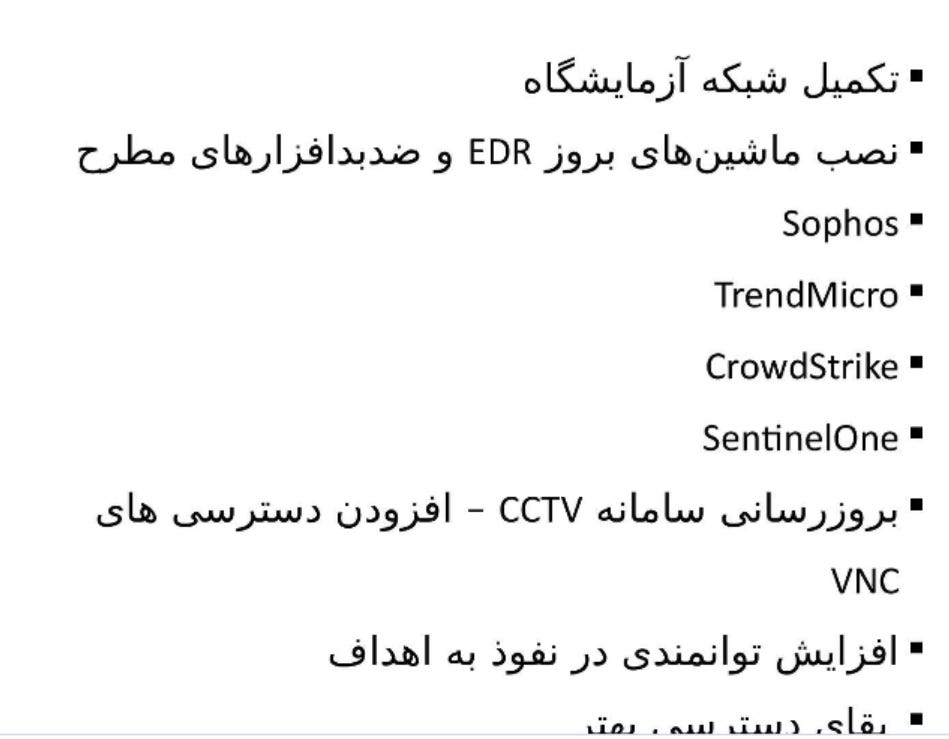
They’ve been looking at SentinelOne, Sophos and TrendMicro EDR - hope that they’re looking into this.
We also see that they’ve compromised a legal data platform.
Other companies targeted here include law firms, financial services firms and others.
Multiple EDRs are mentioned, most notably with the point after CCTV referring to the need to be able to better “influence” targets, meaning they’re working to enhance cyber-enabled IO.
One of the most interesting sections was a part on how they run an online, social media-centric campaign for what’s probably malvertising or phishing (or maybe IO, who knows).
We get a ton of interesting data, including mainly how they view the use of black hat services. The operators found that blackhat services for advertising on social media platforms were too expensive, so they decided to do it themselves. Notably, they had issues creating accounts, so they decided to purchase accounts from Accsmarket.
They purchased aged accounts and connected them to residential proxies from IPRoyal, connecting them then to Android emulators.
We also get a look as to how they developed these accounts further - following some a day and so on, and then also launching their own website as part of the operation.
It’s rare to get a look at the internal methods used, but it’s great to get firsthand confirmation that yes, creating accounts is hard for threat actors and it’s often easier to just buy them.
There’s a lot more in the leaks, so if you’re interested, take a look and download them.
Another interesting event occurred regarding Pakistan-Israel relations and IO. Readers may recall the group Lashkar alTharallah previously covered on Memetic Warfare, which may be Iranian or potentially just Pakistani:
This group is seemingly still active, and claims to have even killed Imtiaz Mir, a Pakistani journalist who was pro normalization with Israel.
This is, of course, unfortunate for Mr. Mir and my condolences to him. As far as IO and physical influence goes, this is a watershed case of a seeming assassination carried out in Pakistan by a group that claims itself to be Pakistani but may well be Iranian.
It wouldn’t be a huge shock - we saw above that Iranian actors are tracking pro-Israel Pakistanis such as Raheel Raza, and who knows - due to the rumors of the looming normalization, Iranian actors may feel the need to take stronger action to prevent it.
Or, of course, it could just be Pakistanis, or even Pakistanis supported by Iran. Perhaps we’ll know more soon.
That’s it for this week. Thanks for reading and please leave any complaints or comments below.