Singapore Slings Attribution
Welcome to Memetic Warfare.
It’s been a big few months for Iran coverage, so it’s time to move on. The first event that I want to discuss is Singapore’s recent public attribution of Chinese cyber activity. RUSI published a look at it here.
For those who hadn’t heard of it, Singapore recently decided to break with tradition of attribution-without-attribution, meaning they’d publish information and attribute a cluster of cyber activity, but not say who did it. This time, they named UNC3886,a Chinese APT as described by Mandiant, as being behind intrusions into critical infrastructure.
While Singapore did not attribute UNC3886 to China itself, only naming the UNC, this is as close as we can get to Singapore outwardly calling China out.
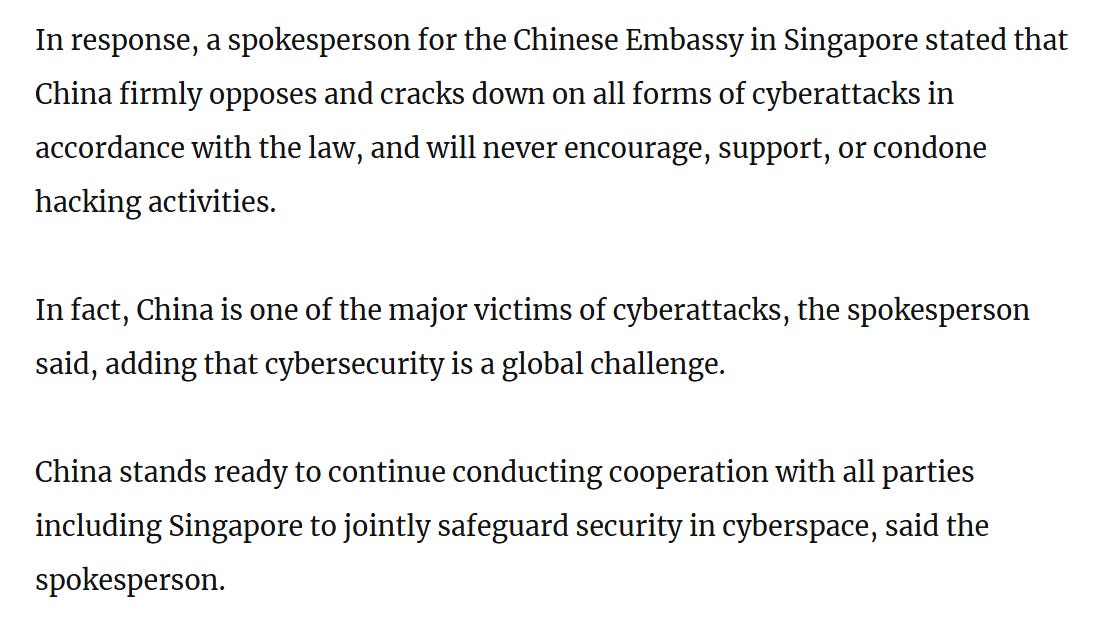
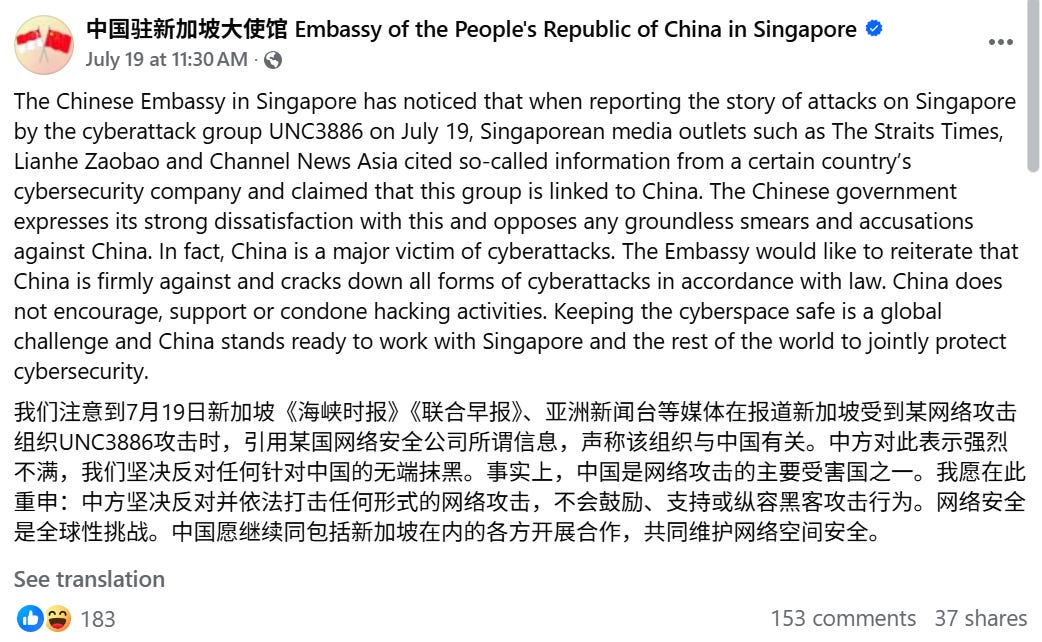
The Chinese embassy in Singapore immediately denied the claims and offered to help Singapore “jointly safeguard security in cyberspace”.
I bring this up because we tend to focus on these topics in a Western context and ignore what’s happening in equally important areas, such as SE Asia. Singaporean takedowns of hostile IO and cyber activity have been ramping up recently as per public statements, even if they aren’t overflowing with information.
This may lead to the targeting of Singapore by Chinese and pro-China actors, some of which I’ve noticed are already subverting blame online to the US. China is incredibly sensitive to this and has no problem putting out reports, as we’ve covered here many times.
Singapore has, with the exception of the occasional mention, so far escaped the wrath of the CVERC and other Chinese outlets that use cyber attribution for their own strategic communication campaigns. Following this attribution, though, I wouldn’t be surprised to see a CVERC or other MSS/MPS attribution of alleged American or other hostile activity targeting Singapore.
The paragraph that you read above was what I wrote just days prior to the publication of this post, and for better or for worse it seems that I was partially right.
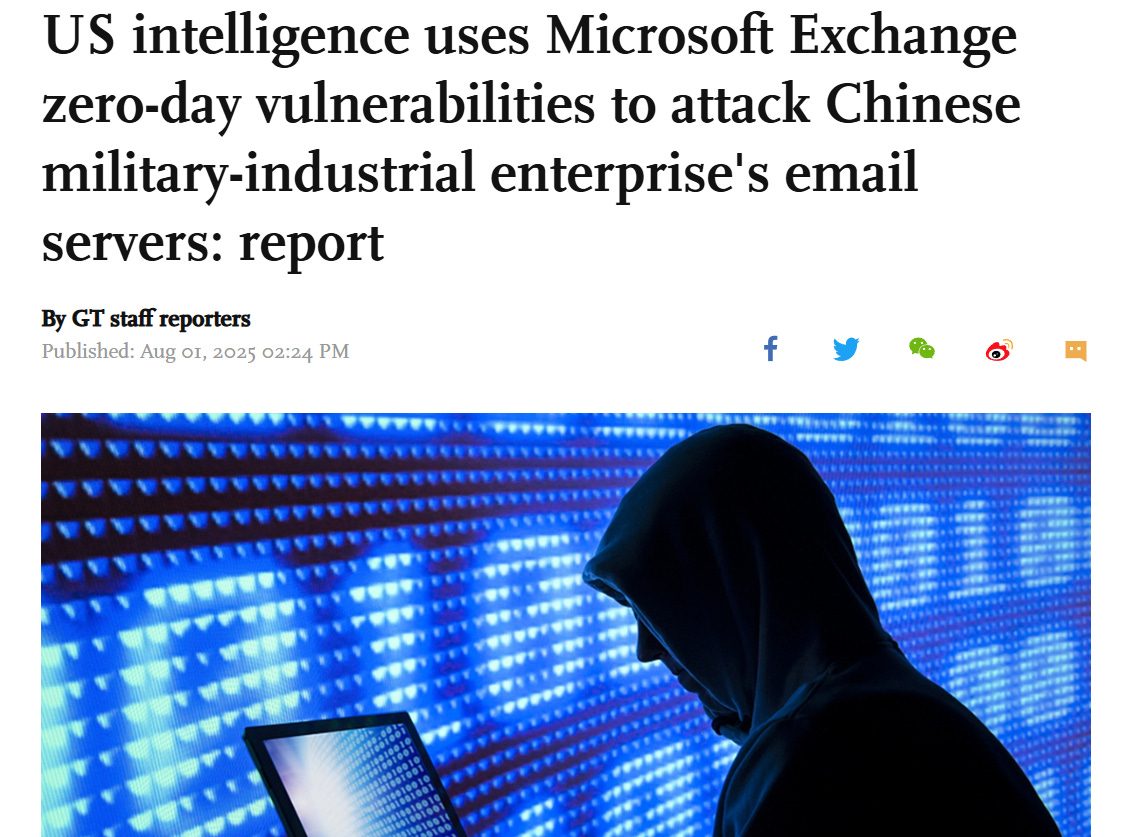
In the interim between my original draft and the publication of this post, the Global Times, a Chinese state media outlet that is often the first to cover Chinese cyber attribution, published on August 1st coverage of a report from the Cybersecurity Association of China:
The report claimed that “US intelligence agencies exploited zero-day vulnerabilities in the Microsoft Exchange email system to attack… a major Chinese military-industrial enterprise”.
Furthermore, the report calls out a number of countries as having hosted “proxy IPs” (not the phrasing I’d use), including Singapore.
Singapore got off here comparatively lightly; Chinese actors could have chosen to escalate in response to Singaporean attribution. Instead, China seems to have chosen to downplay Singapore’s attribution and instead focus on the other China-centric cyber scandal of the day: the exploitation of a Sharepoint vulnerability by Chinese APTs:
China’s report here then makes sense: deflecting the blame for the thing that China is accused of doing to the US.
What’s interesting to me here is the turnaround. China responded rapidly to the Sharepoint situation, getting a report out in about a week. In past cases such as Volt Typhoon (responded to by the CVERC) and Salt Typhoon (responded to by the China Cybersecurity Industry Alliance), Chinese reports from these various potemkin organizations have taken weeks if not months to get out.
The trend has also crystallized it seems into a standard behavior. Country X attributes Chinese cyber activity, China then puts out a report from some new front organization to trot out blaming the US for the same activity.
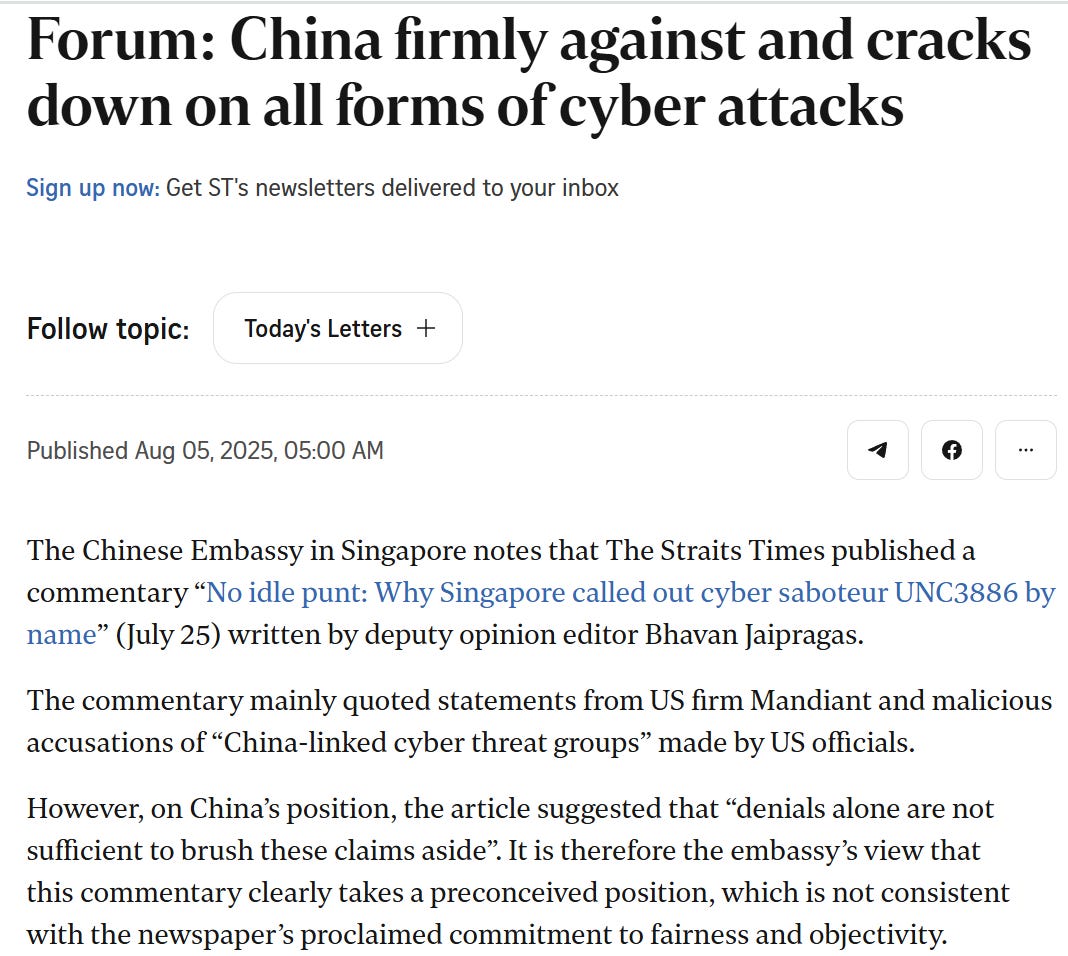
Again, as this story is apparently still developing, it turns out to not have ended here. The Chinese embassy published an op-ed in the Straits Times, a leading newspaper in Singapore, in which it criticized the Straits Times itself for publishing its own op-ed on the attribution
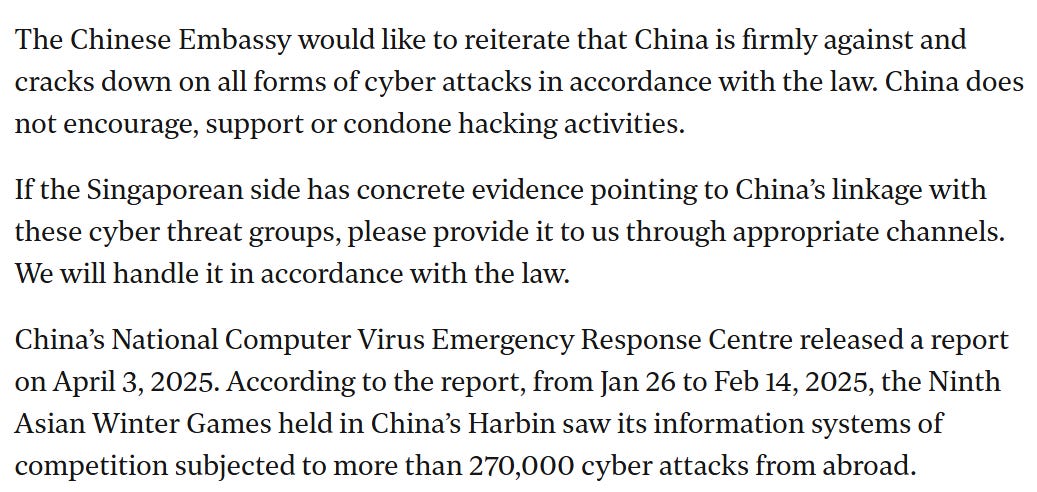
The article, written by a political secretary in the Chinese embassy in Singapore, refers to previous CVERC reporting that also mentioned Singapore:
The embassy posted about it on Facebook also. A brief glance at the comment and share section surfaces many suspect accounts, which isn’t surprising.
The embassy has uploaded apparently at least 4 posts about this recently, showing that it seems to have truly struck a nerve.
It’ll be interesting to see how this story develops and if we see a dedicated CVERC report on Singapore in the near ish future.
Moving on from Singapore, Doublethink labs posted a look at a small network targeting the DPP in Taiwan. I wouldn’t normally bring this up, but it showcases some cool things:
Threads networks
Use of tracking IDs
Solid visualizat with no frills
Password resets
Overall, just a concise, well-done investigation.
That’s it for this week! As always, check out Telemetryapp.io, and leave any thoughts, complaints or jokes in the comments.