Memetic Warfare Weekly: Qin Shi Hack-Di
We Hold These Tweets to be Self-Evident
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also do training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
Let’s start off with various elements of Chinese cyber activity. The first thing we’ll discuss is Bushido Token’s excellent blog post covering numerous other elements of i-Soon activity, available here. I’m of course very grateful for the Memetic Warfare Weekly shoutout as well! Will contributes often to the community and I’d highly recommend following him on Twitter.
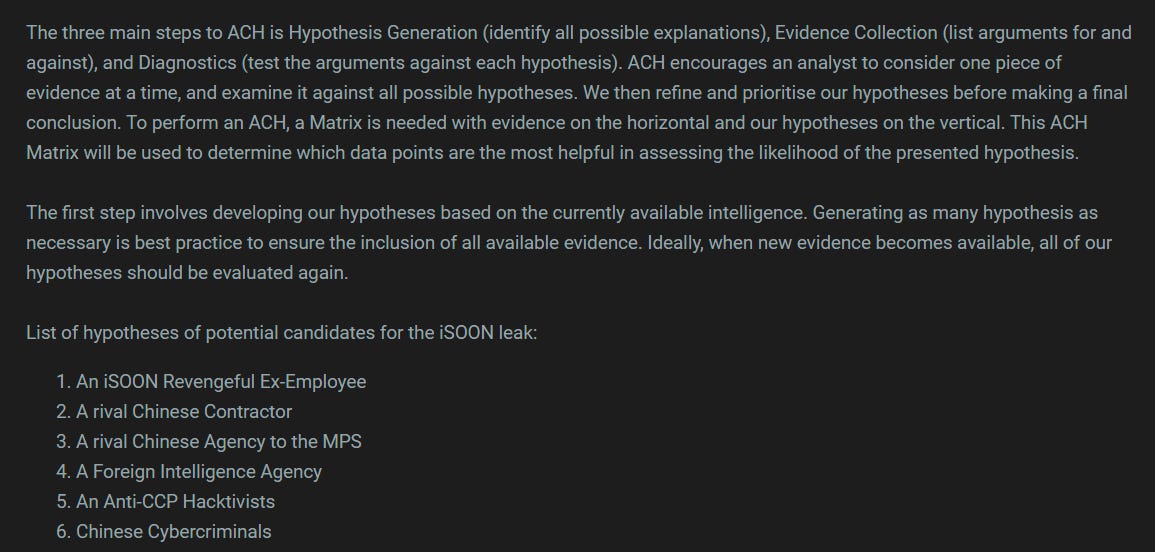
In his latest post he uses a structured analytical technique, something that I don’t discuss often on this blog. He chooses to use the ACH technique, or the Analysis of Competing Hypotheses - see below.
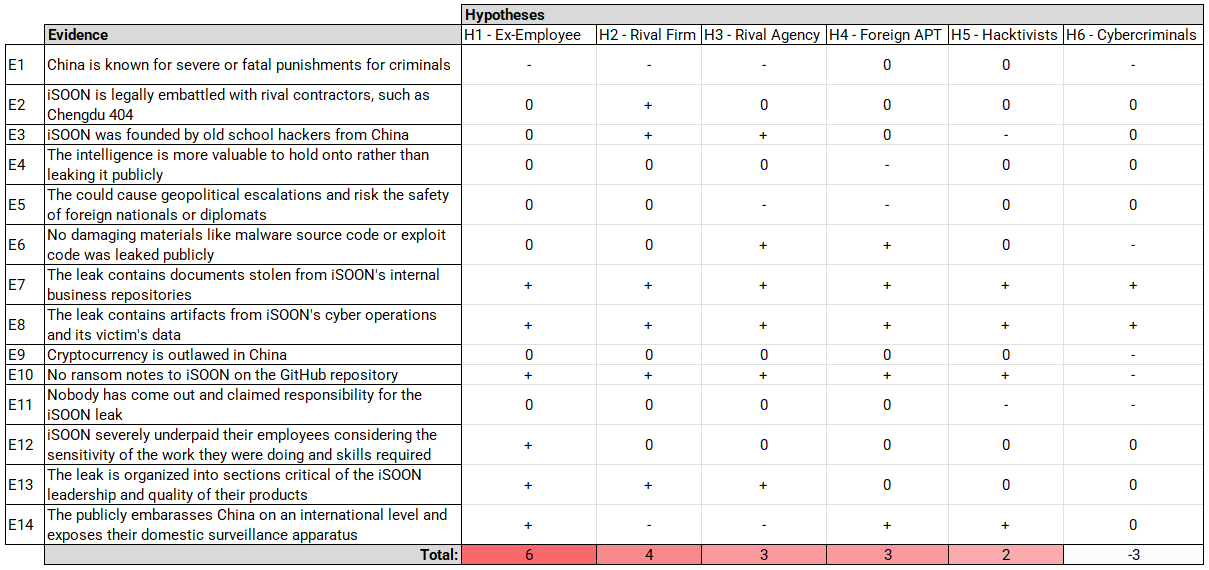
He comes up with a few of the potential perpetrators of the given leak as shown above, and then creates a matrix of arguments for and against the chance of them carrying out the operation:
He then reaches the conclusion that a disgruntled employee/insider threat is the most likely actor responsible for the leak while entertaining other options:
This is a fantastic and accessible use of ACH, but I will say that I’m not so sure that I agree with the finding that a foreign agency isn’t necessarily behind the leak. I do believe that the two most likely options are an insider threat or a foreign intelligence agency, and that it’s arguably probable that a foreign intelligence agency may even be the most likely perpetrator.
It’s quite possible that a foreign agency in fact extracted and exploited much more data than what we have available in the leak. Anything that would have been truly escalatory or exposed sources and methods could have been held back, and only comparatively insensitive or otherwise specific content could have been posted to:
Make the firm and the Chinese government look bad and incompetent
Out the victims and activity to name-and-shame Chinese actors and make the victims take some sort of retaliatory action
Disrupt ongoing operations and deter Chinese firms from taking government contracts
Lastly, groups such as Intrusion Truth, KasperLeaks and others (as discussed on this blog) may be authentic hacktivist groups, or may in fact be hacktivist front groups for government agencies to carry out their own hack-and-leak operations.
This leak could very feasibly be one of those, but one of the main differences in MO is that there was no accompanying social media amplification. This also is a lower-risk method as well, as the more activity - the higher chance one has of being exposed.
There may be evidence that I’m missing here, and I absolutely agree that a disgruntled employee is one of the top two probabilities, but I wouldn’t discount a foreign agency quite yet.
Qin Shi Hack-Di
Dakota Cary of Sentinel One published a great look at China’s domestic CTI industry and its role in Chinese influence operations.
Long-time readers of the blog know that this is a topic especially close to my heart and one that I find particularly interesting (and have published a few posts on), so let’s take a look at the report and discuss the key findings.
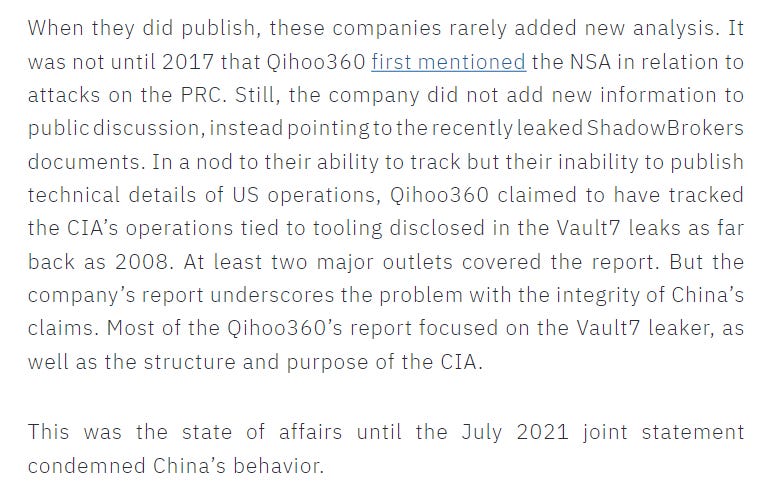
The key finding of the report is straightforward and one that I wholeheartedly agree with: China uses its domestic CTI industry to, clumsily, attempt to shift blame to the US for hacking activity by utilizing the industry-standard threat report format.
These reports are published in a haphazard fashion and with little to no evidence of import. The reports are also often heavily amplified by state media and online networks.
Cary provides much more historical background that I can be bothered to provide, so read below for greater context:
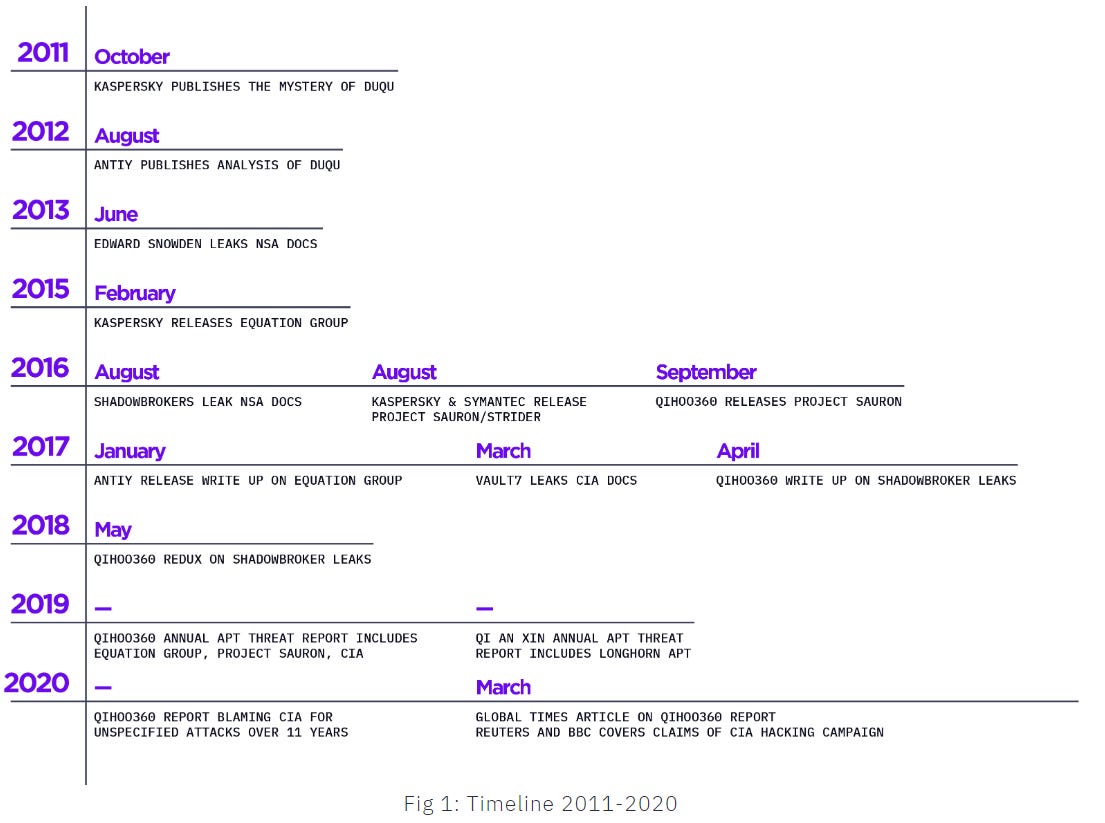
Cary also takes the time to produce an excellent timeline showing Chinese CTI activity in historical context, including providing relevant context from Kasperksy and Russian activity for a broader picture.
I’ve mostly looked at Qihoo related activity in the past, but this report rightfully looks at activity from two other Chinese firms: Qi An Xin and Antiy, which work in conjunction with various Chinese government agencies.
Interestingly and in my opinion rather astutely, Cary points out the probable inflection point in how China uses CTI reporting to the joint US-EU-UK statement condemning irresponsible Chinese cyber activity and espionage:
From this point on, there’s a rapid increase in Chinese CTI reporting and meteoric growth in Chinese state media mentions of CTI and hacking campaigns:
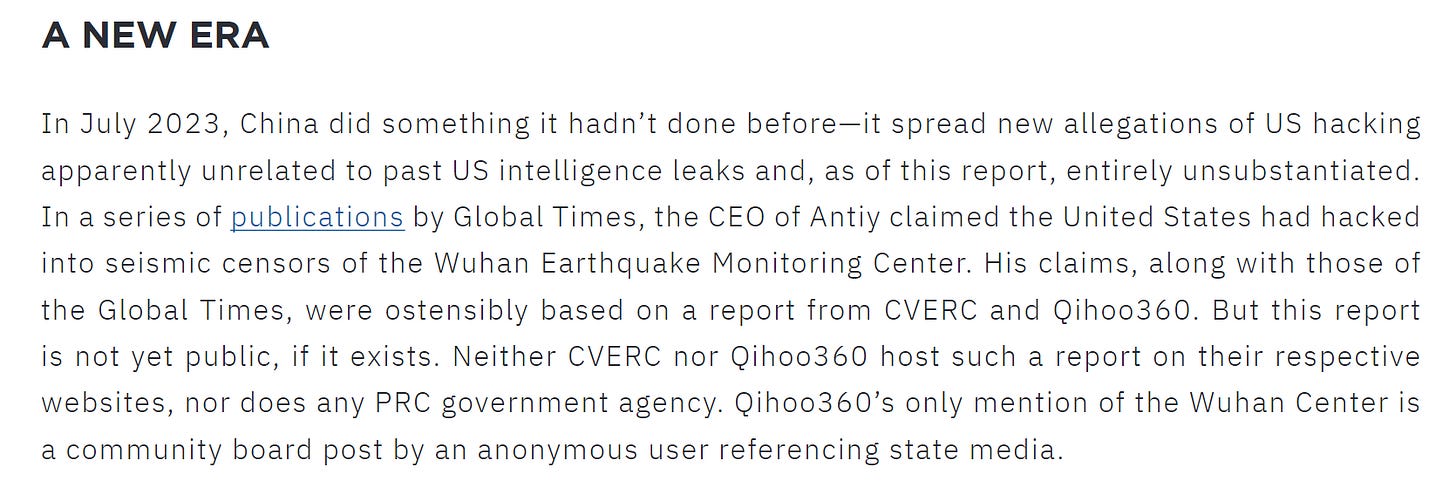
Following the CVERC and Qihoo report on the supposed NSA hack of China’s Northwestern Polytechnical University (which Cary also points out is the first time that a specific Chinese victim is pointed out, describing the propaganda implications of such exposure), the authors also threatened to apparently doxx the supposed US operators involved:
Things are continuing to ramp up as Chinese CTI firms refer more and more to American/Western APT activity in their reporting, more often than not with quite literally no evidence. The landmark “Review of Cyberattacks from US Intelligence Agencies” by the funnily-named China-CIA (Cybersecurity Industry Alliance),
Definitely going to have to add this one to my reading list. The level of quality continues to reach new nadirs, with the below case of the alleged hack of the Wuhan Earthquake Monitoring Center, allegedly done by the US and based on a report from CVERC, either does not exist or isn’t public as per Cary. I remember vividly looking for this one myself only to be disappointed that it isn’t out there wildin’.
The main conclusion though, and what will be interesting to follow going forward, is beyond the realm of just Chinese state media. The use of CTI for external propaganda and IO now aligns with China’s Ministry of State Security’s influence goals, which has posted in the past regarding not only traditional espionage matters, but also alleged American hacking operations:
All in all - a truly excellent report covering one of the least-discussed elements of Chinese influence, hybrid warfare and cyber operations.
That’s not all we have this week for Chinese cyber-research. Spycloud’s Ashley Alloca and Kyla Cardona have come out with some interesting research on the Chinese cybercrime underground on Telegram, available here. There are some useful TTPs and keywords for those who’d like to investigate themselves:
Check out these keywords on Telemetry:
There’s no doubt that Telegram is arguably the leading source for any data breach or other investigation, and it’s great to see more research done on Chinese cybercrime use of Telegram.
We Hold These Tweets to be Self-Evident
Twitter user FluteMagician posted a great thread on #Texit, the political movement calling for the secession of Texas from the union. The thread is available here and highly recommended to be read in its entirety.
The thread points out all of the possible errors one could make in running this sort of operation. Beginning with linguistic analysis, including grammatical and even spelling errors in some cases that abound:
The use of indicative keywords - everyone knows that a red-blooded Aggie takes deep pride in Texas’ array of warm-water ports.
May have some AI-generated garbled imagery:
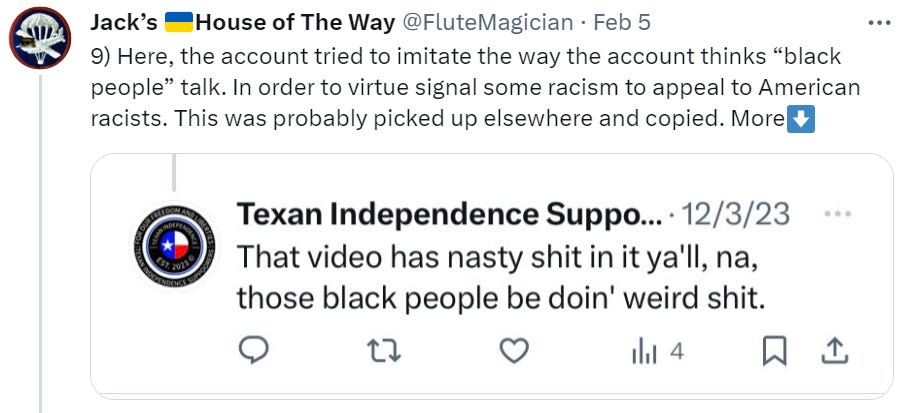
We even have an attempt to imitate black people:
Those interested in the history of the use of/targeting of black Americans can read an article on the topic published by friend of the blog Eugene Kondratov, available here.
My Report Queue Doth Runneth Over:
There have been too many reports on IO in the past few weeks for me to cover each of them in-depth as I’d normally do, so I’ll do the cop-out and provide a list below of most of them. I’ll cover the ones that have some sort of added value in posts in the coming weeks, for example the recent Viginum report to be covered in next week’s post.
In the meantime, check out a list of some of the reporting below:
“Paperwall” - Chinese operation utilizing newswire services as published by Citizen Lab.
Not a bad report by any means but also not a lot of new or cutting-edge insights, still absolutely worth reading and includes attribution to a Chinese PR firm, so that’s always a plus.
“Intercontinental Lies” - an investigation by The Insider on Russian influence operations on Telegram targeting various African nations. The primacy of Telegram here is definitely the wave of the future and we’ve of course added these channels to Telemetryapp.io:
Let’s now move on to Iran and its activity in the broader context of the Israel-Hamas war:
Microsoft has been coming out strong with a two reports and an accompanying podcast for the unlettered on Iranian cyber and IO activity targeting Israel and beyond.
Google also has their own in-depth report, focusing more on cyber activity, available here.
That’s it for this week!
















Oooooh we love telemetry! Another great read Ari.