Memetic Warfare 4: A New Meme
Welcome to Memetic Warfare 4! I’m happy to have you here. My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the counter-influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I also provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or contact@glowstickintel.com.
Frankly, I’ve been surprised by the amount of interesting IO/cyber related activity in the past month. If you have any questions, comments or requests, I look forward to hearing from you - I’m always available on LinkedIn or via ari@glowstickintel.com.
This week we’ll review the interesting developments of the past week with my own opinions about them foisted upon you as the captive reader, but we’ll also go over a short discussion of the importance of double-checking queries and understanding online infrastructure. Let’s start with the true north, strong and free: Canada.
The Globe and Mail in: Not Without My Leaked CSIS Documents
The ongoing saga of Chinese election interference in Canada, exposed by the Globe and Mail, took a sharp turn the other day. The national security official who provided classified CSIS reports on Chinese interference published an op-ed describing why s/he chose to leak this information. This is a fairly unusual act to be taken by a national security official, and criticism of the decision has already begun to circulate on Canadian national security Twitter.
The main issue at hand appears to be a lack of political will among Canadian elected officials to take concrete action against the formerly nascent and now active Chinese threat to Canadian elections. Trudeau recently appointed a special investigator to look into these claims as part of a wider investigation into Chinese interference and potentially lead to public hearings and commissions.
Oh How the Turntables….
Hold back thy tears: Prigozhin’s business “empire” has been hacked. Kevin Rothrock of Meduza posted a great Twitter thread on a hack and leak attack carried out against Prigozhin’s various entities. The leak exposed internal financial documents, IT information and more, including a fair amount on disinformation/IO activity. The first finding that should come as surprise to no one is that a number of Twitter accounts directly receive funding from Prigozhin as per the leak, shown below:
Fear not: Prigozhin is also, as we all know, active on Telegram as well:
The above accounts and channels are a great place to start (anonymously and securely) if you’re into this weird hobby that we all seem to have. If you’re interested in reading more (and you should be), I’ve linked to Olga Lautman’s Substack below.
Avatar: The Way of the Neural Network
Cyber Detective - one of the best OSINT Twitter/Discord/Substack accounts out there recently dove into one of the more difficult elements of avatar creation: developing accounts further beyond 1-2 initial pictures. The below Twitter thread shows an early attempt at the use of AI tools to do so.
The implications for IO, as well as espionage in general, are immediately apparent. Avatar development, or “gardening” as some call it, is one of the biggest challenges in terms of time investment for developing deeper avatars, and the ability to do so effectively with automation and AI tools. Past attempts to make AI-generated images harder to detect with further editing, done by the US government on some online assets, have been reported on by the Stanford Internet Observatory.
Every Framework Everywhere All At Once
I posted last week on LinkedIn about my take on the publication of a new framework for analysis of online operations from Ben Nimmo and Eric Hutchins of Meta. This framework seeks to unify analysis and investigation of both cyberoperations and information operations online, a goal that I wholeheartedly agree with as the right direction. I’m not one to wax poetic about frameworks and theory, but take a look at it if you’re interested in seeing where the industry is going.
AI-nchor(wo)man
Mothership, my favorite source for tongue-in-cheek Singapore content, recently published a humorous look at the first use of an AI anchor for news broadcasts by the People’s Daily, one of the leading official newspapers of the CCP. How could this possibly not be effective?
The use of an AI anchor for covert purposes by utilizing commercial software has been covered by numerous news outlets and further needlessly extrapolated upon in this very blog (so please read our previous issues!).
Near, far, wherever you are (source: above article from Mothership)
While certainly an interesting development, the Mothership article and yours truly are certainly not yet entirely impressed. The anchor herself is meant to be interactive with the end-user, but is currently only really accessible via the People’s Daily app, and isn’t even Chinese state media’s first attempt at using AI-powered and generated anchors.
This attempt is certainly early but there’s no question that the industry is heading towards this direction. Full-spectrum automation of every stage of content creation (including of course disinformation and propaganda) is not far off, although the quality will definitely be lacking for at least the coming years. Who knows, maybe GPT-4 will be the gamechanger needed.
For domestic Chinese purposes, however, this fits the bill. We in the IO/disinformation space often overly hype state media outlets, but much of what state media apparatuses do is really just to impress the higher-ups and bombard the masses with low-quality drivel. They do this because it’s their job and they have to present evidence of work to their superiors and quantity over quality more often than not gets the job done. Throwing in buzzwords like AI and cutting costs while doing so makes it sound even better to higher-level bureaucrats, despite the lack of impact.
Additionally, the use of “data” in everything nowadays, including the centrality of “data-driven” insights in all decision-making, emphasizes quantifiable results - likes, shares and comments. This inherently biases state media and information operation outfits to do work that they can quantifiably show is successful by engagement, and often even boost engagement for that purpose - as well as of course to attempt to game the algorithm and make it appear popular to other users.
525,600 Minutes
How do you measure a year of Russian hybrid warfare in Ukraine?
Microsoft’s threat intelligence analysts have attempted to answer this question in their report, published on March 15th, looking back on Russian activity in Ukraine.
The report covers both cyber espionage and warfare alongside influence and information operations, in many cases correctly referring to them as “parallel” operations. The report also analyzes the development of IO/cyber activity in the wider geopolitical context of the war over time, which I found to be particularly useful.
It’s worth reading for a variety of reasons, but one of the things that I enjoy the most about it are the infographics as shown below. Microsoft recently purchased Clint Watts’ boutique investigations firm Miburo to set it up its own internal Digital Threat Analysis Center, and these types of infographics are hallmarks of past work done by Watts and Miburo in general. Miburo’s substack, now unfortunately inactive since being purchased, is available here for other examples of useful infographics. As an aside, Watts is rightfully one of the best-known thought leaders in the field, so if you’re reading this and aren’t aware of him or don’t follow him - you should go do so.
Source: Microsoft
The report is also a great foundational source for those looking to begin to investigate or analyze Russian disinformation sources directly, listing both overt media outlets as well as relevant Telegram channels and “war correspondents” such a WarGonzo and others.
One of the better uses of quantitative analysis of network traffic for IO analysis appears on page 7 of the report. The Russian Propaganda Index (RPI), created by Microsoft, tracks the flow of pro-Russia sites in Ukraine.
This sort of analysis, while almost assuredly done to a higher degree by Microsoft due to its size, skills and telemetry, could also be replicated to a lesser degree by individual open-source investigators by using tools such as Similarweb. Similarweb is a great tool also for understanding domain popularity internationally, where it’s shared on social media, similar sites and more - more open-source investigators should leverage Similarweb in their analysis.
The report also continues past publications by Microsoft and others emphasizing the importance of “hacktivists” in Russian malign influence and cyber activity. The diverse “landscape” of hacktivists in the service of Russia serves as a convenient backlog of cutouts for Russia to utilize for cyberattacks, as well as mouthpieces to then coordinate that activity online and amplify it to international audiences. The “weaponization” of fact-checking by Russia as a tool for IO as well is a notable development that has been reported on by others, and is also utilized by Iran-linked actors.
I personally also respected that the “looking ahead” section was comparatively modest and restrained. Predicting the future is more often than not a fool’s errand and the report certainly makes no grand claims or predictions about the future that it could later regret.
One thing I will say - please provide more threat indicators for IO! This is a huge issue in industry reports and is necessary for effective mitigation.
FakeReporter on the Roof
Russia has been flexing its polyglot muscles in recent weeks, with an uncharacteristic amount of Hebrew content.
Last week we discussed the DFRLab’s report on the InfoDefense/Node of Time network, which included a number of region and language-focused channels.
Source: DFRLab
Russia’s state media apparatus is active in many of the above languages to varying degrees, and the Russians have always been proactive about producing multilingual content.
What is commendable, however, is that they appear to be increasingly investing, if to a small degree, in Hebrew. A recent report (published in Hebrew by the Israeli organization FakeReporter) exposed a suspected Russian botnet on Twitter promoting anti-NATO, anti-US, anti-Ukraine and other similar narratives in Hebrew to an Israeli audience.
This comes as Israel has (finally) begun to provide more concrete defensive aid to Ukraine, and is apparently even now considering providing other military equipment. While I don’t foresee Russia launching a wave of Hebrew-language information operations against Israel, the past presence of Hebrew shows that even smaller targets can be opportunistically targeted in response to wider geopolitical changes.
Be a Master of your Domain Analysis
One of my favorite pieces of advice to people beginning in the OSINT/CTI space is to recreate investigations done by other people. This is especially relevant for domain analysis, as domains are complex entities with broad attack surfaces for investigation. It’s quite difficult, but obviously not impossible, to create a truly anonymous domain without accidentally breaking OpSec.
Additionally, domains can be quite difficult to investigate, as they require an understanding of:
How domains function and what technologies they utilize.
Understanding how commercial hosting services work.
How to query online infrastructure and understand the results.
The recent coverage of a “fake news site” capitalizing on the recent environmental and human tragedy that occurred in East Palestine, Ohio is a good example of the utility of doing so. The unfortunate incident itself has, unsurprisingly, been exploited by Russian online assets.
A recent investigation into the domain covered the use of GAN-generated images for inauthentic journalist personas, coordinated promotion on Twitter and other hallmarks of the field.
However, there are some things that we can learn from this investigation about domain analysis that are useful to keep in mind.
A reverse IP query was carried out on the domain’s IP address as part of the investigation. This query checks which other domains are currently hosted on the same IP address (yes, it is possible to host multiple domains on the same IP address).
ViewDNS, a fantastic free tool which I recommend that everyone use when trying to save on query credits, was the main tool used. ViewDNS is great, but it isn’t perfect. The data queried by ViewDNS is often limited compared to other tools, and in this case retrieved 19 domains hosted on the same IP.
The investigation then refers to this finding as evidence that the other domains, which also appear stylistically similar, are in fact dormant domains destined to disseminate disinformation.
Looking at the majority of the domains, however, only a few of the domains themselves refer to potential news topics, with commercial topics being preeminent, leaving me unconvinced that this is correct. If anything, this network of domains appears to be preeminently focused on financial gain and probably driving traffic to garner ad revenue. Additionally, similar styles of domains can also be coincidental as certain formats are common as default options for some domain creation services.
Additionally, the number of domains hosted on the IP is in fact much larger.
When using ViewDNS, always verify results with other, paid tools to confirm the findings. This is feasible without spending money in many cases, as most paid tools will provide the number of results while not directly showing you the results themselves, so we can then assume that the domains overlap if the numbers are the same. However, checking the IP address in DNSLytic’s reverse IP shows that there are in fact 100 domains hosted on the IP in question.
The large number of domains here includes other domains that may in fact be news-focused. The majority, however, are spam/commercial domains, and beyond being hosted on the same IP address, their connection is tenuous. This IP address is hosted by a commercial provider. This means that the domains hosted on it are not all necessarily directly tied to each other, as commercial providers can host multiple unrelated domains on the same IP by renting it out. Clusters of domains that are stylistically similar may be - but there’s a lower chance of all of the domains being tied.
Most of the retrieved domains also share highly similar infrastructure arrays - name servers, mail servers and of course - the IP address. These are all commercial, large-scale services, making it further more difficult to find any information on ownership.
Let’s compare the infrastructure array used by these commercial services to proprietary infrastructure set up by Russia Today:
Here we can see that RT uses its own proprietary infrastructure for some of its services:
Name Servers
IP Addresses
Google Analytics ID (we’ll get into this at a later date)
Name Servers: rttv.ru - the name itself is indicative. Additionally, reverse querying these name servers shows a high degree of overlap of the domains themselves:
The same query run on the commercial Google mail servers used by RT are shared by millions of domains and thus we can’t determine any connection between the domains themselves.
We could also query the two IP addresses listed by DNSLytics in a reverse IP query, despite one solely hosting the RT domain and another hosting 3 domains in total.
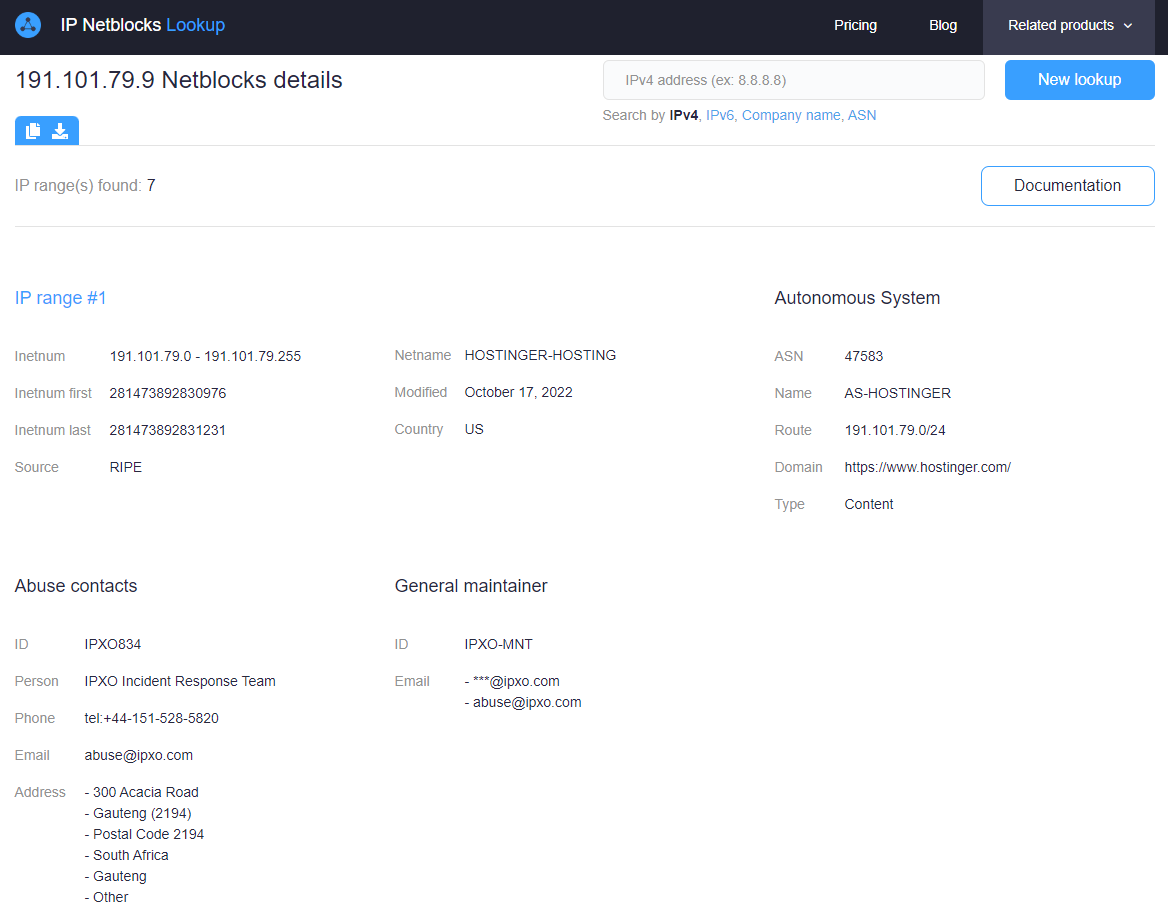
We could also check the WHOIS records of the domain, but for the purposes of this blog we’ll utilize a different tool that is often less utilized, IP Netblock lookups. These are functionally analogous to WHOIS lookups for a range of IP addresses, and the WHOIS results for a given domain are often equivalent. For those interested in learning more about the difference, I’d recommend reading this article from WhoisXMLAPI.
Querying them both in WhoisXMLAPI IP Netblock lookup shows that the IP address itself is part of an IP range named CIREX-RTTV1, which is registered the RT-affiliated TV Novosti outlet. Note additionally that the Autonomous System (ASN) is registered under RTTV also. Most of this information would also be available to us in a WHOIS lookup for a given domain name.
Querying the other domain exposes that it’s in fact owned by DDoSGuard RU, an infamous hosting and DDoS protection service based in Russia.
We can then apply this technique and query the IP address in WhoisXMLAPI’s Netblock query tool to see who owns the IP address. This shows that it’s owned by Hostinger, a commercial hosting service. I’d be beyond happy to hear from anyone who knows more about the dynamic IPv4 hosting industry about this as well if there are any inaccuracies in what I’ve stated here.
Point being - when the infrastructure isn’t privately-owned/rented (i.e. a VPS, or virtual private server, with a small set of domains directly tied to each other and thus probably owned by the same individual), it’s functionally impossible to determine direct relation based upon these ties.
There may be other ties between domains hosted on the same commercial IP address, but being hosted on the same commercial IP address is not substantial enough to make larger, sweeping claims about potential network activity.
Querying the IP in Shodan does a nice job of presenting the data in a more appealing manner:
So, to summarize, let’s conclude the following regarding domain analysis and reverse IP queries:
ViewDNS is a great free tool, but it’s imperfect.
Cross-check data sources and tools when carrying out domain analysis.
Differentiate between privately-owned infrastructure and public, commercial infrastructure. Having domains hosted on the same commercial IP address does not a strong relation necessarily make.
There are numerous other directions that we could take when investigating this domain, but I’ll save those for a later blog post. There’s also an element of privacy involved that unfortunately prevents me from publishing more details as to the actual suspected owner of the domain, so we have to keep all investigations and findings anonymized to the highest degree possible.
Till next week, thanks for reading. If you have any comments, questions or otherwise - feel free to reach out!





















I'm only familiar with the paid tools (RiskIQ, DomainTools). Happy to know there are free, albiet very limited, alternatives. SilentPush has similar capabilities and its free community edition might checking out.