Let's Get Physical
Welcome to Memetic Warfare.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
I’d like to take a moment to recommend that everyone follow Discourse Power , my favorite Substack about China written by the brilliant Tuvia Gering. He’s back after an extended break, and is a fantastic writer, so check him out.
Before we begin, those of you who just can’t get enough of me are welcome to join a webinar that I’ll be hosting soon with Falkor and Matteo Tomasini of District 4 Labs on the use of compromised data to investigate hard targets, in this case ransomware operators:
Anyone interested can register here, and of course feel free to reach out with any questions.
This week’s main topic will be Russia, and to a lesser extent the Olympics.
We’ll start with news reports on physical IO activity in France. Then we'll discuss Microsoft's latest report on Russian activity targeting the Olympics.
Finally, we'll go over Reset.Tech and CheckFirst’s report on Russian Operation Overload, including some fascinating new information on Telegram and a great use case of image forensics.
Let’s Get Physical
Russian subversive activity in Europe appears to be inspired by the special Olympic spirit and is getting physical.
Online cyber and influence operations are by no means falling by the wayside, but as relations between Russia and the EU get worse and worse, sabotage and even real-world IO is becoming a new normal on the continent.
There’s been much discussion already of Russian sabotage across Europe. Something that’s been covered a fair amount but seems to be ramping up is physical influence operations. One of the more recent cases we had was an anti-Semitic graffiti campaign in France:
This has continued as of late, with mainstream media reporting on a Russian “stunt”, in which multiple coffins, “draped” in French flags and having been inscribed with “French soldiers of Ukraine”, were placed around the Eiffel tower:
This kind of real-world activity (meaning, directly carried out and not say just the financing of protests or front groups) has been comparatively rare in recent years, arguably due to the rise of online influence operations.
Real-world IO or psyops are by no means a new phenomena though - just read Active Measures by Thomas Rid or anything by Rory Cormac to read more about the history of this kind of activity.
We’ve begun to see more of this though globally - Iranian physical activity in Israel, for example, as we’ve discussed on this blog.
Fairly safe to say that we’ll see more of this going on, especially considering the ease of outsourcing and low cost (400 Euros apparently for payment, alongside low operating costs) to carry this sort of thing out. The Olympics would also be a fantastic environment in which to carry out a few more of these types of operations - global attention, masses of people and so on.
Let’s move on to the digital side of things.
The Perfect Storm-1679
Online IO is alive and well, as shown by Microsoft’s MTAC writeup on IO threats and the Olympics, available here. The report covers Russian activity, including the various “Storm” groups, as Microsoft calls them. The report is straightforward with two goals as per Microsoft:
AI-generated audio and video, as well as Telegram, are recurring motifs:
Doppelganger, or Storm-1099 is also in it to win it and is pivoting hard to the Olympics:
Where predictions come into play, Microsoft is on the money as well and also warns about “on the ground” action. Fittingly, the physical/IO overlap space seems to be the hot new thing, at least for Russian activity in Europe.
Stop Trying to Make FIMI Happen
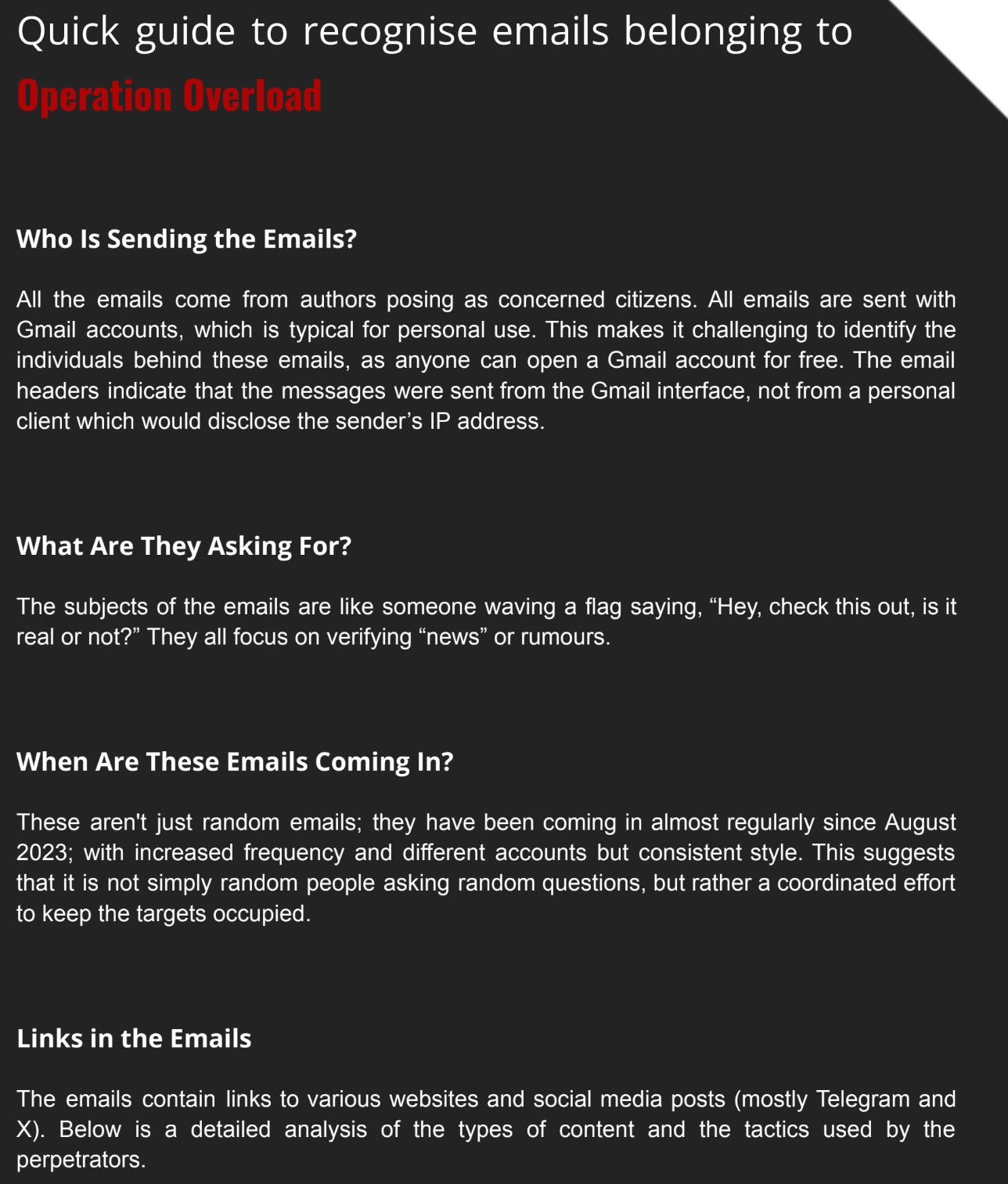
CheckFirst and Reset.Tech wrote a report on a new, sprawling Russian influence operation, available here. Shoutout to Antibot4Navalny and AFP for publishing about the Matyroshka network which catalyzed this report, as per the authors.
They’ve named it “Operation Overload”, in what I assume is a reference to Operation Overlord, but who knows.
I’ll place the executive summary below:
The report has some very, very interesting sections in it that we’ll discuss below, so let’s begin.
Not going to lie, not loving the new trend of people using too much Gen-AI imagery in reports, but not a huge deal.
Let’s get to what’s new as it’s a long report, with a lot of content that we’ve already covered here more or less.
The new TTPs are of interest, especially the use of email and the “amalgamated content” section.
The operation focused on domestic and external targets.
The report also uses the phrase “FIMI” (foreign information manipulation and interference). While certainly not the fault of the authors for including, as I imagine they work with the EU, I personally won’t be using FIMI as a professional term going forward as it’s incredibly cringeworthy and most importantly, unnecessary.
The last thing the IO space needs is more acronyms and definitions which in this case provide nothing new at best and are limiting and confusing at worst. This is a typical EU move - focusing on definitions and frameworks and thought processes and regulation instead of the core issue at hand, while various NGOs and other organizations in Europe are busy actually pushing the field forward.
Now that I’m done ranting about that, let’s review the new TTPs. Content amalgamation is the first one:
That’s all well and good, but we’ve seen similar things before. The interesting part is the email campaign:
Kudos to the authors for breaking things down visually:
There’s an emphasis in the network also on amplifying photos of graffiti, which Russian operations just seem to love!
1,000 points for doing image forensics.
Those who would wish to recreate this themselves can use TruFor by downloading from their GitHub repo here. Other tools I’d recommend include Forensically, FotoForensics and InVid for more accessible tooling.
The Telegram section is also fascinating with impactful findings. The authors found that content on Telegram can be watermarked to the level of the individual user.
The authors then were empowered to look for cases in which the same individual user has administrative access to more than 1 channel, as shown by having uploaded the same content:
Looking at one example shows how images uploaded by individual users creates a unique variation of the original file, visible by the changes in the SHA 256 hash of the files:
And here we go. When uploaded and compressed by Telegram, the files change very slightly in a unique fashion! This is what leads to the hash being different.
The authors also make an interesting claim about Telegram storage servers.
The claim is that the server an image is stored in when uploaded by a user on can be cross-referenced to the server an image is uploaded to by a channel:
They use this claim to make some interesting claims about the network channels:
I’m not necessarily convinced that this would be a relevant cross-reference. We would need to know the exact criteria for which Telegram server is selected to host a given image, which we don’t know, and it doesn’t take into account other factors - the use of proxies or VPNs for example.
Overall, it’s a great report. The visual forensics and general coverage are great, and the Telegram section is highly impactful, with the findings regarding the file hashing being fascinating if niche.
Tip of the hat here to the authors - nothing makes me happier than seeing people take the IO/OSINT space forward technically.
That’s it for this week! If you made it this far, check out Telemetryapp.io and check in next week!