Seek Truth from Transcripts
Web3 Holds Up Half the Sky
Welcome to Memetic Warfare.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also do training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
We’ll start off with an “Emerald Divide” update, cover Chinese forgery activity and from there discuss the latest ASPI report.
800 Pieces of Silver
Iranian activity continues to ramp up their risk posture (meaning that they’re willing to take more risks). We’ve seen this not only with the general increase in operations, but the use of real-world activity as well: sending flowers to a hostage family, for example.
A new development in this regard was the exploitation of a leading Israeli “influencer”, Daniel Amram. Amram has a Telegram channel with over 350,000 subscribers, and he runs ads like any other commercialized Telegram channel.
When Amram ran an ad from the Iranian “Tears of War” Telegram IO channel, FakeReporter, an Israeli NGO, immediately noticed it and posted:
Amram later uploaded an hour plus long mea culpa here. He explained that he uses an outsourced marketing firm for inbound marketing on Telegram, which failed to carry out KYC in this case.
Most interestingly, the firm itself stated that the caller was a Hebrew speaker with no accent who called after initially messaging them on Telegram. The advertisement itself ran for 800 shekels (and the operator even asked for a receipt) showing that the Iranian operators had access to Israeli accounts of some kind.
It doesn’t stop there though. FakeReporter looked at the receipt that Amram posted, showing that the same name was used in this case as was used in the flower-sending incident.
Seek Truth from Transcripts
Now let’s take a look at is the CN-PH tension over the Scarborough/Ayungin/RenAi (and other various shoals).
I actually tweeted about this case and what it means in the broader AI-powered IO space, so see more about it here. Collin Koh has tweeted extensively about this, so follow him for more information as well.
First, let’s summarize the situation for those that don’t religiously follow the Global Times. As part of ongoing tension between China and the Philippines over several shoals and maritime territory, the Chinese MFA claimed that they had a transcript of a call between a Chinese and Filipino official, and later doubled down with claims of an audio recording existing.
In this call, the Filipino official ostensibly accepted Chinese claims about the Chinese “model” of sovereignty over the territory. The PH government of course has denied these claims:
Atlas News has some solid coverage available here.
Atlas also analyzed the transcript and the recorded audio, and provided some reasonably convincing points that they are likely “deepfakes”. This includes logical issues with the timeline of mentioned data
Additional use of linguistic analysis is also reasonably convincing:
The AFP has also called it fake, and Chinese state media has come out to defend it:
This is a truly fascinating case. If anyone else is aware of the suspected use of AI-generated forgeries in the context of overt diplomacy, please let me know.
This is especially interesting in light of the recent NSA disclosure on CNN of Chinese and Iranian low-level “deepfakes” being created, but not used, against the US elections in 2020.
Back in 2020, the NSA was unimpressed by Iranian/ Chinese deepfake capabilities and lack of a Chinese risk appetite to inferfere in the US elections via deepfakes.
By 2024, the Chinese appear to be utilizing Gen-AI text and audio tools for forgeries, and are presumably exploiting commercially available tools as we've seen with Synthesia in the past.
The democratization of these tools alongside an increased risk appetite may lead to serious escalation. The timeframe is also rapid - in just a few years we went from AI-forgeries being too ineffectual to be worth using to setting news cycles as they’re used in diplomacy.
This CN-PH case thus I believe sets a precedent, and also raises multiple questions:
Should deterrence or punitive actions be different for AI-powered IO activity compared to "traditional" IO?
How about if they're used in diplomacy or election interference?
This dynamic continues to develop, as shown by recent NYT coverage of alleged Russian AI-generated deepfake videos:
More on the videos here:
There are some big claims here - for example, that the campaign is tied to “veterans” of the IRA, and affiliated with a Russian think tank.
It’s possible that this information comes from both/either closed or open sources. I look forward to seeing whatever Microsoft open-source reporting shows this, or alternatively further explanation on whatever SIGINT or closed sources were used.
None of this is to say, however, that non-AI forgeries are going to fall out of style. The opposite, in fact, it seems is true as China becomes increasingly comfortable with using forgeries of all kinds.
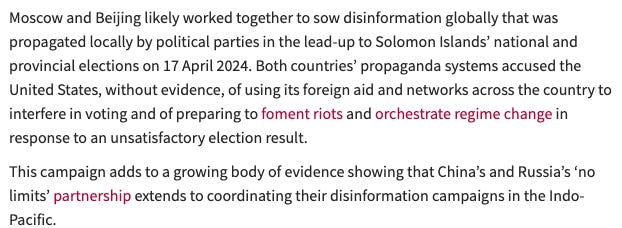
ASPI’s Albert Zhang wrote a great primer on Russian and Chinese influence efforts targeting the Solomon Islands’ elections, see the first paragraph below:
As part of this partnership, a “poorly fabricated” letter was discovered and published on Russian state and grey media sites:
The Chinese may not have created this forgery, but were very comfortable amplifying it much more substantially than Russia.
This case is highly reminiscent of the Ukrainian biolabs narrative - pro-Russia elements create a forgery or false narrative, and the Chinese amplify it greatly (alongside Russians of course).
On that note, let’s discuss the recent ASPI report.
Web3 Holds Up Half the Sky
ASPI has been out there wildin’ on China-oriented reports. Let’s look at their latest academia-style in-depth report, “Truth and Reality with Chinese Characteristics”, into Chinese data governance and the use of unconventional, let’s say, methods for potential “propaganda work” and influence. I’ll let them describe it better below:
The report focuses on four main datasets as shown below:
The report is an ensemble piece with an accompany data-oriented domain, available here. Would it be a report if the data weren’t visualized with a graph? Who’s to say.
The report itself is quite long (50+ pages) so we’ll only focus on a few points. The first point that we’ll look at is the broad scope of data that ASPI claims is utilized by China, including e-commerce platforms, web3, the metaverse, VR/AR and gaming are vectors as per ASPI. In short, they’re going for the crypto/VR grift!
Personally, I’m not so convinced that the party does in fact view the above technologies are critical per se to their efforts, but there are some other notes that are important to bring up. The first is the concept of “media convergence”, read more below.
People in this space often prefer to focus on covert operations. This is especially clear when discussing Russia and it’s much vaunted (but in practice and in my opinion far less impressive) digital influence capabilities. Influence, though, is a spectrum, of which covert operations play a smaller role than one might believe in contrast to grey or even official media outlets.
Chinese influence efforts are broad, multimodal and multifaceted and much more complex than many researchers in this space would believe, and most importantly: this is a matter of doctrine. That doctrine is media convergence, as described in this article and many others.
For those who want to read more about convergence, the article does a great job of visualizing it:
Trying to win over hearts and minds and bring about actual change in their interest is how the Chinese operate. This isn’t a zero-sum game as is often discussed in the context of Russia. Anyway, now that I’ve yapped enough about this, let’s move on.
The report maps out the multiple Chinese bodies that do propaganda work network outside of the MPS and MSS - imagine being on the “eradicate pornography” team.
Media convergence is viewed very holistically, including AR/VR/”XR”, apparently:
The doctrine of media convergence thus mandates the mass collection of data to power its implementation. From there, the report reviews Chinese approach to data governance and collection, emphasizing e-commerce apps and others.
Some of these have been “scrutinised” for gathering data against app store privacy rules.
This data could then be later utilized
I’ll skip much of the later sections as the report is quite long and get to the parts relevant for this blog. It seems for example that the Chinese AGI market will soon have homegrown replacements for Synthesia. I’ve written in the past about KYC needs for these platforms, but there’s no doubt that eventually these will be irrelevant as domestic tooling is created.
Another interesting company is AIME, apparently a subsidiary of a civil-military fusion firm, GTCOM. AIME is working on an “Intelligent Audio-Visual Content Generation System” to disseminate content and overtly states that it works to “disseminate ideological content”.
There’s even more on this specific firm and its relevance in promoting global “discourse”.
While many of the report’s findings are solid, some are less convincing. The claim about online user decisions, for example, is a bit of a stretch.
Overall, this is an interesting and useful report, and is especially relevant on the backdrop of the TikTok ban and its data practices.
As stated by many government officials, there’s no doubt that Chinese applications, TikTok chief among them, gather up too much data and pose a foreign interference threat in multiple ways.
However, it’s also important to not get carried away: personally, I’m not super concerned about Chinese web3 data collection.
That’s it for this week! As always, contact me here or on LinkedIn with any questions or comments, and check out Telemetryapp.io.