Dark Souls (& Thoughts)
Welcome to Memetic Warfare.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
A quick aside - following last week’s post and shoutout to Flinfo, I’m happy to share that they’ve agreed to provide a 10 percent discount on new memberships for those who register for their free trial and mention Memetic Warfare! Again - no commercial relationship here between me and them, just promoting a cool tool.
When it rains, it pours. My cup doth runneth over with news regarding domain infrastructure and hosting and IO.
Let’s start off with an absolutely incredible report from Qurium. Qurium is one of the lesser-known, but in my opinion most-impressive and impactful, research consortiums out there. Follow them!
I don’t have time to go super in-depth into the report, so I’ll list some main points below, but read it yourself in its entirety! Check out the summary below, then my points.
I’ll share the main takeaways and some of my views below:
Russian IO operators use a network of hosting infra providers, including bulletproof hosting providers, to host IO infra.
IO operators are reliant on these bulletproof hosting firms to provide scale and reliability (which they already have by virtue of being active in cybercrime for years)
Bulletproof hosting isn’t ideal for IO though, as it can be easily blacklisted
So, hosting companies open front companies Europe and abroad and then peer networks together, showing importance of corporate registration for investigation in IO/cyber
This is also somewhat reminiscent of sanctions busting as is done now by some Europeans with Russia via third party countries
Some infra providers are even registered in US, exploiting a lack of registration transparency and access. There’s a great need for American corporate registration transparency, and this need isn’t new - cyber operators can register firms in certain US states to prevent American intelligence agencies (beyond the FBI and a few others) from investigating them.
The main actors are Aeza and the Evil Empire ecosystem of over 20 ASNs and various shell firms. Running these ASNs costS over 50,000 EU a month as per Qurium. See past Memetic Warfare investigations involving Aeza and Evil Empire infra here and here.
Aeza and its operators frequently change names, network prefixes and even spoof locations to avoid identification.
As the internet gets more and more fractured and hosting infra becomes harder to acquire for non-Western actors, we can expect more creative ways to whitewash blacklisted ASNs and provide access to Western internet for threat actors. This is a similar dynamic to typical espionage/intelligence operations internationally.
Upside - easier to block ASNs and providers as government responses move up the chain. Can and should blacklist full ASNs, making it harder for threat actors to operate, but not perfect. I wonder when we’ll see US/Western cyber or even kinetic targeting even further up the chain.
If you’re interested in learning more about how ASNs work or investigating ASNs, check out bgp.tools. BGP Tools provides information on ASNs and how internet traffic is routed. Let’s look at AS 210644 below, which belongs to Aeza:
We can see how Aeza routes its traffic, as well as via which ASNs! Interesting stuff for future investigation. We can see upstream providers (in this case, ISPs that provide Aeza with traffic routing).
Not only can we see that, we can see peers. Peers are in this case networks that route traffic through each other for broader internet connectivity. Here we can see a few suspicious ASNs, such as TNSecurity - interesting.
This is the sort of thing that may become more useful as we increasingly move up the chain and look more at hosting providers, so check it out yourself.
Team Ame(liorator): World Police
The good times keep rolling with a US, UK, Australian, Canadian, New Zealand, Dutch, German and even ROK and Japanese agencies signed and published a joint cybersecurity advisory on APT40. This advisory attributes APT 40 officially to the PRC, claiming that it operates under MSS' Hainan bureau.
Notably, this is the first time that Japan and the ROK have joined a public attribution of Chinese cyber activity, presumably due to increased willingness to name-and-shame China over geopolitical tensions.
The more interesting news though, at least for me, was an additional advisory from the US DOJ and FBI, alongside partner agencies in Canada and the Netherlands.
This advisory calls out Russian state media outlet “Russia Today” for using “Meliorator — a covert artificial intelligence (AI) enhanced software package—to create fictitious online personas, representing a number of nationalities, to post content on X (formerly Twitter).”
In tandem, the DOJ seized two domains and just under a thousand Twitter accounts that were used as part of the ongoing operation. Affidavits for the seizure of the domains and accounts are available here.
So let’s take a look at this advisory:
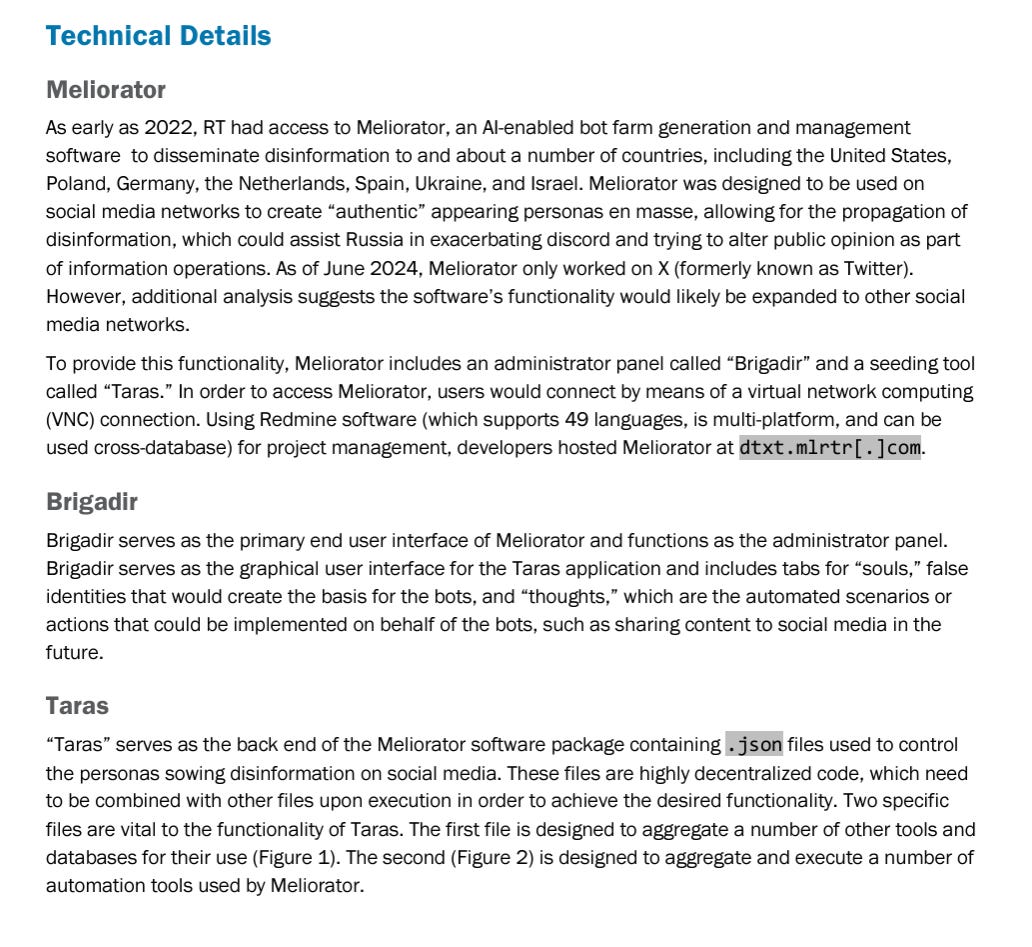
Interestingly, the network operates using “Meliorator”, which is compromised of two parts: an admin panel titled “Brigadir”, and a seeding tool named “Taras”;
See below a diagram showing how this works architecturally”:
See below a more detailed description of “souls” and “thoughts” and how these were algorithmically generated:
The advisory also specified what the platform is capable of doing:
This was so advanced that it generated all of the accounts programmatically with the same domain name!
I’m joking of course - this is lazy stuff, having the username be the same as the email address and all on the same domain.
As an aside - one of my first thoughts when I saw this system was the admin panel. How feasible would it be, with a bit more information, to hunt this admin panel via Censys assuming there are multiple instances of it on various hosts? I may take a look at this later.
Moving on. The network used two listed domains for email registration purposes - mlrtr(.)com and otanmail(.)com.
Anti-bot capabilities had to be bypassed with specific development, and in this case it interestingly is able to bypass the verification method because the email used is the same proprietary email hosted on the domain:
These domains were used to register accounts, as shown by the affidavit used to seize them:
So this is fascinating. Let’s compare it to cyber briefly, because why not. On the “pyramid of pain”, we could compare individual accounts or posts to the “easy” or “trivial”, as they’re easy to replace.
Exposing domains would be arguably comparable to domains in the context of cyber operations, but exposing the software product would definitely be congruent with the “tools” category above - certainly not impossible to replace, but definitely much more of a pain than registering a new domain.
By the way - this isn’t the first time that the US has seized IO domains. The US has seized Iranian domains in the past, see the affidavit here, but the real power move here is exposing the software solution and how it functions to enable platforms to mitigate their risk effectively.
This is exactly why this takedown is great - moving further up the pyramid of pain makes it harder for adversaries to carry out operations. Catching individual accounts or even large networks will never suffice.
The report, unsurprisingly, includes platform-specific mitigations:
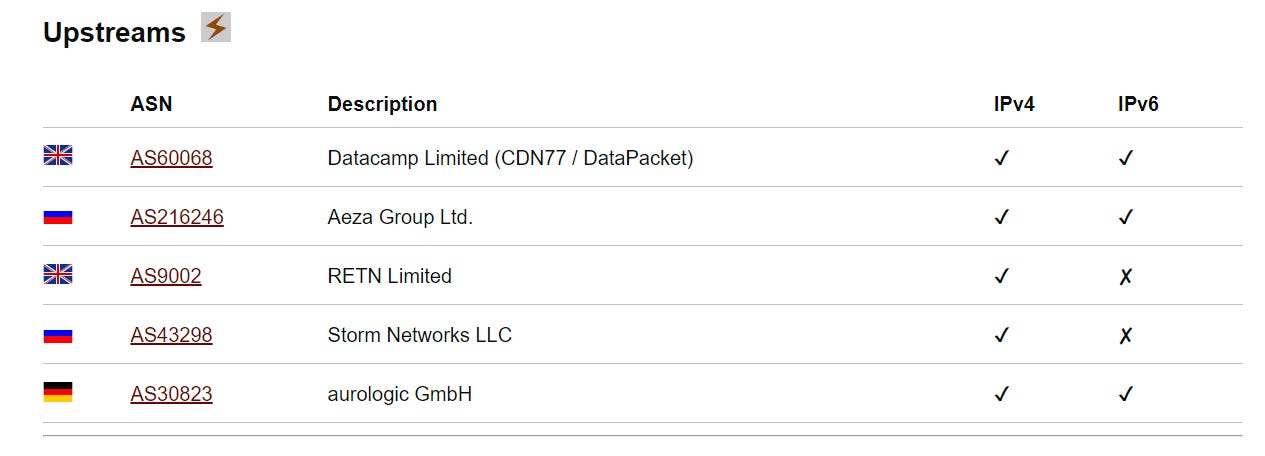
Identified infrastructure is also included:
Let’s pivot on some of these and see what comes up in just a few minutes.
There are more than a few ways we could start, but considering that the domain has already been seized I decided to look at passive DNS in VirusTotal:
Here we see that the mlrtr domain has been hosted on 5 different hosts. From here, you’d want to look at these hosts and see if you can non-commercial shared hosts, meaning hosts that are run exclusively by the operators of the domain.
You can do this very roughly by looking at hosted domains - does the server host thousands of different domains? Is it a known commercial hosting provider for specific domains, or does it primarily rent out VPSes?
In this case, we have a clear answer in the first host registered:
The very first host (as per VirusTotal and a few other sources I’ve checked, but they could be not updated with the best passive DNS data), the first host to host the domain was a Russian provider.
This host also hosted dozens of subdomains all belonging to the same company, movista(.)ru. Let’s look at the archived domain here.
Interestingly, they’re a software development firm for transportation companies.
This doesn’t explain why exactly the mlrtr(.)com domain was hosted on what was clearly their proprietary web server, which is highly suspicious. Definitely an interesting open question with some implications.
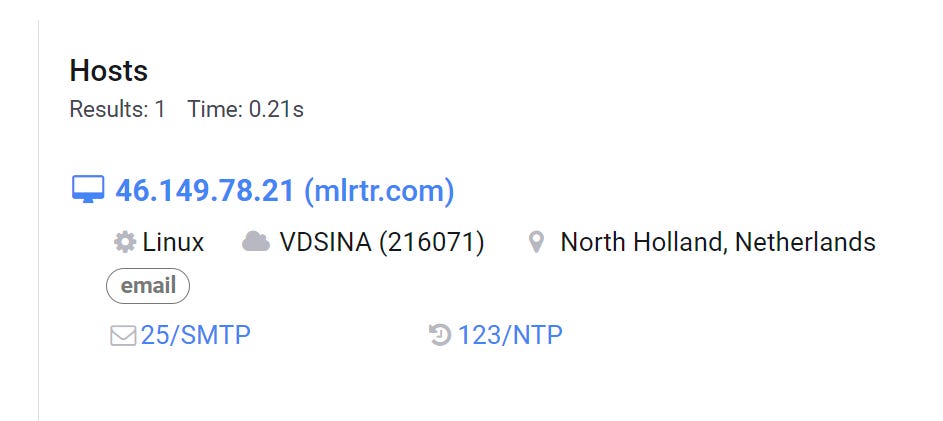
Let’s take a look in Censys. Querying the domain for hosts finds only one:
So far, makes sense. The host is a mail server running SMTP on port 25. Let’s look further:
Pretty standard responses here, os let’s move on. The certificates search also didn’t uncover anything new, other than one Google certificate.
For now, we’ll stop here and look at the next host:
That’s better. Here we see that this host has hosted the mlrtr AND otanmail domains, as well as two new ones - wotkotik and ku4askidok.
From here, I’d recommend beginning to use some different tools - censys, URLScan, Validin, archive.org and so on. In this sort of situation, you’ll have to rely on archives/past scans as the domains are otherwise unavailable.
URLScan caught otanmail about a year ago, but unfortunately it wasn’t fully up yet:
The only HTTP response was a boilerplate response on installing Nginx:
So let’s review again why this is a big deal. We’re seeing critical development and action from US government and partner agencies in a few ways:
Influence operations domain hosting infrastructure and even software is being targeted, moving up the “pyramid of pain” for influence operations
Additional legal frameworks are being used to take down networks, such as the violation of sanctions in this case or the affidavit used to search accounts for more information
Technical analysis and investigation of infrastructure is used to target influence operations, not just counting tweets
International cooperation is apparently increasingly common, which is good and will only get better as this space develops
The mitigation section is written specially for platforms, and will make it harder for trust and safety safeguards to be bypassed
That’s it for this week! If you’ve made it this far, check out Telemetryapp.io, and let me know your thoughts.