Memetic Warfare Weekly, Inc.
Welcome to Memetic Warfare Weekly!
My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I also provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com. This week’s post will begin with a beginner’s guide on basic Facebook ad and page analysis, followed by some more advanced domain analysis techniques. After that we’ll discuss some news updates and analysis.
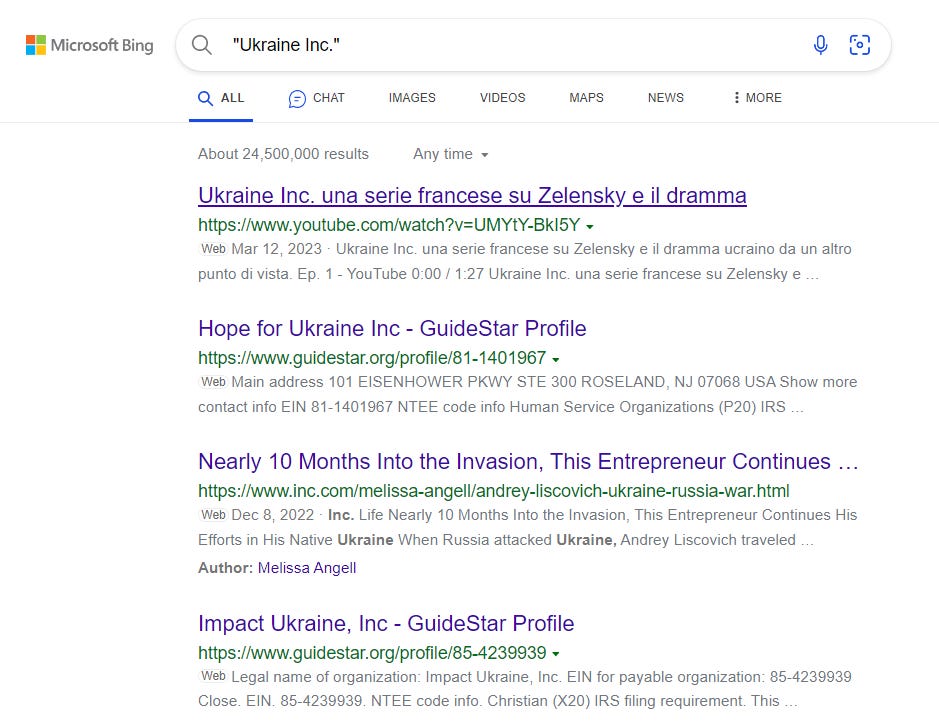
Ukraine Inc.
While doomscrolling through Twitter the other day, I came across the below tweet from Arieh Kovler. Kovler was unfortunately subjected to having to deal with low-quality Hebrew translations of Russian propaganda content via a low-effort Facebook page running ads. I figured that this would be a great example to show how we could investigate such an ad, and uncover other relevant activity.
Kovler points out that the ads promote a Russian cartoon denigrating Zelensky titled “Ukraine Inc”, as also stated in the broken Hebrew below.
Source: https://twitter.com/ariehkovler/status/1646226534380761088
Interestingly, the above ad and other mentions of “Ukraine Inc” (from primarily suspicious/inauthentic accounts) refer to the French provenance of “Ukraine Inc”, despite this of course being almost certainly not the case.
As shown by Kovler, the above Facebook ad was promoted by a Facebook page titled “Bonny eqd5”. The page has already been taken down, but I managed to take a look at it briefly.
The page, featuring a red handbag with the word “Russia” on it, features two 1-star reviews calling it out for being Russian propaganda. The page is otherwise empty, with no other activity.
When examining Facebook pages, one of the first things to do is to look at the page transparency section. The transparency section is often available on the left-hand side, or under the “about” section of the page - often available under the “more” option as well. There are some other important techniques that we can discuss in later posts as well.
The transparency section shows the page history, meaning its creation date and any potential name changes. Name changes can be crucial when checking if a page has been repurposed, and the creation date is of course relevant for a variety of reasons. This page has been created quite recently, which is a suspicious indicator, especially when taken in conjunction with the other suspicious indicators of the page.
The transparency section also shows whether or not the page is running ads, and provides a direct link to the page’s Ad Library page. The ad library is an underutilized tool for most IO research - as well as other OSINT research.
We can also search keywords and so on via the Ad Library search page:
The Facebook ad library can also be interacted with programmatically via its API for those interested in running advanced queries and exporting larger datasets from the ad library.
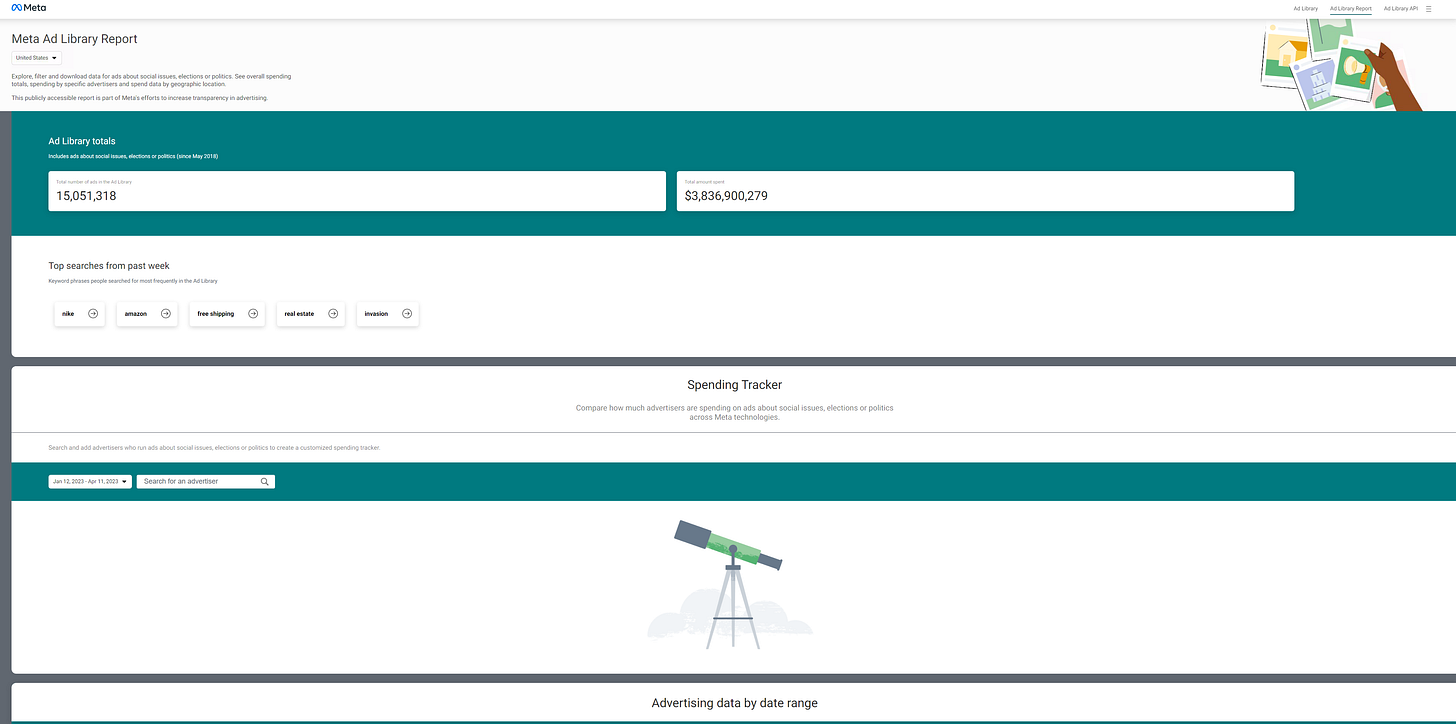
As an aside, the ad library also includes some excellent other capabilities alongside its search capabilities, such as the Ad Library Report.
We can filter by country in the upper left-hand side, and begin to see analytics on the total sum of ads.
One of the main uses is tracking advertisers over time:
We can also download a report based upon date range.
Back to the Russian ads. When looking at ads in the ad library, we can usually see more information on the ad itself - ad spend, demographics of those viewed etc. In this case we unfortunately don’t see any. Pivoting to other ads uploaded by the same page also didn’t bear any fruit.
There are a few things we can pivot off of here. The first thing, and the easiest usually, is to pivot off of the unique text available in the ad. I’ve tried searching a variety of strings and unfortunately have come up short, but something to keep in mind. This essentially means that there is no other identifiable activity in Hebrew, but as Kovler mentions - the cartoon series has been available at least via early March on Telegram:
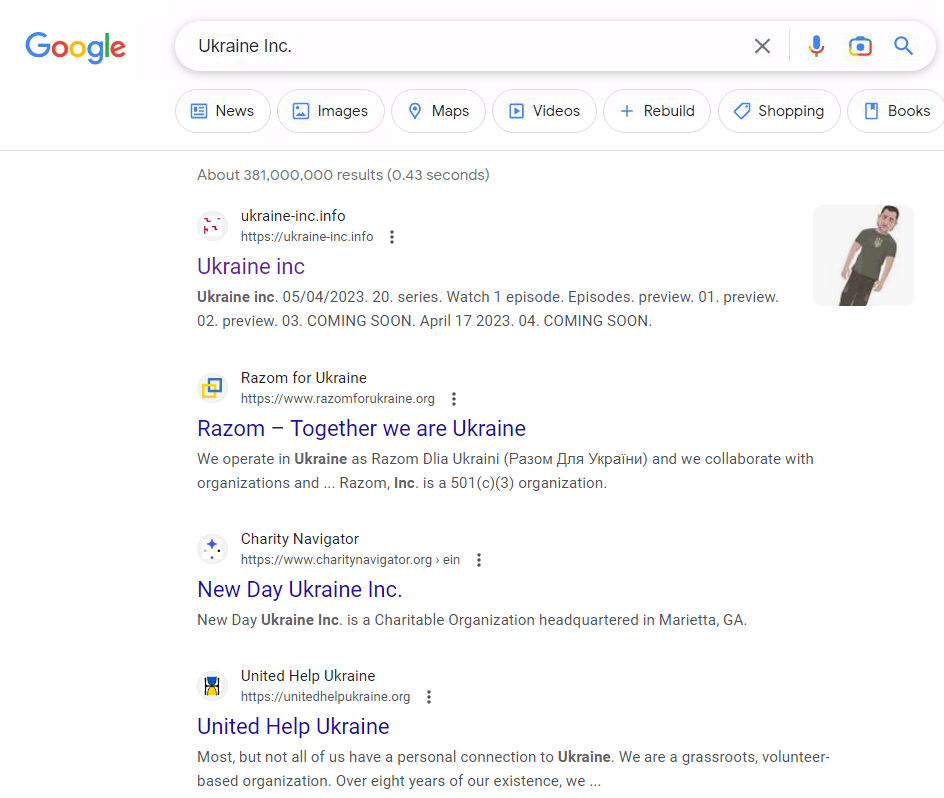
Googling “Ukraine Inc” retrieves the site Ukraine Inc, which hosts all of the released episodes of this apparently South Park-esque disinformation cartoon series.
Ukraine Inc’s domain was created on March 11th, 2023, which makes sense in relation to Kovler’s discovery of content from March 11th.
Most posts with links to the domain on Facebook also took place on March 12-13.
Twitter activity is more recent:
It seems that they’ve built this domain as intelligently and as anonymously as possible. The domain is hosted via Cloudflare, which also provides its CDN services.
The domain has no affiliated direct social media accounts linked or otherwise identified with a quick check.
There were no non-generic/commercial results for the typical reverse IP/NS/MX/SSL Certificate queries. I have yet to spend money and check historical WHOIS records, but I imagine they would be underwhelming also. Historical DNS records via DNSLytics retrieve two IP addresses - both Cloudflare hosted.
I’ve checked other methods - archive.org, analyzing Javascript, source code searching for other trackers or analytics and more.
The only tool to come up with anything of note was one of my favorite tools, PublicWWW. PublicWWW is a search engine for source code, meaning it searches the source code (HTML) that comprises sites - akin to “looking under the hood” if you will for domains. PublicWWW is usually used by digital marketers for online research.
By searching for code snippets that embed other technologies - as seen below - we can find other domains that utilize the same technologies. PublicWWW is an incredibly powerful tool, to say the least, for searches of all kinds.
When we query the domain for “Ukraine Inc” - Ukraine-inc(.)info - in PublicWWW, we get the below results:
Looking at the above snippet, we can see that the first result is irrelevant. However, the next two snippets are not only identical, but appear to be suspicious websites. Let’s take a look at them.
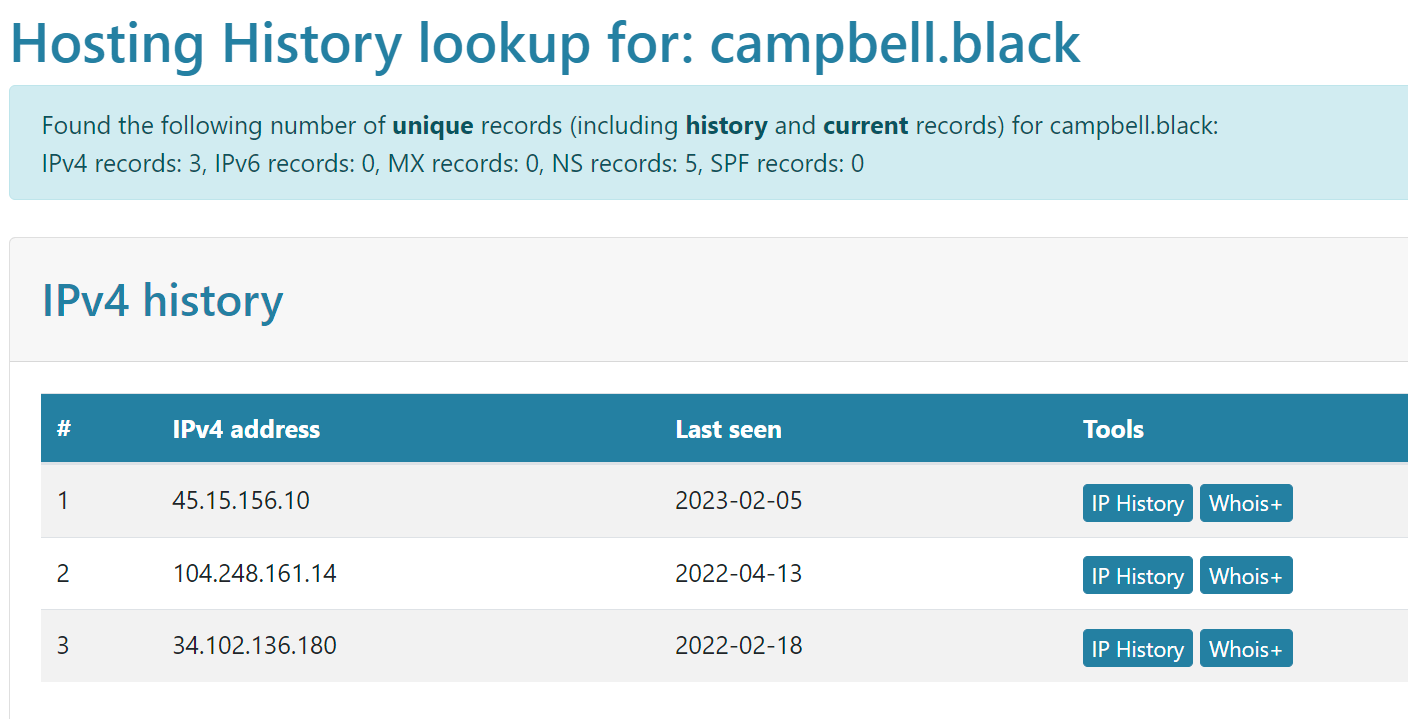
Campbell(.)black is the first result. The domain also immediately redirects to the Ukraine Inc domain, and was registered on February 17th, 2022 - making it the oldest domain here by far. Unfortunately, the only archive of the domain is a 404 message.
We can then go look up its historic DNS records via DNSLytics. Here we see that it has 3 IP addresses - which is starting to be a viable amount of addresses upon which we can pivot.
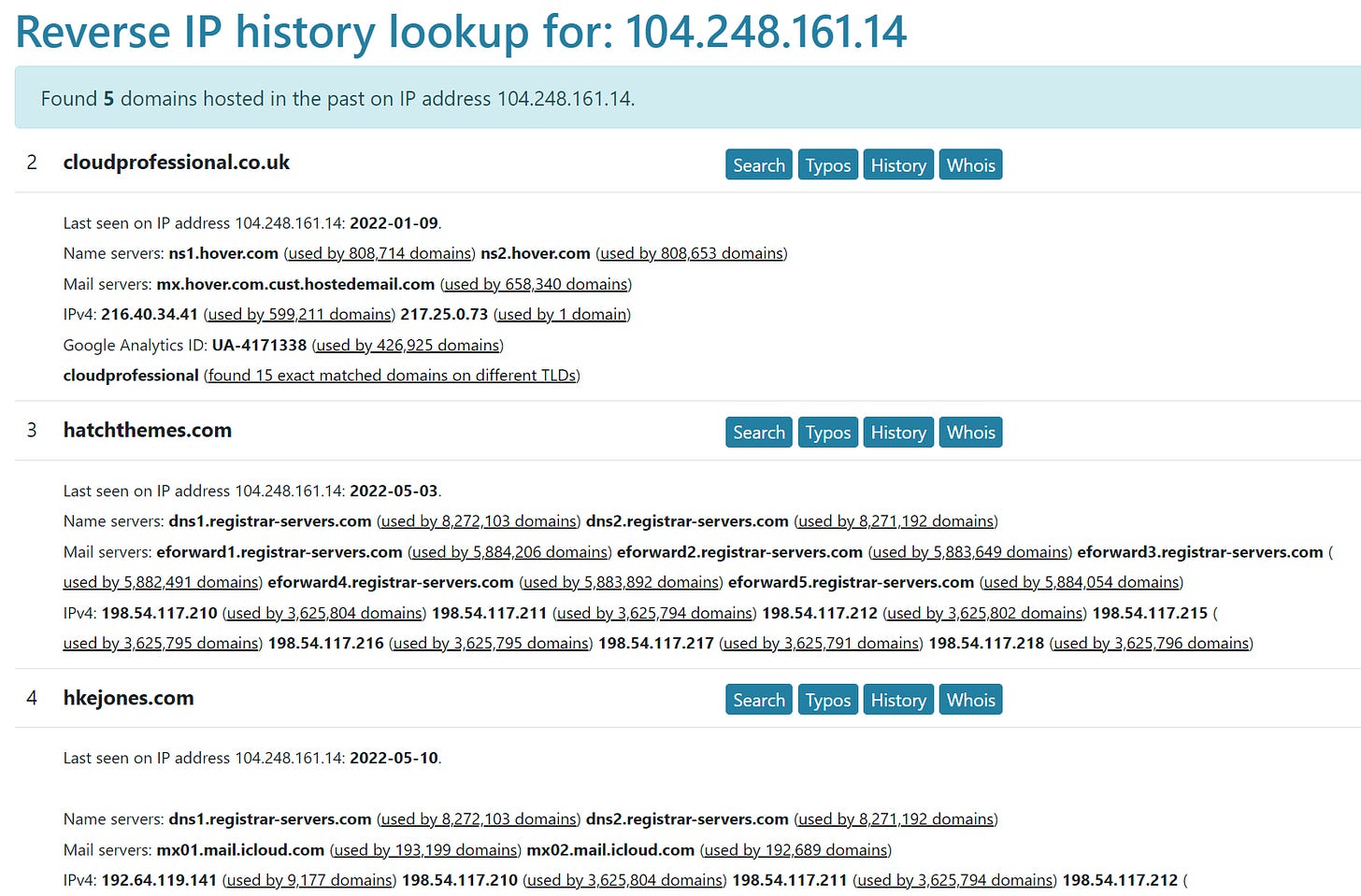
These domains appear to be hosted by commercial services that host thousands of domains, with one exception - 104.248.161.14. This IP has historically hosted only 5 domains - all of which are now down.
We could try to pivot on these as well and try to determine any historic connection, but that’s beyond the scope of this post.
If we attempt to access the second result, Powerposts(.)online, we get an automatic redirect to the Ukraine Inc domain. There are no results for the domain also in archive.org or in several search engine caches that I checked.
We can look first at its WHOIS records, showing that it was created in early February, 2023, and is registered to Maharashtra, India. So far, very French.
We can query Powerposts(.)online via DNSLytics’ reverse IP query, retrieving an additional 69 domains hosted on the same IP address.
If we query that IP address via DNSLytics, Shodan, Censys or any other tool, we’ll see that it’s an IP owned by the Russian hosting service Aeza.
If we look up Aeza we can easily find their domain, Aeza(.)net. At first glance, it appears to be a normal hosting service - and it may well be. However, there are some odd things happening with its host IP address, which hosts an additional suspect site that redirects to the main domain.
I’m not sure why this is the case, but this certainly provides strong evidence that the site is probably run by Russians - there’s almost no reason for French animators to utilize Russian hosting services.
The last thing to take a look at here is the domain mentioned in the Facebook ads themselves: thejantzes(.)com. The site also appears to be inaccessible, and also has a dearth of information available about it online. I haven’t had the time to delve deeply into it, but I will discuss a few of the initial findings below.
The domain was registered under DDoSguard RU, an infamous Russian service that we’ve discussed in the past on this blog. This probably indicates that the origin of this site is in fact Russian - further evidence that Russia is behind the Ukraine-Inc cartoon (not that it’s at all surprising).
Historic DNS records show that the site has been active for years:
Looking up the domain’s SSL certificate via the Facebook Certificate Transparency Tool identifies some certificates in the past for sites that themselves are down.
While I haven’t spent much time delving into this site, it appears to be less interesting. I’m not quite sure why it was included.
Let’s summarize our findings so far:
From one ad, we now have:
A Facebook page
Additional ads
The origin domain
Several other domains that are tied to the target domain
IP addresses
Indicators that the target site is in fact probably Russian
Let’s see if we can identify coordinated activity promoting this domain via search engines.
Google filters its search results to avoid promoting identified disinformation content, engines such as Bing, DuckDuckGo and Yahoo do so to a lesser degree. Yandex and some others have functionally no filter. PublicWWW is also functionally unfiltered, making it an even better search engine in some cases than the above.
Searching via Google:
We can further refine our search with quotation marks as well, but the results are overall underwhelming:
Yandex results are much better, unsurprisingly. and don’t filter out Russian disinformation content:
The first thing we see is a potentially related Telegram account, which links to other entities on Odysee, VKontakte and the domain. The accounts are pretty small and ineffective, so let’s leave them alone for now.
What’s more interesting are the repetitive posts from different entities, including from the illustrious Russia-affiliated News Front site. We could search that text, but It’s not quite as universal in its phrasing as I’d like, so let’s try to find another example.
For that, we’ll go back to PublicWWW, and instead of searching it for a domain, this time we’ll search it for “Ukraine Inc” as a keyword string.
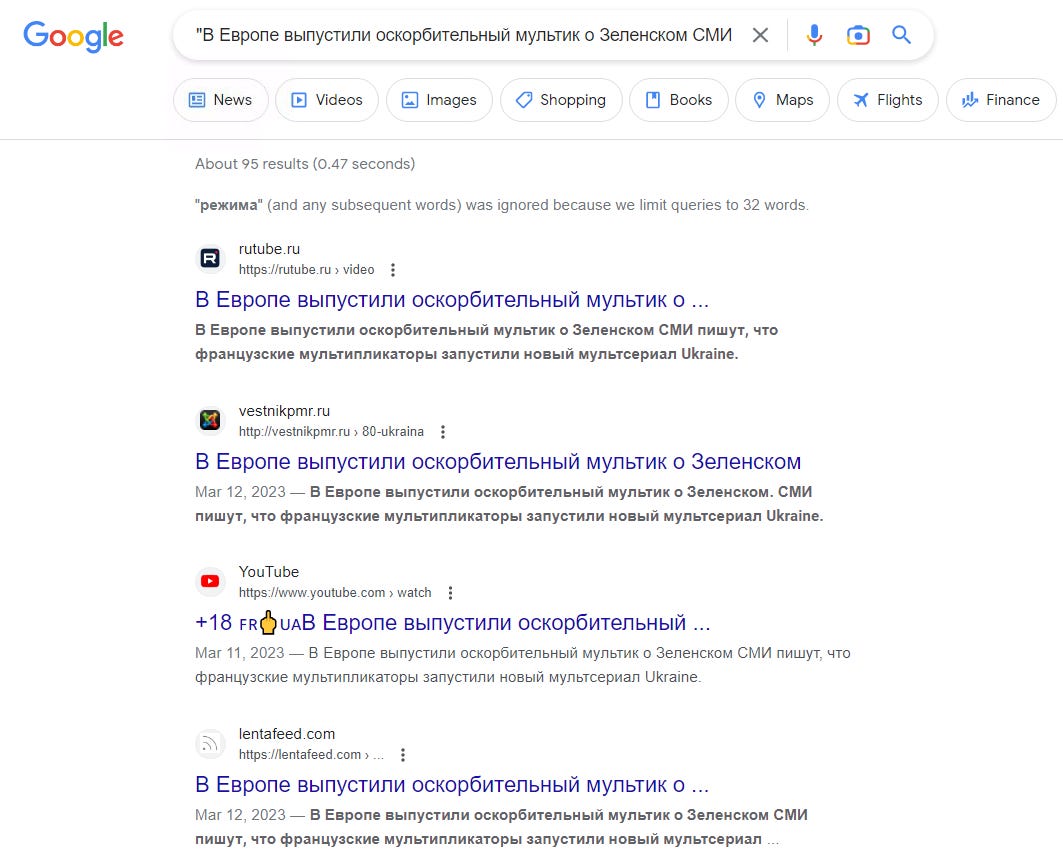
Here we see a number of forums and Russian domains that refer to Ukraine Inc as a keyword string in their source code. This is also a promising lead for us to investigate, let’s take a look at the sources - my apologies for the small text, I’ll post the text content below.
“СМИ пишут, что французские мультипликаторы запустили новый мультсериал Ukraine. Inc, в котором президент "незалежной" Владимир Зеленский стал главным героем. В мультфильме отражены мрачные реалии политического режима на Украине. Зеленский ради повышения собственного рейтинга и приумножения финансового капитала, как показано в мультике (в 1 серии), кидает в мясорубку свой народ. На убой отправляются все без исключения: мужчины, женщины, дети и старики.”
As translated by DeepL: “The media say that French cartoonists have launched a new animated series Ukraine. Inc, in which the president of Ukraine, Volodymyr Zelenskyy, became the main character. The cartoon reflects the grim realities of the political regime in Ukraine. Zelensky, as shown in the cartoon (in the first episode), throws his people into a meat grinder in order to increase his own rating and increase his financial capital. Without exception, all men, women, children and the elderly are sent to the slaughter.”
Both of the above sources have shared the exact same text - this is a good sign that it’s indicative content that we can search. Searching it in Google, the results are immediately apparent: the exact same text has been shared across a variety of platforms on similar dates.
At this point, we’ve completed the first stage of this investigation. From here, we could:
Investigate the network of online assets promoting the domain
Investigate any entities named Ukraine Inc. that may be affiliated officially with the network
Pivot on other indicative network content or posts
Expand our sources based upon this input
Report the network
Pay for premium domain historical lookups
I hope that you found this guide useful! If you look into this and find something, let me know at ari@glowstickintel.com or via LinkedIn.
Now that we’ve completed the long-form guide above, let’s discuss the IO/interference related events of the past week:
Make Love, Not Warcraft
In unsurprising news, Microsoft President Bradford Smith informed the public that Russian government agencies and their on-again, off-again affiliate the Wagner group have begun to infiltrate gaming communities online.
Source https://twitter.com/semafor/status/1646174094562402304
Videogame platforms are no novices in the world of covert operations, espionage and disinformation. As such, they play a crucial role as well in investigations - be it Aric Toler identifying the Discord leaker via his Steam account or Intrusion Truth identifying a Chinese hacker also via his Steam account. Being familiar with and thus being able to investigate these platforms will only become more important as time goes on.
Capabilities to more effectively investigate videogame platforms also would help us right now with gauging the impact of the Discord leaks.
There are still many, many unanswered questions about the Discord leaks, but the one most interesting, to me at least, is the amount to which any were altered beyond what we already know. The documents certainly originated as authentic, and reporting from the Washington Post now shows that about half of the members of the patient-zero Discord server were in fact non-US citizens.
Source:https://twitter.com/PaulaChertok/status/1646589359515394048
Individuals originating from Russia and “Eastern-Bloc” countries in fact expressed the most interest in these leaked documents.
Where they went from there - who knows. We do know that there has certainly been ample time to forge, manipulate or tamper with the documents.
Lin(Ken)din
The Australian Federal Police announced the arrest and charging of an Australian citizen with foreign interference offenses. This is a big deal as it’s the second arrest of an Australian under these charges following the formation of ASIO’s new taskforce to counter foreign interference.
Let’s summarize this in bullet points:
The individual operates a business overseas.
The arrested individual was approached by another individual who claimed to work at a think tank via “social media”.
The individual who purported to work at a think tank organized a trip for the arrested individual to meet his affiliates.
These affiliates, “Ken” and “Evelyn” - shame it isn’t Barbie - are alleged to work for a foreign intelligence service.
Ken and Evelyn requested that the arrested individual gather information and prepare reports on Australian national security affairs, including apparently other countries.
Source: https://www.afp.gov.au/news-media/media-releases/australian-man-charged-foreign-interference
Sound familiar? There have been numerous cases of the same modus operandi being used primarily by China in the past. The Straits Times published an in-depth article on a recent case utilizing inauthentic Singaporean accounts. Other historical cases abound as well.
While writing this, the Reuters published the name of the arrested individual, confirming that he is in fact an Australian arrested upon his return from China. According to the article, Alexander Csergo, 55, a “digital and data marketing consultant” was arrested upon returning from China, where he has lived for the past 10+ years.
That’s it for this week’s MWW - feel free to reach out with any questions or comments to ari@glowstickintel.com, or via LinkedIn.