Aeza Antics
Welcome to Memetic Warfare.
Firstly, we’re going to start with an interesting update to the Cyber Isnaad Front. Following our latest coverage of the group, they’ve since launched a Twitter account for their masked spokesperson, replete with a call supporting Mohammad Deif, the former number 2 of Hamas in Gaza - certainly an interesting move as they double down on the human element here:
They’ve also posted doxxing documents and new, unclassified material from an Israeli Ministry of Defense acquisitions and purchasing portal, very similarly to the “CyberCourt” operation which did the exact same thing.
This week we’re going to cover a ton of different things briefly in a bit of a newsletter-style, then conclude with a longer discussion of CheckFirst’s latest report.
We’ll start with a recent podcast that I did with Max Lesser, hosted by OSINT UK, on one of our past reports on Iranian IO targeting the US elections, and in this case the UK section in particular - see below:
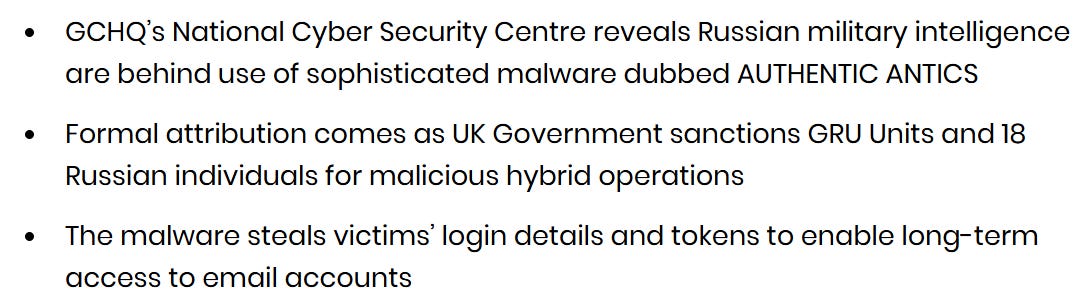
In other UK news, the UK has decided to announce stylized sanctions on multiple known Russian hybrid warfare units:
The StratComs element here is interesting and reminiscent of how the French sanctioned APT 28 - shows that there’s a flair for visual styling and messaging here beyond the sanctioning itself.
The NCSC also published a report on new malware from APT 28 and their analysis of it:
The report itself is technical and a little dry:
So, while there isn’t much new here as these units have already been exposed, it’s nice to see both the UK and France lean into a holistic approach to push back, though it remains to be seen if this will actually impact anything.
Going back to Iran, Max and the team at the FDD have been putting out great stuff on Iran, including:
A look at an Iranian operation using crowdsourcing to target Israel and Saudi Aramco apparently.
A former Iranian state media employee running an overt influence operation called “Iran Hayom” (Iran Today, a play on the Israeli newspaper Israel Hayom) that sprang up during the war.
Moving on there, two more things that I want to point out:
Let’s Encrypt is now issuing IP address certificates - will be very useful and interesting for pivoting and I hope to use it soon in investigations.
The EU has taken significant action against the hacktivist front NoName05716, which has interfered in past EU elections and targeted other European victims.
The US has sanctioned Aeza, a well-known Russian bulletproof hosting firm that has provided infra for Russian, Iranian and other cyber/IO threat actors. It’s great to see them designate a front company in the UK (known to be highly porous) for sanctions, and also doubling down on targeting the key infra that really powers hostile operations.
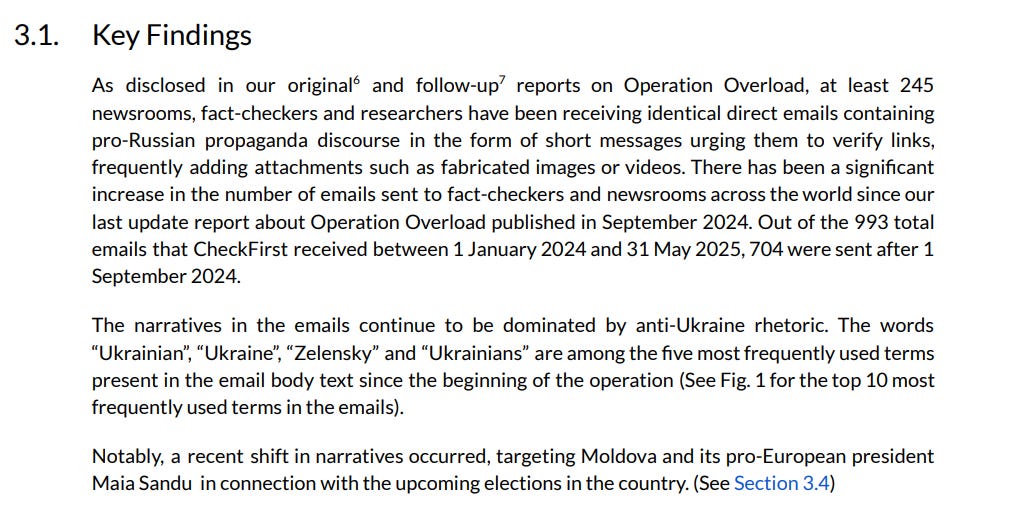
The next thing that we’ll look at is CheckFirst’s latest report on Operation Overload, available here. This is a very long update (130+ pages) on an operation that we’ve covered here, so we’ll only look at a few specific points. First, the executive summary:
For the most part, what we’d expect - just more emails, more AI use, BlueSky and TikTok and that’s about it - which is fine.
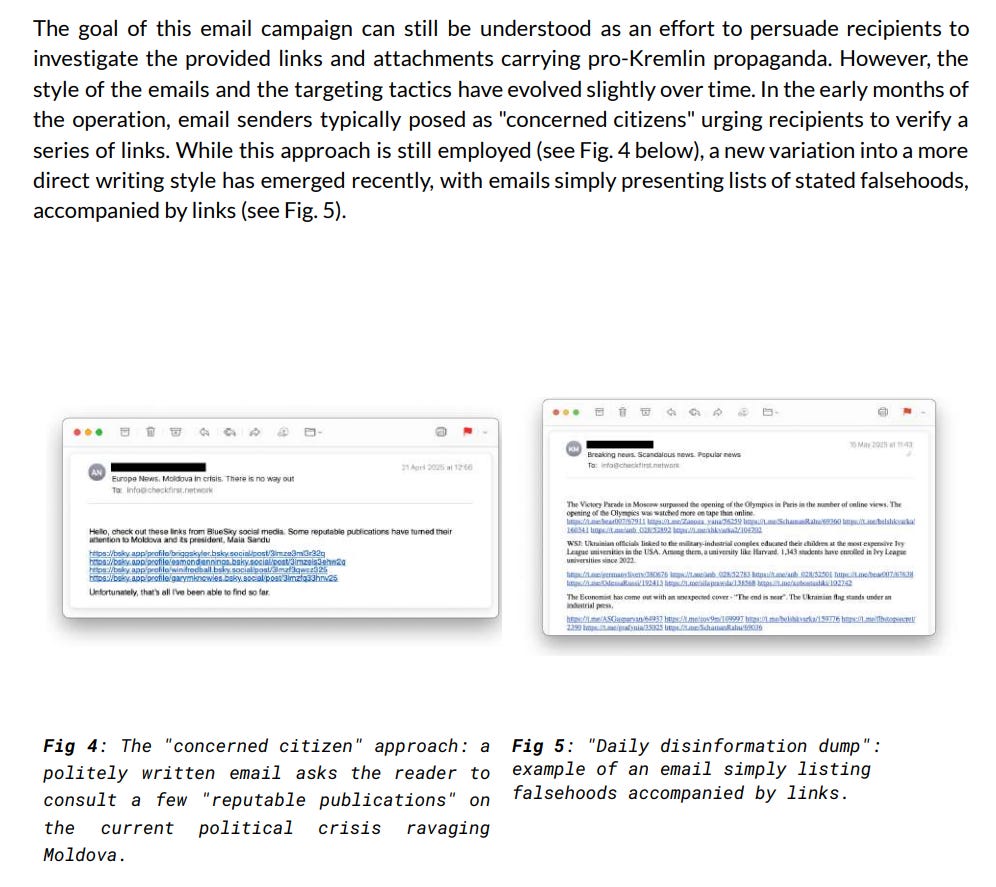
The report goes full in on TTPs, which I still have a hard time taking seriously:
Emailing journalists and fact checkers directly is by far the most interesting part of the whole operation:
We see some more examples here, including types:
While I like CheckFirst a lot, they fell for the useless graph meme that I can’t stand:
They also track posts across Telegram by user signature, which isn’t something commonly discussed:
There’s much, much more, so give it a read.
That’s it for this week!