Where is my mind colonization?
Welcome to Memetic Warfare.
I’d like to kick this week off with a shoutout to Max Lesser and Maria Riofrio who published an excellent investigation into a Chinese espionage operation available here.
A quick summary:
There’s a bit of everything in this report, so check it out - email resolution, domain analysis, Craigslist and much more.
Also, this is a super hot topic and one that we’re getting a better look at. For years, people thought of Chinese espionage as just people approaching other people on LinkedIn, but there’s much broader infrastructure out there if you know where to look, as Max and Maria do.
We’ll also look at some other fun Chinese activity here, with a new article from Xinhua calling out US “Mind Colonization”.
This is interesting for a few reasons. Firstly, it aligns with recent Chinese strategic IO as we’ve discussed here many times regarding cyber attribution. Chinese actors are increasingly investing in long-form, high-investment reports from think tanks and other front groups to push narratives, such as the CVERC in the past. As always, these reports are a case study in deflection - accusing the US of doing what China is actually doing (not that the US doesn’t run influence operations also, of course).
In this case,the “Xinhua Institute” think tank held the “Global South Media and Think Tank Forum” to promote the report, inviting international guests:
The text says more or less what you’d expect, in the style that you’d expect, and it’s available here if you want to read it. The report is about 30 pages long and very lightly researched, with only a few references throughout it to other publications, mostly Chinese.
The grammar and spelling is at least good, though the content is unsurprisingly derivative. What stood out to me was the acknowledgements section, in which we learn that the turnaround time for this was about half a year and that groups such as the PLA and Chinese Academy of Sciences contributed.
The true standout organization here is the China Institute of Contemporary International Relations, which is a well-known MSS-affiliated think tank.
Lastly, it’s interesting to see this approach broaden. If China started this type of long-form report writing and strategic IO work with cyber attribution, it’s now expanding to the counter-IO space, and who knows where else from there.
We’ll take a look at a different part of Asia now, heading south. Recorded Future recently published an excellent and unique look at the recent mini-war between India and Pakistan, available here.
The report is unique for a few reasons. Firstly, we simply do not see enough coverage of this region. Secondly, it covers IO activity specifically during wartime, another topic we don’t see enough coverage of usually.
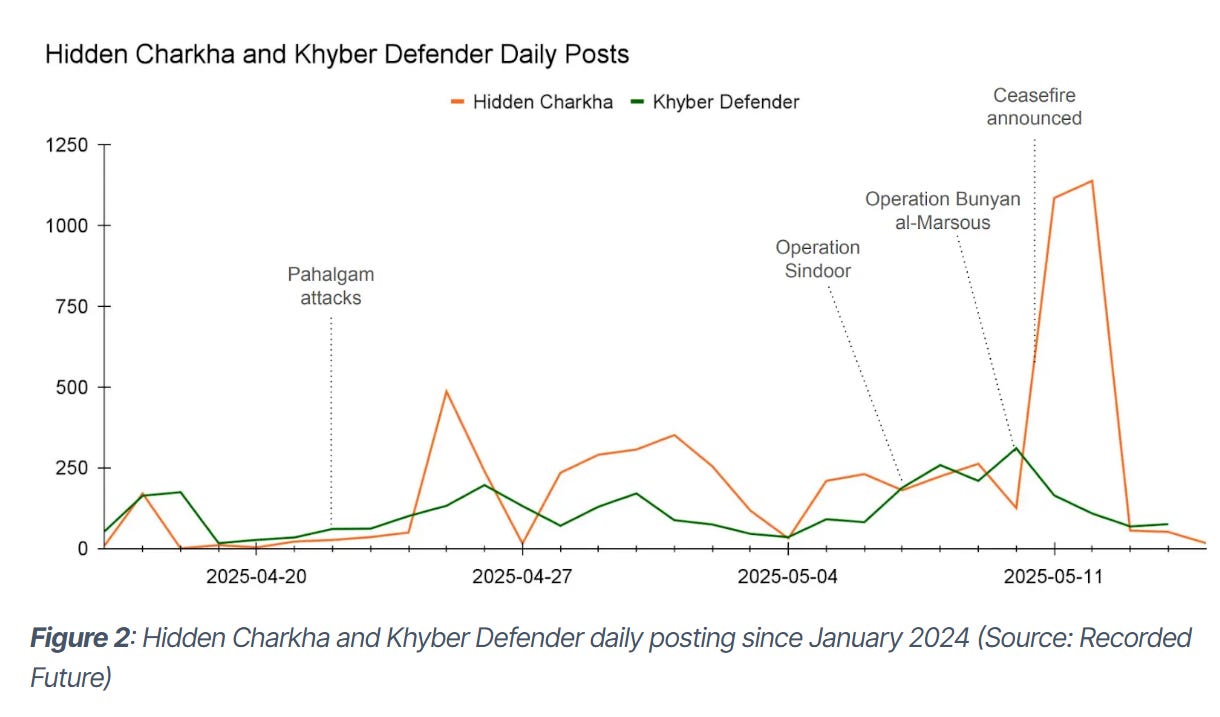
Lastly, it looks at operations from both sides, Hidden Charkha and Khyber Defender:
We have the typical collection timeline from these reports, which is almost legally mandated. Recorded Future deserves a shoutout for doing solid collection as well as timing them with real-world activity.
Some things never change though - threat actors will always use low-effort memery.
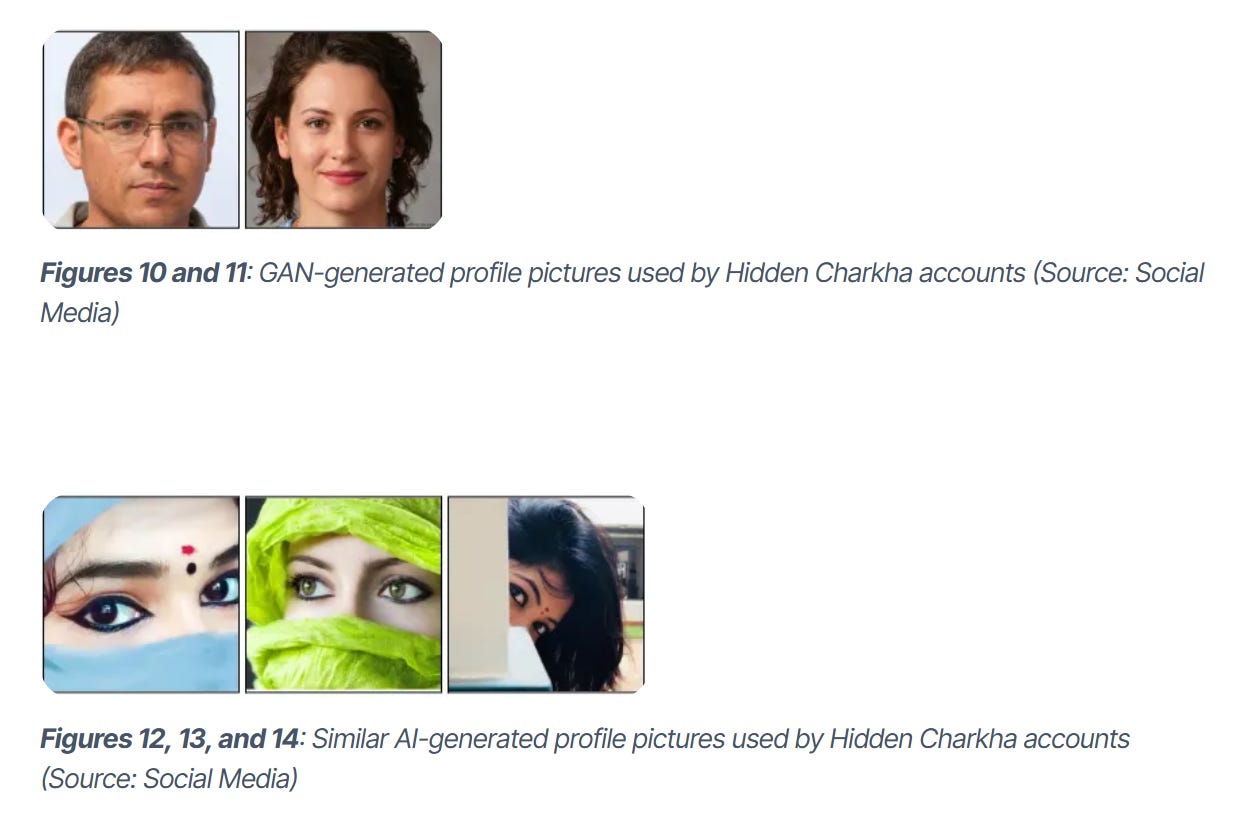
I also noticed that the use of AI face-covered individuals is slightly more convincing than the stock GAN image:
Attribution here also seems straightforward:
Attribution also includes ties to groups that crowdsource activity. This is a dynamic that we’ve also seen in Iran, with people semi-affiliated with a given state getting into the IO game.
One of the many great things about this report is that it ties online activity to IRL activity:
Another interesting point was the use of forged documents, a tactic increasingly adopted by actors globally:
As a final note for anyone who doesn’t get enough of me here, I recently joined a webinar at WikiStrat on IO - see below.
That’s it for this week!