Three Election Threat Vector Problem
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also do training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
This week we’ll look at Google’s new report on election security and then take a look at the current state of American IO capabilities.
Let’s begin with the Google report:
Those looking for a great overview of big 3 threat actor hybrid IO activity should check out “Poll Vaulting”, Google Cloud’s new report on election security.
The report focuses on past activity, TTPs and more while looking forward to the maelstrom of elections that 2024 seems to be.
As an aside, the report really is great despite my few points about it, and I’m always beyond excited to see quality discussion of IO/Cyber and their confluence.
I’ll put the executive summary here for those who can’t be bothered:
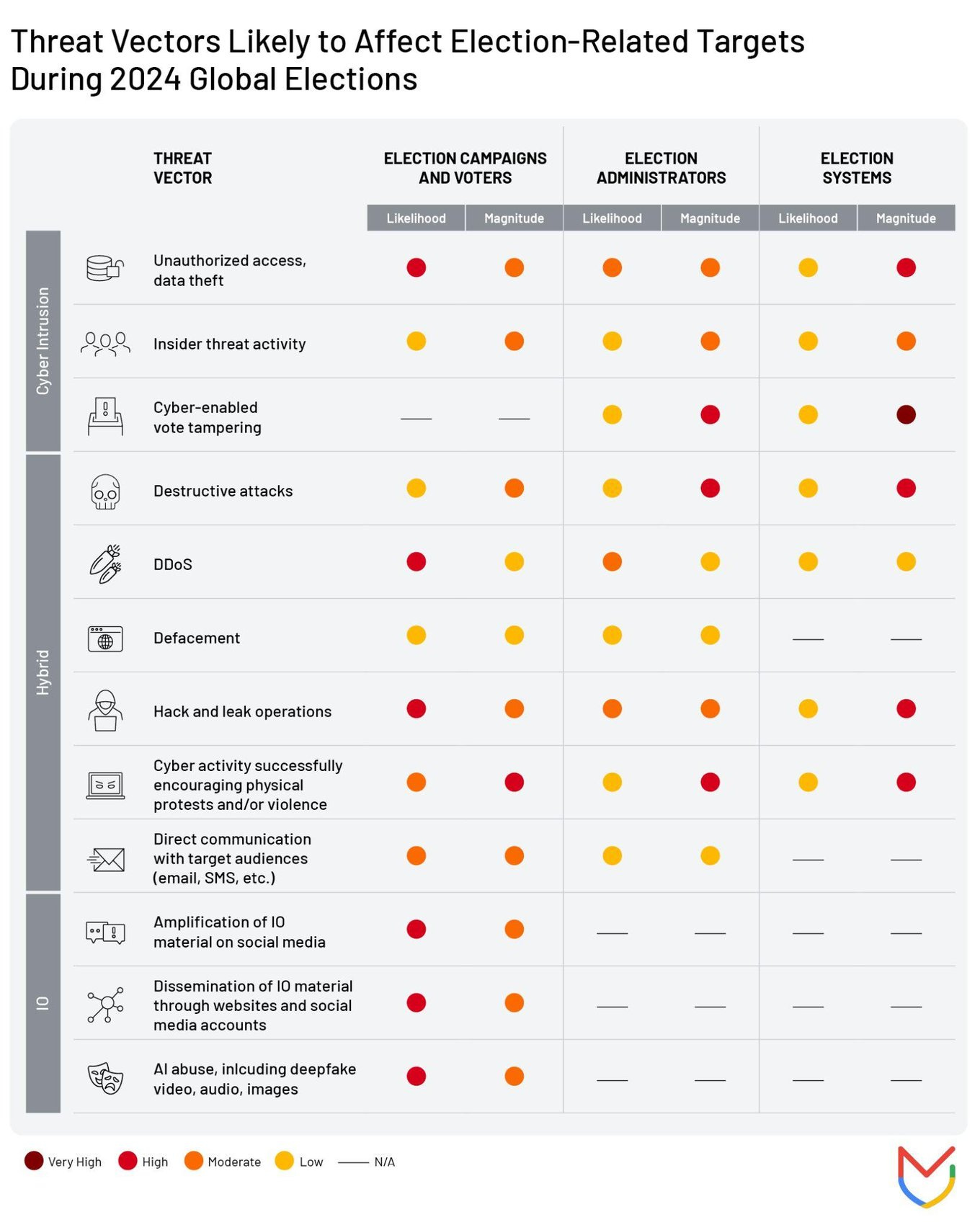
Let’s review the report. I’m not one to be overly scientific in the way I view IO, but I do like how they broke it down to election campaigns and voters, administrators and systems alongside the triptych of “Cyber intrusion”, “hybrid” and “IO” categories.
The TTPs are also solid, but I’d have liked to see a bit more specificity in a few of them. Where does, for example, the recent case of a Czech news site being hacked and publishing disinformation regarding the attempted assassination of the Slovakian president fall, defacement? Amplification of IO material on social media? Where would ATO fall?
For elections, in my opinion, there’s room for highly-specific TTPs. The report excels in driving home the centrality of hybrid operations:
The holistic perspective is also refreshing. Why limit our perception of IO to state actors when it’s empowered by the broader cyber ecosystem?
One thing I would add here is that some of these actors are one and the same, at least sometimes. A state-sponsored actor can run a hacktivist front, as well as be active in the criminal underground.
Mandiant’s findings on protests in the US are noteworthy in that they’re an “escalation in tactics” by Chinese actors, but of course ineffective. Anyone who’s been outside of the White House knows that one can find protests of any kind there on a daily basis.
In this case I’m sharing the screenshot simply because the actual protest banners are hysterical. Look at banner, Michael!
There’s also level-headed discussion of the actual goals here. Election interference is the leading case of “perception-hacking” in IO:
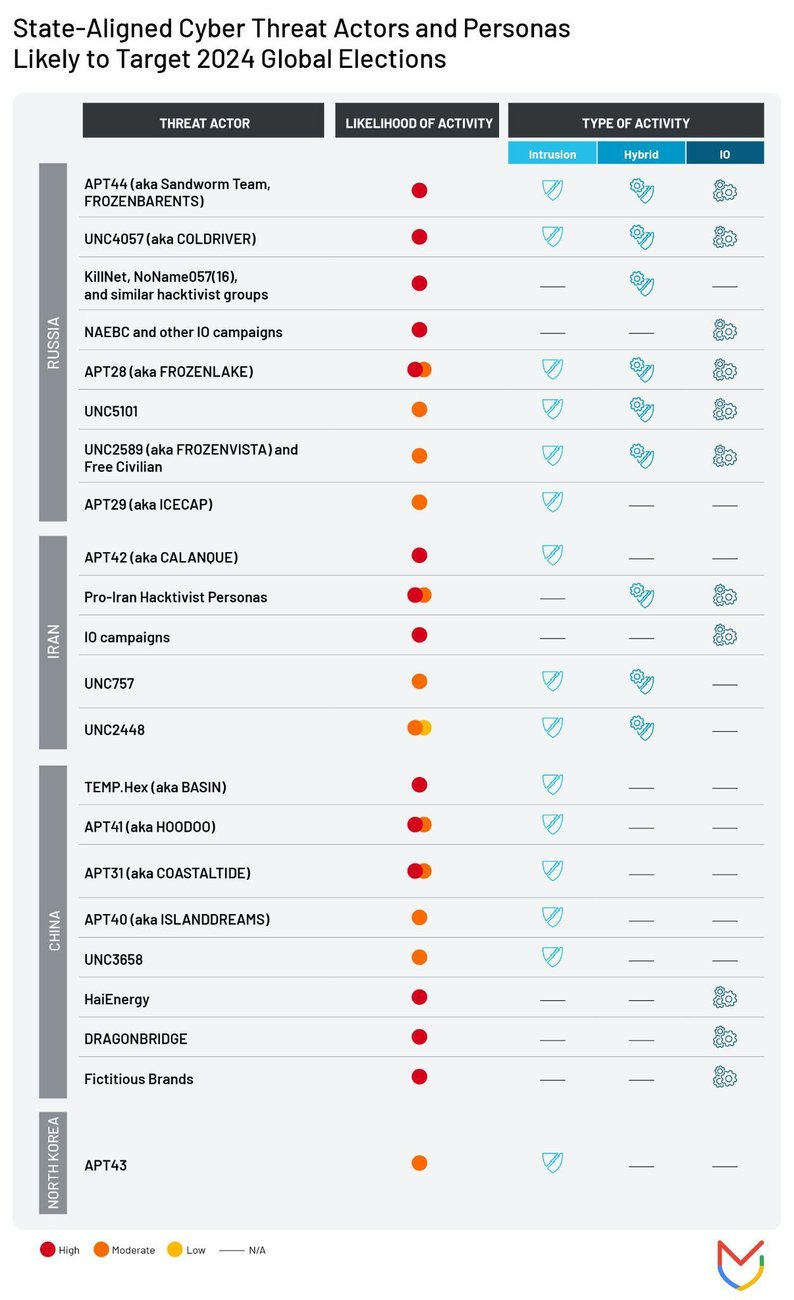
At this point, the report moves to covering the big 3, breaking down the main actors. The likelihood of activity is a bit funny as almost everything is moderate risk at minimum, but we’ll leave that aside.
While I’m not opposed to this sort of modeling per se, this is a bit limited in my opinion. We’re still focused on high-level discussion of key entities, such as “Pro-Iran hacktivist personas” that may be far more critical for certain parts of the world than say Haixun.
Additionally, other, smaller or otherwise currently unlisted state-sponsored actors may have been worth including. States like Cuba, Venezuela, Belarus and even semi-state actors like Hizballah are obviously not as impactful as the big 3, but probably worth mentioning regardless.
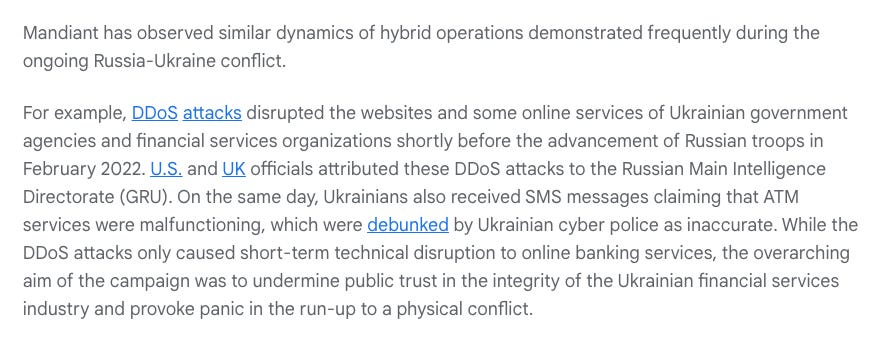
Mandiant then assesses that Russia will be the great risk to elections in the US, EU and UK, which may well be the case:
Russia may still be number one, but I’d be willing to bet that Iran will punch above its weight this year considering the ongoing war in Gaza and general instability in the ME. If Iranian activity in Israel is any indicator, there may also be a significant uptick in Iranian activity in the US/EU as apparently Iran continues to invest heavily in IO.
On China, the main talking points are all hit: generative AI, “nuanced” tactics, forged/falsified materials and so on. In my opinion the increasing willingness to use falsified content, especially in conjunction with generative AI, is the real development in Chinese activity in the past year:
With forgeries comes seeding, as readers of this blog will remember, suspected Chinese actors seeded hacking forums with forgeries:
I’ll finish this section up with the conclusion.
Influence is a rough business. Chinese activity didn’t noticeably impact the Taiwanese election, and as the space develops, it’ll only get harder.
Some points that I’d like to have seen brought up alongside the IO/Cyber spectrum:
Additional hybrid methods described more specifically, such as ATO as done by Ghostwriter and others.
A discussion of platform dynamics as risk vectors - messaging applications, short-form video, audio platforms and so on beyond traditional coverage of Facebook, Twitter and so on.
A slightly more global overview.
Having said that, the report is very, very solid as a primer and review and I’d recommend reading it.
Doomscrollers Wanted
We’ll finish off with some development of note regarding the US military’s 4th Psychological Operations Group and psyops in the US military in general.
This group has developed a reputation for some edgy/well-produced social media content, starting with their famous “Ghost in the Machine: Psywar” video, available here.
This video is a “psyop” in of itself, in addition to being a recruiting video, and I always enjoy bringing it up whenever training on IO to discuss the multi-layered use of any publicly posted content, at least from official actors. Watch it yourself and see what you think of what’s being insinuated here about American activity regarding protest movements in adversarial countries.
The group’s Instagram account put out 3 new short videos recently, titled “Conditioning”, “Time”, and lastly - “Belief”. Take a look at them below:
Conditioning:
Time:
Belief:
These are a bit shorter and seem more oriented towards “just” recruiting Americans by showing them some cool videos about how “psyops” work. The timing couldn’t be better, as a recent DOD report showed that “MISO”- Military Information Support Operations - is a greatly understaffed field, with only 25 percent of the captain-rank officers required.
The inability to directly recruit to psyops seems to be a big issue, but other issues are equally important. For example, not having carried out any auditing or assessments in the past 20 years seems to be problematic. Not like there’ve been any serious changes or developments in the world of IO in the past 20 years, right?
The recommendation section has some content worth noting as well. The first recommendation is a given:
It starts to get more interesting in the second recommendation.
The restructuring proposed above seems to be necessary, but again, not my area of expertise.
Some correspondence referred to shows a new structure, indicating that a more integrated capacity here will be spread throughout the US force command structure, including a Joint Force Influence component but interestingly divorced from the cyber component:
So, the recruitment drive continues in full force despite American IO capabilities being understaffed. Hopefully they manage to fix these issues and get some young doomscrollers in there fast!