The Mauve Cyb3rAv3nger
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also do training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
I usually don’t spend so much time on Israel-related activity, but as is said in Hebrew, so fate desired.
Recently, I came across what appears to be another potentially Iranian influence operation targeting Israel after a friend informed me that he had seen advertisements for a suspicious domain on social media sites. Let’s take a look at the promoted domain, dofek(.)tv, which appears at first glance to be an Iranian influence operation.
The made some bold stylistic choices, including a very appealing shade of purple, perhaps a mauve. Make it work, designers!
We’ll come back to the domain soon, let’s look at its social media presence in the meantime - the logo also is interesting, appears to be some stylized form of a menorah?
Here we see YouTube, TikTok, Instagram, Twitter and Facebook. Let’s start with Facebook briefly.
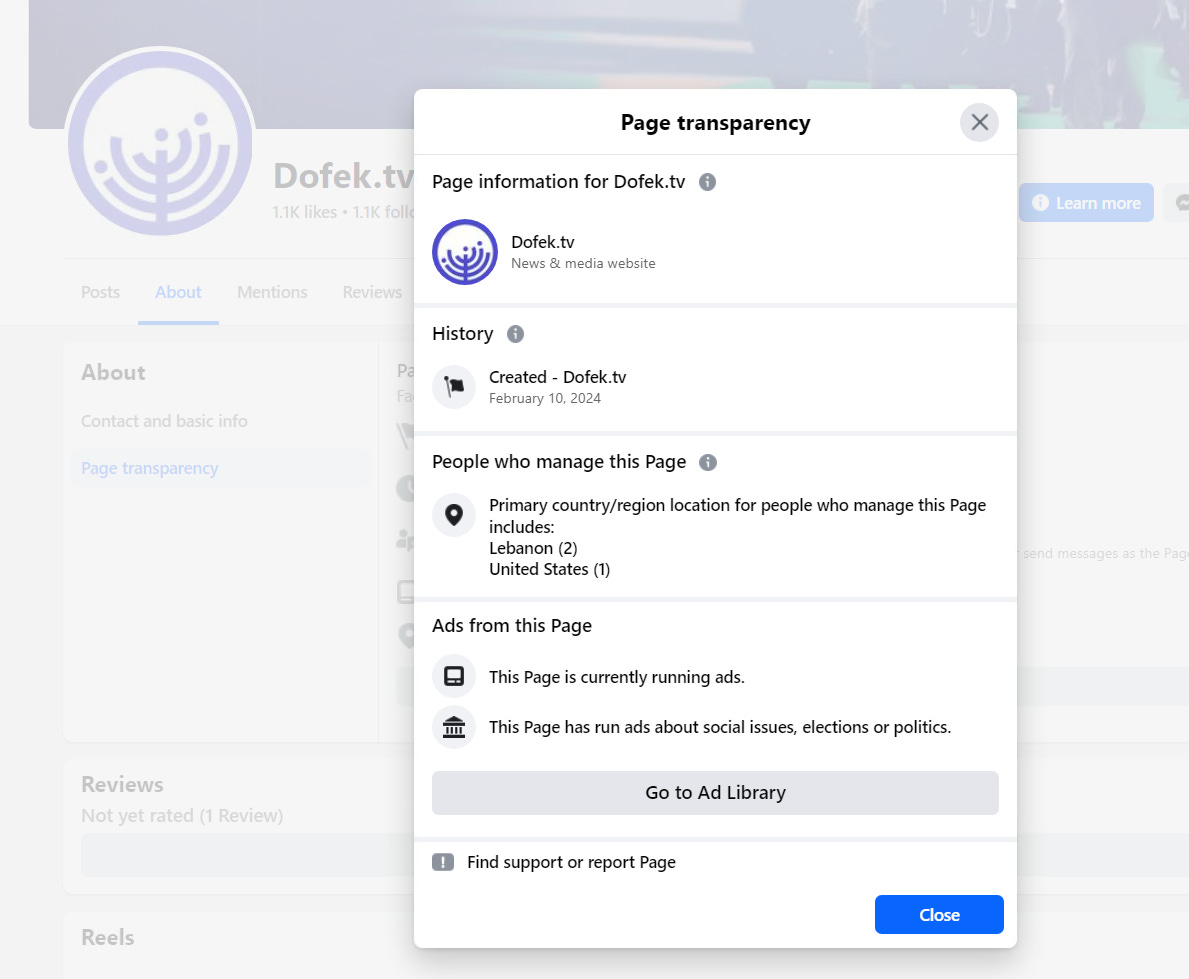
The Facebook page is pretty straightforward - when looking at pages, checking out the “page transparency” section is useful to see where the managers are based, the creation date and whether or not its running ads.
Amazingly, this is still a source of OpSec breaches:
Normal things here - why can’t this be automated? Would it be incredibly difficult to flag pages that have a location discrepancy with the main language of content published by a given page?
From there, we can see that it’s not only currently running ads, but has run ads about social issues, elections and politics. Let’s click on the Ad Library to see what’s up:
So four ads have been run on Instagram and Facebook, with one being flagged as having run without a required disclaimer. This also gives us insight into the budget and other information:
Yawn. Shows that they’ve managed to run ads, unimpressive numbers/sums, and paid in dollars.
The posts garner some small amounts of engagement:
There’re noticeable differences in engagement for posts, could be indicative of paid promotion or artificial amplification in some cases:
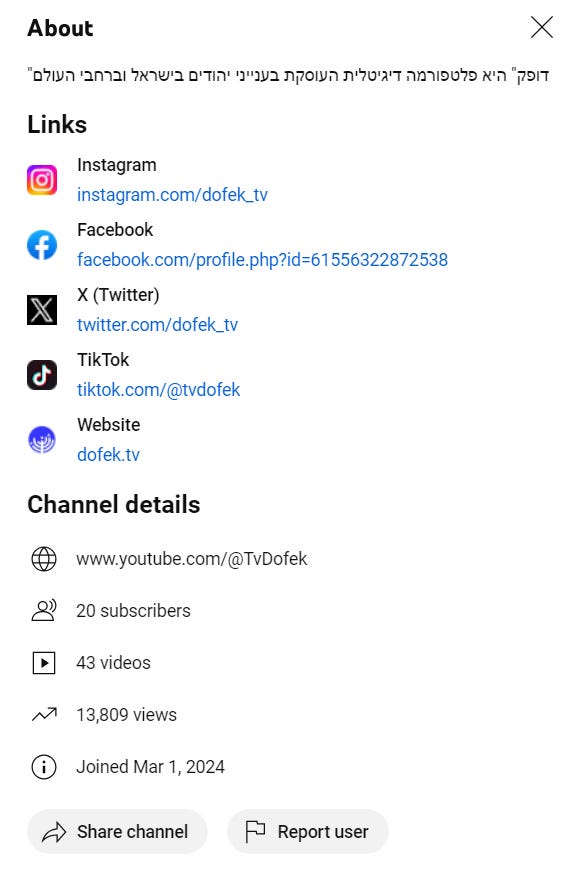
Let’s go to the YouTube channel. The about section provides some context on basic stats:
The channel has uploaded both videos and shorts:
Very few views:
Shorts get more views but still lacking:
Nothing else interesting was available in the account section (sometimes you can get an email address, creation date and so on if of interest), so let’s move on to Instagram.
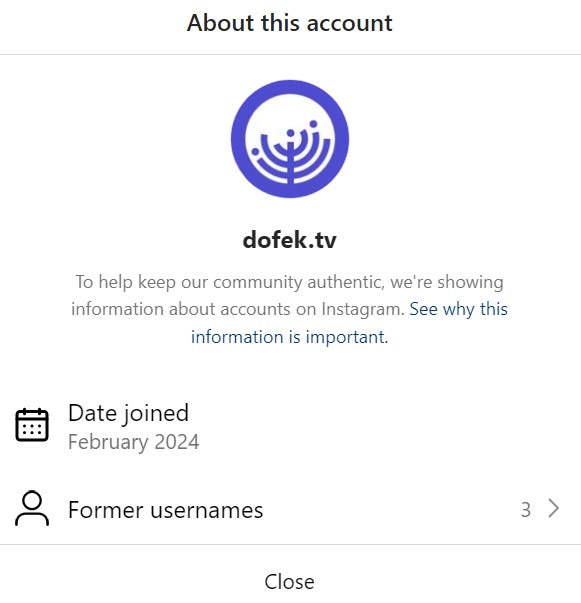
There have already been several name changes despite having joined on February 2024, the oldest one of the entities if my memory serves:
Interestingly, TikTok is the most underwhelming:
A zaap.bio page is also being used as a replacement for Linktree:
Let’s go back to the domain.
Overall, production values are pretty high with multiple types of content, with below an emphasis on “Posters and infographics”, presumably for easy sharing on platforms.
Even long-form video it seems is included:
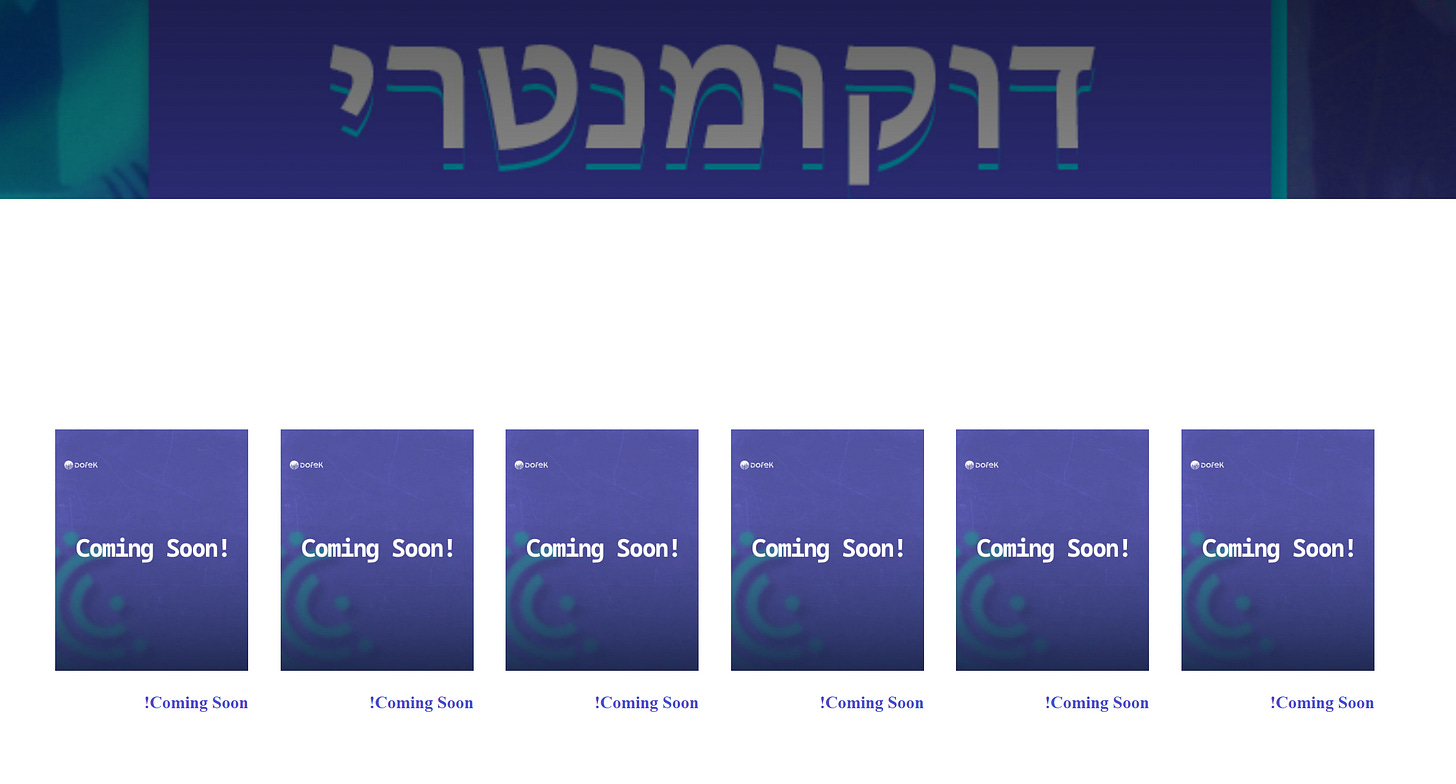
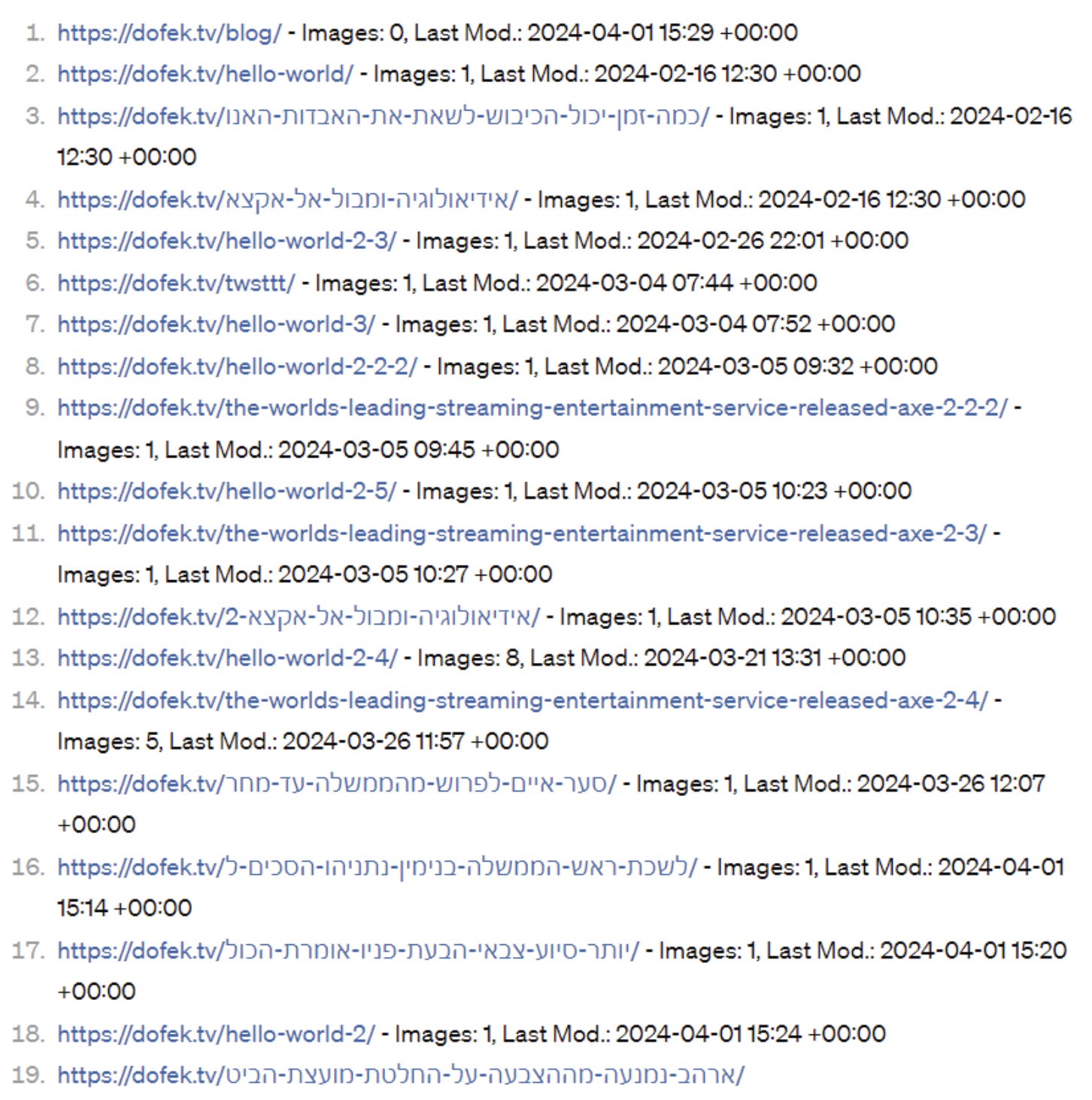
One fun trick that Ran Locar tweeted was the use of the sitemap to bypass the “Coming soon” locked content - see the “coming soon” locked sections below:
By accessing it via the sitemap as Ran did, we can see the content itself:
We can also decode those URLs to Hebrew. Below is a separate example of indicative content that I tweeted recently.
Beyond this stuff, the domain itself is locked down pretty effectively. The JSON of the WordPress is still open, showing that one of the authors is named “Fadel”, and there aren’t any trackers of note or other technical information available, so we can look at it in Crowdtangle, and then check out the hosting infrastructure.
A non-zero amount of shares, but very little engagement per share on Facebook. Looking at a few of the shares, they seem to be from real people, one of whom appears to be also a Corona denier, so probably best to take it in stride.
From here, let’s look at the hosting infrastructure (host, domain name, TLS certificate and so on).
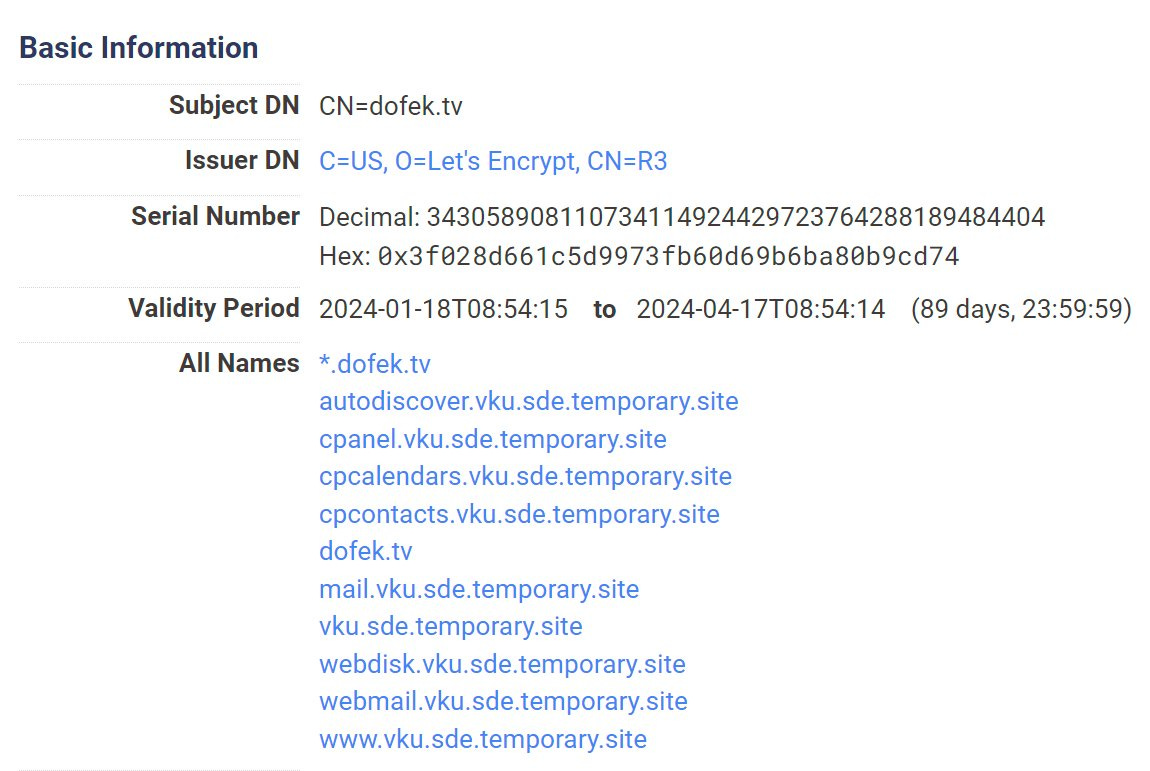
We can see that the domain appears to have been created by an outsourced firm based upon its subdomains and past hosting infrastructure. This is especially apparent when looking at the TLS certificate:
Here we see that the same certificate was used for various subdomains on the “temporary(.)site” domain. Looking into “temporary(.)site”, and by then checking out its host, we can see that it’s hosted by Network-Solutions-Hosting, and that it hosts primarily, but not exclusively, subdomains on the “temporary(.)site” domain.
Those interested can look into this further, but investigating it leads to an outsourced technical hosting/domain site. It isn’t that interesting beyond showing that the domain hosting and creation was originally outsourced/handled by an external service.
Other methods come up short - seems that this is a pretty invested-in domain, and shows more OpSec awareness than say Russian domains of late.
This, alongside recent other activity such as the Cyber Court and other hack and leaks, may be indicative of a sharp rise in the operational tempo of suspected Iranian threat actors.
As Microsoft has pointed out, Iran often turns to low-level but high-volume cyber-enabled influence operations, or in this case regular influence operations, to promote its goals.
This makes sense in the context of the ongoing war, and while still more context is needed to state whether the recent uptick in hack and leak/IO activity is an outlier or not, it’s something worth keeping an eye out for in the coming weeks. I also would add that the lack of a Telegram channel or Whatsapp group is an omission that I’m surprised to not come across considering past operations, and their popularity in Israel.
Notably, Iranian operations seem to be outperforming say their Russian counterparts in putting out reasonably high quality, targeted content, as well as maintaining (for the most part, FB page about section excluded) a higher level of OpSec. The Dofek domain and the Cyber Court all maintain higher degrees of OpSec awareness and are more securely created, for the most part, than most Doppelganger domains or otherwise.
Oftentimes those in the IO community miss the other threat actors for the Russian trees, and it’s important to keep in mind that Russian capabilities are often overstated whereas others are still, many times, underappreciated.
Next week, after a short delay, we’ll finally take a look at Microsoft’s latest report and talk about other topics beyond Iran/Israel.