The Guancha Menagerie
It's always sunny in Tianjin
Welcome to Memetic Warfare.
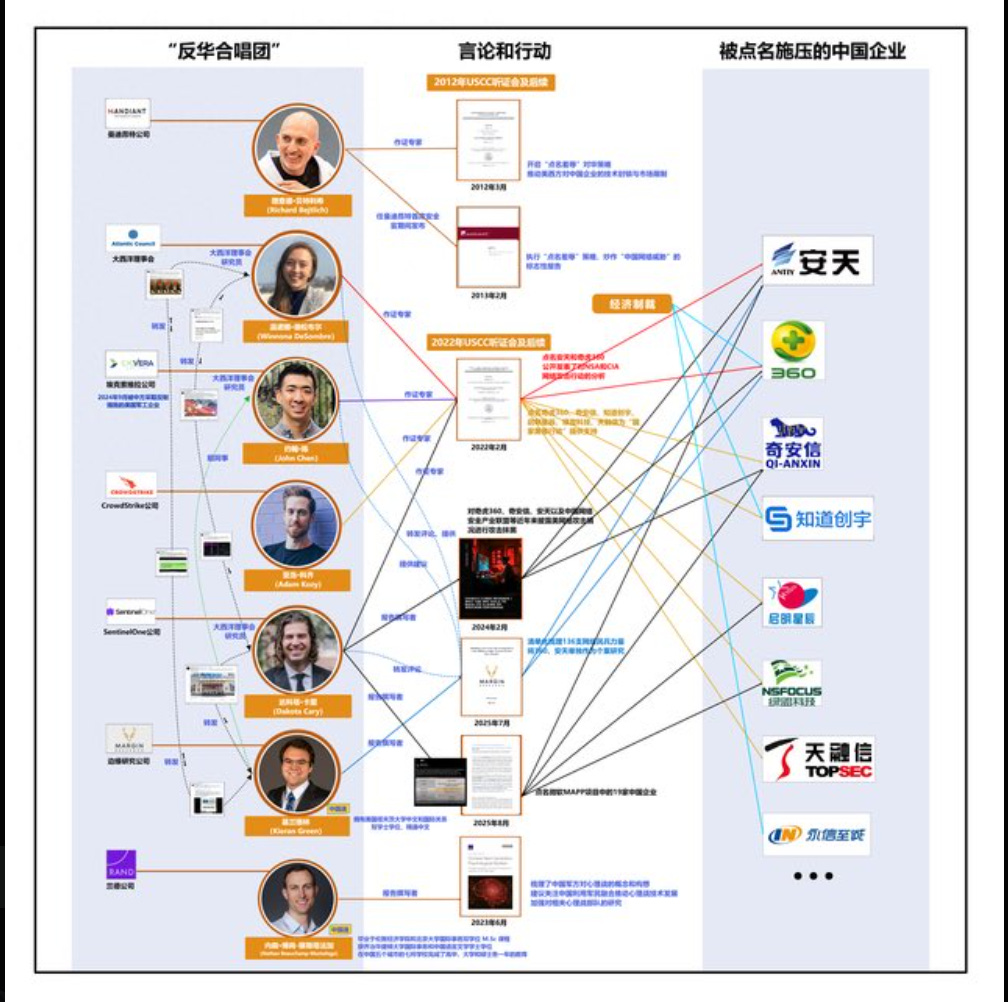
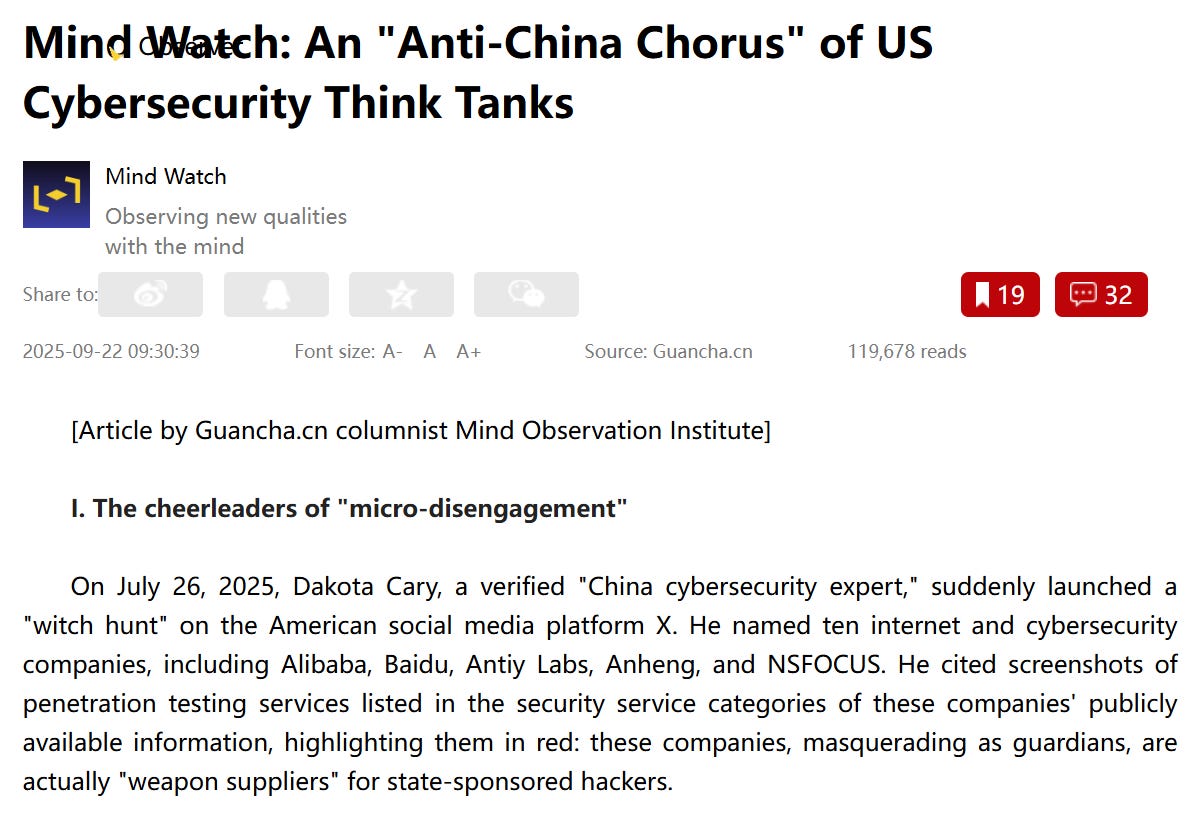
We’ll start off with a tweet from Dakota Cary, whose prediction that Chinese state media would publish a “hit list” on Western cyber analysts has seemingly come true. See below a graph from it:
I have to call out the use of the chart also, what is going on here. This type of chart belongs in the eventual Chinese adaptation of It’s Always Sunny in Philadelphia, which as per ChatGPT would apparently take place in Tianjin.
The article accompanying the graph was published on Guancha, calling these analysts (published seemingly in response to Cary’s past content) "cheerleaders of “micro-disengagement””.
Beyond just listing information regarding the analysts, the article also accuses Sentinel One of pushing Microsoft to kick China out of MAPP in order to win contracts - a highly similar narrative to past CVERC reports:
Section 5 then describes the background of what’s going on here - a “struggle” between Chinese and US CTI firms:
They break it down into three stages, the first being the exposure of alleged US operations and the Snowden leaks. Stage 2 began with the discovery of the “Equation Group”, the Kaspersky name for the NSA, presumably TAO if my memory doesn’t betray me. The article talks about how Antiy Labs apparently was the first to provide samples from some Equation group operations. The third phase refers to Chinese analysis of content from WikiLeaks, which IMO is a bit weird in its timing and phrasing here, but appears all of the time in Chinese cyber reporting. We even get a note referring to how the Chinese MFA builds on these and presents reports on these “phases” to the public:
The report describes the US as feeling the “threat of suppression” from Chinese companies, which incentivized the US to change its stance. The article then accuses SentinelOne of being a key actor in the US’ plot here to respond, referring to Cary’s report in 2024 which discussed how China essentially makes up a lot of its cyber attribution work. Dynamic aside, the best part here is the last sentence, accusing the US of having a logical process that is “typical of colonial-era aggressor arrogance, viewing the arduous resistance of the colonized, invaded and harmed as an original sin.”
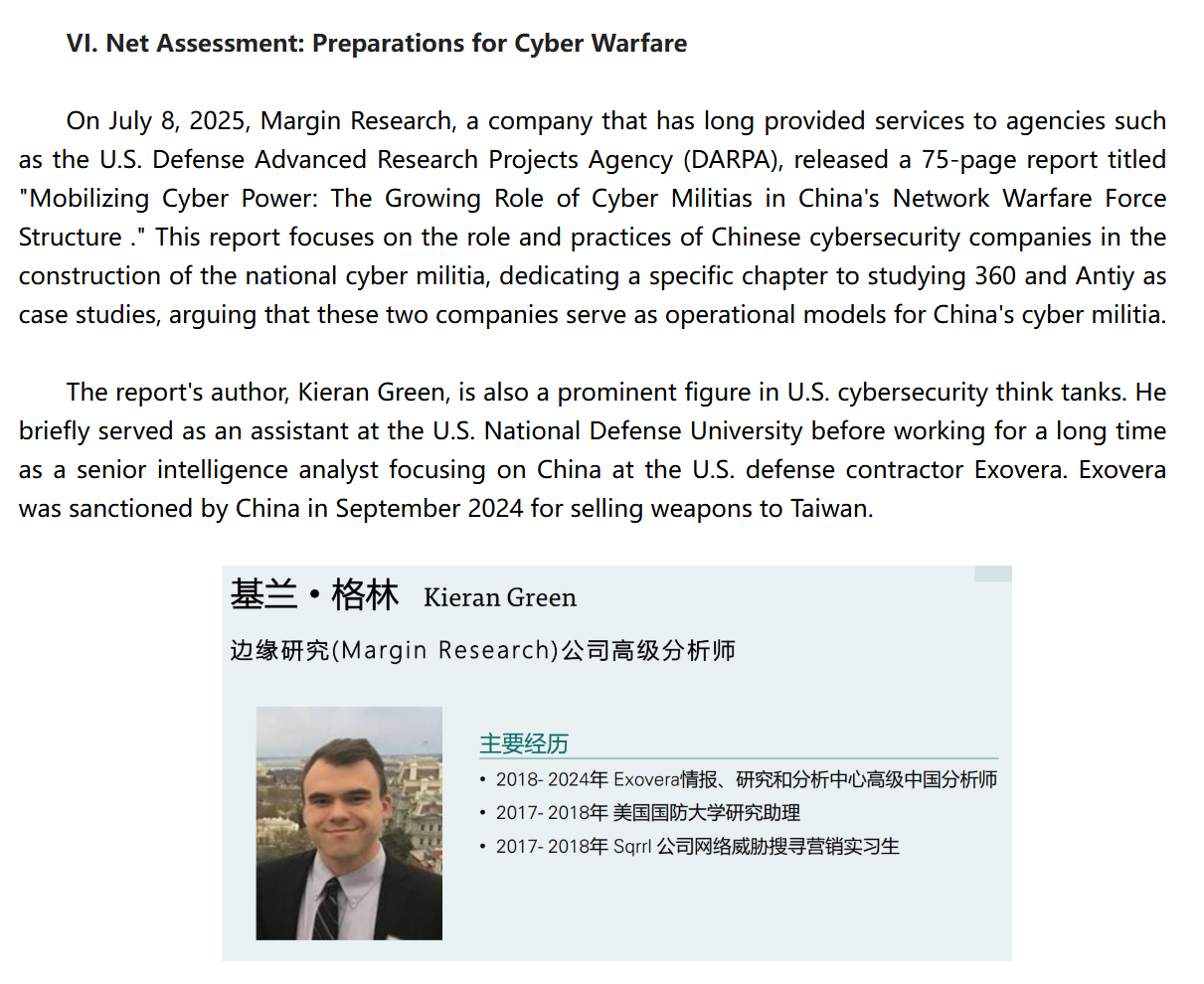
After Cary, the report targets Margin Research’s Kieran Green:
The report claims that his work on researching Chinese cyber militias is a sign, as per sources, that the US is “planning to launch a cyber war”:
There’s more, including discussion of the others mentioned, as well as some truly nonsensical discussion of their motives:
This is super interesting as a piece and I wish we had more information on who authored it. It does show that someone in the Chinese government does follow US attribution and analysts, which is unsurprising, and I’m curious to see what we see next from China’s menagerie of cyber attribution outlets.
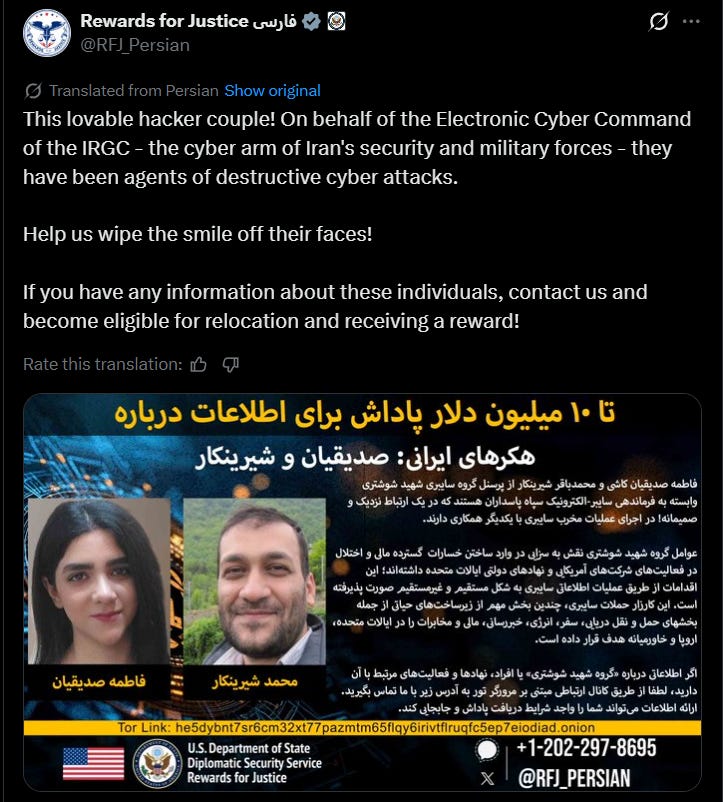
We’ll conclude with the DOJ and Rewards for Justice, which have been killing it lately with exposure of hacktivist IO activity, ranging from Iran:
to Russia, targeting Cyber Army of Russia Reborn and NoName:
Germany also is stepping it up, having summoned the Russian ambassador over some of its cyber-enabled IO. Not clear yet if this is a coincidence, part of a joint push or otherwise, but certainly an interesting time to see more naming-and-shaming and even diplomatic escalation against cyber-enabled IO.