The Bear (Not That One)
SQL… So Quick and Lethal: Apparent Perception Hack Attempt Post-2024 US Elections
Hello everyone and welcome to a special guest post edition of Memetic Warfare.
This week’s guest post is by Max Lesser, a close friend and colleague of mine at the FDD. You may notice that he’s much better at prose than I am, so try not to get overly used to his superior writing style, as we’ll be back with regular Memetic Warfare later this week.
Check out what Max has to say on an interesting account below:
Hi all. My name is Max Lesser, and I am crashing this week’s edition of Memetic Warfare Weekly.
Ari and I work together closely at the Foundation for Defense of Democracies (FDD), but we decided to publish this research independently as the investigation is still ongoing. Our incredible intern, Mason Krusch, also helped with these findings, and he is open for work… so better hire him before someone else snatches him up!
Prior to the election, the ODNI warned that foreign threats to U.S. elections might continue after voting ends, seeking to cast doubt on the integrity of the elections. We recently discovered a hacktivist persona who claimed to have hacked election infrastructure. The persona appears to intentionally feed the impression that it is Russian, but it is difficult to determine whether it is in fact Russian or someone posing as a Russian. It is clear, however, that someone created the persona expressly for the purpose of spreading highly suspect claims of having hacked election infrastructure to tip the scales in Trump’s favor.
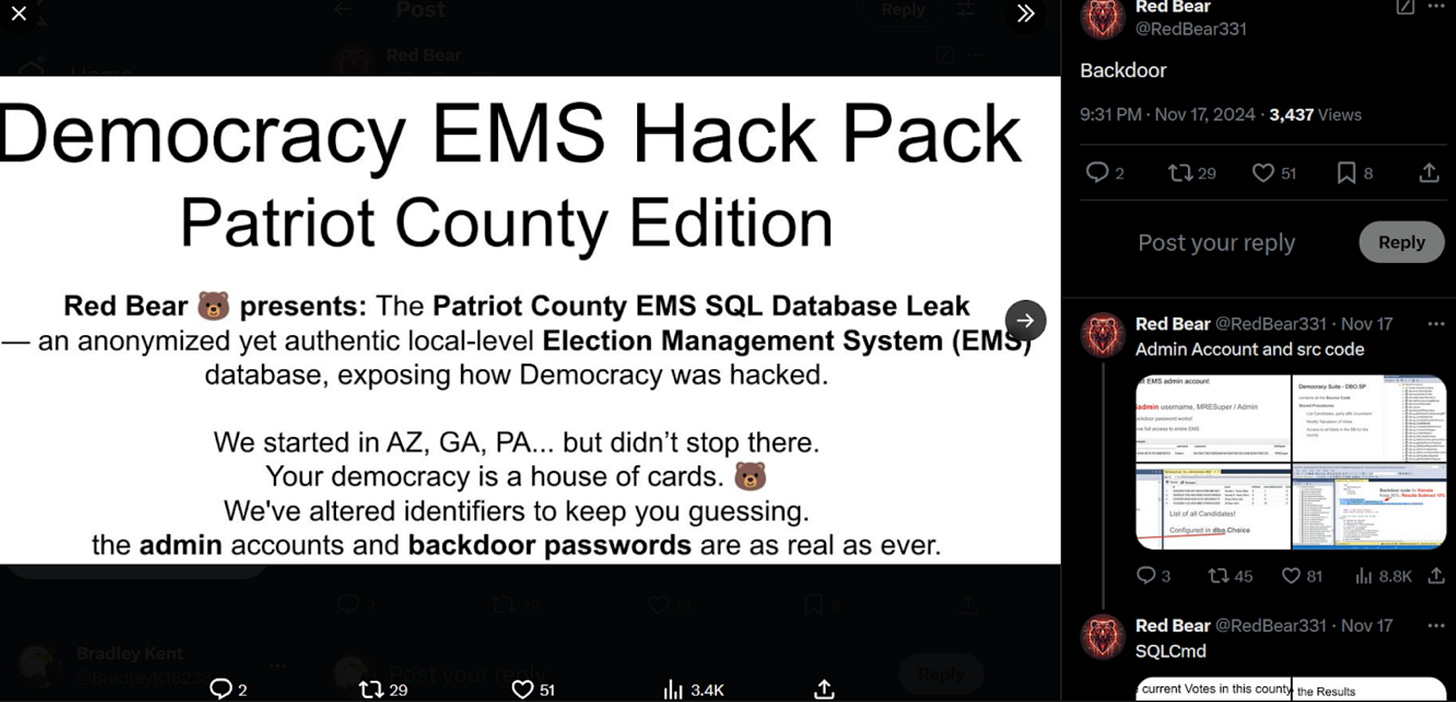
On November 17, 2024, an unknown hacktivist persona known as Red Bear claimed on X to have hacked into Dominion Voting’s Election Management System (EMS) to flip votes in Trump’s favor in unspecified regions across Arizona, Georgia, Pennsylvania, and other states.
Figure: Photo shared in Red Bear post claiming it modified results in Arizona, Georgia, Pennsylvania, and other states.
Red Bear warrants attention not only because of the nature of its claims, but also because the claims have gained significant reach. Red Bear’s own posts on X have collectively garnered over 80,000 views. On top of this, Elections Focus, a suspicious account discussed in a previous edition of Memetic Warfare Weekly, shared screenshots of Red Bear’s posts multiple times, collectively gaining over 180,000 views. Prominent entrepreneur-turned-philanthropist Chris Klaus shared Red Bear’s claims over multiple posts that collectively garnered over 420,000 views. These posts on X are only a few prominent examples, and do not comprehensively represent the reach of Red Bear’s claims across various platforms.
A surge in election denialism on the American left may be responsible for Red Bear’s relative success in gaining traction. If Red Bear is in fact a foreign influence operation, it demonstrates a striking example of a malicious actor successfully leveraging a highly divisive domestic conversation.
Red Bear’s claims are highly suspect for several reasons. First, Red Bear claims it used a backdoor password “dvscorp08!” to compromise EMS databases. However, Election Assistance Commission disclosures published more than a decade ago reveal that cybersecurity researchers first reported this vulnerability in 2010 and remediated it in 2012.
Figure: EAC document from 2012 disclosing hard coded password in Dominion systems and noting that the issue was subsequently resolved.
On top of this, Dominion also states on its website that “Dominion voting systems are designed and certified by the U.S. government to be closed systems that do not connect to the Internet” and that “state and local requirements also serve to maintain air gaps for security.” Air-gapped networks (simply put) lack connections to external networks including the internet. They help prevent malicious actors from using remote access to tamper with the election results.
More ink can be spilled debunking Red Bear’s claims. For example, Red Bear also claims to have modified SQL Server databases in a manner that evaded detection. But all SQL server databases have transaction logs that record all modifications, and so it is not possible to modify or even create an SQL server database without a transaction log file.
Aside from the merits (or lack thereof) of Red Bear’s claims, the manner in which Red Bear created and spread his claims proves highly suspicious. Red Bear created its X account on November 17. On the same day, it created an account on Reddit, and also an account on Pastebin, where it shared a torrent file. Hackers historically have used Pastebin to leak breach data, and so Red Bear’s use of Pastebin bolsters its self-presentation as a hacktivist persona.
Figures: Creation dates for Red Bear’sTwitter account (as per OSINT industries) and Red Bear’s Reddit Account, u/Global_Department119, which links back to Red Bear’s X account.
Figure: Screenshot of Paste in which Red Bear shares a Torrent File.
Unfortunately, by the time we discovered Red Bear, the torrent file was no longer available for download, as it was no longer being seeded. And so, we were unable to further analyze the torrent file to assess the credibility of its contents.
Red Bear also created a TikTok account on November 18. On TikTok, Red Bear shared two separate videos showing the same sequence of images with identical subtitles. One video includes a whispering voice reading the subtitles, and the other includes recordings of Trump claiming “we don’t need the votes” and discussing an unspecified “little secret” he allegedly had with Speaker Johnson. By including the Trump voice overs, Red Bear seems to suggest that the “little secret” is the alleged EMS backdoor.
Across X and Reddit, Red Bear copied and pasted identical text at least six times between November 17 and 18. The text said that, “Democracy Suite EMS contains backdoor password: "dvscorp08!" . This Hardcoded "security" + SQL commands = Trump's victory. Worked in AZ, GA, PA, etc. File has county SQL DB, backdoor/admin info, SP code: [link to Pastebin].”
On X, Red Bear shared this message and other messages that claimed the election was “hacked” as replies to apparently authentic users questioning the integrity of the 2024 U.S. elections, repeatedly attempting to inject its suspect claims into organic social media discourse. On Reddit, Red Bear similarly attempted to inject its claims into subreddits such as r/Hacking_Tutorials, r/NetSec, and r/electionfraud. Red Bear also appeared to reach out to at least one cybersecurity researcher via direct messaging on X.
Figure: Red Bear’s posts on Reddit.
All of Red Bear’s activity across X, TikTok, and Reddit began on November 17 and ended on November 18. This short period of high activity suggests that Red Bear, rather than representing an authentic hacktivist, may be a front persona built for the purpose of spreading false claims of hacked voting systems.
Red Bear also appears to intentionally feed the impression that it is operated by Russians. The name ‘Red Bear’ evokes names commonly assigned by cybersecurity researchers to Russian advanced persistent threats, such as ‘Fancy Bear’ and ‘Cozy Bear.’ Red Bear also refers to “Krasny Medved” in one of its posts on X and in its TikTok videos. “Krasny Medved” is the English-language transliteration of the Russian word for Red Bear, красный медведь. These decisions are clearly intentional. Red Bear also occasionally omits articles in its text, which may or may not be intentional. For example, Red Bear writes on X, “Can you help discuss election hack I found?” This suggests the person behind the Red Bear persona speaks a Slavic language, such as Russian, which typically do not have articles.
Figure: Red Bear’s post on X referring to ‘Krasny Medved,’ the English-language transliteration of ‘Red Bear’
Figure: Still from Red Bear’s TikTok video referring to ‘Krasny Medved,’ the English-language transliteration of ‘Red Bear’; interestingly, this post also explicitly gives ‘credit’ to ‘Elon’
Though Red Bear may seem obviously Russian, one should not jump to conclusions. Red Bear may be a Russian hacktivist or state-sponsored threat, however, Red Bear could also be a false flag posing as a Russian operation.
On one hand, Russia has a history of on-the-nose influence operations. As Steven Lee Meyers and Julian E. Barnes of The New York Times have aptly noted, Russian influence operations targeting the 2024 U.S. election often did not bother to hide their hand.
Red Bear’s clear intention to appear Russian could be a Russian attempt to convince Americans that Russian interference significantly impacted the results of the 2024 U.S. elections. For example, before the 2018 U.S. midterm elections, the Kremlin-linked Internet Research Agency set up a website titled USAIRA[.]ru that claimed “Whether you vote or not, there is no difference as we control the voting and counting systems. Remember, your vote has zero value.” Red Bear could similarly be a Russian attempt to ‘perception hack’ Americans into thinking that Russian interference more significantly impacted U.S. elections than reality suggests.
Red Bear also could be a false flag operation meant to appear Russian. For example, the hacktivist group Hunt3r Kill3rs claims to be Russian but is likely Iranian. It is difficult, however, to imagine Iranian threat actors being sophisticated enough to occasionally omit articles to imitate how a Slavic-speaking person would write in English. A domestic actor in the U.S. could also have created Red Bear as a false flag to cast doubt on the integrity of the elections. However, this is highly unlikely, as there is no precedent for American citizens launching foreign false flag influence operations of this nature targeting other Americans.
It is difficult to confidently attribute Red Bear with the available open source information. Red Bear has no obvious operational security slips revealing the identity of its operators. The timing of Red Bear’s activity on messaging platforms and social media does not clearly align with the waking or business hours of Russia, Iran, China, or another U.S. adversary. Nor has Red Bear set up its own domain, which might provide more technical indicators to investigate.
We welcome any input from the research community that might aid attribution. Moreover, the platforms that Red Bear uses might want to conduct their own investigations, as they might have access to internal data such as registrant emails that can aid attribution. Lastly, considering that Red Bear has spread suspect claims of hacking election infrastructure that have gained traction, the U.S. government might want to look into it to determine whether a nation-state was involved in this activity.