THANK YOU FOR YOUR ATTENTION TO THIS MEMETIC WARFARE
Welcome to Memetic Warfare.
This week we’ll look at one specific group that we haven’t discussed here at all to my knowledge but has recently made some headlines, and that’s Ares Leaks.
Ares is one of the better-known Telegram data leak providers, selling mainly hacked/stolen/compromised government documents, databases and more on Telegram. They’ve been known to publish data from all kinds of countries, including Russia, China and Iran as well as general cybercrime stuff - KYC breaking guides, private-sector leaks and so on.
I normally wouldn’t discuss them here as there wouldn’t be much worth mentioning beyond general data brokerage. However, they’ve made two interesting decisions that I thought were worth noting. One is that they decided, out of the goodness of their hearts, to provide the New York Times with “Secret Russian Intelligence Documents” that show how China spies on Russia. Breaking news - everyone spies on everyone, and that’s generally accepted as an OK thing by most states.
The New York Times, in a very controversial and perhaps not well-thought out choice, decided to uncritically cover these leaks after trying to verifying them and seeing that they were probably legit.
There’s no real reason for Ares to share these documents with the NYT. The financial motive is nonexistent, as they’re already well-known and aren’t trying to appeal to a wide audience.
If anything, this would just piss off Russia a lot - not something that the average cybercriminal is interested in doing, and clearly something meant to foment some unrest between Russia and China - I wonder which countries would want that?
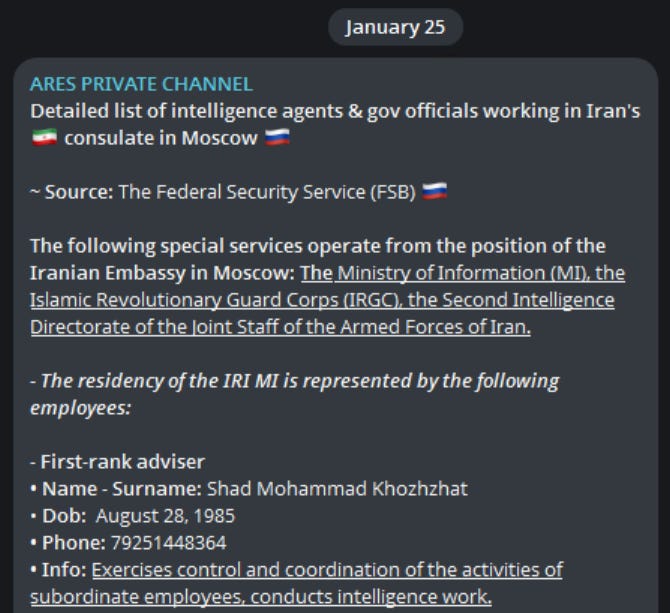
In of itself, the above is a weird occurrence but not necessarily a trend. Well, it turned into a trend this week as Ares again decided to poke the proverbial bear, or in this case lion, and publish dozens of leaked mini-case files on IRGC officials - see below:
Ares has done this before also, posting similar information on alleged Iranian intelligence officers active in the Iranian embassy in Russia:
We’ve covered a lot of activity in this vein on the blog, and as of late I’ve been looking at Ares as a potentially similar type of operation, albeit one that augurs a significant change of direction. If Ares is in fact a nation-state operation, it crosses an interesting ethical and legal threshold as it as a channel engages in selling leaked data.
This is arguably fine if the ends are worth it, especially if it’s just repurposing otherwise available data and then using the channel itself to launder new data. Personally, if so, I’d be in favor and hope that Western nation-state operations get edgier.
I’m not saying that Ares is definitely a nation-state operation, but it certainly is odd to see a data broker work actively against its own financial best interests on a somewhat regular basis.
So, while absolutely far from clear here, Ares’ decisions as of late have caught my eye and what once appeared to be run of the mill, if successful and prominent, data broker may be more than meets the eye.
Let’s move on to an interesting case of potential kinetic-information warfare overlap in the past war. According to some claims, Storm-2035 accounts targeting Scotland went dark following the initial Israeli airstrikes following the recent war:
Some users posted specific examples:
While it’s unclear what exactly happened, there are a few possibilities as described:
The first is that the airstrikes and subsequent internet and electricity disruption caused the operation to shut down temporarily. This is feasible, but also not necessarily airtight; I’d imagine that nation-state affiliated operators, even if working out of a front company, would have power and even internet (starlink perhaps?) backups available. This argument only holds water for the first day or two as well, as eventually power and the internet were restored, even if the internet was occasionally shut off by Iran (though this wouldn’t apply to the government).
The next possiblity that IMO is quite feasible but not brought up is that the airstrikes themselves hit offices or facilities in which the operation was based. I think that this is quite possible and could explain a much longer outage if say the offices were destroyed or damaged, servers hit, or even operators killed.
I don’t buy the internet outage causing this alone to be an issue - the government could easily bypass that in multiple ways, including just whitelisting the specific facility used. Regardless - a rare look at how different vectors tie in together.
We’ll conclude with a quick discussion of another development from the war - overt recruitment and IO efforts. There’ve been multiple Iranian attempts to target members of the Arab population of Israel:
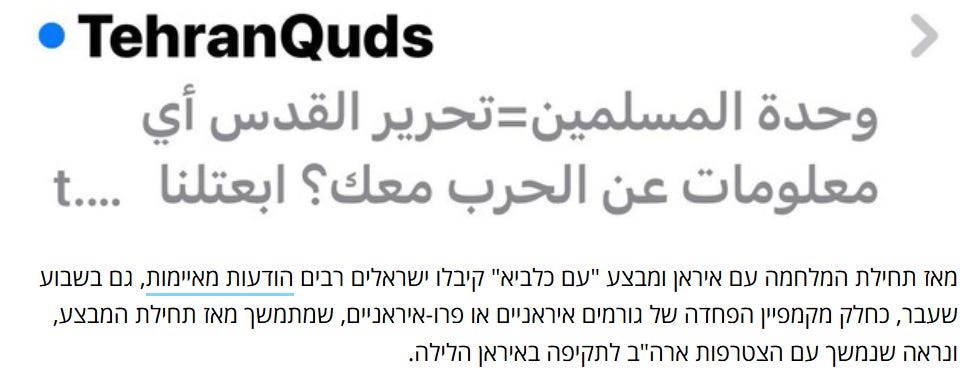
Some of these refer to a Telegram account appealing specifically to “48” Arabs - a common name used for Arab citizens of Israel. Perhaps the most interesting is a mass SMS under the name “TehranQuds”, which is as overt as one could be, saying that “Muslim unity = freeing Jerusalem”, and asking recipients to send them any information on the war:
Wartime is seemignly a great opportunity for everyone to shake off the mask of covert operations and begin acting overtly. This is an interesting change from “subtle”, covert operations meant to impact one’s perspective on the world, to operational, overt and tactically-oriented operations.
That’ll be it for this week! Check out Telemetryapp.io and let me know if you have any complaints, jokes or otherwise in the comments.









Of all the names, why choose
Jake, Fiona and Lucy?