Source: I made it up
Welcome to Memetic Warfare.
We’ll keep the party going from last week’s post and discuss yet another unusual hack and leak in Iran with some interesting similarities to past week’s case.
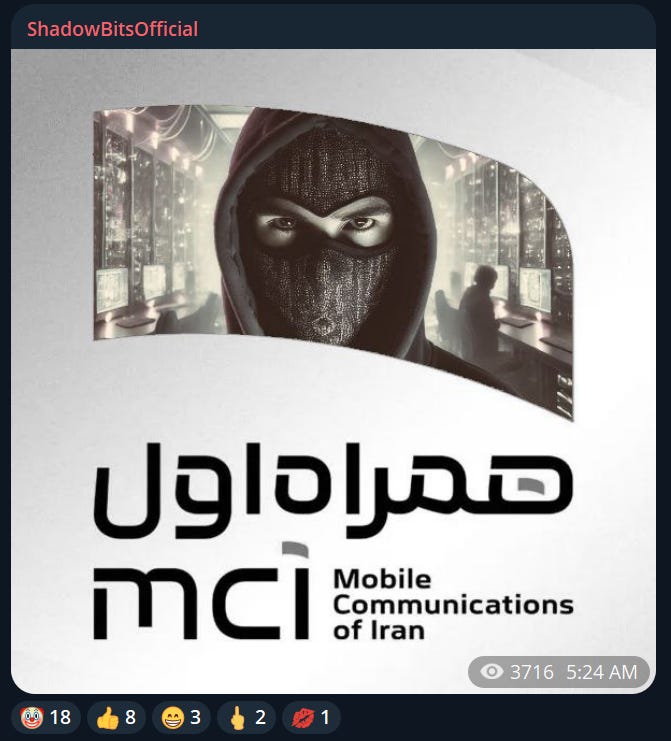
This unusual hack and leak was carried out by the nascent hacktivist group “Shadowbits”, which successfully compromised MCI (Mobile Communications of Iran), a leading Iran telecommunications firm. They’re really hamming up the visual aspect of their operation, not something commonly done by purely financially-motivated actors.
Like Codebreakers, they use the same style of AI-generated meme profile picture with a similar colorscheme:
Compare that to Codebreakers. Arguably alike due to use of gen AI, but still something.
Shadowbits has provided some significant samples, such as 300,000 records from the leak as well as full data on 300 employees, showing they really have something. This is also similar to Codebreakers, which published an unusually large sample size, arguably not to their financial interest.
Interestingly, they chose to post the leak on Leakbase and Exploit.in and not say something super popular like Breachforums. When they first posted it, Breachforums was still up, but was taken down just a few days ago. What a coincidence!
Just the other day they released another leak, this time of 80 Iranian parliamentarians:
This is an ongoing affair that seems super similar to Codebreakers, so I’ll keep an eye on it. Wonder which major Iranian company or organization will be popped next week.
On that note, I’ll throw out a mention to clearsky’s latest report on Houthi IO, available here. It’s not bad, but needs more depth and some improved production values, so if you’re interested, take a look.
Onto the next big topic: Chinese cyber attribution.
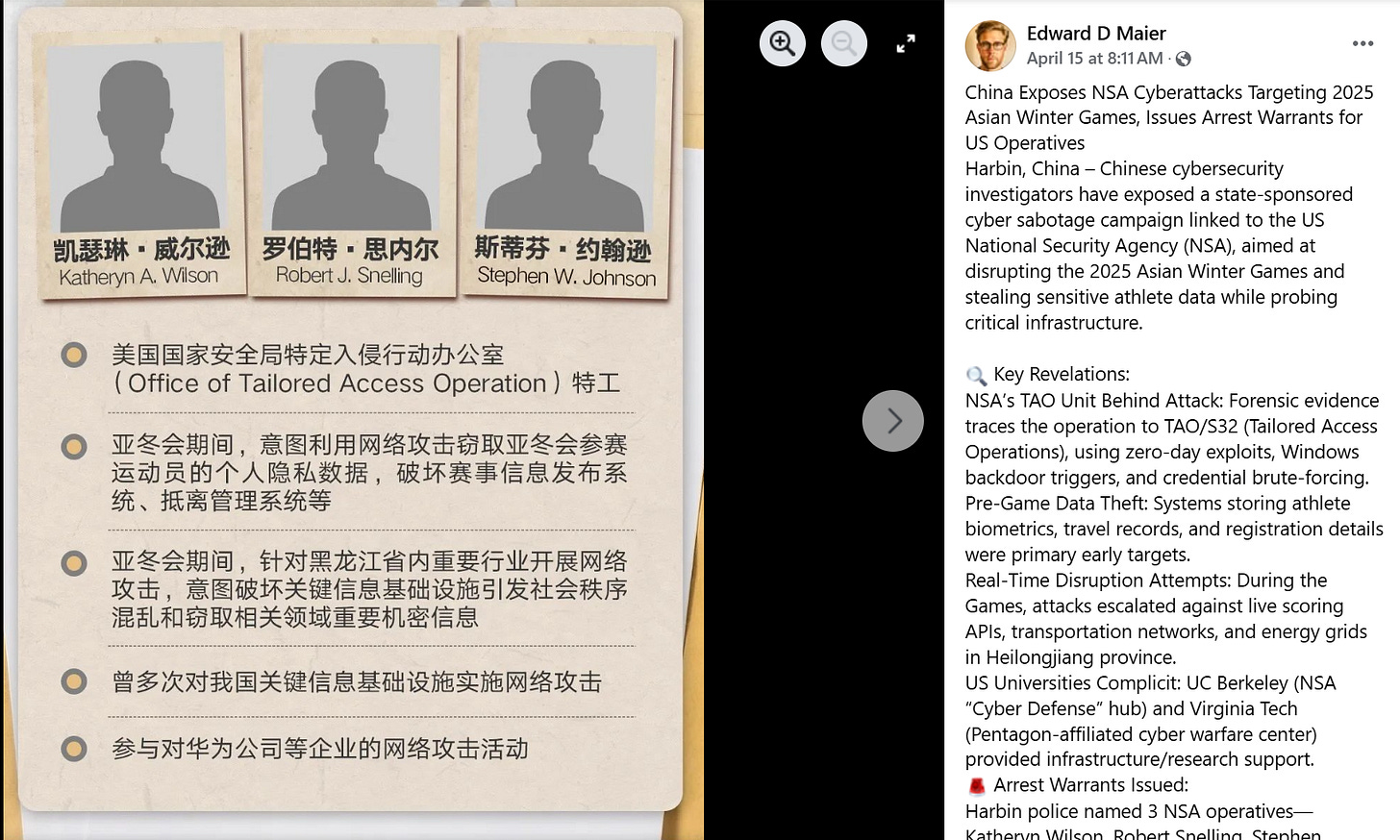
It’s shaping up to be a huge month for Chinese cyber attribution, a topic I hope to have something in-depth coming out on in the coming few months. Following the CVERC’s original report on alleged US operations targeting the Harbin Winter Games, the Chinese MPS has now come out and named-and-shamed the apparent US TAO (the one unit they keep harping on about) operatives involved in the attack and offering a reward for their arrest in a recently published statement.
Attributing individual US cyber operatives is a first for China except for that one time they claimed to have exposed Rob Joyce as the head of TAO despite him having stated that publicly before, showing we have now come full circle with the Chinese fully imitating US attribution efforts.
There are a few unusual things here. Firstly, why just names and no pictures or other personal information? If the Chinese had successfully penetrated the NSA, which I certainly think they could, they could probably have provided some pictures, ID numbers or other relevant information. China has done this with Taiwan when they have the access (or claim to at least)
The names used also strike me as odd - the use of the middle initial for each of them, the untraditional spelling for Katheryn, it all has a very uncanny valley feel to it, and reminds me of that Japanese videogame in which they made up random names that they thought sounded like real American names like “Sleve McDichael”, “Dwigt Rortugal” or “Todd Bonzalez”.
There are some other open questions. Are the names in fact real or fake? Personally, I’m inclined to say fake, but let’s entertain the possibility that they’re real. A recent episode of the 3 Buddy Problem discussed this, bringing up an interesting point: assuming that the leaks are real, the data was probably sourced via human or signals intelligence sources, perhaps from Salt Typhoon-enabled capabilities. Regardless, I still don’t believe that the data is in fact authentic.
It doesn’t end there though! Antiy, a Chinese CTI firm, put out their own technical reporting on these US operations which is one of the crazier things that I’ve read out there. If you’d like, check out the original here.
Apparently Antiy considers port scanning to be an attack, calling out Censys (one of my favorite tools even if I don’t love the new platform UI) for port scanning them, despite port scanning being totally fine and normal. The authors also review their workflow - looking up the IP address, seeing that the range is owned by Censys and thus cracking the case that CENSYS-ARIN-01 is in fact owned by Censys.
They then further call out Censys for - God forbid - selling to the USG:
They also claim that BinaryEdge attempted to exploit a vulnerability?
There are some other attacks that they describe, but the trend remains the same: either incredibly poor quality reporting and investigation, or alternatively a somewhat capable team being forced to make stuff up for political and IO reasons. Who knows, perhaps it’s both.
There’s also been some seemingly inauthentic/suspicious amplification online, including from one suspicious account with a gen AI-created profile picture posing as an American with no other personal information, who posts (and tweets) almost exclusively about China in a positive light.
The post itself also looks ChatGPT generated based on its structure, use of emojis and so on. Funnily enough also, this account insists on using the full name with an initial, not unlike the indictment itself. Overall an interesting account, would be interesting to follow.
Looking up that image itself shows that it is a cropped version of a poster created by the MPS, interesting that they cut out the full version for that sole Facebook post of it.
There’s some other amplification in English by suspicious accounts, if minor.
There’s more of the typical stuff - inauthentic accounts sharing posts from embassies and so on, and also more stuff in Chinese, but on the whole pretty standard operating procedure for this stuff - post it, amplify it with inauthentic accounts and so on.
Natto Thoughts has additonal context and takes on this, so check out their always prescient writing below:
That’s it for this week!