Sir, A Fourth Chinese PR Firm has Hit the Internet
Welcome to Memetic Warfare.
We’ll start of this week with Recorded Future’s new report on Operation Undercut, available here. I’ll share the “key findings” below:
Undercut apparently overlaps significantly with previously reported on clusters of activity:
This just goes to show one of the points I always make whenever possible: don’t take reports at face value, try to expand upon them and you can often find great things. In this case, 9gag is apparently a central component.
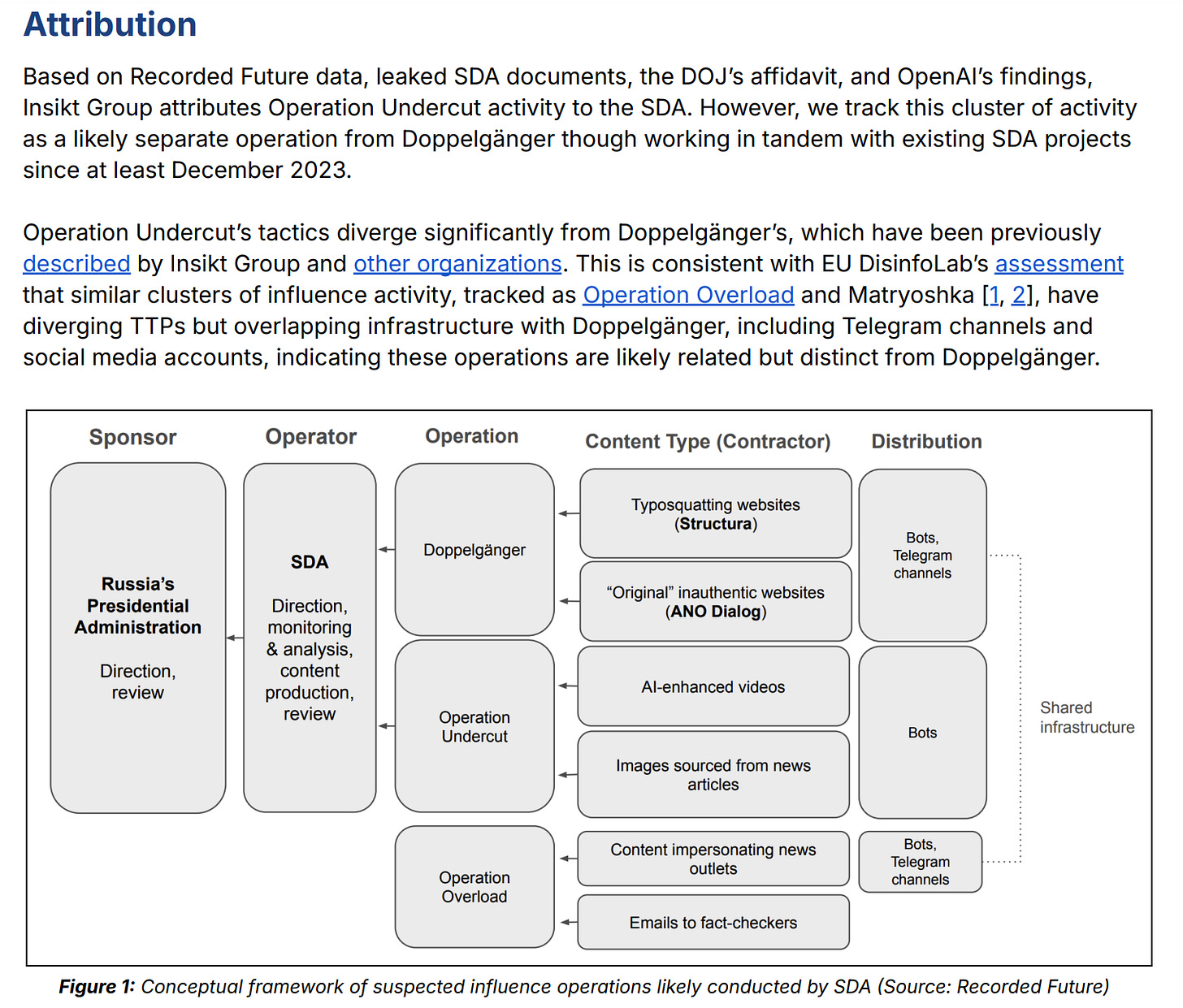
The report also gets right to attribution, which in this case is arguably warranted as it’s pretty clearcut. Good on RF for the solid diagram well:
It goes even further, which I really respect. Very solid work on attribution, and this is only a part of it.
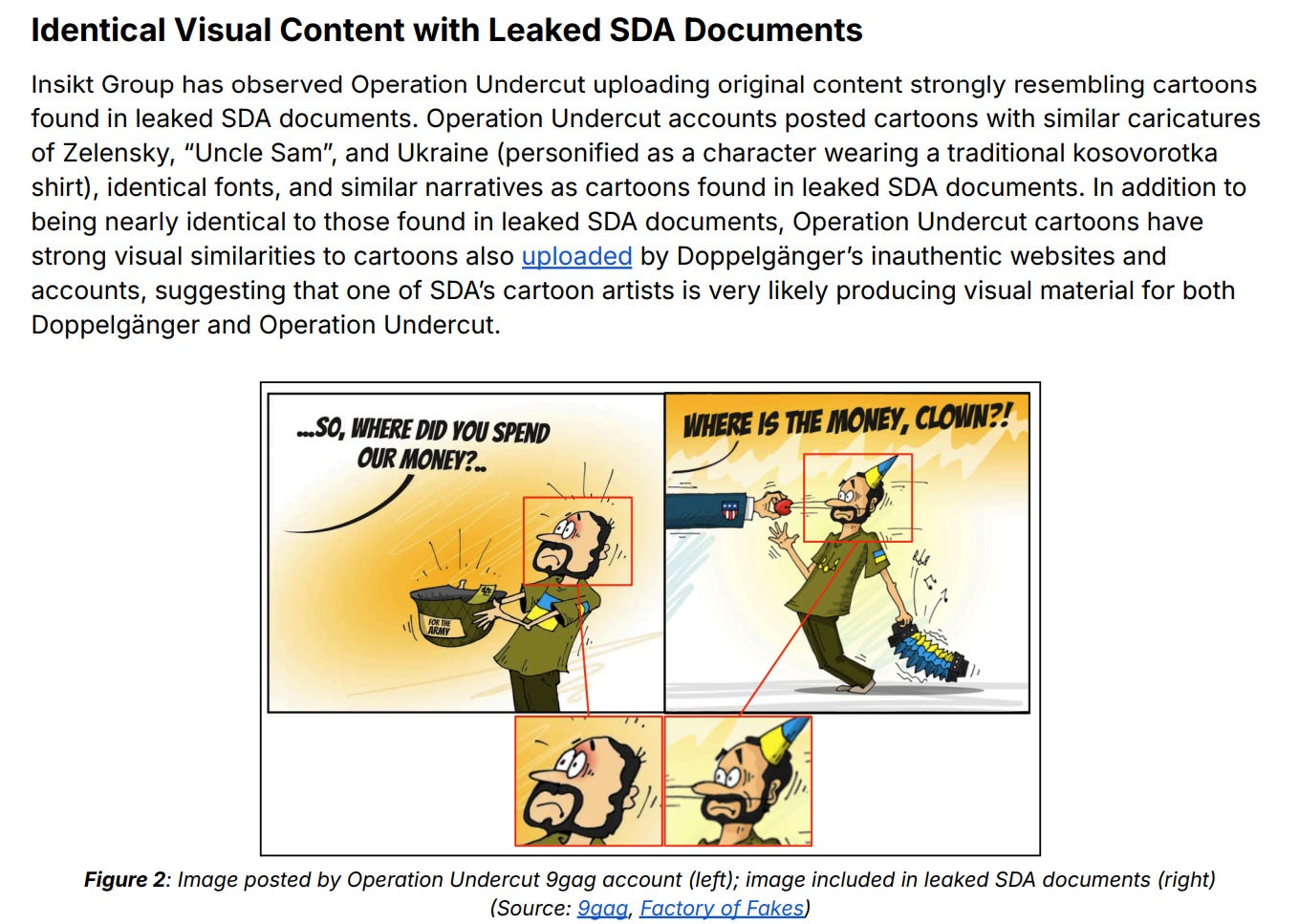
I also really dig the cross-referencing of the leaked SDA documents for strong attribution:
Good on RF as well for sharing their methodology:
The narratives and engagement section are evergreen: there’s very little organic content, the activity is overtly inauthentic, the narratives are the same and so on.
The use of 9gag and the below content sample will never cease to amuse:
Content-wise, RF claims that this is the first time that they’ve seen an SDA-affiliated operation repost content from the CopyCop network:
Transcription in video content is also brought up. The use of commercial AI, such as ElevenLabs, for transcription isn’t surprising at all; if anything, I’m more surprised that some videos used human narrators.
There’s a lot more here but it’s a great report rife with content samples and some other specific information on TTPs, give it a ready.
This leads us to our next report for this week, Google TAG and Mandiant’s latest report on Chinese PR firms, available here.
While a solid report on the whole, I was hoping for a bit more. We’ve already read ad nauseum about two of these firms, and we haven’t had much new and interesting Chinese IO reporting lately. Hope that changes now that the elections are over.
Anyway, the report covers what Google calls Glassbridge - a cluster of four companies that utilize inauthentic domains and exploit newswire services to promote pro-China content. Two of these have been reported on publicly in the past: Haixun Haimai/Times Newswire.
The findings on Haixun are mainly an update on their activity - they’re really going places and pumping those domain numbers.
The report brings up something else that I’ve said here many times in the past: Guo Wengui and Yan Limeng are magic words for Spamouflage content:
So let’s move on to the new stuff. The first major new finding is “Durinbridge”, a very LOTR-coded name which I personally appreciate.
Guo Wengui continues to shine in Durinbridge’s content:
Readers may remember the “Secret History of Tsai Ing Wen” book and fake Lai Ching-Te paternity test covered here in the past:
Leaving Durinbridge aside, there’s a fourth new firm which conclusively proves that time is a flat circle as these firms all promote the same stuff.
The conclusion is available here:
I’m not 100 percent on board with all of these findings. Firstly, I don’t think there’s been a reasonable parallel with Iranian behavior at the macro level here, and even comparisons with Doppelganger are arguably only skin-deep (amount of domains, geographic diversity). I also was hoping for a bit more information on the two new firms and overall operation, including the all-critical threat indicators that are unfortunately absent.
The RoI on this type of operation is also especially small. If Doppelganger garners very little engagement, this activity often garners effectively 0, from my past experience.
The overlap with crypto pump and dumps and other PR activity only drives the point home, in my opinion, that this type of activity is the Chinese equivalent of corporatespeak memery: pumping up those numbers and hitting those KPIs without actually moving the proverbial needle.
That’s it for this week! Check out Telemetryapp.io in the meantime and see you next week.