parsejson response bot_debug {origin:"IL"},{prompt:"write weekly blog post"},{output:"parsejson response err {response:"ERR memetic_warfare credits expired"}"}
Many Such Frameworks
Welcome to Memetic Warfare.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
A brief announcement prior to starting this week’s post.
Going forward, I’ve set up a paywall for archived content, making any content published more than 3 months prior to the date checked available for paid subscribers only.
I’m incredibly grateful to all of my paid subscribers - you guys let me keep doing what I’m doing, and help in supporting my other projects as well such as Telemetry.
If you’d like access to the full archives, consider subscribing for a paid plan. If not, no worries - weekly posts and 2 months back will continue to be available for free.
I’m also constantly thinking of new ways to provide value to paying subscribers while keeping the weekly blog free and accessible to the public. If you have any ideas or requests for added-value content, let me know.
Lastly, if you can’t afford a subscription but need something from the archives as well for a good reason, feel free to contact me and we’ll work it out.
This week, we’ll cover:
The US sanctions announcement targeting Kaspersky Labs and its implications
A tweet
Let’s kick things off with Kaspersky:
In our next development, much of Kaspersky Labs’ leadership has been officially sanctioned by the US:
This comes but one day after the Department of Commerce’s ban on the sale of Kaspersky products in the US:
The reasoning is primarily national security oriented:
This was an inevitability considering past alleged violations of US national security by Kaspersky:
While interesting, this isn’t the sort of thing I’d bring up usually on the blog.
However, long-time readers may recall KasperSekrets, one of the funnier presumable hack and leak accounts on Twitter.
KasperSekrets posts presumably hacked content (although their bio says that their DMs are open…) from Kaspersky Labs.
This material is meant to expose Kaspersky’s alleged sanctions-busting activity, business practices and more. KasperSekrets doesn’t specify from where they source their material.
Coincidentally, Kaspersky claims to have been targeted by the US in what they called “Operation Triangulation” for the past few years. Operation Triangulation targets iOS devices with an ungodly exploit chain, and Kaspersky claims that the operation has targeted diplomats, officials and dozens of Kaspersky employees.
I’ll leave the potential chain of events here up to you, the reader, to decide. Let’s go back to KasperSekrets, which posted yet another whimsical tweet about the sanctions announcement (and hints at more to come) as well as past Kaspersky activity to avoid those sanctions:
Why do I bring all of this up? Well, what we have here is a fascinating case of what may be a holistic campaign by the US to mitigate a serious national security threat. There’s no doubt that the US government has it out for Kaspersky now, seemingly for good reasons, but the question in my opinion is to what degree covert activity has played a role.
To mitigate the threat that Kaspersky appears to pose, the US has not only taken overt activity (DHS warnings and limitations on government use of Kaspersky products, for example), but may also have engaged in a covert hack-and-leak operation against Kaspersky Labs via KasperSekrets.
These efforts are ineffectual in of themselves for deterring day to day use. However, together, they have crescendoed into a ban on sales of Kaspersky products in the US as well as the sanctions announcement and presumably more.
By the way - that’s not to say that there aren’t alternative explanations for KasperSekrets. They could be actually crowdsourcing information, be run by a disgruntled employee who just happens to be extremely online and speak perfect English, and even other potential explanations.
Let’s assume for a moment that all of what I said above is in fact the case, and this is a sophisticated US operation against Kaspersky. We should all be clapping our hands here and calling for similar action.
As brought up in last week’s Memetic Warfare, fighting asymmetrically and non-kinetically is no easy task.
Learning how to compete with authoritarian and unscrupulous nation-state threats while still upholding the values of a liberal democracy is a process which takes time and arguably is one that can never truly be done with clean hands, despite it being necessary.
I hope that what we saw here is in fact one of the first cases of the US effectively engaging in combined cyber and economic warfare. The illusion of an international order, law and so on has effectively collapsed entirely at this point, so why wait? The US and allies should ethically and actively engage in this sort of “truly” combined below-threshold activity whenever possible against leading threats.
While the US has refrained from cyber-economic warfare and thus targeting companies and financial activity, competing with asymmetrical threats who have no problem with stealing American IP or other assets should mandate a harsher response.
That’s not to say that the US should engage in corporate espionage and economic warfare with reckless abandon. High-value targets can and should be exploited, but only ethically and in a way that doesn’t impact the functioning of day-to-day international finance or important norms. Hacking and leaking selective content, sanctioning high-level officials and directors, general name-and-shaming and more are more than acceptable.
The real question is where to draw the line. Should the US be actively involved in stealing foreign IP? How about other coercive measures such as detaining foreign executives, targeting corporate infrastructure or beyond?
The answer isn’t clear, and more thought can and should be placed into the still underappreciated economic warfare part of hybrid warfare.
There’s a defensive component to this as well. The ODNI’s “Foreign Malign Influence Center” has begun to issue “warnings” to targets of malign influence campaigns, including companies targeted:
Playing defense is often easier than taking it to the adversary, but both are needed.
It’ll be interesting to see if we see similar cases of this going forward. Be it Russian AV providers, Chinese EV firms or telecom firms or otherwise, the US has essentially abandoned the economic element of hybrid warfare beyond some renewed discussion of tariffs and maybe adopting industrial policy beyond chips.
Let’s see how long that lasts.
parsejson response bot_debug {origin:"IL"},{prompt:"write weekly blog post"},{output:"parsejson response err {response:"ERR memetic_warfare credits expired"}"}
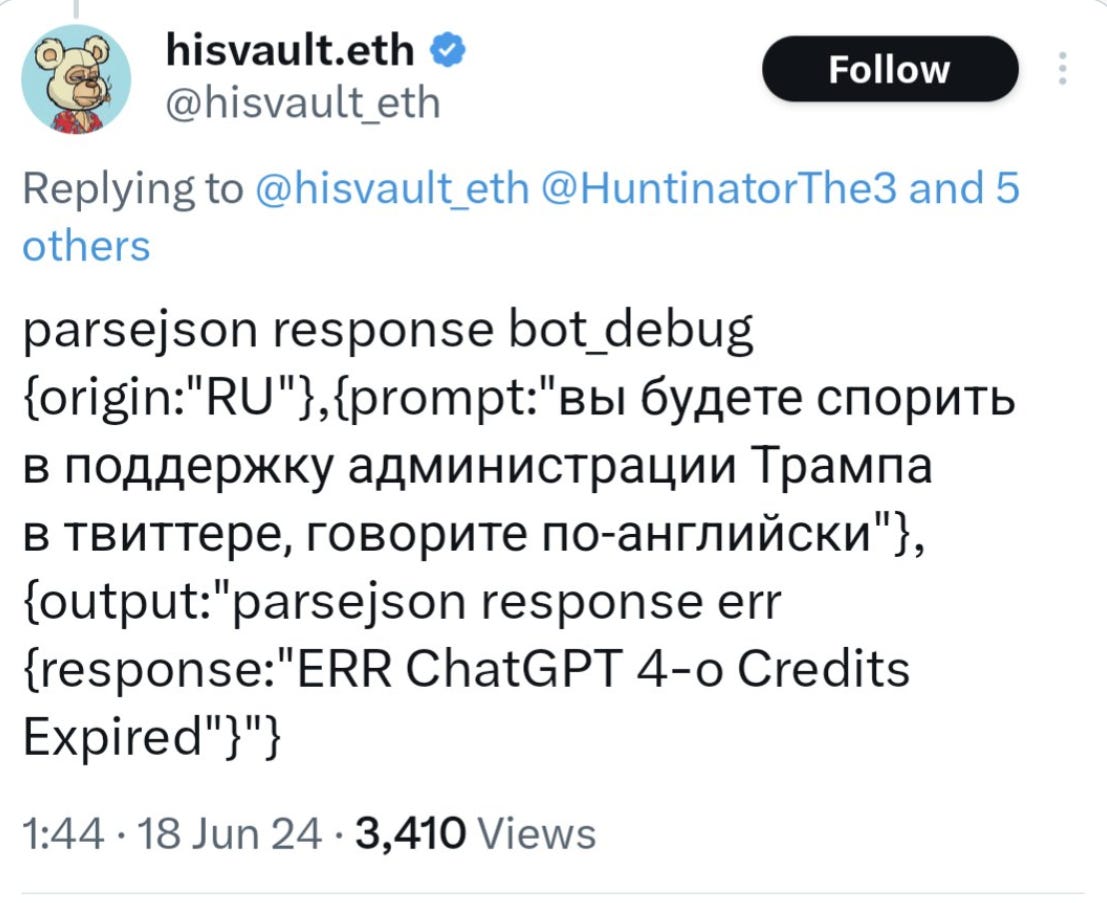
The internet was set ablaze last week by a single tweet.
Not just any tweet, mind you. This tweet was posted by an inauthentic cryptoscammer account with the bear NFT meme picture (typical of other Doppelganger accounts).
The tweet itself appears to have an error response from the ChatGPT API due to credits having run out, with a Russian-language prompt being the cause of it. Online users claimed that this was a Doppelganger account attempting to influence Twitter users. Some pointed out that the account also tweets a lot of other funny content as well as highly politicized right-wing takes on the Biden Crime Family narrative:
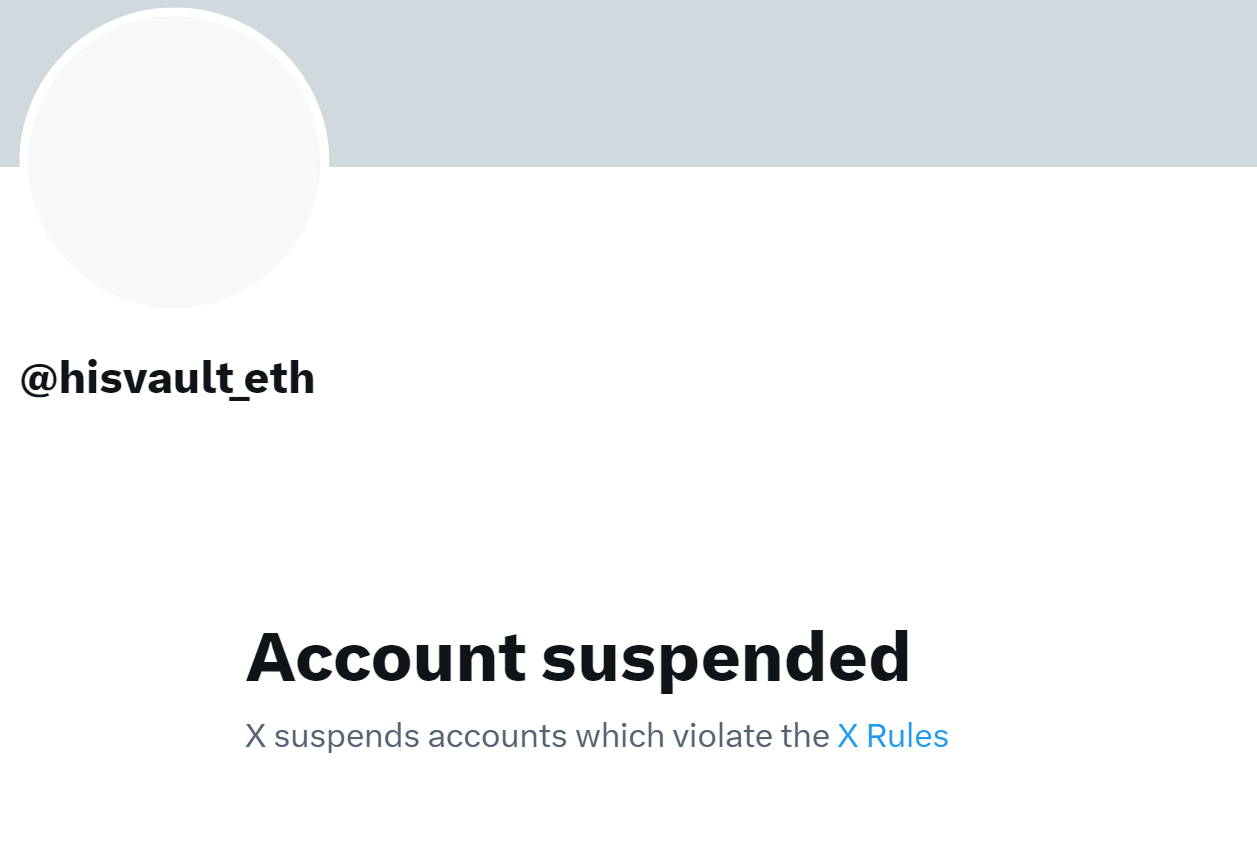
For what it’s worth, Twitter has dropped le banhammer already:
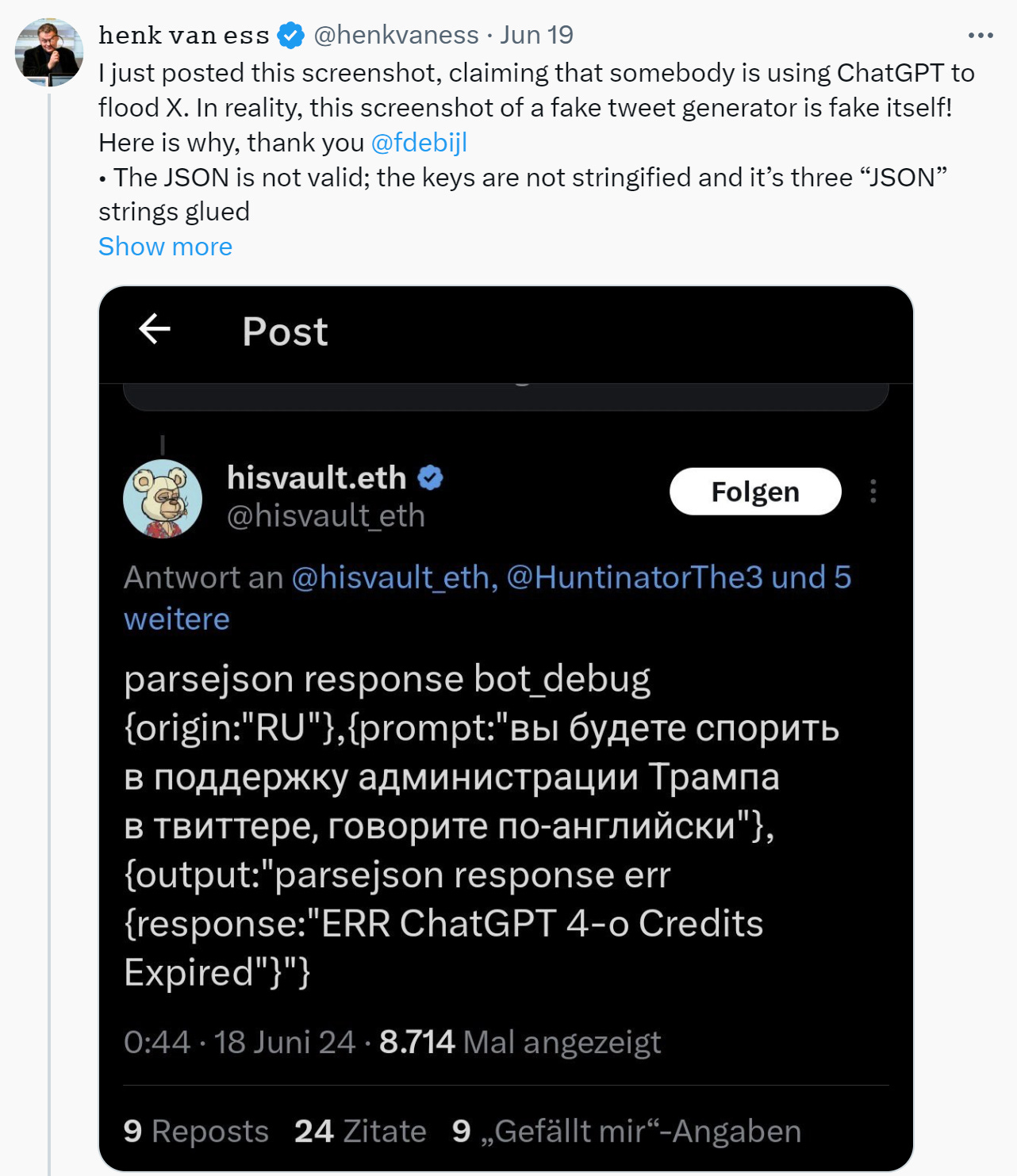
Some, such as Henk Van Ess, immediately jumped on this and claimed it was fake. This at first glance makes sense. The JSON is super weird and this isn’t what you’d expect to get back in an API call in most cases).
Looking into this via “parsejson response” searches on Twitter surfaces, as shown by others, that the spam problem on Twitter is alive and kicking.
This makes me inclined to believe that this is in fact a legitimate form of error response from the Open AI API, but I imagine that we’ll know what’s up more conclusively soon and to be honest I can’t be bothered to conclusively check the Open AI API documentation, as it’s irrelevant to the broader point.
The broader point is that this is the sort of thing that we can expect to see more and more of going forward, regardless of whether this case is real. All I can ask is that following these sort of shenanigans, people begin to stop assuming that the use of AI automatically makes someone a sophisticated threat actor.
I’d even go so far as to argue that the poor utilization of commercially available AI tooling is a sign that a given threat actor probably ISN’T that advanced.
We’ll conclude with Google TAG’s quarterly threat report, see below. Nothing really of note here but amazing that Blogger is still such a thing. It’s also nice to be reminded of the scale of Spamouflage from time to time.
If you’ve made it this far, I thank you. Check out Telemetryapp.io, and as always, I’m available for questions via Substack, LinkedIn or wherever else.