My Brother in Zhongguo
Welcome to Memetic Warfare.
Margin Research has put out a great follow-up to their longer piece on Chinese cyber militias available here.
This topic is especially interesting to me as it dives into a general concept that we’re still working on in the IO/cyber space: cutouts/civilian companies (or front companies). Many countries have real contractors that do IO or cyber work for them, such as the US, but many also choose to use contractors as well as front companies, such as Russia and Iran. China of course uses both as well, but also has its own unique model of cyber militias. What makes it unique is the following point from the article:
They also deserves some real credit for busting out the trinity meme. Great work, my brother in Zhongguo.
I’ll skip some of the content, though you should read it, to get to the final point: cyber companies can be/are integrated, at least partially, into the Chinese military/defense apparatus:
That means that companies that we’ve discussed here such as Qihoo 360 aren’t necessarily “just” private-sector firms working in the interests of China, but rather may be integrated actively into Chinese defense efforts.
The MSS has also engaged in another case of IO, this time against Australia.
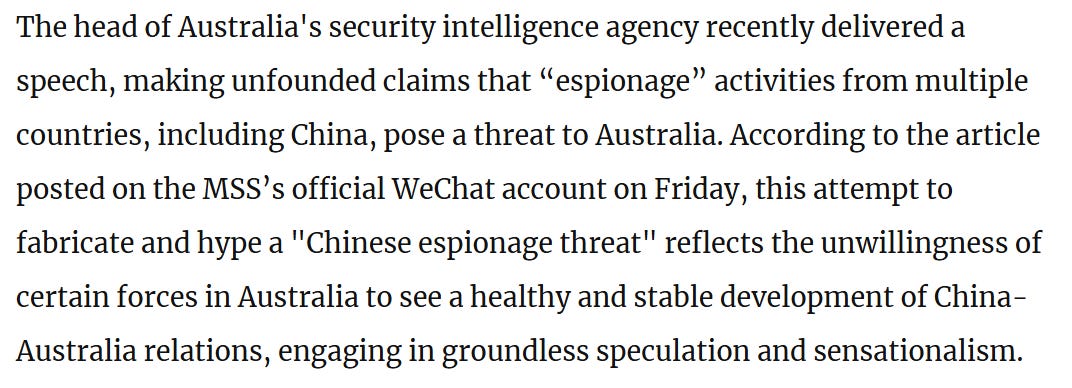
This article, rebuking Australia following a speech from a head of one of its intelligence agencies about Chinese espionage, follows the main trope of Chinese denials of attribution.
Firstly, the relevant Chinese agency accuses the country that attributed or called out their activity of doing the same thing:
Australia, like every country, undoubtedly does collect intelligence and engage in espionage in China - the difference here is that China categorically denies ever doing so. The next step is pointing that out, in this case referring to the new variation of the “China Threat” theory:
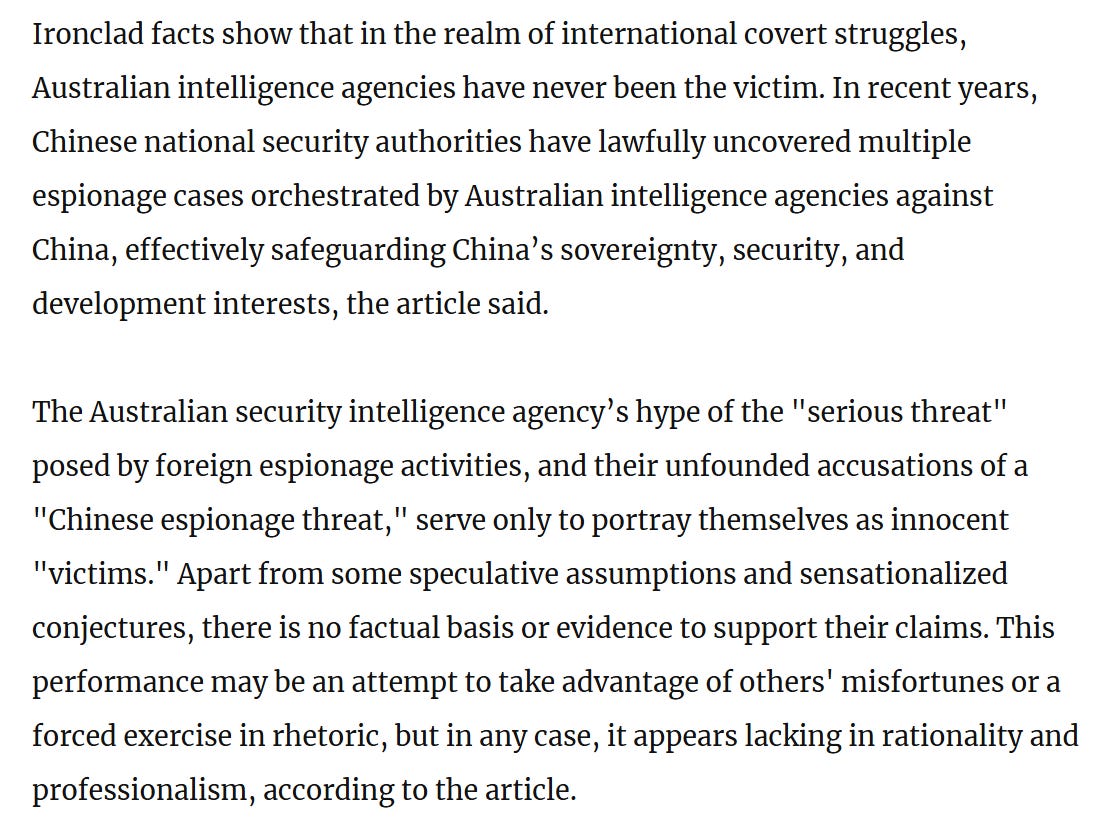
Lastly and in seemingly classic fashion by now, the Chinese claim to have legally uncovered multiple cases of Australian espionage.
Essentially, and as we’ve seen with the CVERC, China is incapable of discussing espionage/intelligence/cyber and so on and instead chooses to engage in a clear pattern:
Gaslight
Gatekeep
Girlboss
Jokes aside, Chinese actions as shown via the CVERC, MSS, MPS and other organizations couldn’t be clearer: Following foreign accusations or attributions of Chinese activity, China then denies that it has ever engaged in that activity, accuses the accuser of having engaged in that activity against China, and then makes up some cases (real or not, mostly not) to make their point.
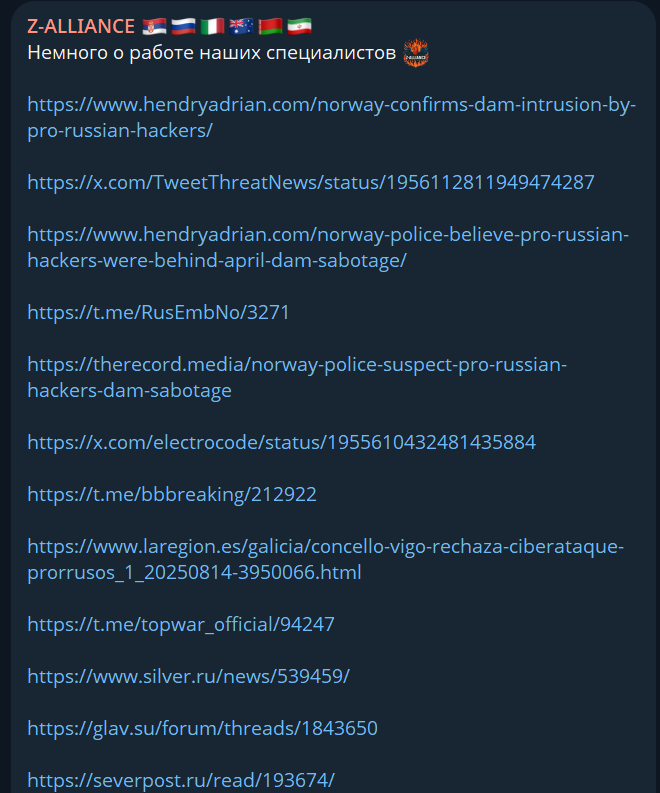
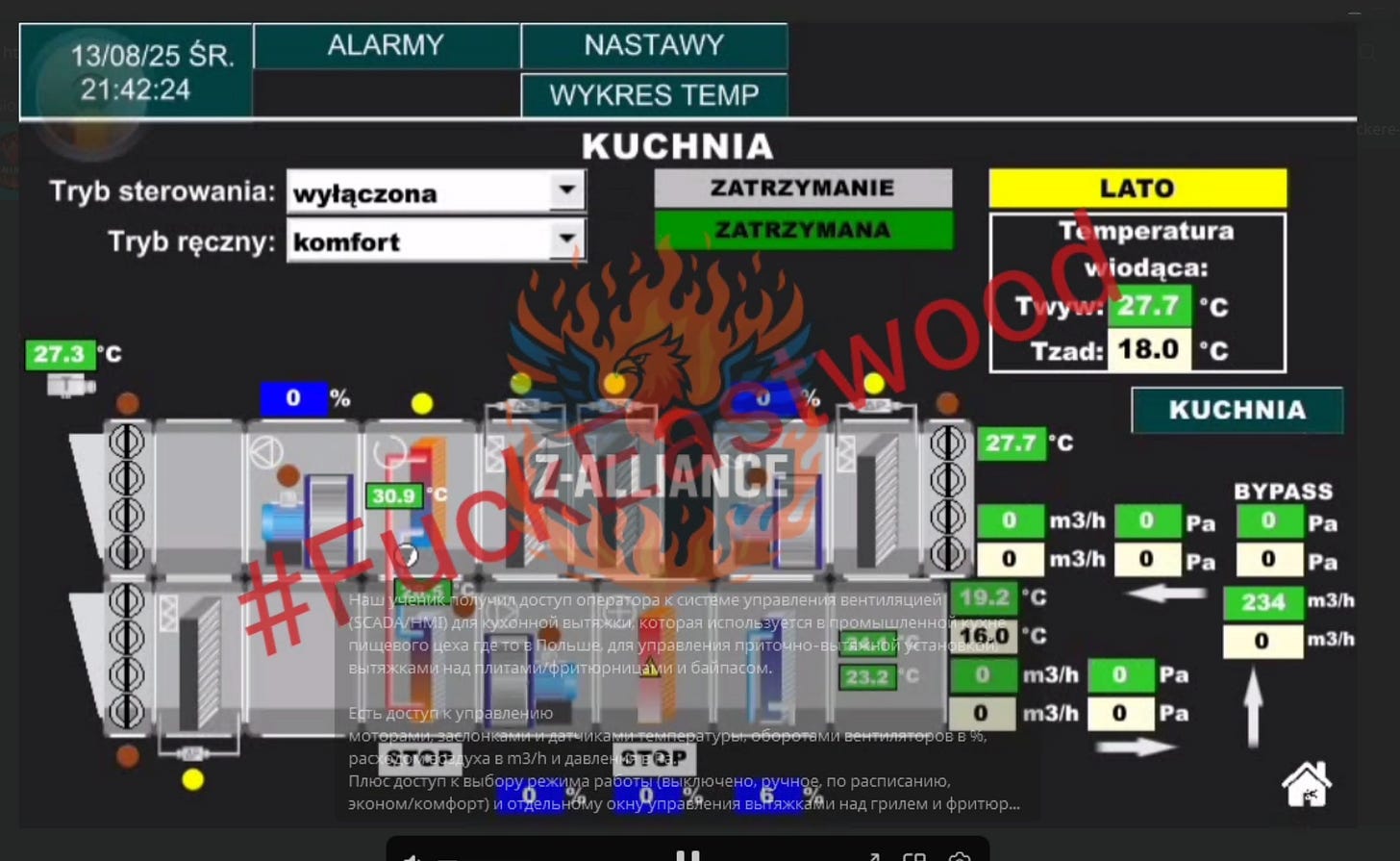
In other news, attacks on water infrastructure in Europe have been a hot topic lately, with both Norway and Poland publicly stating that they’ve been attacked, and in Norway’s case blaming Russia for it as the attack actually succeeded.
Pro-Russian hacktivist group Z-alliance has taken credit for it, though it has been known as the group behind it for a while:
Z-Alliance claims to be affiliated with APT 28 (using that framing, funnily enough) and also Noname05716, which was recently targeted by EuroPol.
They’ve been out there wilding as of late doing everything from DDoSing to targeting PLCs and other systems in water and desalinization plants in Europe, so definitely a group to keep watching going forward.
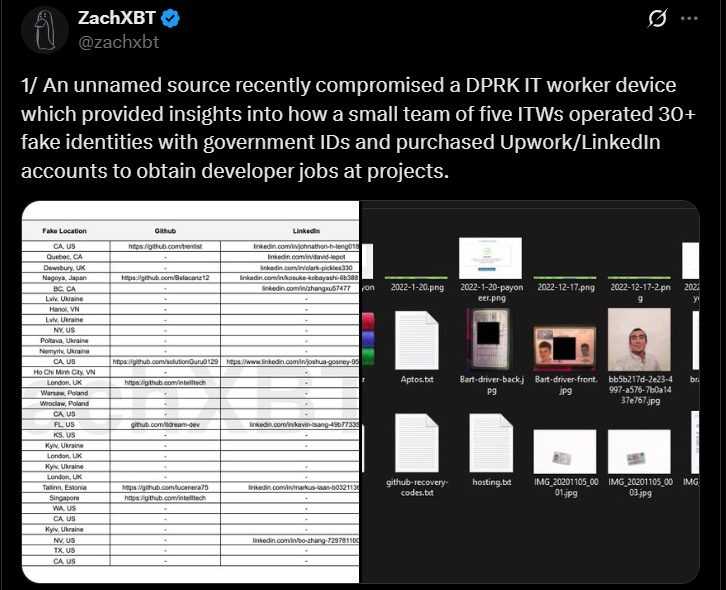
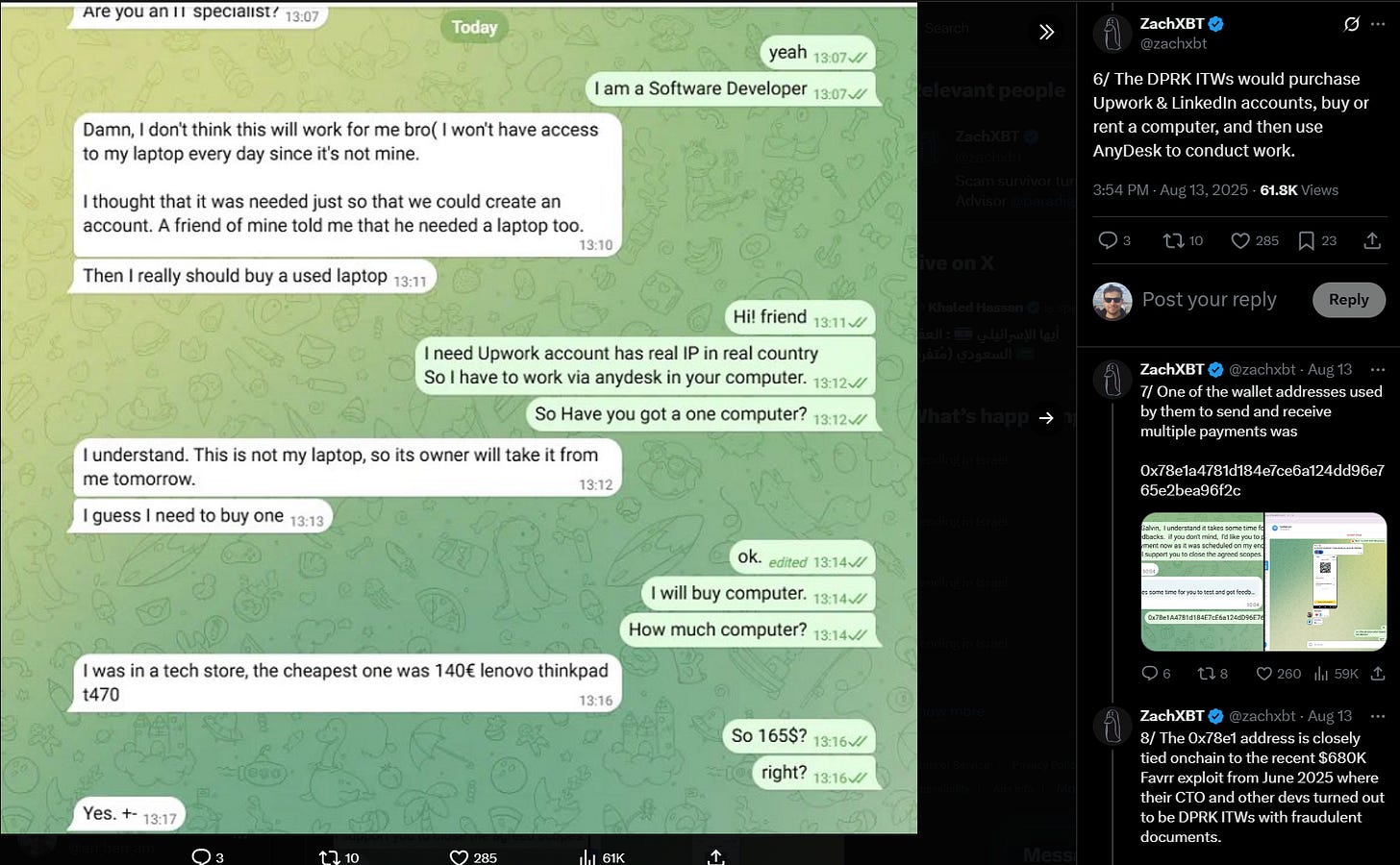
We’ll conclude with a look from ZachXBT at DPRK IT workers and their use of Google products, available here. Received from an “unnamed source”, the data shows how DPRK IT workers run fake identities and use hacked freelancing platform accounts to get jobs.
Compromising freelancer accounts for initial access is a great idea and very creative. Most notably, the DPRK IT workers are showing how literally anyone could in fact pull off cyber or IO with just free resources available from legitimate providers as well as affordable illicit resources available on any criminal forum.
For example:
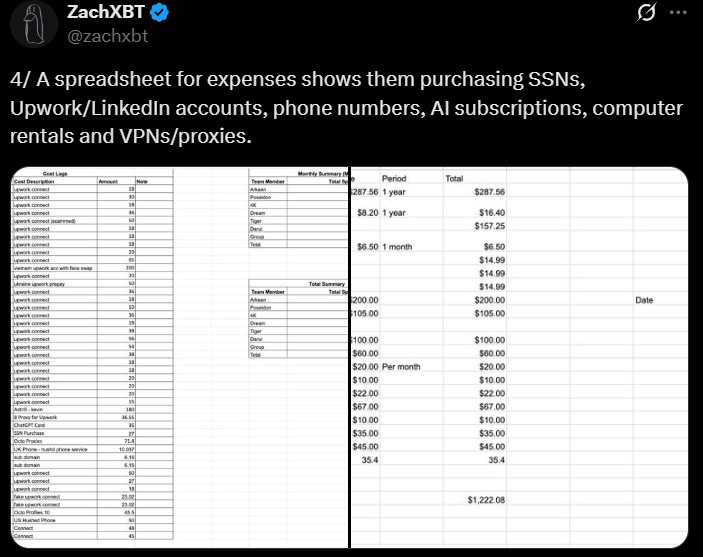
The use of laptop proxies is also fascinating IMO:
I’ll reiterate my point: every single element of this activity could be replicated by your average person or small team with a small budget.
On that positive note, thanks for reading.