MWW: Press VirusTotal to Pay Respects
Welcome to Memetic Warfare Weekly!
My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
Before we begin I’d like to give a shoutout to my friend Skip Schiphorst, who runs a number of language-oriented OSINT courses. His flagship course focuses on the Chinese internet, available here. Skip works hard so there are multiple dates coming up for the course:
25 - 29 Sept 2023, 13:30 - 17:00 CET
13 - 17 Nov 2023, 08:30 - 12:00 SGT
11 - 15 Dec 2023, 13:30 - 17:00 CET
I’m also happy to offer a promo code that will give a 10% discount for MWW readers - IINT102023. If interested - let me know or reach out directly to Skip. I’d definitely recommend his courses to those who wish to improve their research capabilities in languages that they don’t speak.
On that note, let’s begin:
Summit Old, Summit New - Graphika
Graphika has published a report on two Russian information operations, which they believe to be potentially part of operations Doppelganger and Sekondary Infektion. These operations targeted NATO’s 2023 Summit in Vilnius, as well as Lithuania itself.
The report is worth reading in its entirety, and there’s no need for me to summarize it for you here. Let’s go over a few of the key points though:
Firstly, and this is perhaps most important - the operations weren’t effective. According to Graphika, there as little real world traction from the operation’s activity, and even pro-Russia propagandists called it out as suspect. Rybar coming out swinging against the domain is something that I wouldn’t have foreseen, and shows how oftentimes IO is done by compartmentalized teams across disparate organizations, and often not planned centrally or effectively.
The operations notably utilized typosquatting - the creation of either similarly spelled, yet misspelled domains (or in some cases the same domain name but on a different top level domain). For example, Nato.int became Nato(.)ws. This is commonly done as part of phishing attacks or watering hole attacks, but is also increasingly utilized in IO, especially by Iran and Russia.
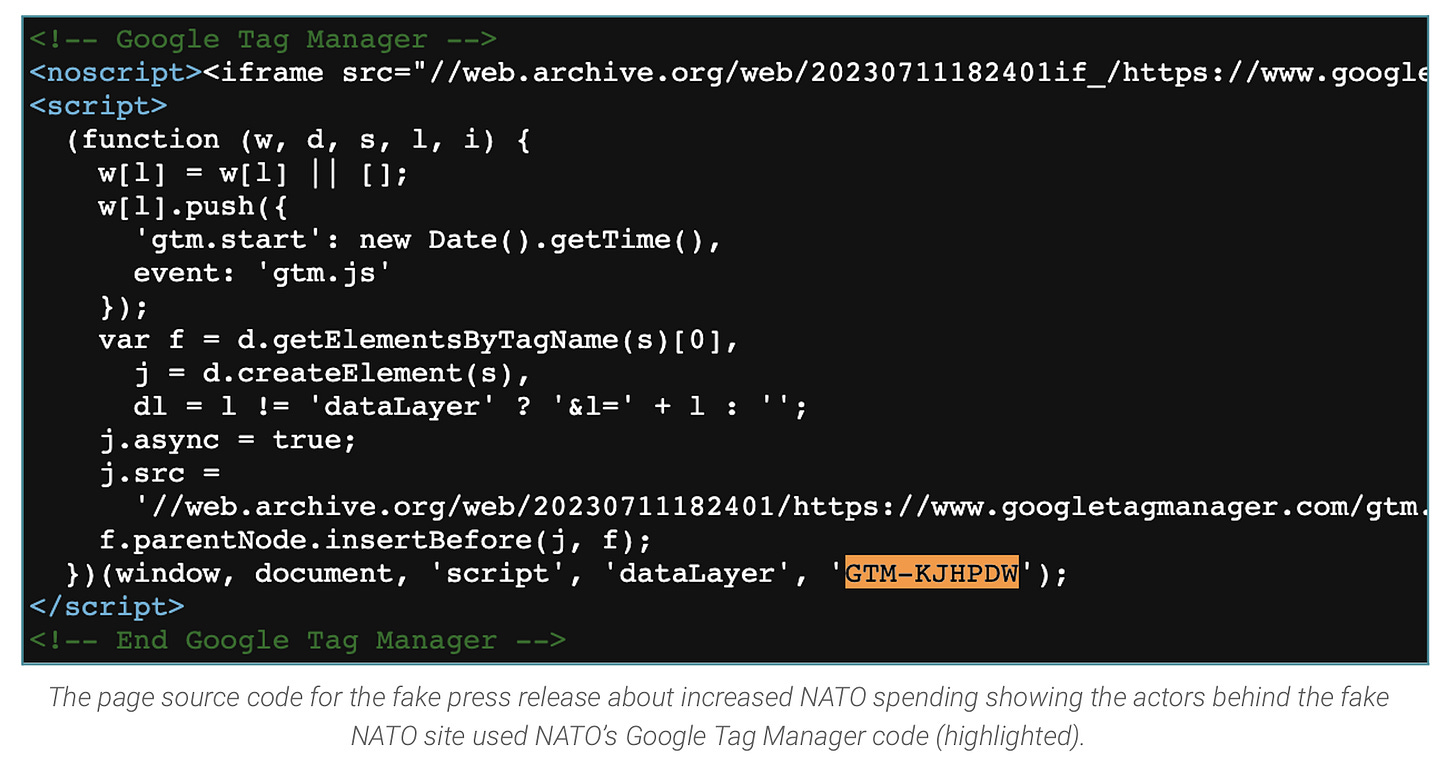
Next, one of the operations effectively copied the original NATO domain. This is a common TTP used by Russia, primarily in operation Doppelganger. This extended - either purposefully or not - to the Google Tag Manager code on NATO’s site.
The fake NATO domain was, alongside two other domains, amplified by a network of over 600 Twitter (sorry, X) accounts. Notably, redirects via Twitter accounts were a unique TTP used by this organization, which used those redirects to mask the end destination of a given URL.
As an aside - whoever created these accounts made some interesting anime deep cut references - Kuroko no Basket is one I wouldn’t have foreseen being used.
I’ll give technical attribution credit as well - the report attributes the domains as being tied by not only having shared design elements, but also the use of the same control panel provider:
My little review here only covers the Doppelganger-affiliated operation - the report further elaborates upon the Sekondary Infektion subset, so go read it!
Press VirusTotal to Pay Respects
On an additional note - let’s take a look at one of the domains from a different perspective. One of my favorite tools for domain analysis is VirusTotal, so let’s throw the URL in there.
So far, clean for AV detection. Let’s take a look at the other tabs:
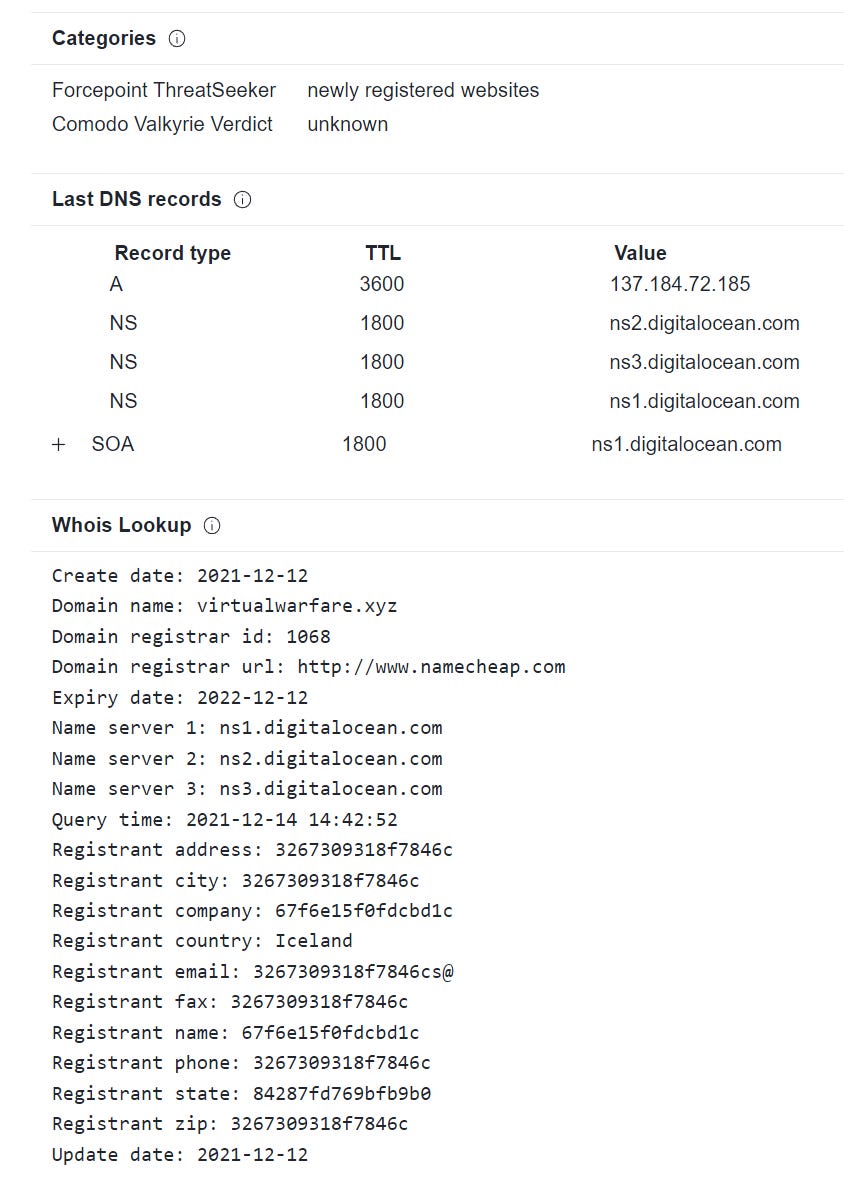
Nothing interesting in the WHOIS lookup, and it’s registered via Digital Ocean - which interestingly is an increasingly common cloud provider for IO/Cyber ops as its KYC is seemingly weaker than other providers. I’ve seen Digital Ocean used for a number of malicious C2 servers recently that really shouldn’t have passed.
From here, let’s look at the “Relations” tab.
Here we have some more interesting results. The domain has been hosted on just one IP, which has been flagged as malicious by just one provider. Interestingly, the domain also has a seemingly nonsensical subdomain hosted on a different IP address - we’ll come back to this soon.
Let’s take a look at the original IP - hosted by Digital Ocean.
This host has only hosted a small number of domains, indicating that it’s probably a VPS (virtual private server)rented by just one threat actor.
The domains hosted on it are highly suspicious, and appear to be typosquatting domains used as part of presumable phishing attacks - one of them also has a nonsensical subdomain as well, which is interesting. Note also that the domains hosted on this IP have also changed rapidly - with new domains being added in some cases over the course of several days. This is commonly done with VPSes used as part of infra for cyberattacks.
We don’t have enough information here to conclusively say that this is a VPS used exclusively by the same threat actor for malign purposes, but I’d say that we could reasonably assume that that is the case based upon the above indicators.
Let’s move on to the IP address that hosted the subdomain in the previous domain. Here we have a lot more information: the SSL cert is self-signed (i.e. highly suspicious), the IP address has been used historically to host at least 200 domains - many of which are highly malicious and clearly phishing domains.
The host also appears to be a C2 server for potentially 946 different files! Pretty staggering amounts of malign activity.
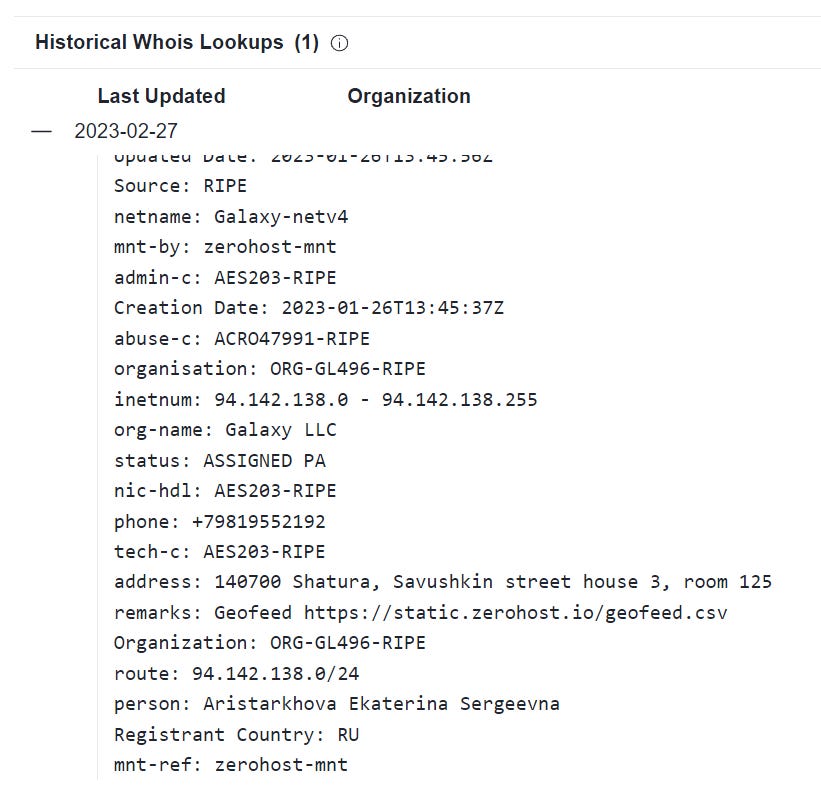
Looking at the historical WHOIS via VirusTotal shows us that the IP address is owned by a Russian provider, Galaxy LLC - based in the below listed address and registered under one Aristarkhova Ekaterina Sergeevna. We could go further and look into this hosting firm, but that’s beyond the scope of this post.
So the above host is definitely utilized by presumably a number of, or potentially one very active, threat actor (s) for malign cyber activity. This is also crucial for attribution for the above information operation exposed by Graphika - just by looking at a subdomain of one of the dissemination sites, we can uncover masses of other malign cyber activity as well as more direct ties to Russia - thus aiding our overall attribution efforts. If I had the time to do so, I’d look at the other network domains and see what else could be found via technical indicators.
What’s the lesson here? Simple. OSINT and CTI are one and the same, and VirusTotal is an incredible tool for both.
That’s it for this week, thanks for reading!