MWW: Imagine (Too Many) Dragons Edition
Welcome to Memetic Warfare Weekly!
My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
Imagine (Too Many) Dragons
Much good-natured fun was had at the expense of Microsoft for its recent decision to give APTs silly names. Such naming conventions are still par for the course for IO. Recorded Future bursted on to the scene the other day with their report on their tracking of a Chinese IO group “Empire Dragon”, report available here.
See below a scientific and sophisticated representation of the current state of IO naming conventions:
Recorded Future has claimed that there is some overlap with their report and others, which doesn’t shock me.
We can even see some examples of content overlapping, for example, the “182:1” headline below being identified in RF’s report as well as Meta’s list of headlines (see below).
So, summarizing the above - it seems that all roads lead to the same network/cluster of networks investigated by different organizations, which in of itself is an interesting phenomena!
Ribbing about the naming aside, it’s great to see RF get into publishing long-form, technical IO research. Let’s look at Meta’s report now:
Meta Q2 Adversarial Threat Report
Meta’s quarterly threat report has been released for Q2 2023, and this one - as they usually are - is pretty impactful for the industry.
I used to go more in depth into all of the various aspects of each threat report, but frankly I’m tired and this one is a banger/too long. Insomuch as brevity is divine, I won’t go over all of the different sections on Iran, Turkey and so on but will rather focus on China.
For those curious, the specific section I’m referring to is the “China In Depth Analysis” section.
In this report, Meta claims to have taken significant action against Spamouflauge (see more on attribution from Adam Rawnsley below), taking down over 7,000 accounts, hundreds of pages and dozens of groups and Instagram accounts. Meta’s Head of Global Threat Intel, Ben Nimmo, has called this one of the biggest information operations ever.
As a side note, the disparity between accounts and pages and groups and IG accounts is interesting - there may be less policy willingness to take down groups as they presumably have “real” people active in them, whereas individual accounts and pages are standalone entities.
Beyond that - let’s discuss some of the new findings on Spamouflauge as discussed in the report:
Firstly and most noticeably is the platform diversity in the operation. Spamouflauge has covered dozens of platforms, sites and forums - more than commonly seen in most Russian operations.
Spamouflauge outsourced engagement and liking/sharing of accounts and pages to third parties in Vietnam, Brazil and beyond - as this behavior is hard to scale automatically.
Presence of ad funding across all mentioned operations shows that tracking money and ad funding is a key indicator for Meta and presumably other platforms.
The above points help our overall understanding of this sprawling operation, but in my opinion what was really interesting were the investigation and attribution methods used:
Temporal Analysis - Meta used temporal analysis of operation activity to understand the operational patterns of the operators. This is always a fun area of overlap between IO and CTI investigation as both use this frequently to attribute actors.
Downside - this is only really feasible for internal teams with access to proprietary data at scale.
One of the interesting methods also used - historically as well, not just here, is identifying the reuse of infrastructure. Reusing infra is a key OpSec breach/overlap in IO/CTI, as it can be used as a pivot point tying together seemingly disparate accounts, servers, malware families and more depending on the operation.
Additionally, utilizing American infrastructure as well could also limit the possibility of American government agencies, FBI excluded, investigating effectively as many can’t investigate domestically.
Perhaps my favorite part of this whole report is the use of text itself as a pivot point and indicator, similar to say hash files as an Indicator of Coordination (IoC).
Unique text can be very easily pivoted upon in platforms or via engines, so treating it as such - quite useful. This is an underutilized element of IO investigation.
Meta also took the next step of treating text as an IoC - sharing it en masse in the report as a threat indicator. More of this please.
Note also how the scale here means that most headlines are low quality.
Doppelgänger, Doppelgänger, Doppel Doppel Doppelgänger
Let’s look briefly at a few of the findings from the investigation into Operation Doppelganger in brief. The operation is sprawling, so read the report for context. A few points:
The most notable element of the domain was the mass use of domains, which isn’t easy to do and comparatively easily blocked by platforms:
The ease of blocking forced many of these domains (remember the blog post on Ukraine Inc?) to use redirects and backup domains to be shared on Meta platforms:
Great to see XYZ TLD being utilized for reasonable purposes:
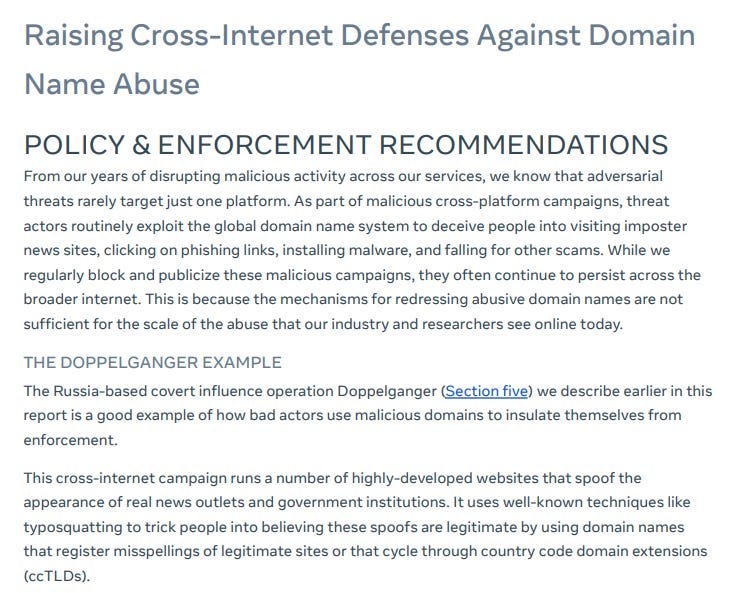
The next great development of this report is that Meta, as one of the largest companies in the business, is attempting to lead with policy and enforcement recommendations. The main focus here is towards reforming WHOIS procedures, legal procedures and more - there’s a lot more potential in this specific field:
Going back to the Chinese operation quickly:
Adam Rawnsley, one of the best IO-related resources out there to follow, published a great article on the exposed operation, available here.
The main finding is that Rawnsley has attributed Meta’s own reporting to the FBI’s indictment of the Chinese’ Ministry of Public Security’s 912 Working Group as the organization behind Spamouflauge. How, you may ask? Read his article, but I’ll spoil it a little: via shared content and other indicators.
Some key quotes from the article, in which Rawnsley interviewed Ben Nimmo:
“Once you put everything together from 2019 until now, it is the largest known covert influence operation,” Meta’s global threat intelligence lead Ben Nimmo says in an interview.”
People love to harp on about Russia in this field, but perhaps China is just as capable - if not more so?
Another point that I insist on frequently is that many operations aren’t actually focused on quality but rather on clicks, shares and metrics, which Nimmo claims here as well:
“It always comes back down to this question,” Nimmo says, “of who’s kidding whom here? To what extent are [Spamouflage Dragon] targeting foreign audiences and to what extent are they targeting the people who might be paying them – to make them think that they’re reaching foreign audiences?”
Part of what helped make this operation so large and impactful was its utilization of outsourcing for engagement - showing that certain capabilities are still not feasible to be run in-house for many governments.