MWW 7 - Panic! In the Discord
Loose Servers Sink Ships
Welcome to Memetic Warfare 4! I’m happy to have you here. My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the counter-influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I also provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
In this week’s edition we’ll focus on what may be the most important leak of American military documents since Snowden- see below:
Stealing (War)thunder
The grand tradition of leaking sensitive military documents via videogame-related platforms continues unabated with the recent leak of sensitive US military documents.
I, for one am glad that videogames and their relevant platforms are taking such a prominent role in both suspected-IO activity and in general in our day-to-day lives as it is:
Funny.
Advantageous to me, as someone who has used these platforms for years and thus is familiar with them.
Warthunder was the first notable situation of a videogame - in this case, a related forum - being used to publish separate leaked Chinese military documents on a number of occasions.
Social media, messaging applications and other online platforms are most certainly not new to being weaponized. Discord servers, for example, have been used as C2 servers in the past for cyber operations and can be easily configured to enable a variety of types of benign and malign activity.
All of this is to say that we are living in a brave new world of the internet. The “deep web” of Discord servers was deep enough to prevent the American government from being aware of a massive leak for over a month. Messaging applications - from Telegram to Whatsapp to Discord and beyond - all provide varying degrees of anonymity and privacy for their users, and most importantly aren’t indexed or searchable for their public content, making it incredibly difficult to investigate.
The “black box” of messaging applications of various kinds poses an issue not only to the average investigator, but also to massive government bureaucracies.
On that note, let’s dive into this week’s main focus: the Pentagon leaks and their potential exploitation by Russia as part of a suspected hack and leak IO operation.
Panic! In the Discord
What a week it has been for IO and Discord-related memery and antics.
There have been initial reports of leaks of sensitive (TS) military documents from the Pentagon being disseminated - where else - on a variety of Discord servers, and later other social media platforms.
The leaks, amazingly, seem to keep coming as well, with more reporting today of a new tranche being leaked, with the documents themselves being initially leaked in early March. It’s unclear still whether this is just a leak or an actual hack-and-leak or something in between - some people have come out conclusively on either side.
So far it seems that the US government has confirmed that most documents at least were authentic originally prior to any potential altering. The Republic of Korea has already released a statement saying that the leaks were at least partially altered and meant to make the alliance between the US and the ROK look bad.
What is clear is that these documents are being actively promoted by suspected Russian assets online: be it on Twitter, Telegram, 4Chan and beyond.
It’s unclear to which degree these leaks are in fact authentic or legitimate, and whether or not they’ve been manipulated or edited - we’ll take an inconclusive look at this below briefly.
Aric Toler of #Bellingcat published a thread on Twitter (which later turned into an article on Bellingcat’s site) in which he identified the earliest post of the leaked content not on 4Chan's /Pol/ board (available here) as thought earlier, but rather from Discord servers (screenshots here). Notably, according to Toler, these leaks have been in the wild since early March and comprise potentially 100+ documents.
The leaked documents themselves claim that Ukrainian losses are much higher than reported while Russian losses are much lower than reported - some highly original thinking on the parts of the editors here.
Eric Ellason looked into “MrLucca”, the leaker on Discord identified by Toler. As per Toler, Lucca claims to have received these documents from a different Discord server, but regardless - Lucca himself appears to be quite the fan of the “Orchestra” as shown below. I certainly wouldn’t take these documents at face-value.
Toler and other commenters pointed out numerous errors and oversights in the documents - such as flipping "61" to "16" in one case. Some real big brain energy here from later editors.
IMAGE REMOVED
A number of these documents as well have suspicious linguistic indicators - Molfar has also done some work that emphasize the suspicious nature of some of the documents.
Molfar pointed out that throughout the documents, the Wagner group is referred to as “Vagner”. This to me is quite odd, as almost all official references to Wagner are spelled with a “W”, but there are a minority with a “v” in some semi-official sources. I also would note that the order to me sounds off - personally, I’d place “PMC” after “Wagner” and not before it.
IMAGE REMOVED
Molfar also pointed out that the documents don’t adhere to NATO guidelines on the use of the metric system:
IMAGE REMOVED
Additionally, Molfar points out that the date convention used is not typical of American documents:
IMAGE REMOVED
Not all of the above indicators, other than spelling Wagner incorrectly, appear to be incredibly strong in my opinion, as they could be feasible errors otherwise. However, the presence of numerous potentially coincidental errors is certainly suspicious, and warrants a deeper look at these documents.
There are some serious questions here.
Are these leaks in fact authentic documents or are they forgeries?
If authentic in origin, have they been manipulated or edited?
If manipulated or edited, at which stage were they edited?
The above document, for example, appears to have been lazily edited at least once following its initial leak.
It’s unclear how reliable these documents are and we should most definitely take them with the largest grain of salt imaginable - even small amounts of Russian manipulation/editing of these documents could drastically change their overall impact.
Considering the total number of documents and their content, I would venture a cautious guess that the majority, if not all of them, were originally authentic - creating such a large number of documents from scratch would be quite difficult. However, tampering with these documents for whatever reason would be infinitely easier, and even forging a few additional documents here and there could be also easily done.
Let’s see what we can do with example of one of these documents though by ourselves. While it may seem that we're stuck with looking for spelling errors or other qualitative issues with phrasing or so on in the document to debunk it, there's in fact more that we can do even without a high level of expertise.
We can take one of the images in the leak and analyze it using image forensics tools, such as Forensically or the InVid “Fake News Debunker”.
Please note: utilizing these tools, especially by people not specialized in image forensics (I am certainly not an expert in image forensics), can lead to false positives and potentially false negatives as well. As such, only derive findings from these in a very, very cautious fashion and ideally after consulting with actual experts in the field. Having said that - let’s take a look at what we can find.
The InVid tool features an excellent image forensics module with explanations as to what we see. Below I’ve turned on the “Double Quantization” feature, which as per InVid:
“Double Quantization inconsistencies occur when a foreign object is inserted in a JPEG image. When the new image is saved, the untampered part of the image will have been compressed twice, while the inserted region only once. In this case, the tampered area should appear light-colored (see the scale) while the rest of the image remains dark. If other colors are present (green, blue) then no conclusion can be made. Also, the light-colored region must be object-like : spurious light dots scattered across the image should be ignored.”
IMAGE REMOVED
We can see the above dots in a pattern on a black background for the same image:
We can then also utilize error level analysis to further investigate this image, and we see additional patterns that are similar to Double Quantization emerge as well. More about error level analysis below:
“Error Level Analysis is produced by recompressing the image as a JPEG of quality 75 and subtracting the new image from the old. The resulting image of differences is then enhanced and displayed. Areas of interest are those with higher values than other similar parts of the image. Only similar regions should be compared, i.e. edges should be compared to edges, textures to textures, and uniform regions to uniform regions. Color discrepancies (commonly blue regions) are also generally suspicious. ELA is an enhancer and is not enough to conclude about an image forgery.”
While the above aren’t enough for amateurs in the field such as ourselves to determine that the above image is in fact a forgery, there are some signs to look at:
Similar patterns for error level analysis and double quantization
Signs of significant editing that overlap with notable locations on the document:
Text/Stats in the left-hand side - “associated losses” etc
Editing in the title/header
Page numbers on both sides
Other editing in areas across the document
While we still can’t make sweeping claims about the document at this stage based just upon this, it’s certainly interesting. These documents warrant further, more advanced technical forensics.
The Hacker Known as 4Chan
While initially I had planned on emphasizing the role of 4Chan in disinformation and hack and leaks, it seems to have not been the true origin. However, it’s still relevant, so let’s discuss it.
4Chan is a common tool for seeding disinformation and hack and leaks - perhaps most famously Russian leaks targeting Macron (Macrongate, see below), but there are numerous others.
Source: https://mediamanipulation.org/case-studies/muddy-waters-forged-macron-leak
While we’re already discussing 4Chan, let’s discuss a few key elements and some investigation tips about it before diving into the actual leak.
4Chan is a key source of information for OSINT analysts for geopolitics/extremism/disinformation/general memes/more. I’m a frequent reader of /pol/ myself, but the most important reason to follow 4Chan is that it serves as a nexus of activity.
This harkens back to MWW’s previous post on source development - work smart, not hard. Relevant disinformation content is often posted first on 4Chan and then spreads either naturally or via inauthentic amplification to other platforms. Information operations often utilize 4Chan for seeding content for a variety of reasons:
Incredible ease of posting anonymously (and can even mask posts with meme flags).
Presence of pro-Russia/FRE/China/Iran apologists makes it easy to “blend” in.
Functionally no content moderation - “janitors” only take down overtly illegal content.
Easy to manipulate - cross-post, forum slide, etc.
Nature of the community - 4Chan anons are quite energetic and will often actively promote content both on other boards of 4Chan but also on other platforms.
Even if a given piece of interesting content isn’t posted first on 4Chan, it will almost definitely make it to 4Chan as one of the first platforms it is posted on, making 4Chan, and /pol/ in particular, a key source to follow.
So, how can we investigate 4Chan more effectively?
The first thing to know is which board to visit. I won’t go into the history of 4Chan here as it would take too long, but for any follower of this blog, the board that you’ll want to spend time on is /pol/, short for “politically incorrect”. There are other boards that can be relevant - /k/ for firearms, /r9k/ for other content, /b/ if you hate yourself and so on, but /pol/ is really the place to be.
Once you’ve identified your boards, you can begin investigating. We’ll focus on /pol/.
4Chan boards vary, but /pol/ is based upon 10 pages of incoming/outgoing content - as new content is posted, old content gets pushed back further and further to the point where it hits 10 pages, and then disappears.
The “catalog”, available in the upper left-hand corner of the posts (see above), shows all of the threads active in /pol/ at a given point in time, so you can easily select the thread most relevant to you.
When doomscrolling, look out for out for “X” General Threads - Donald Trump General, Ukraine Happening General and so on. These threads are general discussion groups for certain topics and often have relevant content posted as responses to the thread itself (as happened in this case).
Once you’ve identified relevant threads and content, we can begin investigating users. Users on /pol/ are anonymous, but they do have a unique user ID which we can use to track their posts across /pol/. Look at the below screenshot from Toler’s thread:
IMAGE REMOVED
We can see, next to “Anonymous”, the ID: CXWfLHRB, which is the user ID assigned to this individual across /pol/. We can also look up post numbers in a given thread ( No.422411747 above) but this just finds mentions of that specific post. If searching for posts, searching by text match is often effective also.
4Chan has its own archive next to the catalog on the homepage, but if you’re looking for historical content I recommend that you check out 4plebs.org. In addition to having a great name, 4plebs is incredibly useful as it archives content on a number of key boards:
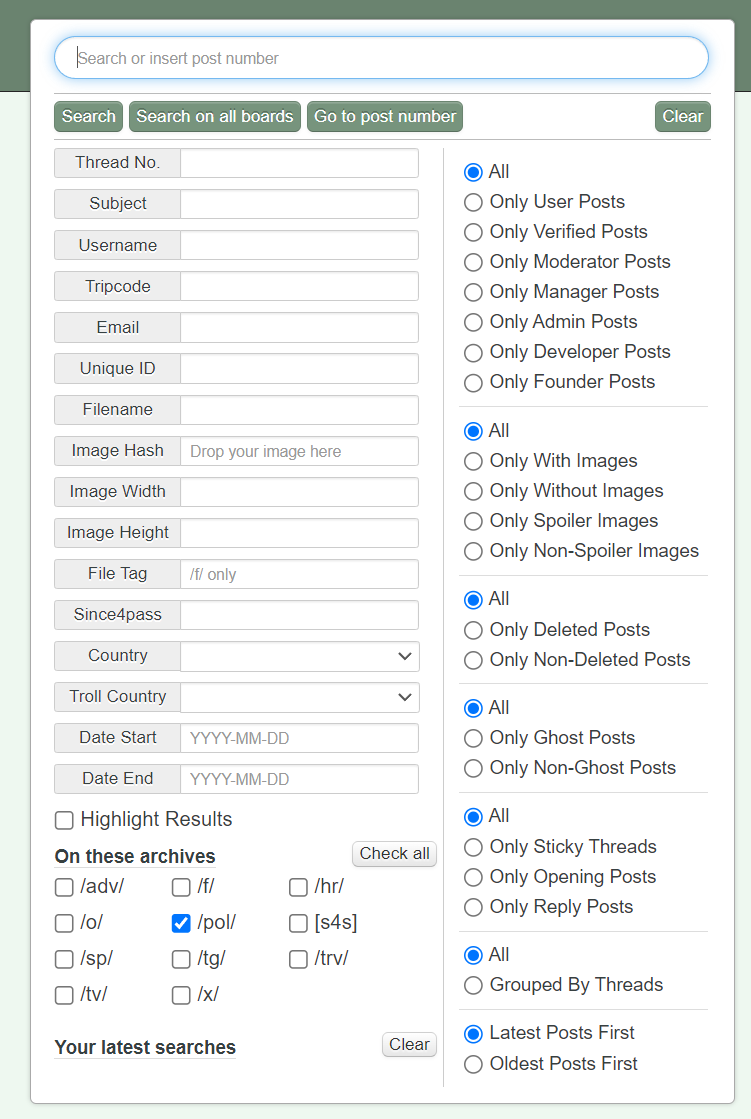
4plebs not only archives a number of boards, it also has an advanced search feature which is much more powerful than 4Chan’s native search:
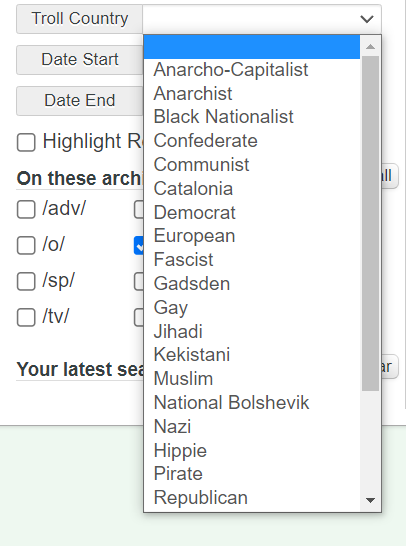
Note that here we can search by a lot of powerful methods, such as Memeflag/Troll Country:
While the above is a lot of fun and useful for some research, the real value is in the ability to reverse search images via image hash and search by file name. 4plebs has some great capabilities, and I’ve used them to even write academic articles in the past.
To summarize, 4Chan is a powerful source of information, memes and top kekery for analysts of all stripes, and with the right understanding and tools, you too can weaponize armies of anons for your own investigations and analysis.
Thanks for joining this week’s Memetic Warfare Weekly - I look forward to hearing from you via LinkedIn or ari@glowstickintel.com.