Meming Well is the Best Revenge
Welcome to Memetic Warfare.
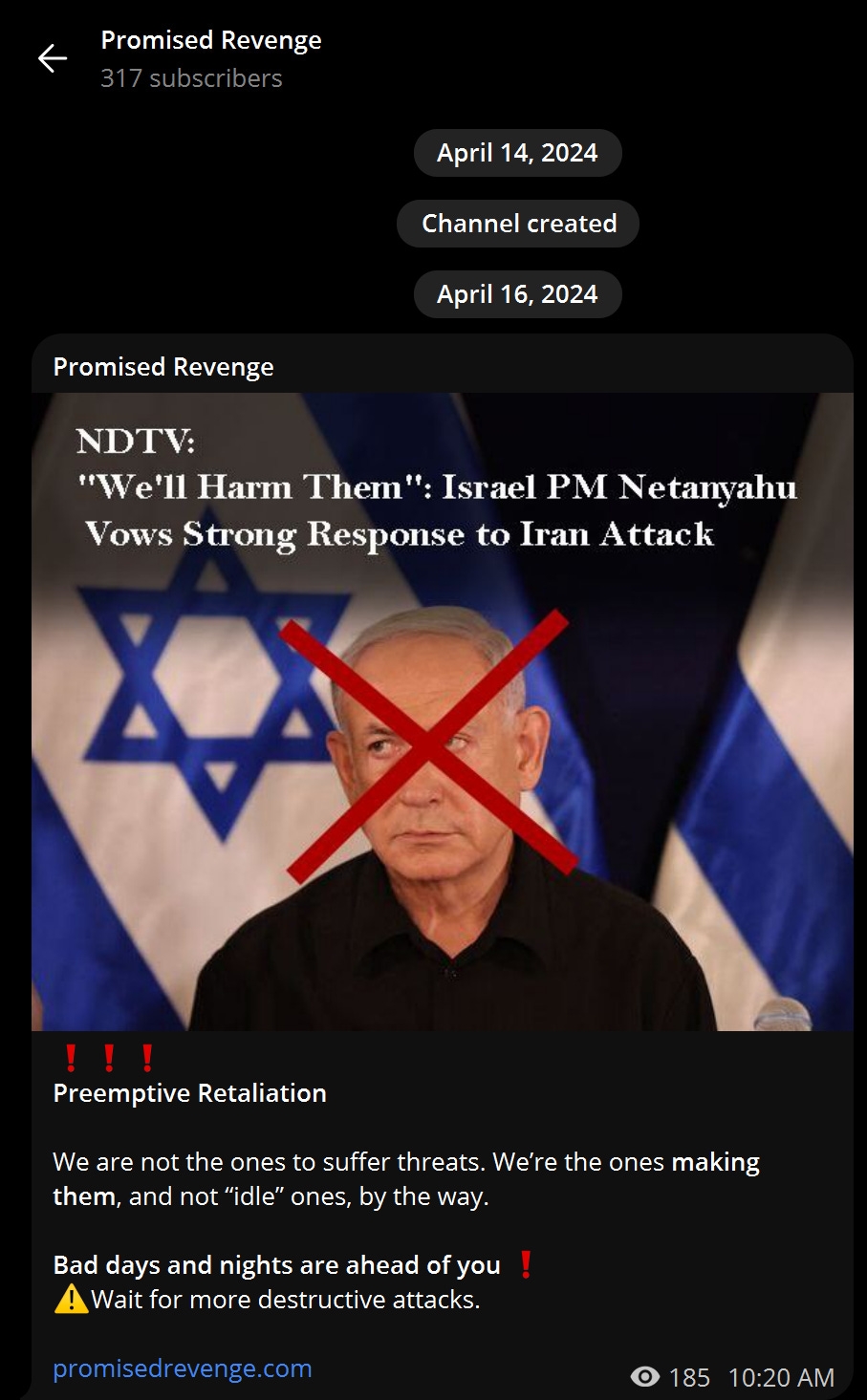
This week we’ll look at a long-running but only recently prominent Iranian hacktivist group, Promised Revenge. Promised Revenge made news in Israel this week after hacking the local national parks authority, so I figured why not take a look at what is one of the more unique groups out there. This isn’t really an investigation per se, but rather a look at the group in a broader sense with some interesting findings.
This group is an interesting one, and is one of the comparatively few (alongside others covered here) to set up a domain. Not sure if the hand symbol is meant to be a “timeout”, but the cufflinks sure are a snazzy addition. Edit: a reader has informed me that this is apparently commonly used by pro-Iran proxies, see here for more context.
The Arabic logo below means “Eat, Pray, Love”.
I’m obviously kidding, but it does mean “laugh a little, and cry a lot”, which they also translated into clunky Hebrew on the domain.
This isn’t just any hack and leak domain as well, but a domain done in a news-domain style with some comical titles, including prose that would make the bard proud, like “We will definitely drown you in the Litani river”. Some of the images also appear to be AI-generated.
The domain itself is worth discussing qualitatively. It’s not common that we come across an Iranian hacktivist front with a news-style domain, including one that utilizes generative-AI content for propaganda/psychological impact alongside overtly hacking and leaking material.
Usually threat actors stay in their lane; hacking and leaking material and posting on Telegram or their domain, or alternatively not operating as an overt hacktivist group and setting up inauthentic news domains for psychological impact. It’s not common to see both combined, so that’s interesting.
Looking at their Telegram channel, we can see that it was created in April 2024, which coincides roughly with a few other Iranian hacktivist groups such as the Cyber Court. Having said that, there are new groups almost every month, so that may not say much. The new .net domain has also only been active it seems since February, despite the .com domain having been set up months prior.
At least in this case, they pretty much overtly say that they’re Iranian in their first post:
The first posts refer to a .com domain, later ones move to a .net domain. We saw a similar dynamic with the Zeusistalking and RGUD operations.
Sollutium is also used here, and has been used a few times in the past as a VPS provider by Iranian actors also. Looking up DNS records via VirusTotal (which, by the way, has solid but not perfect passive DNS, I’d always recommend verifying with tools like Silentpush, Validin or Zetalytics) shows that the IP hasn’t been used in a while, but that its past use was for illegal purposes, perhaps indicating some issues.
We can also just look up both the .com and .net domains for passive DNS on VT or other tools to get more options:
We’ll come back to the 45.141 IP address later.
Let’s see if we can find some other affiliated domains or hosts, as these are solid but not enough as far as I’m concerned. Let’s take a look at the the HTTP responses from URLScan:
Quite a few overall. When using URLScan, one of the things I recommend doing is looking for unique file names and seeing if they’ve been scanned as responses on other domains. For example:
Here, any of the longer ones would be good pivot points. Battlefield.jpg would be a bad choice, but “maybe several nights in a row”, or “we warned you” or “the knesset network” or “the infrastructure of knesset network is out of reach now” would all be great choices. I couldn’t resist and had to look up some of the more funnily-named files too, like “maybe tonight”.
Looking up one on URLScan by clicking shows other domains that have hosted the same file:
Here we have two more domains: hackreboot and fushaar. We can confirm that they both were mirror domains for promised revenge in the past by looking at past scans:
The 45.141 host hosts a number of domains of ill-repute with at least some being self-signed (bad):
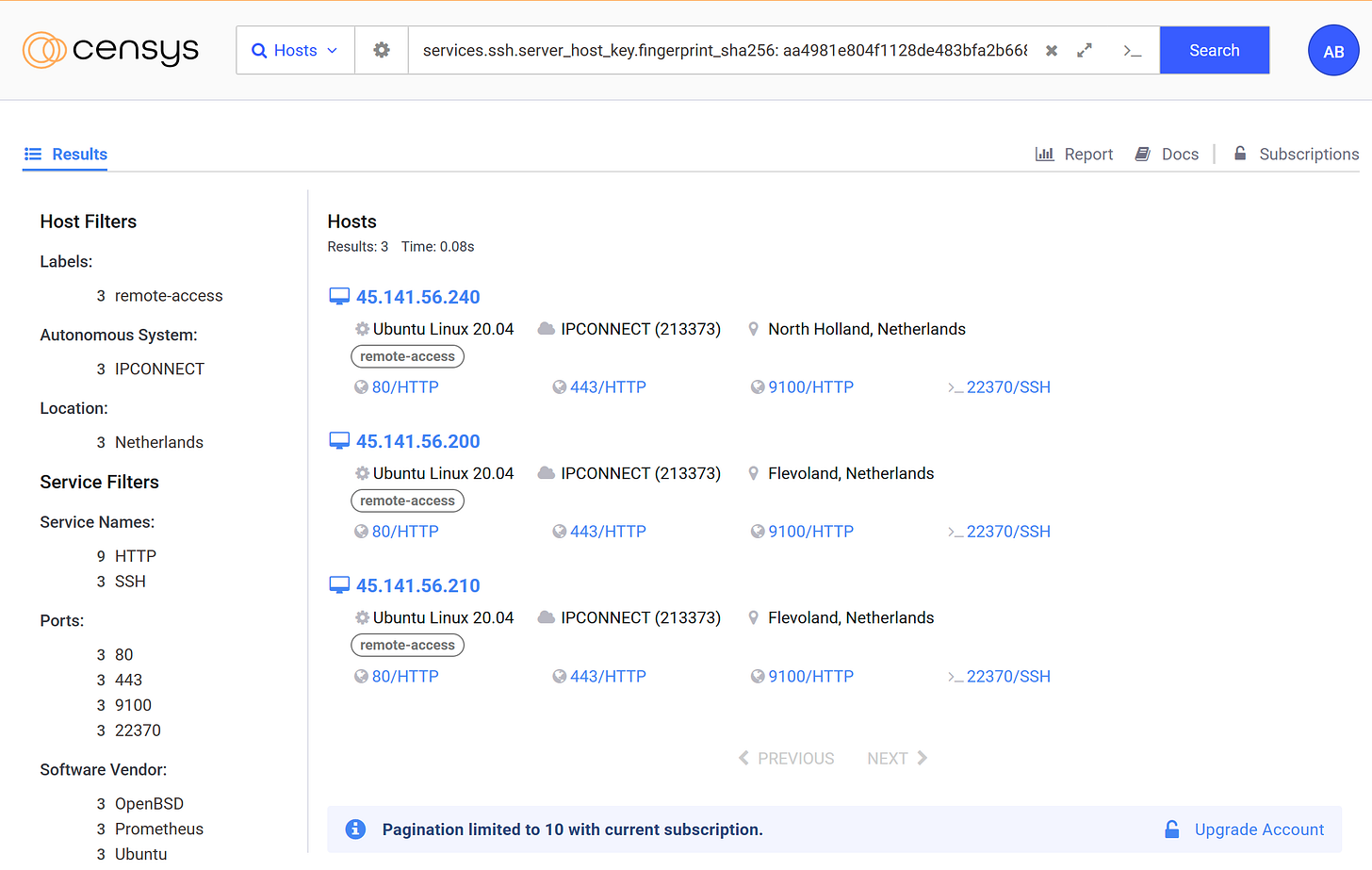
We can look it up on Censys as well to get some interesting results. The host is running SSH on a non-standard port, and as readers of the blog will remember, we can pivot on SSH keys:
As a reminder, SSH keys are how one “SSHes” into a given rented VPS, hence the “remote access” label. Those keys should be unique per server, and if reused, it usually is indicative of the same person running the same servers. It could also be indicative of a hosting service using the same key as a standard key, depending on the situation.
Pivoting on the key here retrieves three hosts in total including the original, all unsurprisingly on the same hosting provider and within the same subnet.
This is already great, as the more hosts, the better for threat indicator tracking, investigation and takedowns.
In this case, I’ve looked at the other two hosts and they don’t appear to be directly related. The hosts themselves, one of which is entirely inactive, could be either inactive, potentially unrelated or simply reusing a key provided by IPConnect as they don’t have anything of interest on them. They also could be operated by whoever rented the original host for
Let’s look at the DNS records then for the original host:
Here we have interesting ones. We see fushaar and hackreboot again, but we also appear to have other sites - yalla-shoote, bytehost, and cambeauties. Odd, and potentially unrelated, but unclear as the actual site for the hosting provider doesn’t have much detail, but is highly suspicious. It’s unclear what’s happening, so let’s move on.
But wait, there’s more! URLScan, one of my favorite tools by a country mile, can do more. We can continue investigating by looking at the 45.141 host in URLScan:
If you look in the bottom right-hand corner, you’ll see an image that caught my eye. Looking at it, we can see that the domain hosted is in fact the official domain for Saraya al-Quds, the al-Quds brigade of Palestinian Islamic Jihad. What a coincidence, right? This is especially interesting in light of Iran providing its proxies hosting infrastructure in the past. Not saying that that’s happening here, but certainly a funny coincidence.
So, on this one odd, shared host, we have either currently or in the past hosted a sanctioned terror group, Turkish hacking sites, porn sites, an Iranian hack and leak domain, and multiple other domains.
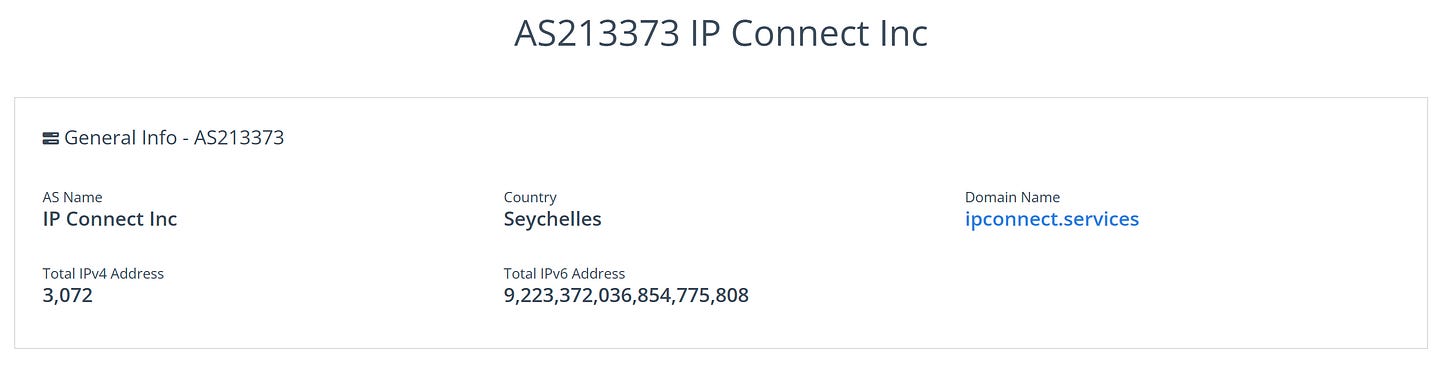
Based on what we have: odd, overtly problematic and unrelated domains on what appears to be a dedicated host hosting multiple unrelated sites, this may be a bulletproof host of some kind that provides shared hosting for this sort of stuff and simply has a given VPS hosting a small number currently. Looking at the host, we can see that it’s based in the Seychelle Islands:
The domain itself is the acme of professionalism, immediately misspelling its own brand in the first sentence of its description and adopting a prose-forward stream-of-consciousness description:
So, I’m certainly suspicious of what’s happening here to say the least, and am inclined to say that whatever oddness is happening here is probably at the level of the hosting provider.
Having looked at the domain and infrastructure and finding some interesting ties to other groups, let’s review what we have:
A comparatively rare style of IO domain, combining hack and leaks with generative AI propaganda and IO content
A network of domains, hosts, and a Telegram channel, including some hosts with ties to other suspicious activity and even Palestinian Islamic Jihad
A longwinded investigation writeup
I’ll conclude on that note and keep tracking this activity as usual.