Memetic Warfare Weekly: Top Kek Telegram Trolling
It Takes Labelling to Make a Thing go Right
Welcome to Memetic Warfare Weekly!
My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I also provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
Let’s review this week’s events, including CIA Telegram antics, a new e-mail reverse lookup tool, state media labelling efforts at Meta and Google Maps review bombing.
Top Kek Telegram Trolling
The CIA is finally getting with the times it seems and has officially joined Telegram only 5+ years or so too late!
This is a great idea on their end for a few reasons. Firstly, Telegram is an incredibly popular messaging app, and it will make their lives easier having a presence on this platform to promote access not only to Russians and central Asian states, but also for other regions in which Telegram is popular - Latin America, Africa and beyond.
Note that the CIA isn’t actually soliciting tips over Telegram, but rather provides information on how to access its .onion site to more securely contact them, share tips or even potentially become a spy/informant. Telegram is only E2E encrypted over secret chats - and even that is in question to some degree.
This idea itself is a good idea but also serves as some top-kek trolling, including the video of Russians contacting the CIA included in the message and posted on other platforms titled “Why I Contacted the CIA: My Decision”.
This is a great example of perception hacking as part of psychological warfare. Now that Russia knows that the CIA is active on Telegram, it will be easier for Russians to find information as to how to contact the CIA, making the Russian government even more cautious and paranoid about contact being made. Some statements are already being made - see below.
This may make the Russian government have to double down and invest more resources in monitoring or investigating Telegram, which would serve as a waste of time and resources for their otherwise strained counter-intelligence (CI) offices. If they’re smart - I imagine that they’re behind at least a few of the copycat Telegram channels already active.
This is analogous to the underlying strategic rationale of some malign influence threat actors - exposing their operations theoretically can undermine trust in the wider information sphere, with potentially greater impact than the operation itself.
OSINT.Industries Reverse Email Lookup
It's not often that I come across a tool that really excites me, but today is that day.
Reverse e-mail lookup, or querying an e-mail address to find out what accounts it has been used to register, metadata, account ownership and more is one of the mainstays of OSINT, CTI and IO. Reverse email lookups are often one of the first, if not the first, lookups to be done and are often the most fruitful in terms of results.
Epieos and its e-mail and phone lookup are famous, and justifiably so, for providing the best results for queries, but there are some other new tools that have potential. Epieos also provides a great phone lookup - so best practice is to always use both.
Perhaps most importantly, Epieos is transparent about ownership - this tool isn’t yet (see below).
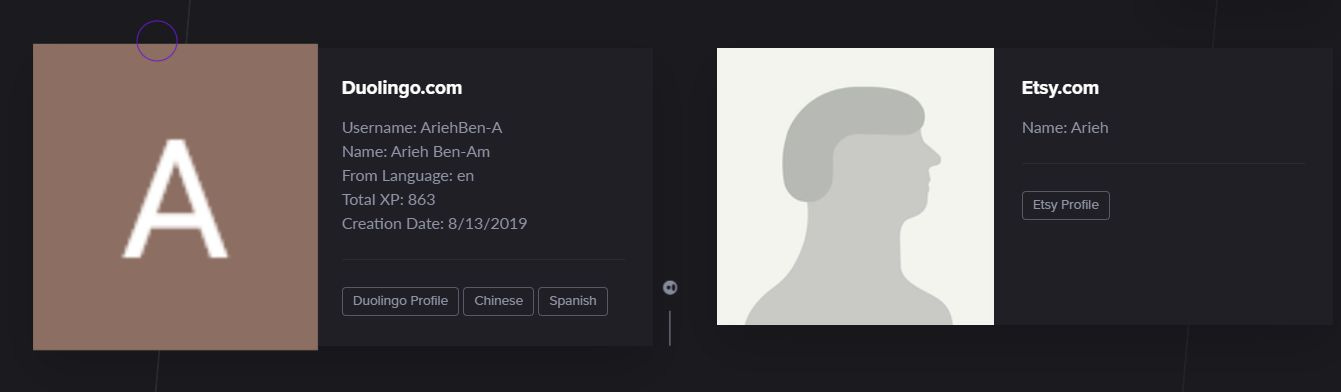
Redundancy, however is always a good thing in OSINT. OSINT.Industries, a new site (around for only a week or so old), released a new, powerful and free - for now - e-mail lookup tool, link here. They’ve also recently added a phone number lookup tool that I haven’t had the time to adequately test yet.
I've added a screenshot of my email address as an example - note that data includes specific information in some cases indicating that direct lookups are done via platform APIs, such as Duolingo, further enriching the possibility of results and retrieving results of a quality that Epieos users will be used to.
The potential here is quite large as the tool covers a variety of platforms, and will hopefully expand - I always recommend using multiple lookup tools anyway for maximal coverage.
Note that while the tool is great, OpSec shouldn't be forgotten! Ownership and logging policies are still unclear (I haven't looked into it deeply myself) - so take precautionary measures like registering under a pseudonym and burner email address, as well as connecting via a VPN as a minimum.
It Takes Labelling to Make a Thing Go Right
Some heavy-hitters in the counter-IO space from Meta - published an article in Lawfare about the difficulties of addressing state media outlets online. Recent developments, such as EU states banning access to say Russian state outlets following the Russian invasion of Ukraine, further complicate this issue. State outlets often play an outsized role as threat vectors on platforms, as they:
Exploit their often official and protected status to promote conspiratorial content or disinformation.
Enjoy some degree or veneer of legitimacy.
Have higher production values than many other outlets.
Are common central nodes for dissemination that are amplified by networks of inauthentic assets.
The authors refer specifically to measures taken by Meta, led by a “transparency-first” approach to mitigate the risk that these outlets pose. These include downranking their content in feeds, adding friction to the sharing process from state media outlets and more, all of which have proven to be effective to at least some degree. The risks of removing any labelling or algorithmic mitigation/enforcement methods from state media outlets has become quite clear following Twitter’s controversial decision to do so.
We won’t go into depth into all of the details of the article - though you should read it - but we will discuss Meta’s policy criteria, which I am taking verbatim from the article below:
Mission statement, mandate, and/or public reporting on how the organization defines and accomplishes its journalistic mission.
Ownership structure such as information on owners, shareholders, board members, management, government appointees in leadership positions, and disclosure of direct or indirect ownership by entities or individuals holding elected office.
Editorial guidelines such as transparency about sources of content and independence and diversity of sources.
Information about newsroom leadership and staff.
Governance and accountability mechanisms that protect editorial independence, such as correctional policies, procedures for complaints, external assessments, or oversight boards.
One of Meta’s main pro-transparency methods is labelling state media outlets as such and enforcing content and policy violations, which has led to demonstrably reduced engagement with state media outlets, which is great. There are some issues with labelling, like label fatigue, but these can be addressed.
What isn’t addressed to the same degree, and nor can it be, is the use of covert, authentic assets. Overt state media is a risk vector, but one of the bigger challenges for platforms is combatting grey outlets or even state-funded influencers. These assets - be they media outlets, backpacking YouTubers or otherwise - can be covertly funded and directed partially or wholly by governments, and are a much more difficult threat vector to address and enforce. The Microsoft TI team formerly known as Miburo has done research on this - see below.
China’s use of numerous Western influencers, and programs such as the CGTN “Media Challenger” journalist recruitment efforts and other use of covert influencers globally are a much larger issue for platforms. Investigation techniques using open and closed sources are key to identifying, labelling and taking other enforcement action. Many of these individuals are active on a wide, wide variety of platforms - ensuring that in most cases they’re labelled at best on only a portion of their online assets.
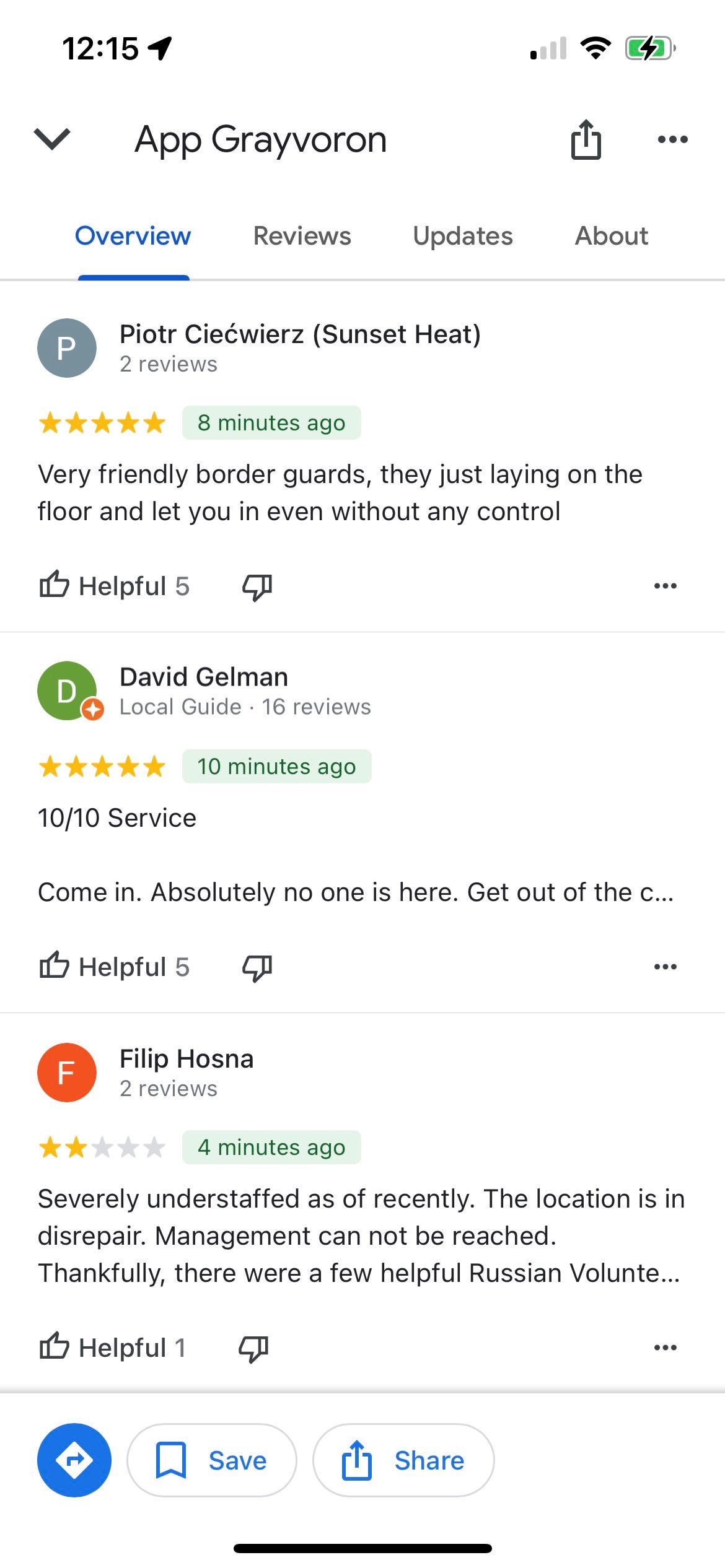
Google Maps-etic Warfare
Following a particularly successful Ukrainian and Russian dissident raid in the environs of Belgorod, Russia, Pro-Ukraine users have stormed the beaches of another front: Google Maps reviews. I’m always in favor of humorous content online, and this sort of thing while small scale can be useful in other certain contexts. Flooding geotags/hashtags or review sections for other online assets is also a common vector used by malign actors, such as in Russia’s flooding of geotags during the Navalny protests.
That’s it for this week! Please message me with any comments, memes, jokes or otherwise on Linkedin or ari@glowstickintel.com.