Memetic Warfare Weekly: The Empire Strikes Hack
Also Featuring: WeChat, Texas Ranger
Welcome to Memetic Warfare Weekly!
My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I also provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com. With no further ado, let’s begin taking a look at recent events below - we’ll be discussing CTI in the service of Chinese IO, “Cotton Sandstorm”, Chinese influence in the US and more.
The Empire Strikes Hack
I’ve discussed the role that Chinese CTI firms have in Chinese influence operations in the past here and on LinkedIn, and it seems that we have another case here of Qihoo 360 and the Chinese state media apparatus collaborating.
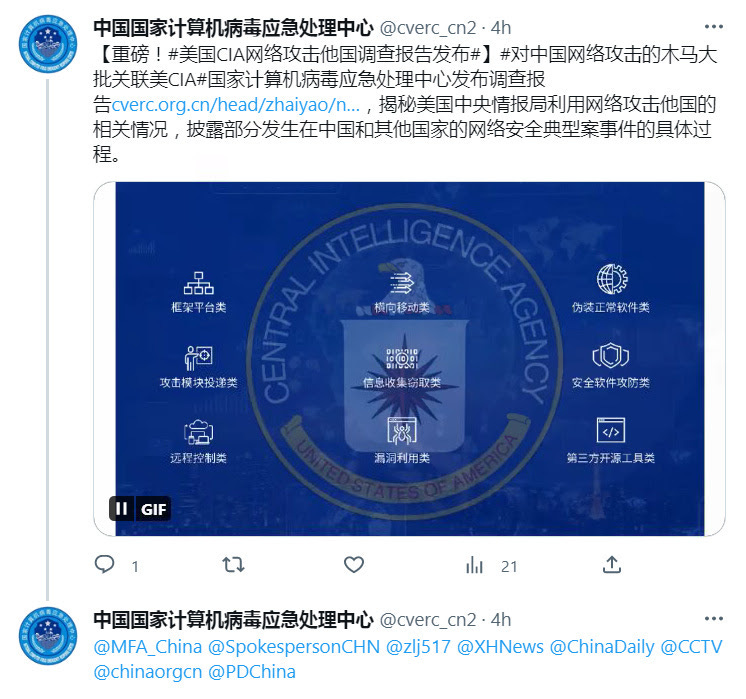
On May 4th, the Chinese National Computer Virus Emergency Response Center (CVERC) in conjunction with Qihoo 360 published some threat intelligence reports on CIA hacking and malign influence activities, calling the US the “Empire of Hacking”
Interestingly, the report accuses the CIA of carrying out global “infiltration, subversion and upheaval activities”, with an emphasis on CIA operations supporting American “puppet agents” globally. Essentially, accusing the CIA of carrying out combined cyber/IO operations to promote its goals. As discussed in previous blog posts, these reports are almost always weak at best and unfounded entirely at worst.
Chinese state media has already begun to promote the report, but with no actual copies of the report being circulated (only days later did Chinese embassies begin to publish copies of the report)
So, how can we take a look at this content directly?
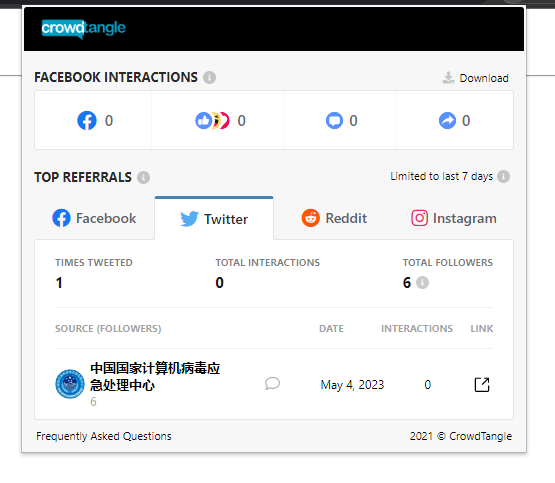
If we try to access the domain normally, we get a 403 forbidden notice.
We can still work with even just the link though! Crowdtangle works via the link and isn’t dependent on the domain actually being available.
So we see that only one somewhat odd Twitter account has shared a link to the actual report. As an aside - what’s odd about this account?
Has “2” in the username
No cover photo
Created in April, 2023
Let’s go to the actual Tweet.
We see the account, authentic or not, promoting the article, but we can’t access it.
What can we do? We can try to access it in a few ways:
Using a Chinese IP address via a paid VPN provider (most free ones don’t include Chinese IPs).
Check via archive.org or other archives - unfortunately, no results yet.
Access it via TOR, which I find often provides direct access to Chinese domains.
Using TOR, we can access the domain:
We see that there are PDF reports available at the bottom of the page as well, including a poorly-written report in English. We don’t have the time to delve deep into the content, but to summarize - the report accuses the CIA/US government of funding and supporting “color revolutions” globally.
Ominously, this is titled part 1 - so we may be subjected soon to another poorly written threat disinformation document masquerading as a threat intelligence report soon. Including a translation in English is also a first I believe - but I could be wrong - and I imagine that we’ll see further adoption of CTI as part of China’s IO apparatus in the future.
WeChat, Texas Ranger
The Diplomat - a great source for east Asian affairs for those interested - published a look at Chinese influence efforts targeting American state and local elections via WeChat (Weixin).
Interestingly, these efforts focused on Texas and Florida following bills proposed by their state legislatures to ban Chinese, and in Texas’ case also Russian, Iranian and North Korean citizens, companies and organizations from purchasing land.
These bills understandably instigated domestic opposition to them, and for good reason. Chinese state efforts in this case aligned naturally with those of concerned American citizens, as well as civil organizations in America that have ties to China.
Interestingly, WeChat - often used also by Chinese-Americans to communicate with their relatives abroad - was and is a central vector for Chinese influence. Chinese-American WeChat groups are already targets for Chinese influence efforts, and in this case protests against the bill were successfully organized thanks to WeChat groups. There’ve been numerous other attempts at influencing Chinese communities via WeChat - Canada, Australia, New Zealand and so on.
This is unsurprising insomuch as the Chinese state has editorial control over WeChat and what is allowed or promoted on it. Developing capabilities for investigating WeChat is quite difficult without exposing analyst PII as I’ve discussed in the past, and it remains to be seen how this will be handled by the wider OSINT community.
Despite all of the above, it’s still historically less-common to see tier-1 threat actors try to influence down-ballot US elections, but there have been some precedents - especially from Russia and Iran.
Meta’s Adversarial Threat Report
On May 3 Meta published their adversarial threat report for the first quarter of 2023, available here. The report covers a number of international information operations, as well as cyber campaigns from APTs. I won’t cover all of the operations, but will rather focus on the Chinese operations exposed and Iranian operations (discussed more in-depth below).
The most notable operation is a Chinese operation that’s been in the works for at least several years - let’s call it the “New Europe” operation, despite it having targeted global audiences.
The operation was notable due to its complexity - Adam Rawnsley, for example, has already compared it to past Internet Research Agency operations. He’s also putting his money where his mouth is by reaching out to New Europe and offering his services as a freelancer - the first thing making it a notable operation:
The second is the use of a front entity - London New Europe Media Ltd, which attempted to hire freelancers. Thanks to the UK’s comparatively transparent registry (with shockingly lax controls), we can see the incorporation papers here:
We see that one Liu Yong of 36 Applegate House, 20 Victory Parade London, born in 1972, is the Director at the time of incorporation. Interestingly, only one other company has been registered at this address in the past as per the UK Company House, but it’s probably unrelated.
We can see the current registration here:
The address is shared by thousands of other companies, indicating that it of course is a front:
This is notable in that this tactic has historically not been utilized by Chinese actors for interference- though it has been utilized on countless occasions by Russians for IO purposes, as well as Chinese actors for other, non-IO related purposes. Many past Chinese operations have also been run by outsourced digital marketing firms in Hong Kong or Southeast Asia. Information proprietary to Meta - such as user IP addresses, user profile data and so on - indicate that the operation was actually outsourced, but domestically in China, to one Xi'an Tianwendian Network Technology - which I may look into in a future post.
The operation also was notable in that it was multilingual, with content in English, Russian, Uyghur and Chinese. The operation was also multi-platform - often to the detriment of its operational security as seen below:
Additionally - it’s great to see that Meta is adopting the threat indicator reporting mechanism that its team developed to make life easier going forward.
Cotton Sandstorm
Iranian malign influence activity is unfortunately still under-researched compared to Russian and Chinese activity, but in many ways is coming into its own.
Microsoft’s recent report on Iranian state actors and their “preferred techniques, combining cyber and influence operations” is very much worth reading to better understand Iran’s role in the wider threat landscape. This development also further illustrates the need for combined CTI/IO investigative teams in governments and firms, which Microsoft’s DTAC does well.
Microsoft’s report provides some interesting analysis as well as to why Iran has chosen to rely on cyber-enabled IO, meaning essentially the use of IO to amplify the impact of a given cyber operation, usually a hack and leak. Microsoft posits that a decline in Iranian capability to carry out complex attacks, such as ransomware of wiper attacks, leading to the adoption of “low-impact, low-sophistication” cyber-enabled IO - as well as the need to “undercut” national protests sweeping Iran and promote the regime domestically, including slandering opposition figures.
Microsoft attributes much of this activity to “Emmenet Pasargad”, or “Cotton Sandstorm”, which was sanctioned by the US Treasury Department for attempting to “undermine the integrity” of the 2020 US elections.
Generally speaking I agree with this analysis - IO is not that hard to carry out, especially if done to promote low-energy attacks such as domain defacement. Additionally, for us as analysts focusing on cyber-enabled IO is great for attribution - the more complex the operation, the higher chance of an OpSec failure.
Microsoft also refers to cross-industry collaboration with Meta, which is inspiring to see and should become an industry-standard going forward. Microsoft’s internal telemetry is also powerful, as shown by datasets referred to in the report, and being able to fuse that data with other platforms will serve as a force-multiplier for analysts.
Some of the trends mentioned also are increasingly common, chief among them the use of alleged dissident organizations as cut-outs. Most famously may be the allegedly-Russian operation “Anonymous Sudan”, but other organizations have been attributed to Russia as well - such as allegedly-Ukrainian hack and leak groups like Beregini and numerous others. Much of this specific activity is carried out via Telegram.
The reference to anti-regime hacktivists such as Lab Dookhtegan and others is also noteworthy for analysts and investigators, as they often provide relevant information for those carrying out CTI/IO investigations - for example, Lab Dookhtegan has leaked information on COBALT MIRAGE members in their own Telegram channel. Their channel was recently taken down, but they’ve revived it at t(.)me/lab_dookhtegancyber.
Two other less-common vectors were used: bulk messaging and impersonation. Cotton Sandstorm launched SMS spamming operations against Israel on a number of occasions by utilizing commercial bulk services. Iranian threat actors also often carry out impersonation attacks as part of their IO efforts; Israeli journalists such as Gil Hoffman and others have had inauthentic domains created in their name, and other journalists have had their identities impersonated as part of active outreach efforts. Adam Rawnsley published a great investigation into Iranian operations targeting Israel that featured this as well, available here.












I love the phrase cyber-enabled IO. Another great read Ari!