Memetic Warfare Weekly - Straight Outta Redmond
Microsoft.With.Attitude
Welcome to Memetic Warfare Weekly!
My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
Memetic Warfare (bi)Weekly is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.
I provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
Last week we focused on Chinese activity, but Microsoft has come out swinging with some great reporting on Russian IO and cyber activity. Let’s take a look at some of their reporting in this blog.
The first report that we’ll take a look at focuses on Russian networks in Africa, particularly in the context of Russian influence on coups.
Coup D’Meme
Before we actually discuss the content, I beg of everyone, please, please please stop using the word “playbook” when describing cyber/IO activity.
So, what are the main points brought up in Microsoft’s Threat Analysis Center report?
The report’s main thrust is that the recent spate of 9 coups seen in mostly Francophone Western Africa are, to some degree, catalyzed by Russian influence networks and activity.
How does Russia go about doing this? The report brings up multiple interesting points, several of which I will summarize below:
Long-Term Influence Investment & Outlook
Russian invests significantly in its influence apparatus in Francophone Africa, with Microsoft referring to previously exposed IO such as Afrique Media as well as now well-known influencers, such as Kemi Seba and Nathalie Yamb. Russian overt media entities are also popular among target audiences.
“Align with the coup leaders”
Russia has nary a scruple about immediately aligning itself with coup leaders. As Microsoft states - and I enjoyed their logic here - this is a “low-cost” decision.
As per Microsoft, “if the coup fails, Russia has snubbed a government already unfriendly to their interests; if the coup succeeds, Russia has signaled early their willingness to work with the undemocratic junta. Support can be communicated by proxy: in Niger, for example, the Russian government has not declared official support for the coup, but Prigozhin did, before his death.”
The ability to fuse IO and influence efforts into traditional statecraft is a fantastic example of a holistic hybrid approach.
Seize the Means of (Narrative) Production
Russia’s influence apparatus “capitalizes” on the post-coup information fugue state and actively promotes the coup leaders and other nationalist themes while, of course, inciting against France.
Hoist the white, blue and red:
Russia also promotes pro-coup demonstrations. These presentations are often quite comical, with small groups of west Africans jauntily hoisting the Russian flag, replete with other anti-France and pro-coup paraphernalia.
Following the recent interest in the life and times of Prigozhin and the Wagner group, Microsoft also provides some context on the Wagner group’s past and current role in these coups. The future of Wagner in Africa, however, is very much still an open question.
Alongside the aforementioned moves, Wagner also plays a role. Much of the above can be outsourced to Wagner in some cases, and in others Wagner can provide its own utility. This ranges from “coup-proofing” via providing physical security, while also running their own IO campaigns.
Following Microsoft’s discussion of higher-level topics, the report also discusses some specific suspected cutout organizations in Niger known for their “unusually strong pro-Russian stance”.
These organizations, PARADE Niger (PARADE, of course, also has other branches in Africa) and the Union of Pan-African Patriots, are called out by Microsoft as being pro-Russia front organizations that supported the recent coup and junta in Niger. They’ve also been active, as per Microsoft, in creating multiple Facebook pages to “artificially promote content”.
Perhaps they should invest more in their production values for those pages:
I haven’t had the time to delve into these myself, so I’ll refer to Microsoft’s research with my own occasional joke.
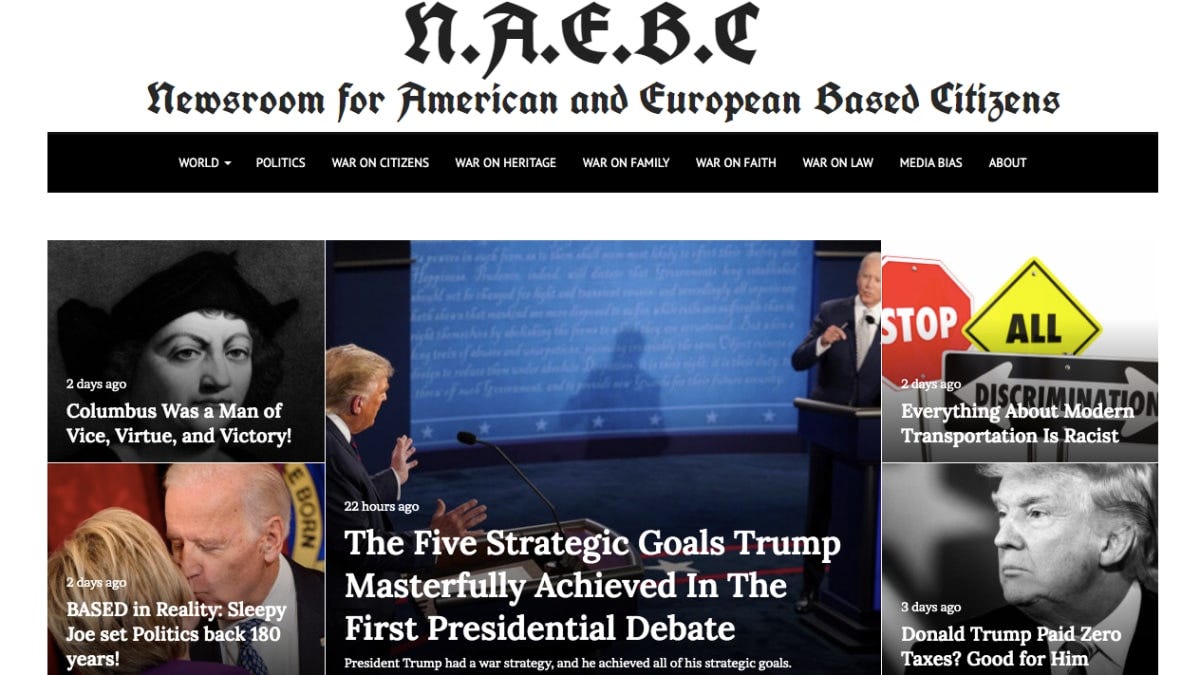
The first thing that I noticed was the predilection for silly, acronym-based names for organizations. PARADE, standing for Partenariat alternatif Russie-Afrique pour le développement économique, immediately brought to mind the NAEBC, the Gothic-font “Newsroom for American and European Based Citizens”, which was exposed as a Russian influence operation.
These sorts of names are the kind of thing one would expect from 2000s Europop satirists, such as DJ Crazy Times and Ms. Biljana. It’s also funny that forgetting the “-” in European-based makes it appear as if the newsroom appeals to “based” citizens only, but I digress.
Is the utilization of silly acronyms and names a TTP for Russia? Probably not, at least not without more evidence, but it certainly adds some spice to our investigative work.
Microsoft also points out that representatives of the Russian MOFA have in fat visited branches in the past, “indicating a possible connection”, amongst other ties. Interesting, to say the least.
Digital Buffalo Soldier
Somehow I only now am hearing about the FP Analytics & Microsoft “Digital Front Lines” project. The project is comprised of a series of reports hosted on the digital front lines domain and will be launched at a UN-hosted event in late September.
The site has numerous interesting reports and articles from industry thought-leaders, see below a few notable ones:
Clint Watts on Russian influence via traditional methods in Latin America
David Agranovich on Threat-disruption models
Tom Burt on Russian hybrid warfare
The site even hosts a quiz which is fun, because why not, but there are some factual errors in the quiz, for example see below where Mandiant’s APT 1 report is attributed not to China, but rather another country:
That’s it for this week - Microsoft also published another fascinating report on Chinese and North Korean activity available here, perhaps we’ll look at it next week.