Six Years a Palm Beach Police Officer
A Song of Emeralds and Generative AI
Welcome to Memetic Warfare.
You may have noticed that we’re undergoing a facelift, so hopefully that makes the reading process more pleasant.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also do training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
We’ll be covering ASPI’s latest sometime next week.
This week we’ll cover Recorded Future’s latest reports as a duo, and I believe that there’s a lot to take in by viewing these as both separate report. There’s even more to take in by viewing them as being representative of the state of influence operations and perhaps a glimpse of the future of the field. Let’s start off with “Emerald Divide”.
Emerald Divide covers a broad range of Iranian activity targeting Israel in past months. I’ve covered a bunch of these in the past, as have others, and it’s great to see holistic coverage as an operation. Deeper, in-depth and most importantly a broader perception of campaigns over operations is critical and something that only dedicated teams can do effectively, as otherwise the time investment is too large.
The network is very Telegram centric but has other accounts on other platforms, see below a sample of the first stage:
Let’s review the highlights of the operation:
So, there’s a lot to go through here - use of Google Maps and forms, QR codes, physical impact and more. I’ll share some of my thoughts below:
One of the more interesting things in the operation was the utilization of Google Forms and other services for recruiting. I’ll save you the Hebrew, but below you’re looking at a sign-up form for volunteering for a political group in Israel.
In addition, the use of LinkTree is something quite commonly seen, and the operation also covers both WhatsApp and Telegram - useful in that Israelis love both.
This is a high-risk decision. Google suite capabilities are monitored and investigated by Google and Mandiant teams, and Facebook’s teams cover WhatsApp and other services, so takedowns are quite possible, then even leading to potential attribution.
The report covers the timeline of the operation in both of its stages over several years:
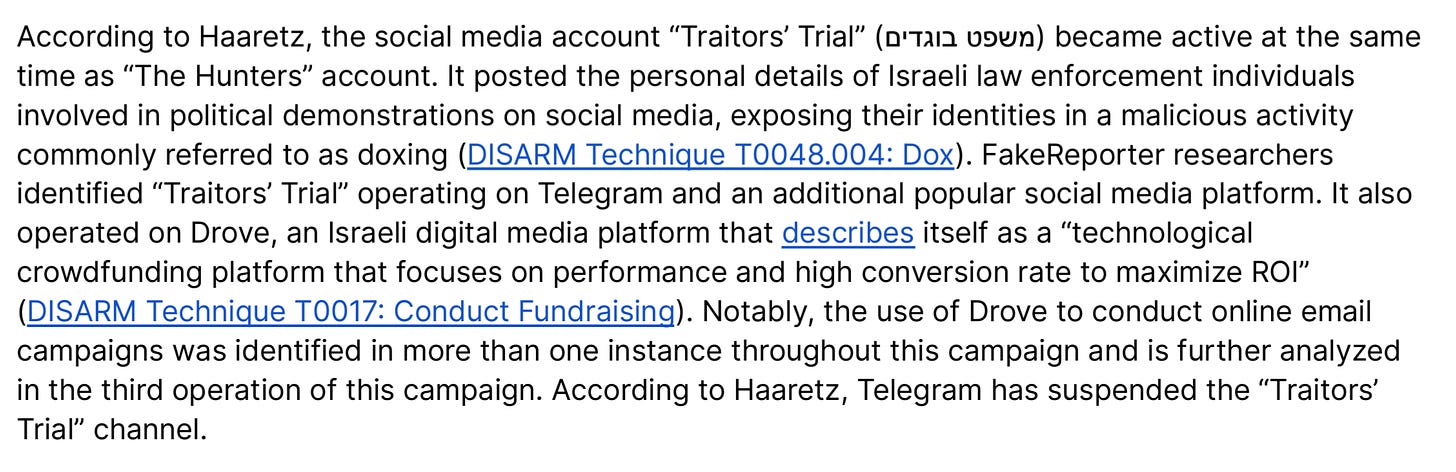
Drove, an Israeli crowdfunding platform, was also exploited by one of the network entities:
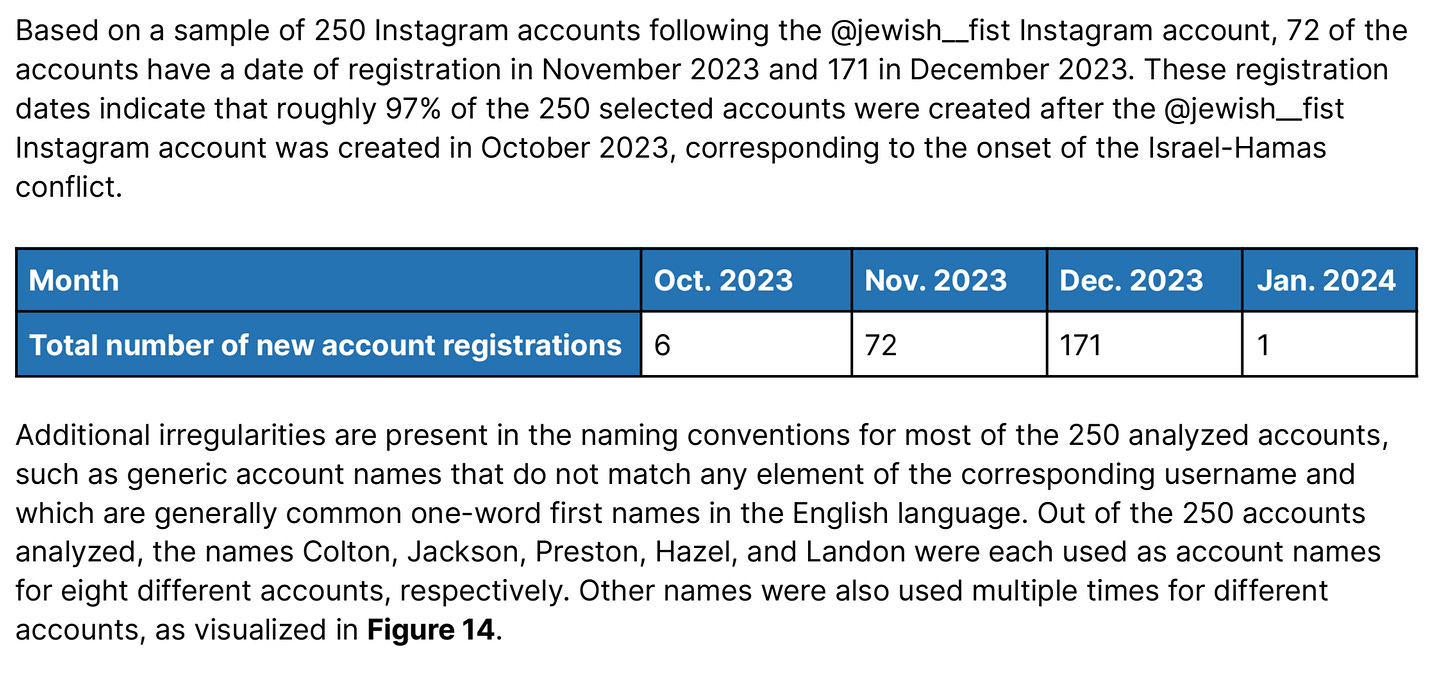
Having time also leads to better findings. The account analysis in the network also paid off:
Strong millennial name choices here - from Braxton to Colton to Jackson to Hazel to Lincoln and apparently Jaxon.
There’s much more to the operation, so take the time to read the full report, linked to above.
As always, we shouldn’t take this operation as a standalone affair.
The Iranians have been restless recently, potentially running multiple operations such as the Dofek TV network and the Cybercourt hacktivist ensemble that we’ve discussed here.
But wait, there’s more! The Iranians have also carried out additional influence/psyops activity, such as the sending of flowers with inciteful content to a hostage family. They’re really firing here on all cylinders, and some historical perspective here will do us well to really deeply understand full spectrum IO.
Six Years a Palm Beach Police Officer
But wait, there’s more! Recorded Future also published a report on Russia-linked activity, available here and given the palindromic name of CopyCop. Check out the executive summary below:
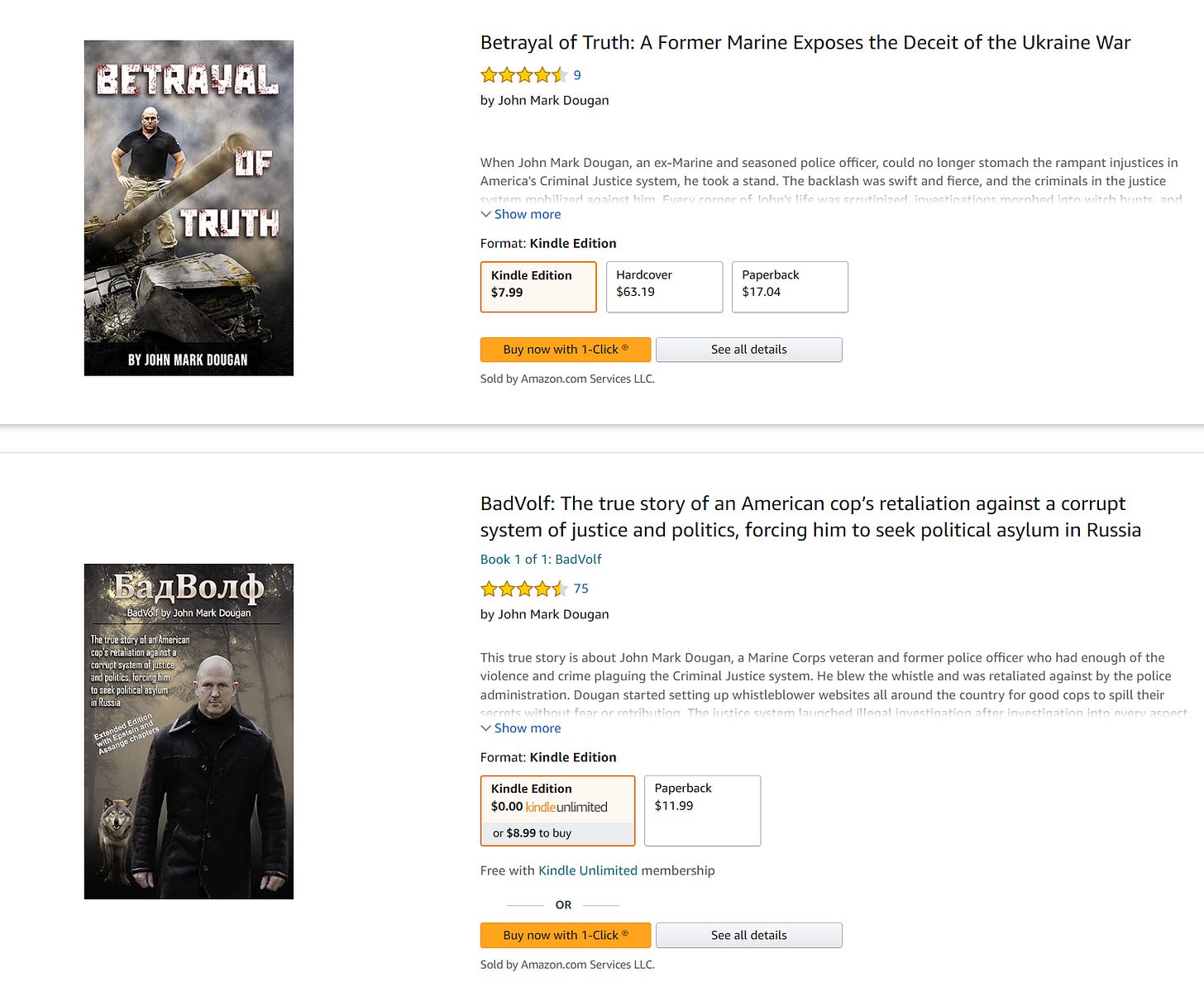
The “CopyCop” network is a domain-centric, generative AI-powered, pro-Russia network attributed to John Mark Dougan, meant to generate pro-Russia content at scale.
Dougan, or “BadVolf”, is a former Palm Beach police officer implicated in quite the background story (read more here). He’s now out there wearing long leather coats (only the good guys do that), tactical pants and polos and apparently communing with his inner wolf.
Dougan is quite the dude with an incredible IMDB trivia page that sound like bad Chuck Norris jokes:
I can only imagine being this guy’s dedicated FBI analyst.
Anyway, on to the report. I’ll put the main points below:
As always, read the report yourself in full, and I’ll focus below on some key points. The first I want to touch on is the difficulty of using analytics, at least for Russian actors or apparently second-tier ones. Iran has no difficulty it seems acquiring Google accounts for exploitation, and it raises interesting questions about the ease of access internationally. It’s also simply possible that alternatives that can’t be used for attribution or taken down are desired, who knows.
This isn’t just for fun, apparently there is a concrete need for this. I’m not surprised and have always guessed that those who actually order IO want to see numbers go up as part of their strategy, thus incentivizing inauthentic engagement from the operators:
Matomo, an open-source analytics platform was integrated. If you watn to see how to find that out - read here.
From there, the report shows how they identified that the site had a numerical ID:
Those requests lead to the ability to run domain enumeration via the Matomo API on the falconeye site:
The operation was lackadaisical regarding OpSec in other methods. Prompts were occasionally left in - there are many such cases:
Other OpSec errors occurred also, in this case finding other entities tied to Dougan and his translator:
Overall, two really really excellent reports.
I couldn’t help but write down some thoughts:
These two networks are both emblematic of the general approaches and TTPs often attributed to their patrons. Russian operations often utilize domains whereas Iranian activity often exploits messaging groups and channels - not to say that this is the case universally by any means.
The Russian operation was RIFE with OpSec breaches, in comparison to the Iranian one which had far fewer. These breaches emanated primarily from the network’s domains.
Gen AI is used by both, but the Russian network utilizes it more frequently and apparently more frequently for text.
The Russian operation had little authentic engagement at the beginning, but as the report states it’s begun to garner real engagement by posting higher-quality, targeted content.
The Iranians managed to get some real engagement from Israelis on social media, if a small amount. Thus, the Iranian operation is arguably more impactful than the Russian despite having a lower level of operator investment in the network as a whole (at least at the domain level).
This can be credited to an apparently better understanding of the target society and its culture and politics, and in my opinion and most importantly - the choice of using messaging applications. Israelis love WhatsApp, and Telegram has grown greatly in popularity in past years.
Creative uses of third-party services, such as crowdsourcing information via Google Forms and others, provide an additional added-value element here of data collection. Potential targeting in the future based on this data would also be much easier, and in practice lead much more easily to real-world impact via organizing protests, holding flags and so on.
Looking at the two reports, I’m going to harp on a point I make frequently. We in the IO space often overhype Russian capabilities and make light of others, including Iran.
In my opinion, the Iranian operation here is more complex, impactful and multimodal than the Russian operation (and similar operations such as say Doppelganger), and should be viewed as more successful.
We often tend to view Russian activity as being sophisticated, at least comparatively. This is in part to our perspective that running domains and domain-based infrastructure for operations is a sign of operator skill, arguably similarly to the CTI space.
In practice, domains are a serious issue for operators. They’re easy to misconfigure, are prone to OpSec breaches, and are hard to promote online, necessitating external assets for dissemination and amplification.
An analogy for this would be the decline of the dark web and the rise of messaging applications, including Telegram and others. This is due to the inherent advantages of utilizing messaging applications over domains (clear or onion):
Groups and channels are easy to set up more securely on burner infrastructure, and there’s less incentive to reuse infrastructure.
It’s easier to acquire “white” infrastructure instead of using suspicious hosting or domain registrar services,
It’s easier to avoid KYC measures via burner infrastructure compared to domain registrars and hosting services.
The cost is overall lower over time.
Groups and channels are harder for analysts and investigators to identify and investigate.
Dissemination and amplification is much more easily done at a larger scale thanks to built-in forwarding mechanisms.
Groups and channels can serve as multimodal file repositories for seeding and other activity at a large scale.
Telegram in particular is a technical marvel in this regard. Users can upload files up to 2GB in size, and once a user downloads a file of , s/he can easily forward that file to as many people as desired. Compare this to domains, where sharing such large files easily would be a significant pain point.
If burned or taken down, content can be easily moved to backup channels much more quickly than with domains.
None of this is to say Russia doesn’t utilize messaging applications, they absolutely do, but domains are still the leading entity choice for most threat actors.
What I do think we’ll see is a transition to messaging application groups and channels replacing in many cases domains as the central or key entity, as they already can replace most of their relevant functions.
As always, if you liked this blog and want to support it, check out Telemetryapp.io, and feel free to reach out via the comments, DM or LinkedIn.