Memetic Warfare Weekly: Reno 911! Miami Chronicles
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also do training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
This week, we’ll take a look at a very cool OSINT tool, discuss the ODNI’s new 2024 threat assessment, and then take a look at a Russian influence operation and how to investigate it yourself.
Let’s start this week with a quick shoutout to Louis Tomos Evans and his new and improved tool, Hunt Intelligence. HuntIntel is one of the few tools out there that provides geosearch, check out an example here.
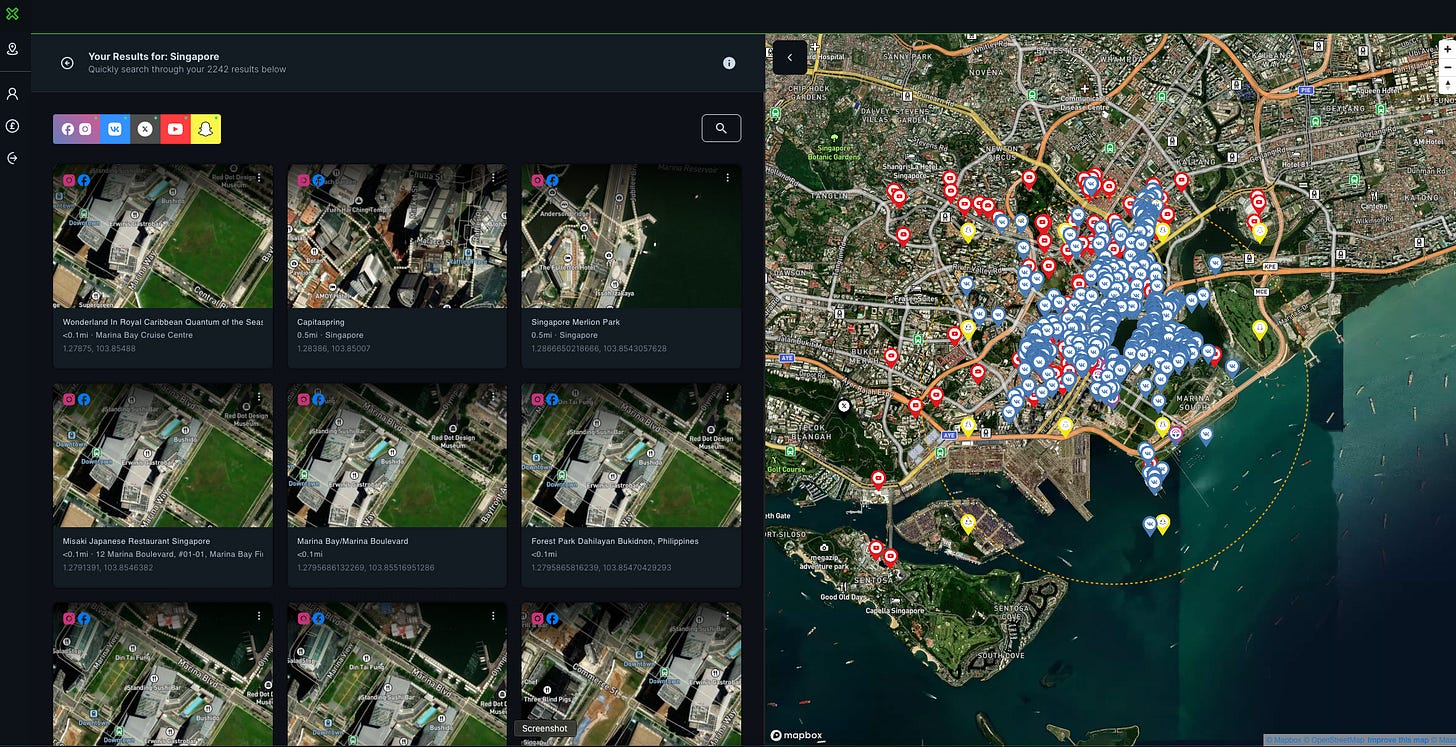
Let’s look at Singapore just for fun:
Nice to see a solid amount of results overall, just over 2,000 and from a variety of platforms.
Overall VK seems to be over-represented, but beggars can’t be choosers, and the power of the tool is still obvious.
Kudos to Evans for making it affordable also and easy to use, I’ll definitely be using it in the future.
Halo 3: ODNI
The ODNI 2024 Threat Assessment is now out and available here, and it’s worth reading for the wonks in the crowd.
I’ll focus on the malign influence sections below, which unsurprisingly begins with China:
My first note is that the use of the word “playbook” is incredibly overdone and trite should be banned for the next 5 years by everyone not using an actual playbook in sports. Every time someone says “Moscow’s playbook”, an angel loses its wings.
The other findings aren’t very groundbreaking either, and I personally would question the claim that China is showing a “higher degree of sophistication” - China has historically been more sophisticated than many think, and Russia in comparison has been simultaneously less sophisticated than is often thought. I agree that China is investing more in attempting to actively shape discourse on core interests in the West, but that’s not news per se at this point.
I also would claim that “experimenting with generative AI” is not inherently a sign of sophistication, as the barrier to entry is having access to an internet browser.
The specific note on activity in academia is interesting though, and I’d like to see that further explored in the future.
The same goes for the note on elections. Calling out that many IO actors for China, and others, aren’t necessarily under “direct” supervision is accurate and may be impactful in the future.
From here, let’s move on to Russia:
Nothing really to add here, it’s the same points that we’ve seen in the past and nothing new is brought up here, so a bit disappointing.
Let’s check out Iran:
Firstly, credit to the ODNI for finally grouping cyber and IO together. This section includes some deeper insights than the other sections despite being shorter, and takes a more integrative view.
Overall, the influence sections were a bit disappointing. I certainly don’t expect them to take up large sections of the ODNI report, but they read more like summaries and not forward-thinking analysis from an all-source integration team. The field is still new though to the ODNI, and I’m looking forward to seeing what they publish going forward.
Reno 911!: Miami Chronicles
The New York Times published on article on a new domain in a Russian influence operation targeting the US, available here.
I figured that it’d be useful to take a look at the domain itself, the Miami Chronicle, and look at a few specific elements.
The domain is https://miamichron(.)com, but only access it securely via an investigative workspace. Let’s begin then and look at a few of the things mentioned in the article and see how you could recreate them yourself:
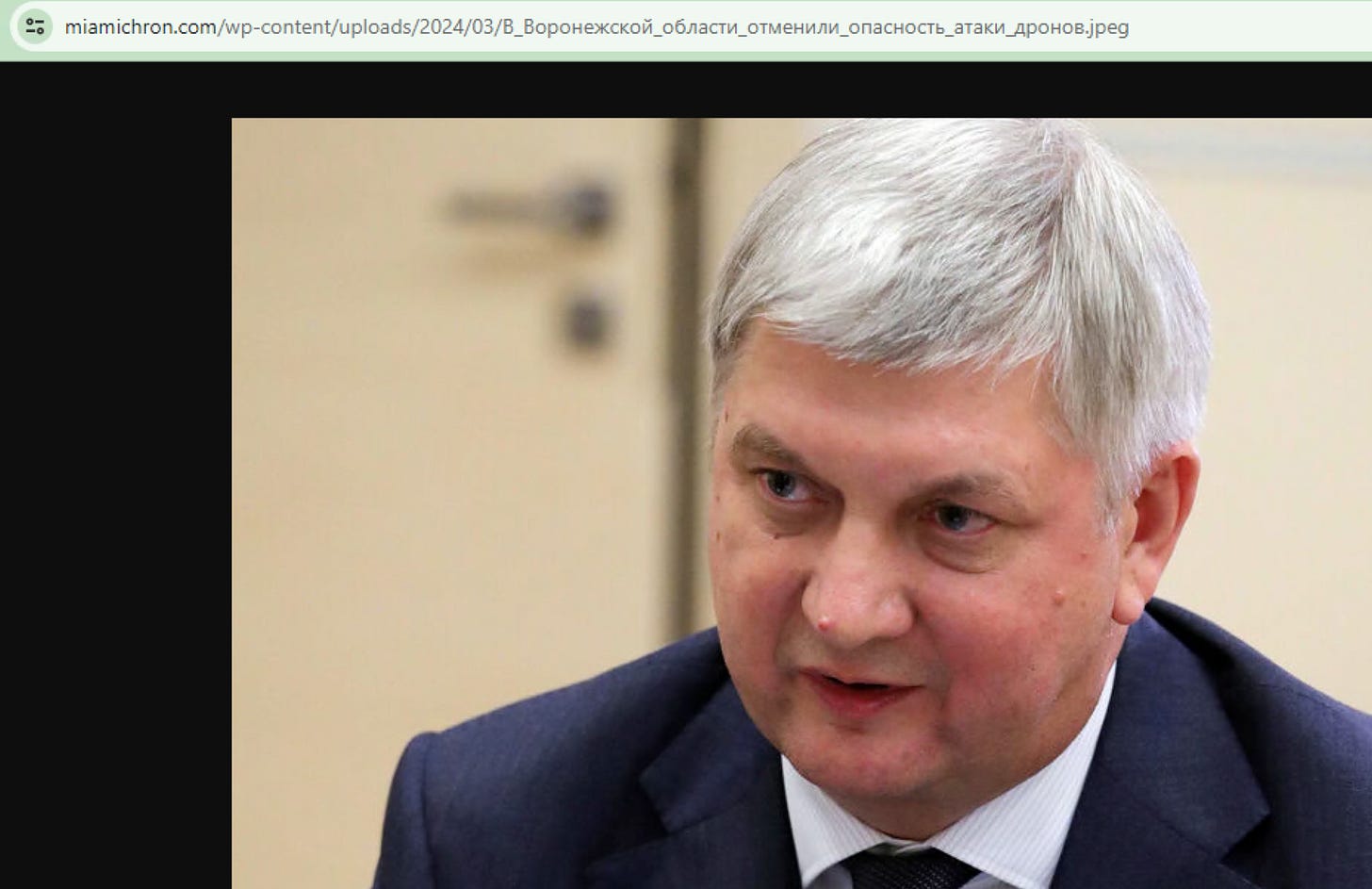
The article mentions that some of the files on the domain had Russian names, let’s take a look.
So just checking out any given image on the domain has a solid chance of the actual file name being in Russian, very poor OpSec to say the least. Note also the URL - it’s a WordPress site, and has a folder titled wp-content/uploads, we could go to that folder later and look for more examples if needed.
The poor production quality though is a constant here; we’re talking about people who couldn’t be bothered to replace the Lorem Ipsum text across the domain:
Most of the domain’s content is boilerplate or otherwise empty as well. Many of the linked sections don’t have functional links, and the domain uses a generic Wordpress theme that they didn’t bother to remove in the about section:
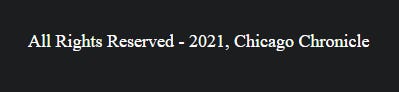
They also didn’t bother to replace the reference to the Chicago Chronicle:
Anyway, now that we know that the site is Wordpress-based, we can take a look at the source code. Wordpress sites often expose raw JSON data, and in it we can find a lot of relevant information.
Opening it up shows a wall of text - not much we can do here without painstakingly reading each line, but clearly there’s much more here that we can do to investigate:
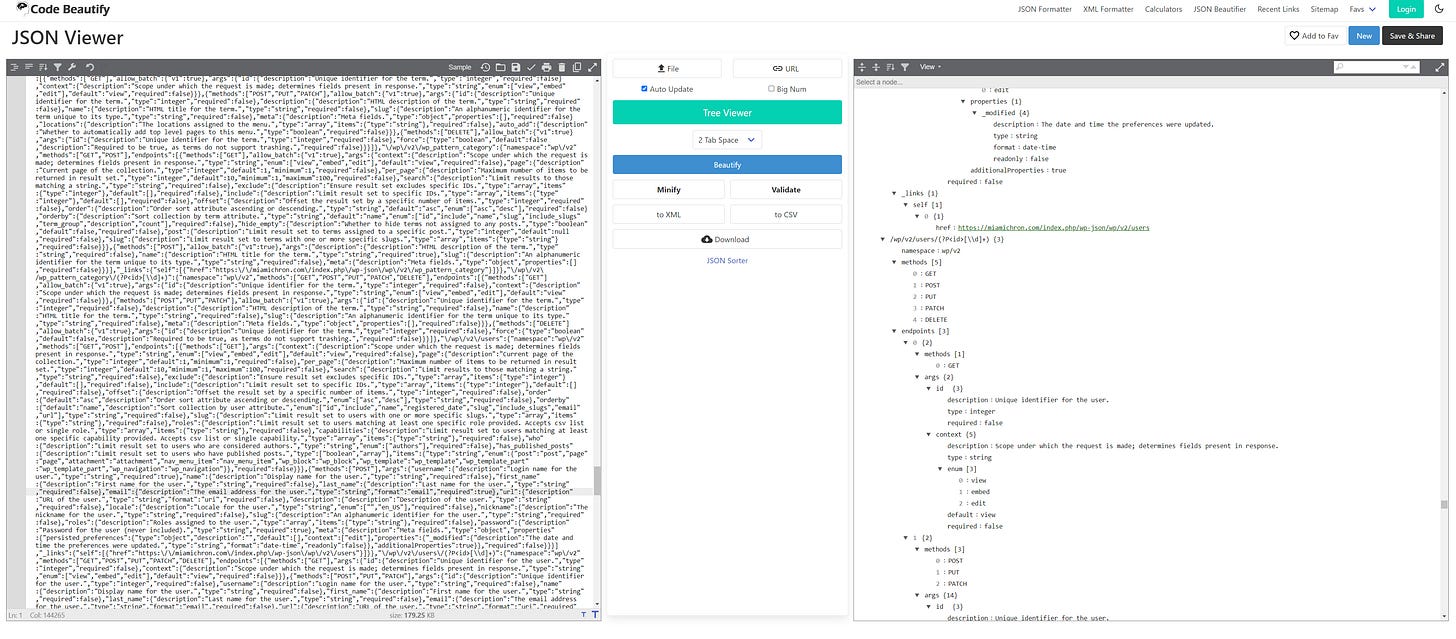
In cases like this, I’d recommend taking all of the JSON and throwing it into a JSON beautifier to structure it - see below:
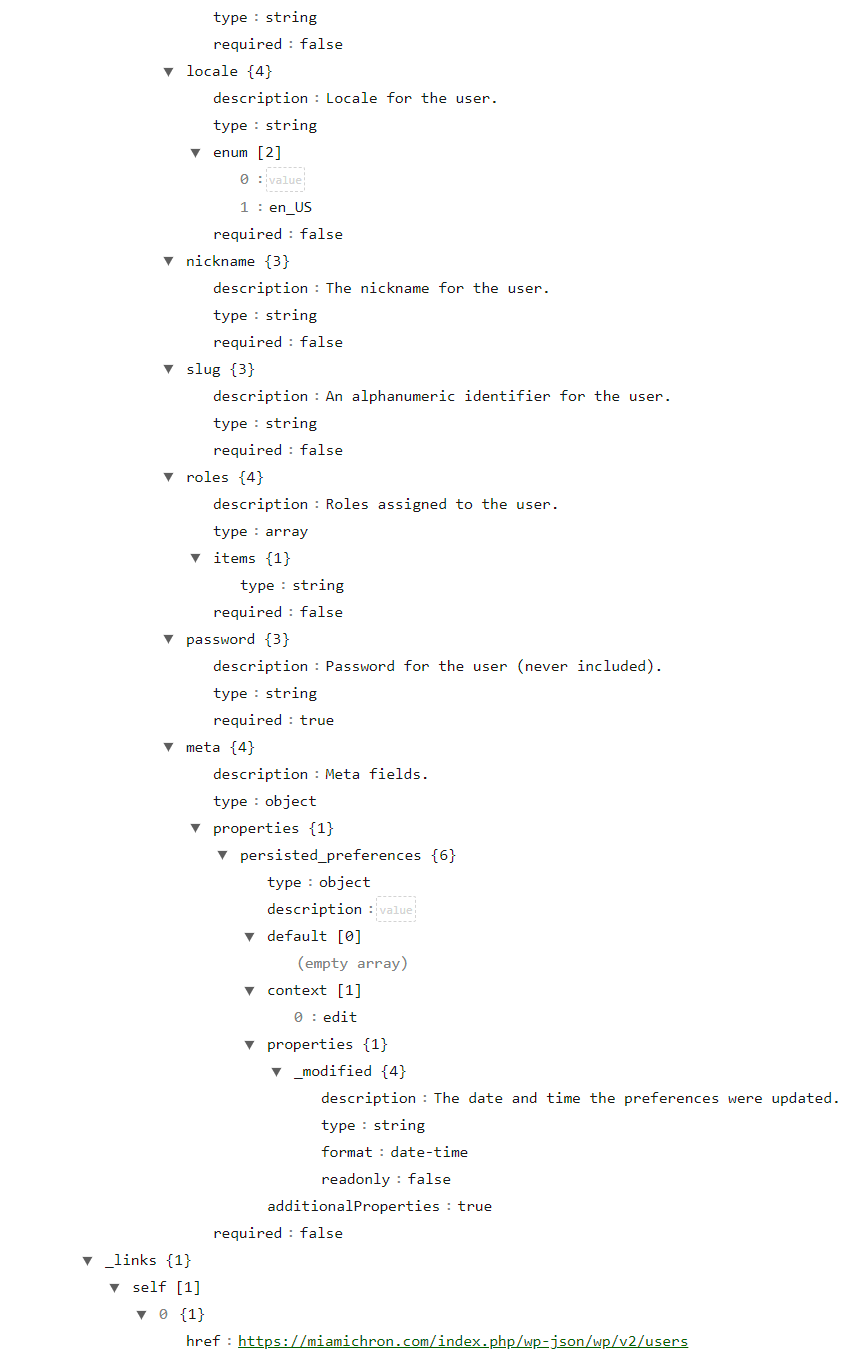
Now we can scroll through the structured JSON content and see if there are any interesting sections. Scrolling through brings us towards a user information section with various fields and an href, or reference link below:
Checking out the link (https://miamichron(.)com/wp-json/wp/v2/users) then takes us to this page, which shows a list of the domain’s user accounts, including not only their name (clearly made up here, Donald Hill, George Clark and so on) but also a Gravatar account.
Interesting! A little-known fact about Wordpress is that Gravatar accounts are created automatically for users upon registration.
The particularly perceptive may notice also that in the avatar URL, which goes like this: secure.gravatar.com/avatar/X, there’s a long string towards the end. That string is an MD5 hash of the email address used to register the account.
THAT means that if we have the email address, or a potential email address, of a user account - we can run it through an MD5 hash function, and see if the hashes match.
Think for a moment what else we could do:
Search the hash in PublicWWW to see if it appears in other domains
Check the Gravatar accounts to see if there’s any information (oftentimes there isn’t)
Hash any email address we have as part of any investigation and check to see if there’s an affiliated Gravatar or Wordpress account
Search the Wordpress theme in PublicWWW to find domains using the same theme with other keywords
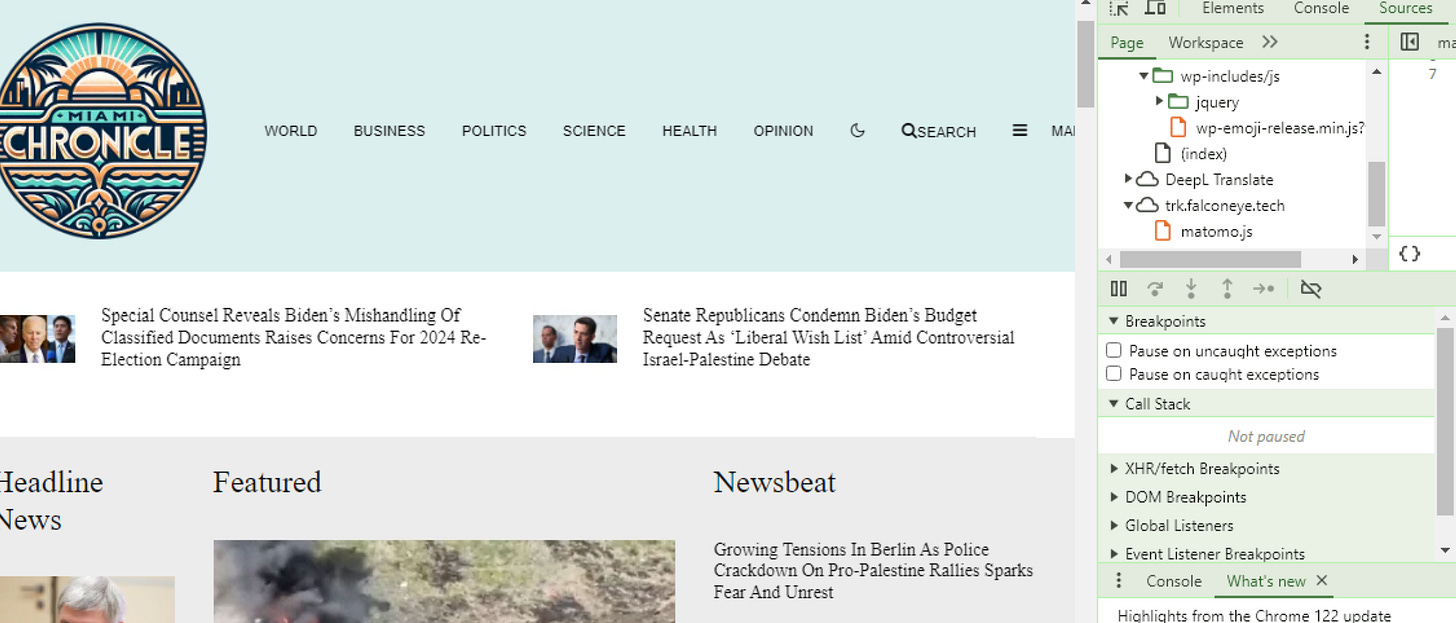
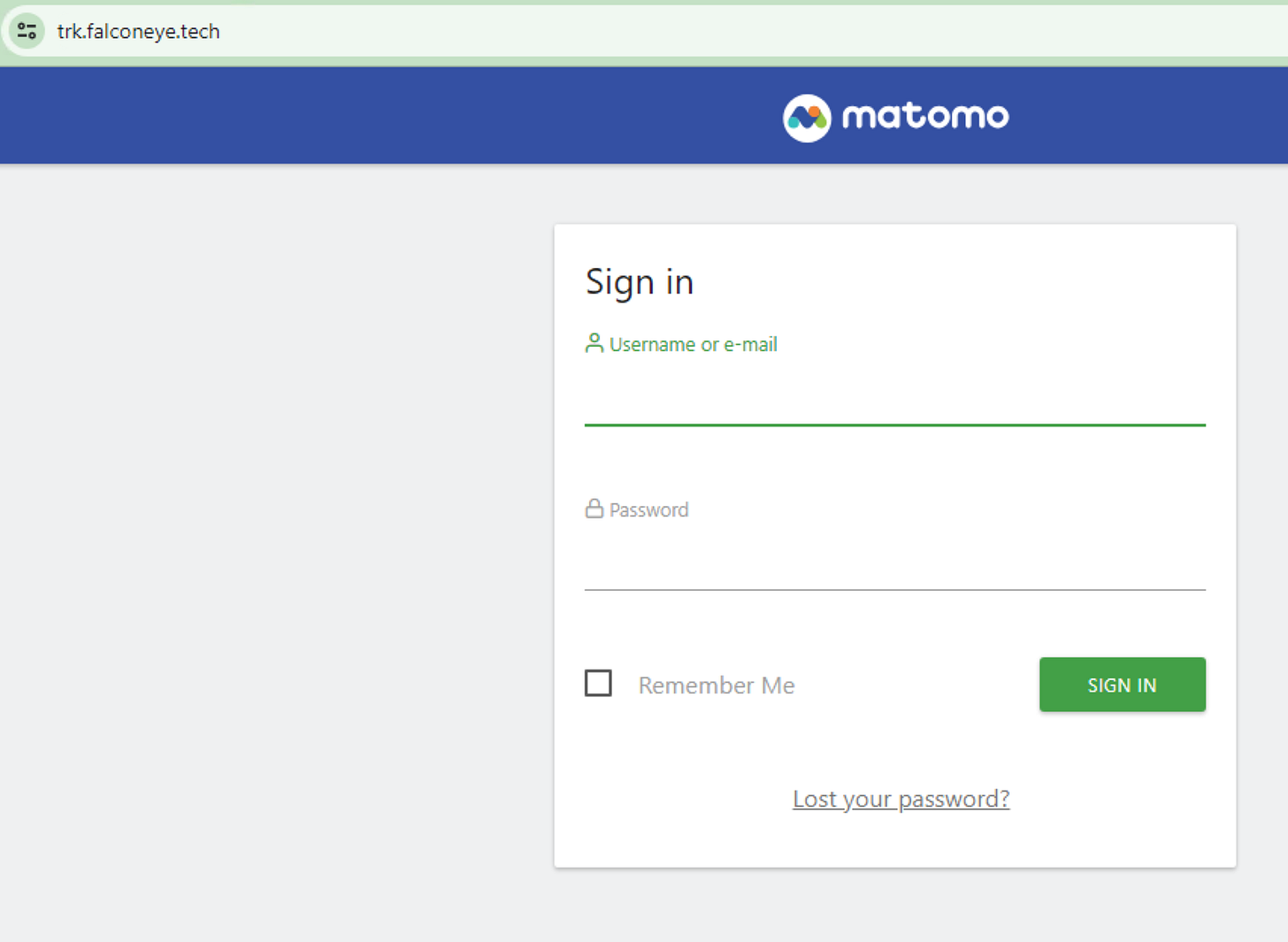
Looking at the domain via “inspect element” and checking out the sources shows that the domain interacts with “trk.falconeye(.)tech, with a script attached called “matomo”. This stood out to me.
Accessing the URL itself leads us to a sign-in panel for Matomo, the analytics tracking script:
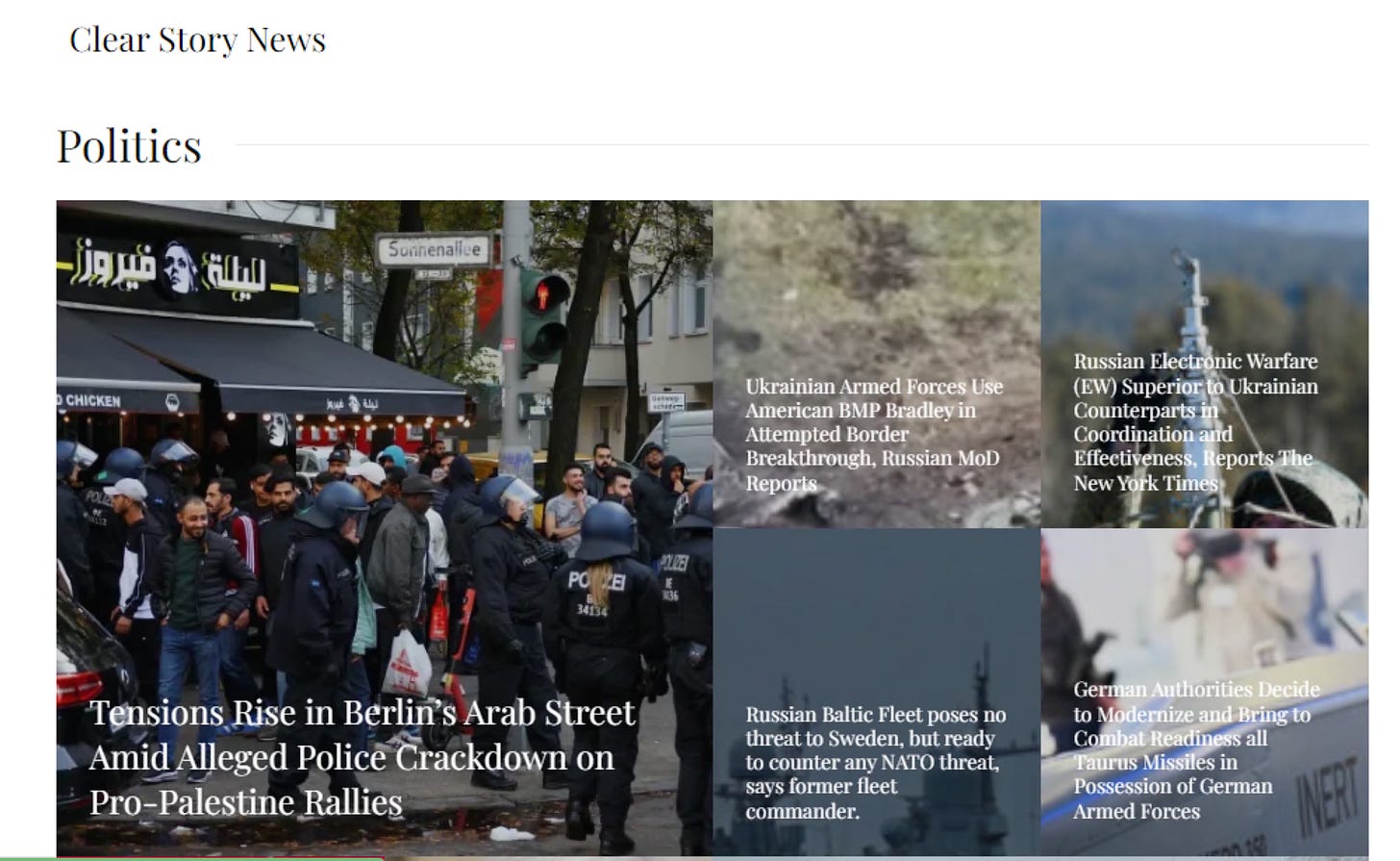
Interestingly though, accessing the root domain (Falconeye.tech) redirects one to a highly similar Wordpress domain, “clearstory(.)news”.
Clearstory is the same domain outed as part of this network in the past. Checking it out on urlscan.io confirms the redirect:
This would be a great new direction for further investigation, which I may get around to sometime.
In the meantime, we’ve:
Found evidence of Russian involvement
Laughed at the poor production quality
Accessed, beautified and analyzed JSON
Found new leads for investigation
That’s it for this week!










We love the step by step investigation walkthrough. Another great read Ari!