Memetic Warfare Weekly: Oh Hai(xun) Mark
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io - and Glowstick Intelligence Enablement.
Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
This week we’ll discuss the South Korean’s National Intelligence Service exposure of Haixun-related activity, it’ll be a bit shorter than usual this week but hopefully I’ll get back to writing some guides in the near future.
Oh Hai(xun) Mark
The South Korean National Intelligence Service has identified 38 Haixun-related domains as of a recent press statement.
The statement could not be more bland. Luckily, though, there is some better public reporting, courtesy of the “NCSC Joint Analysis Team”, available on Medium.
See the below lineup, comprised primarily of private firms alongside the NIS:
NCSC Joint Analysis Team
(National Intelligence Service· ESTSecurity · SK shieldus · S2W · WINS)
Let’s talk for a moment about this before we look at the actual content.
The outsourcing of IO investigation work to private firms is an interesting phenomena, although not entirely surprising. Much of today’s DFIR work is done by private firms - not surprising considering that most critical infrastructure (in the US at least) is run by private companies.
Additionally, large tech firms a la Google and Microsoft are often the best situated to utilize their own internal telemetry to better investigate and expose malign cyber activity in the ways that others can’t.
Lastly, for better or for worse, it’s way easier for a private firm to hire some edgy teenagers who know their way around the memetic space and online investigation much, much better than say, jaded government employees.
It’s therefore in many ways logical to outsource work for IO investigation. IO investigation often centers around multiple platforms with closed-access to data, and trying to cooperate formally with or demand data from large tech firms is no easy task as a government agency. There are legal questions to this as well, so in many ways it’s better to have a private firm(s) handle this.
Now, to the content.
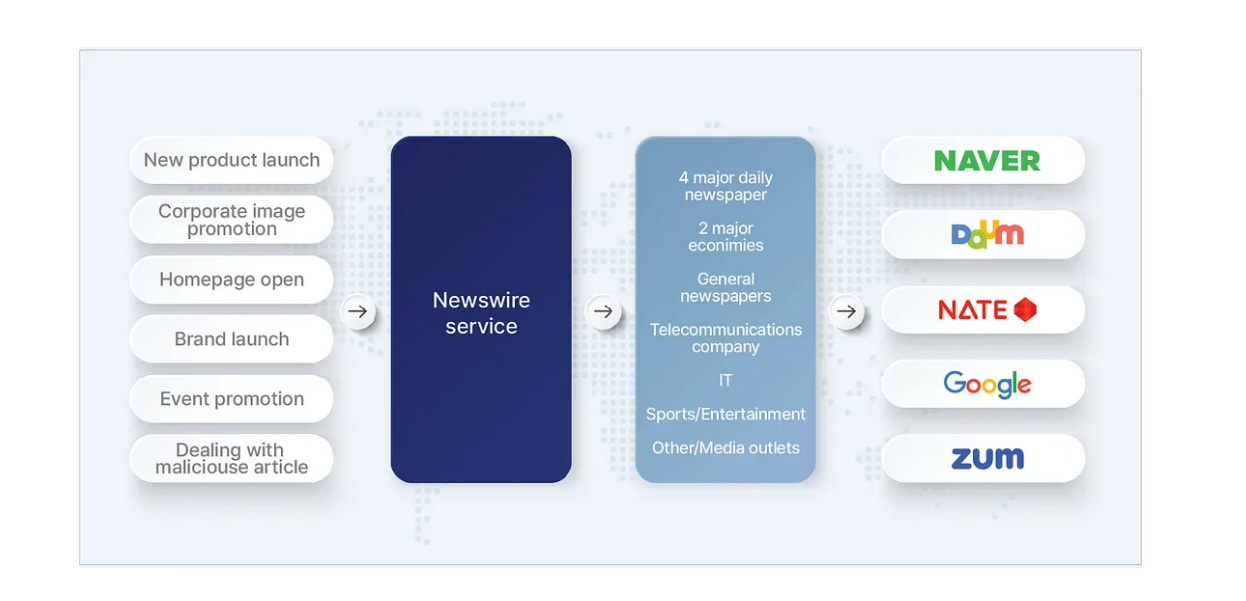
The report emphasizes the utility of a newswire service in laundering content - leading it to be covered and promoted in daily newspapers and so on. From there, it spreads to - interestingly - Korean platforms such as Naver and Daum, with a lesser emphasis on Western platforms.
To be honest, I’d have thought we’d see YouTube somehow in there considering how ubiquitous it is in Korea.
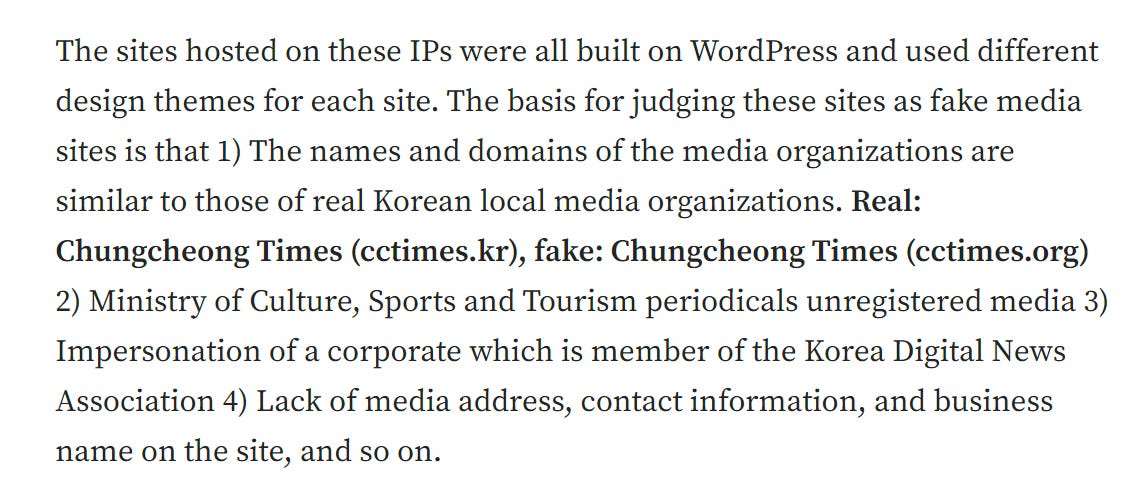
The report also discusses how Haixun, Haimai and so on utilized Times and World Newswire to not only publish press releases, but also host IO domains. Cloudflare was used for one subnetwork, but interestingly a Tencent server was used for 18 sites - bit of an opsec breach, but more common than one might think.
The attribution game here is a bit weak if relying exclusively on the public data referred to, although it’s arguably enough in this case. Reverse IP is enough in these cases when it’s clear that the server is dedicated to the domains, but I’d still like to see additional technical indicators.
Some solid tracking of usernames and content:
Overall, not a bad report and an interesting first for Korea with an agency with a somewhat troubled past in this space.
That’s it for this week!