Memetic Warfare Weekly: Many Such Domains
The Right to Bear APTs
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also do training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
First, we’ll briefly touch on Viginum’s addition of new domains to the Portal Kombat network.
After that, we’ll go over a basic Censys search technique based on SSH public key fingerprinting to find new hosts.
Then, we’ll be fashionably late to the party and review Mandiant’s official upgrading of “Sandworm” to APT 44. In my opinion, the new findings are much more interesting than the APT affiliation.
Finally, we’ll go over the US/NATO/EU/UK attribution and naming-and-shaming of APT 28 and some musings on the brave new world that we live in.
Many Such Domains
One of the lesser-appreciated research methods done historically in IO research is checking in occasionally on past-reported networks. Luckily, that’s beginning to change with consistent reporting on Doppelganger, and in this case - continued reporting from Viginum on Portal Kombat.
Check out the hyperlink above to see the addition, in this case adding over 31 new domains to the Pravda network including 19 new targeted EU states and most interestingly (in my opinion) domains targeting east Asian states:
SSH - Pocket Sand
Long-time readers may recall the “Times Newswire” domain network and its affiliation with Chinese networks as shown by Mandiant. Other research, such as the “Paperwall” report done by Citizen Lab, has found more ties to additional domains, including domains targeting central Asia and Russian audiences, available here.
There’s been a ton of research done on this specific network recently, but I wanted to take a look at some lesser-used methods to show how additional hosts and domains can be found.
Looking at the Times Newswire domain, one can see that it’s currently hosted on an AWS host, while still using a QQ mail server:
As an aside, that host has been used by Times Newswire in the past, focusing it seems on various Brazilian domains for clients:
Anyway, prior to being hosted on AWS, the domain was hosted on a Russian server. The port 80 HTTP response is in Chinese, saying that the page can’t be found, and 443 says something about “Aksay Daily”. Let’s look into that.
Looking at the header response gets us the domain - aksay daily (.) com.
Searching that domain retrieves a surprisingly 5 hosts on the same Russian provider as well as American hosting services. In these scenarios, we have some an interesting pivot to do.
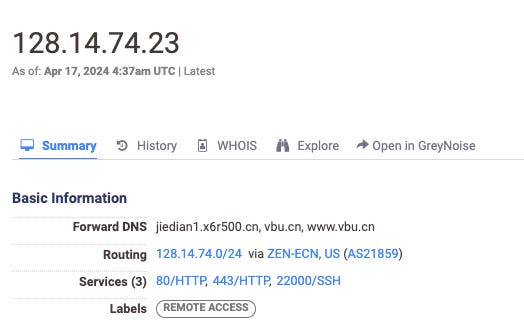
When looking at host results in Censys, be sure to note what services they run. Seeing 80 and 443 is almost always a given (they’re the ports for HTTP and HTTPS), but other ports and services such as 21 for FTP or 22000 or apparently 36339, for example, for SSH.
SSH enables two devices to create a secure connection between the two for remote access via cryptography, and thus involves the use of public and private keys to initiate the encryption for the TCP connection. These can be uniquely generated per host, but are also often reused across the same servers owned and operated by the same operator.
By opening the host above beginning with 128, we can scroll down to its SSH remote access service to see the service.
Then, we can click on “fingerprint” to search Censys for any other hosts with the same SSH key:
Here we get 9 hosts, all in the same IP range, with some sequential IPs even, all of course on the same ASN and provider.. The hosts are highly similar in some cases in terms of their services, and in some cases have the same TLS certificates provided by Chinese providers:
Many of them host Chinese domains as well, see one example below:
The point of the above exercise is to showcase how in many cases, especially when looking at sprawling infrastructure from companies, the hunt never truly ends. Low-hanging fruit from Censys and other tools can still be quite effective in mapping out hosts!
You WILL Post about Ze Sandworms
The mentats at Mandiant published a great new report on APT 44, more commonly known by having the coolest threat actor name of “Sandworm”, available here. It was nice to see the obligatory Dune reference in the image:
The report is holistic, focusing on global activity:
Beyond global activity, the report also covers “full spectrum” activity, including combined IO activity:
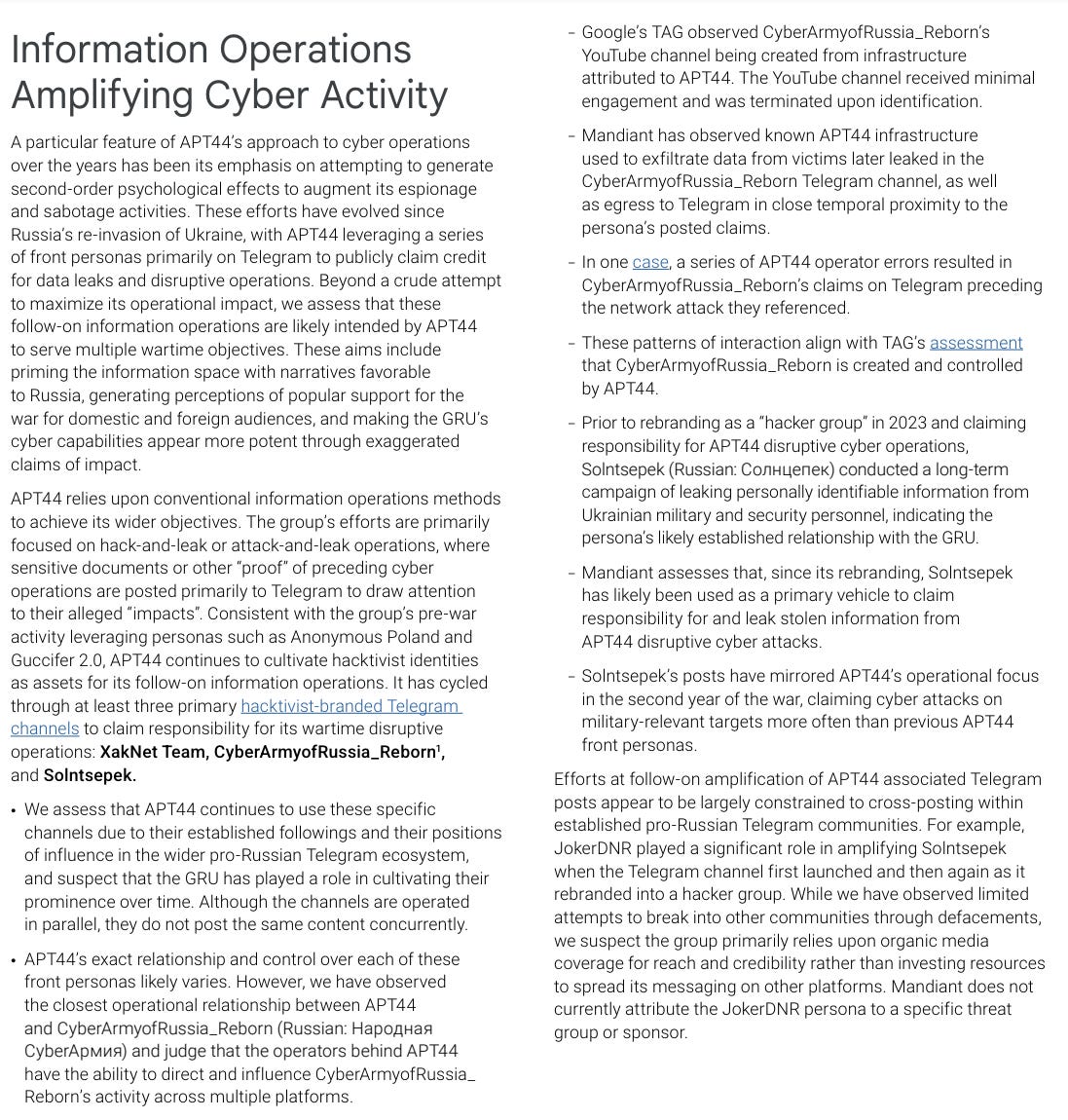
The emphasis on influence/information operations is noteworthy in that it primarily comes to bear via front channel activity on Telegram:
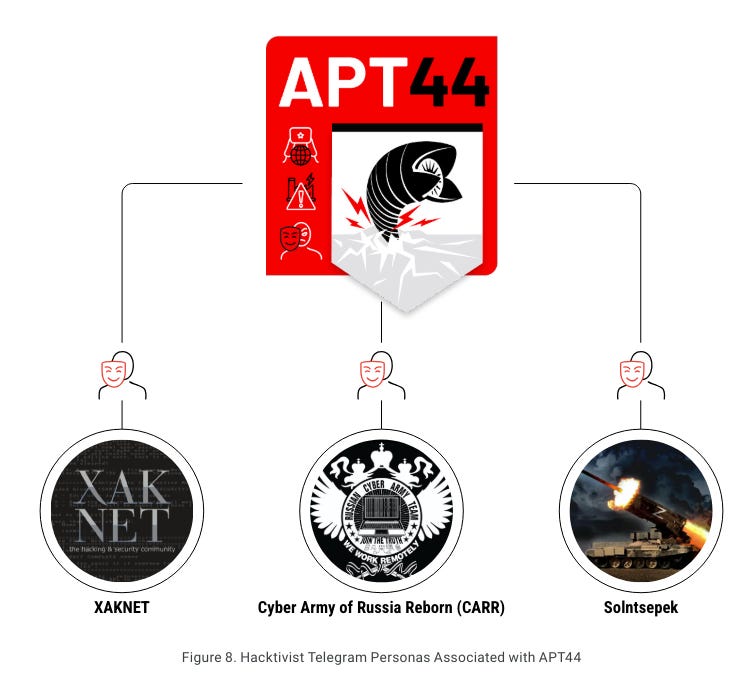
We’ll now skip to the IO section. APT 44 activity, as per the report, focuses on three hacktivist groups:
See below the description of their activity:
There’s a lot to take in here. What are the points that we can take from this though?
Telegram front activity for cyber-enabled IO appears to be the new standard, although that is by no means to say that traditional social media won’t be exploited.
Amplifying otherwise underwhelming attacks can be done by state actors as well as hacktivist groups incapable of more serious intrusions.
State actors can play the long game. Cultivating audiences for maximal impact months or perhaps eventually years down the line is in-play.
OpSec is still hard - note that APT 44 has had observed infra being used to create a YouTube channel for CyberArmyofRussia. Known cyber infrastructure being used later for IO may not be a new trend; ASPI found some evidence that APT 41 infrastructure was potentially tied to Spamouflage actors, available here.
Internal telemetry is key for investigating high-level threat actors. There would be no other way to determine that said infrastructure was used to create that YouTube channel.
I’d be curious to read more specifics about how Mandiant observed APT 44 infra being used to exfiltrate data from victims later doxxed. I presume that this could originate from whenever a known, doxxed victim had a Google asset compromised that left artifacts from the intrusion? There are other interesting points as well:
The emphasis on organic media coverage and growth is interesting and IMO noteworthy. It also helps minimize exposure to social media platforms that could be used to disseminate content.
Lastly, there’s an interesting emphasis on a few cases of IO and critical infrastructure attacks overlapping:
Lot to take in here, and I’m looking forward to reading what the rest of the community has to add to this - especially now that we’ve reached full IO/Cyber convergence in analysis in leading firms.
The Right to Bear APTs
Continuing this week on Russian APT activity, there’s been a veritable circus of activity surrounding APT 28 and its activity in Europe. APT 28, one of Russia’s leading hacking groups, has been a thorn in the side of the European Union for years.
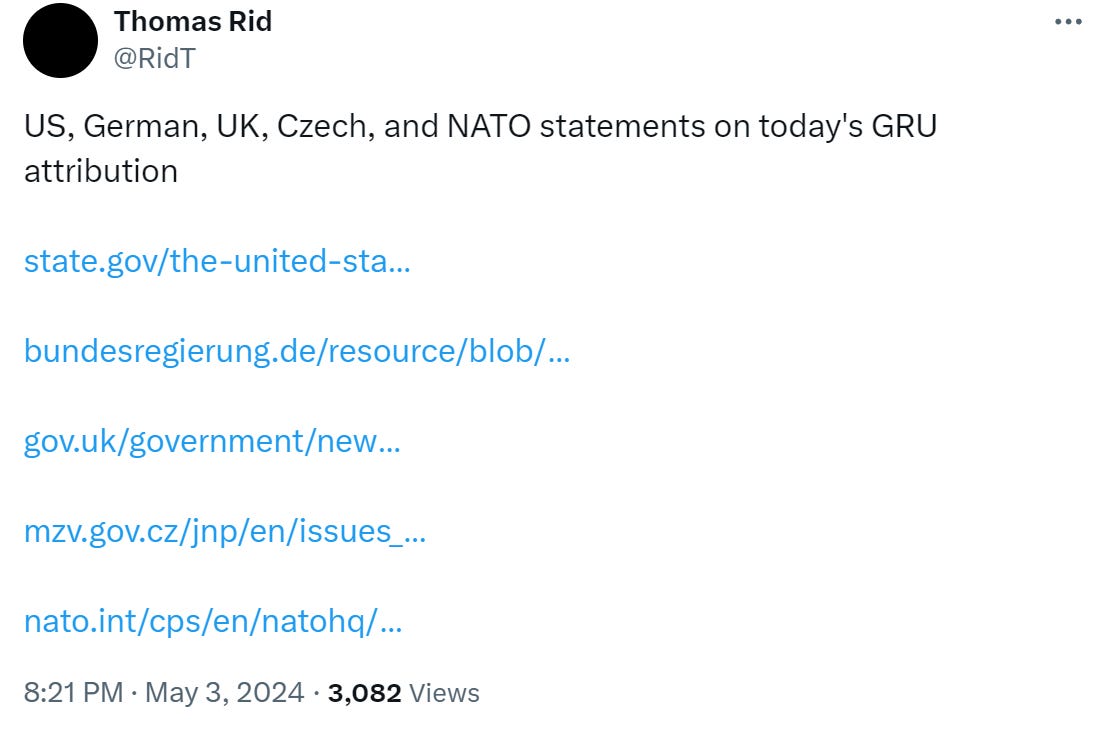
After years of malign activity and a much, much delayed time to respond, the US, NATO, Germany, the UK and the Czech Republic are finally attributing APT 28 publicly and calling out recent malign activity.
Thomas Rid’s coverage, available here in part, is worth following to gain a holistic view:
Rid’s criticism of Germany is very much appropriate considering the past 10-15 years or so of Germany policy on Russia, beginning primarily under Merkel to the best of my knowledge. Germany’s weak stance on Russian activity and incredibly late attribution here (as per Rid) is much-warranted and hopefully is yet another harbinger of a new sign of European geopolitics regarding malign foreign activity from both Russia and also of note as of late - China.
Dan Black of Mandiant pointed out that APT 28 has been involved in “active measures” in Czechia, and that the threat isn’t just phishing, compromising elected officials and government agencies, targeting election infrastructure and more:
Following the unusually strong public naming-and-shaming of APT 28 and Russia, and even the call for “consequences” from Germany and other states, a fire broke out at a factory in Berlin. It’s still unclear what happened here, so let’s be careful before making any assumptions, but some are already claiming that the fire was started by Russian agents.
The factory belongs to Diehl Metal Applications, a subsidiary of Diehl Defense, a company that produces air defense systems for Ukraine amongst other systems. According to some online commentators that I haven’t been able to verify, Diehl Metal only carries out civilian work, with this factory manufacturing automobile parts.
TASS, Russian state media, is already out there quoting Der Spiegel saying that the fire won’t impact IRIS-T production, so there may be some truth to the above claims that the wrong factory could have been targeted.
Russian state and grey media outlets have already jumped on this, emphasizing the potential threat that the fire poses to Berlin residents
Sputnik also got in on the action:
Let’s see how this pans out. Could be a normal industrial accident, or could in fact be Russian sabotage, and as tensions grow and naming and shaming becomes even clearer, we can presume to expect more hostile action in Europe between the US/NATO/EU bloc and Russia.
This has arguably already occurred. The Financial Times has reported that European government officials are already stating that Russian sabotage operations in Europe are already a significantly higher risk vector than they were before, despite them already having been a significant one in past years.
The much-vaunted inherent advantages of influence operations (and cyber operations to a lesser degree) is their presence in the grey zone, below the threshold of overt or kinetic retribution.
Countering influence operations and cyber activity is often more expensive and difficult (practically and politically) to do than carrying out offensive IO/cyber activity, a dynamic that provides significant operational incentives to the side on offense. Taking a strong stance and incurring significant cost for IO/cyber could lead to significant escalation - a situation usually not desired by both sides.
This dynamic makes sense so long as the victim is not interested in escalation, as said, and is incapable of conclusively attributing the perpetrator of said activity. This was the case for the past 10-20 years in between Russia and China and the “West”, but it’s not so anymore.
Cyber war, as Rid stated it in his now seminal article, will (probably) not take place. Now, it seems that a move from the memetic to the kinetic, or a combination of the two, may well take place, at least in Russian-EU relations. It’ll be interesting to see how this develops, as sabotage and other “below-threshold” kinetic activity, such as assassinations, can lead much more quickly to full-blown kinetic escalation than a few malicious posts.
That’s it for this week, next week we’ll discuss ASPI’s latest report and other developments.