Memetic Warfare Weekly: Into the Breach(forums)
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io - and Glowstick Intelligence Enablement.
Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
We’ll kick this week off with a shoutout to Margot Hardy, a former Viginum analyst with her own election interference-oriented Substack, check it out below:
2024 will be a big year for elections, so be sure to follow her for analysis regarding elections, the DISARM framework, and other topics.
Taiwan 3: Rise of the Bots
Let’s get back to the Taiwanese elections. The recent elections resulted in the victory of Lai Ching-Te, a third consecutive victory for the DPP. The actual numerical split of voters is interesting as it was a three-way split, but I’ll leave that for election wonks.
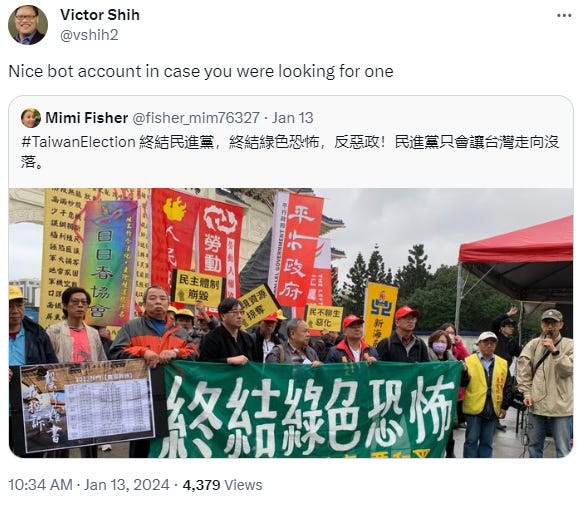
Unsurprisingly, there was interference as to be expected, but overall the election went smoothly. Victor Shih, a great resource on Chinese/Taiwanese affairs, pointed out a Twitter botnet active during the Taiwan elections denigrating the DPP:
With this one we have the resurgence of the use of a GAN profile picture - anecdotally I can say that I see these less and less over time, so always fun to see these come back. The operator lost points for not adding a cover photo and using such a new account and not having any followers/following, but at least the username and the display name are congruent!
The account itself may not be immediately apparent as a GAN image for those who aren’t versed in the ways of generative adversarial networks, but I promise you: if you spend a lot of time investigating IO, you’ll be able to spot these from a mile away.
Other network accounts utilize GAN images and stylized anti-DPP content:
The use of GAN images, similar display/username alignment and content overlaps all indicate that these are probably part of a wider network.
These kind of networks garner 0 engagement and frankly aren’t even worth operating in my opinion, and yet - it moves.
Into the Breach(forums)
ASPI’s Albert Zhang also published a longer look at Chinese interference in the elections, available here. Zhang claims that known Spamouflage clusters were active on Twitter, Facebook, blogs and so on. I haven’t had the time to look at this in-depth, but it’s quite possible that the accounts mentioned above are Spamouflage-related, even with their comparatively unique aesthetic for content.
Have to say I’m loving the use of AI pictures to get Lai Ching Te into a Mets jersey.
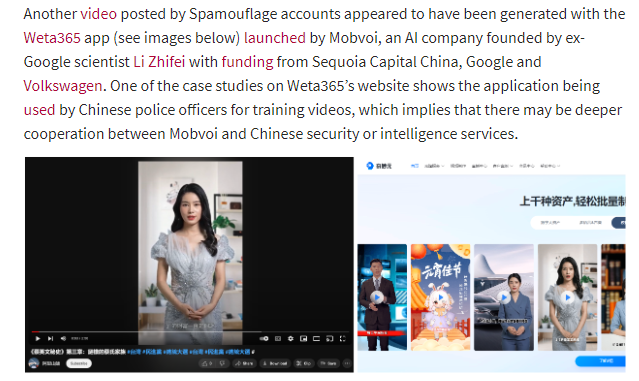
Zhang of course mentions the “Secret History of Tsai Ing-Wen” document, and links to a few relevant entities on X/Twitter, Facebook, Reddit, WeChat and TikTok. Commercial AI announcer tools unsurprisingly make an appearance, this time from the D-ID and Weta365 tools.
The most interesting part of this, by far, is the utilization of BreachForums in whatever iteration it currently is by an inauthentic account as Zhang describes. This account uploaded supposed information and a document regarding an alleged “love child” belonging to Lai Ching-Te - see below.
From BreachForums, the post and document were then posted on 4chan, and eventually the narrative, titled “‘Lai Ching-te’s illegitimate son’ (賴清德私生子)” made it to mainstream social media and other forums. Below we have a screenshot of the actual document - to be honest, it should scream suspicious to anyone looking at it. Absolutely unprofessional work here - be it “DNA Test” and “Report” not being on the same line and not being centered screams inauthentic to me.
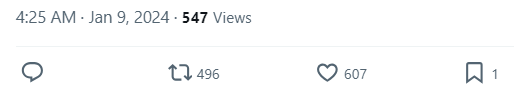
This tweet of course has levels of engagement that show artificial boosting: 547 views with 496 retweets and 600+ likes.
Having looked at this Twitter account as a miniscule sample, it definitely appears to be Spamouflage-related. Why do I say that? Because beyond tweeting out this document, it also has an unhealthy obsession with Guo Wengui, which in my experience is a pretty indicative behavior from Spamouflage clusters.
Looking at the rest of the network, as Zhang did, shows that a central node in the Twitter network was, amazingly, a Jonas brother, user @ NickJonas 154141! Jokes aside and in all seriousness, it’s fascinating to see that a central node was identified by Meta in their last Adversarial Threat Report but wasn’t taken down, enabling it to then continue to act freely.
There is significant overlap with anti-India/BJP content pushed by these networks, but that is beyond the scope of this blog.
All in all, Zhang did an excellent job looking into this and brought some interesting points to the forefront.
It’s fascinating to see the overlap between IO and CTI continue to be relevant - in this case using Breachforums as a platform for seeding. I haven’t come across Breachforums being used in this context - if anyone has, please let me know! We also see some greatest hits come back, like using 4Chan as an early seeding platform similar to Russian use of 4chan for the Macron leaks and numerous other information operations.
The Chinese use of hacking forums and 4chan for seeding if anything is the most relevant section of this report for further research and is probably the closest actual case we have yet of Chinese activity presumably learning from Russian activity when it comes to seeding, and not the use of “AI” or whatever other low-level TTPs people mention when they promote the platitude of China copying Russia.
Lessons learned here? If you want to be good at IO research, you have to know your way around the internet beyond mainstream social media, and you have to spend time on hacking forums, messaging applications, and 4chan. Having a broad view of the internet is critical to being able to actually investigate effectively and understand the threat landscape.
The other lesson here is that past identified entities are critical for monitoring and source development! I’m a big believer in entity-based source development, as I’ve written about here, and the Nick Jonas Twitter account is an excellent use case.
Terrance and Phillip: Behind the Asset Freeze
In an interesting legal case, Graham Phillips, a pro-Russia former British civil servant now residing in Ukraine, was sanctioned by the UK government due to his support of Russia online, primarily on YouTube.
Phillips took them to court and lost, claiming that he wasn’t accused of being part of any sanctioned Russian organization. The UK government responded, with the court stating that “decided to set his face against an overwhelming international consensus, to align himself with Russia’s invasion of Ukraine, to travel to the frontline, and to help Russia fight its propaganda war”., which the UK government presented as a risk to UK national interests.
Phillips is the “first mono-British national” to be sanctioned by the British government.
This is a fascinating legal case to follow in quite literally every aspect for those interested in the legal and policy implications of interference and influence work.
There’s a lot of legal precedent and issues here to unpack, so I’ll let those more qualified than myself do so. Have a legal background and want to write about this here as a guest post? Reach out!
Continuing in the vein of AI-generated content, Benjamin Strick uploaded a fairly length look at AI-generated imagery and how to best analyze it. This is one of the more in-depth, qualitative looks at this topic so far so I’d recommend watching it, and much of the overall methodology is relevant for any kind of investigation in terms of mindset.











Giving this some authentic boosting: a like and a comment. Good read!