Memetic Warfare Weekly: Formosan Facebook Fakes
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io - and Glowstick Intelligence Enablement.
Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
It’s time to ring in the new year with a presumable sneak peek at what we can expect to see much more of coming soon: alleged Chinese interference in Taiwanese domestic politics from Graphika’s reporting. We’ll highlight their investigative use of TikTok Web IDs and discuss them a tad more in-depth.
After that, we’ll take a look at the ODNI report on foreign interference in the US Midterm elections.
Formosan Facebook Fakes
Graphika’s latest report on what they don’t attribute as Chinese (but let’s be real) activity has some points I’d like to bring up. It’s available here, and is surprisingly brief, which I mean in the best possible way - brevity is divine.
The network was active on various platforms, including Facebook and TikTok, and was of course oriented towards influencing Taiwanese politics.
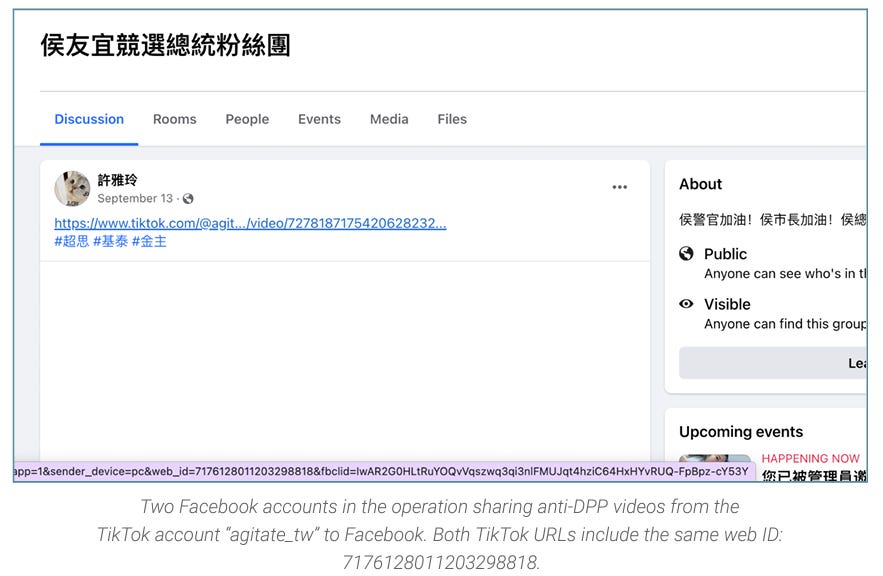
Some high points of the report include the various OpSec breaches almost inherent to running any large network. The best breach is the utilization of TikTok’s “Web ID” to identify content shared from one specific account:
The web ID for TikTok is a bit different from other platforms, as it doesn’t follow the traditional web ID/tracker format for Twitter or other platforms.
On Twitter, the same shared web ID would follow a question mark appearing in the shared Tweet. Want to make sure that you never share social media content with your own web ID exposed? Remove anything appearing after a “?” in the link, and check out Brave, which has a “copy clean link” feature.
Back to other OpSec breaches. Network accounts would apparently often check in at shared locations, thus exposing other accounts that also checked in at the same location. This is an OpSec breach that may be indicative of automation as well, and may additionally be an attempt to carry out diverse, on-platform activity to convince enforcement algorithms that the accounts are in fact authentic.
The classic TTPs, such as reusing stolen profile pictures, resharing content and so on are also of course all in attendance.
What’s lacking here is, in my opinion, a deeper attempt to attribute and investigate via identifiers. I’m sure that Graphika pursued this avenue, but I’d prefer for this to be mentioned, even if no quality results were found, than to have this avenue not mentioned in the report. Same goes for attribution - even if it’s just content-based or heuristics based, would be nice to see a bit more.
Borrowing an Influencer Out to Sea
The ODNI declassified the American government’s “Intelligence Community Assessment” on foreign threats to the 2022 elections, available here.
A large portion of it is redacted, so we’ll discuss briefly what has been brought up and is of note. Let’s start with “key findings”:
Pretty much all of the above could have been independently surmised by anyone that follows the IO space, but nice to see it written down still. The “Discussion” section is where it starts to get more interesting:
Activity is of course still below any presidential election, but seeing an uptick for midterm interference from 2018 is overall a solid indicator of the growing importance and maturity of the space.
Most interference efforts weren’t cyberattacks but rather IO operations. These operations themselves are still very much in the process of transitioning to influencer/PR/proxy use. Also unsurprisingly, but intelligently, most actors focus their efforts on amplifying America’s best and brightest social media influencers to get their message across - why not? We’ve discussed it in the blog - it’s cheaper, more effective and more deniable.
Apparently a “named” senator was denigrated with inauthentic accounts by China, any idea whom? Based on my experience this could be essentially any senator with any past statements on China - I’ve come across multiple cases myself of US politicians being denigrated by inauthentic accounts, so wouldn’t exactly call this unusual behavior.
Unsurprisingly, and as everyone says, there are weaknesses in tradecraft for limited traction.
Much of the report is unsurprisingly dedicated to China, but then, and interestingly, it jumps to Iran before Russia. Some of the sections would be entertaining Mad Libs:
Twitter takedowns were mentioned - in my opinion this contributes to my belief that a fair amount, if not arguably most, of the US and any government’s capability to investigate and counter IO relies on OSINT at worst and platform cooperation at best.
We’ll skip the Russia section, as it’s interesting but overall what you’d expect. What I especially enjoyed seeing was what came next: Cuba.
Cuba is very much under-the-radar when it comes to cyber and online IO activity. Unsurprisingly, much of this is Florida-centric:
From here on out it’s almost all redacted, but still worth reviewing.
Reviewing the public content as a whole, it’s pretty much what you’d expect. A reasonable overview of foreign/malign influence activity, and I didn’t see anything that would change my view on American government approaches to the topic. Perhaps that’ll change in the future.