Memetic Warfare Weekly- Every Op, Everywhere, All At Once
Put on your thinking Ushanka
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, research and consulting services in IO, CTI and OSINT.
Memetic Warfare (bi)Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
This week’s blog is going to focus on hack and leaks, hacktivist fronts, cyber-enabled IO and everything in between.
Every Op, Everywhere, All At Once
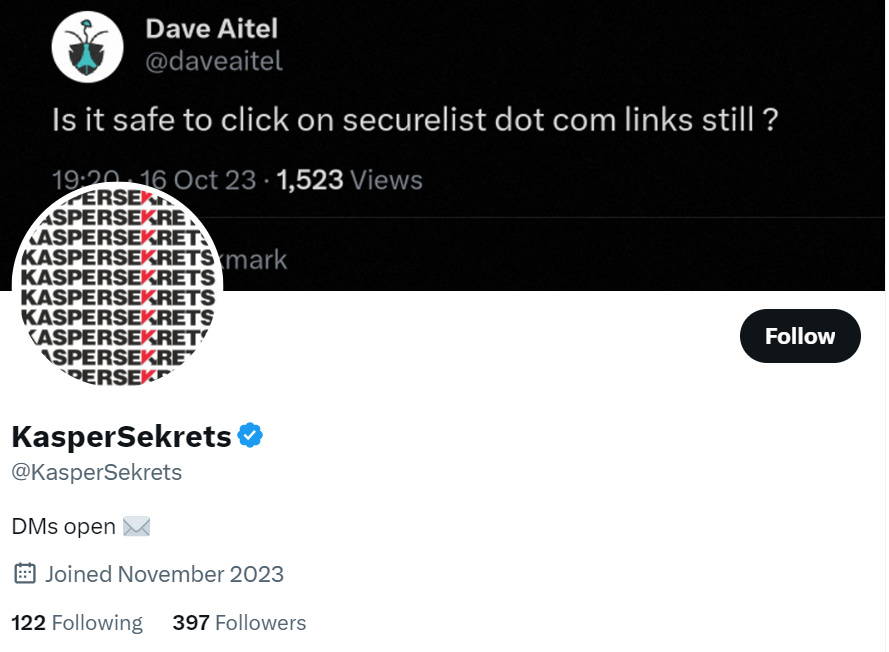
Independent researcher and prolific Twitter user x0rz (worth following also) brought to my attention a new Twitter account leaking data on Kaspersky Labs.
X0rz accurately points out that this is quite the coincidence considering the recently exposed, suspected US-hack of Kaspersky Labs with a God-tier 0-day vuln chain of Olympus, utilizing no less than 4 new 0-days. I may be wrong here, but the last time I saw so many quality 0-days burned was in Stuxnet - if I’m wrong here reach out and let me know which op I’m missing!
The account has a very tongue-in-cheek and even Extremely Online™ style of speech, which I can’t help but appreciate. KasperSekrets, the stage is yours at Memetic Warfare Weekly for guest posts if of interest!
The account also has its DMs open and waiting to be slid into. This is a TTP seen by other IO actors who seek to provide themselves with a “veneer of legitimacy” by seemingly crowdsourcing their data via leaks and others.
Intrusion Truth, another of my own favorites, does the same. This is useful for two reasons: it provides an easy way for the actor to launder data acquired by hacking or closed-sources as having been “crowdsourced”.
Additionally, who knows? Perhaps someone actually will one day reach out and send them some confidential documents.
Intrusion Truth takes this a step further - they claim that their findings are primarily OSINT-related with only a few user contributions. This may be the case, but it’s also very possible that they acquire high quality, “exquisite” intelligence and then reverse-engineer it with OSINT to make it presentable without burning their sources.
Back to KasperSekrets. They post primarily leaked documents taken from Kaspersky meant to embarrass Kaspersky, oftentimes by showing alleged violations of international sanctions:
Notably, the account (or Intrusion Truth for that matter) leaks responsibly by not publishing all available raw data which could endanger low-level employees, or innocent, unrelated victims.
It wouldn’t be a good online operation if it didn’t include some memery:
The use of humor and memes is a well-known “TTP”, if we choose to call it that, in IO and counter-IO work:
The Superbad meme is great but honestly also may indicate that the individual of a certain age; the average zoomer wouldn’t immediately recognize McLovin even if he were to whip out his fake ID.
Some of the wording may also be indicative of it being an American operator, or at least someone well aware of the time-honored practicing of pouring one out for the homies:
In addition to being quick with the puns, the operator(s) also speaks Russian.
Notably, KasperSekrets actively retweets American/Western security researchers and others, and occasionally retweets them. KasperSekrets also follows and actively trolls Kaspersky Labs accounts, occasionally doing both at once:
Hacktivist groups and front groups often don’t follow other accounts or engage with other accounts at all to preserve their OpSec and not expose any biases.
I believe that the choice made by the KasperSekrets operators to actively be in the broader community and troll Kasperky is meant to help drive engagement and make their content reach a broader audience, thus harming Kaspersky and their international sales efforts. This is especially relevant in the light of American and European bans of Kaspersky products in certain contexts.
Let’s put on our thinking Ushanka for a moment. Leaving the recent hack of Kaspersky aside, who could:
Compromise Kaspersky and exfiltrate data?
Make consistently relevant, well-written American cultural references?
Have a basic understanding, at least, of Russian?
While you may immediately think of a government agency, frankly the possible answer set of who may match the above criteria is reasonably broad.
That means that it’s not feasible with the information we have to conclusively or even confidently attribute KasperSekrets to an American or Western intelligence agency or group, as appealing as it may be.
If we do assume that it is a Western agency though, I have to admit that I’m pretty impressed. It’s not really feasible to have a truly anonymous AND effective information operation, as the necessity to amplify and propagate content makes anonymity very difficult. This is the sort of contradiction in IO that lets us attribute (very, very roughly) cases such as these.
As an aside, I have nothing against Kaspersky in of itself (assuming that the leaks aren’t verified yet). However, assuming that they are, this is the kind of 4-D Chess that I’d like to see in the Western IO space (assuming that it is a Western actor): targeted yet impactful IO activity that Western countries should engage in alongside their network intrusion efforts. Impacting high-value targe, even companies IF they engage in illegal activity or otherwise overtly cooperate with certain regimes, with minimal collateral damage and in a responsible fashion is the way forward.
Advanced Persistent Telegram
On the Israel-Iran front there’s been some interesting activity recently as well. Israel’s domestic security agency, the General Security Service (shortened by its Hebrew acronym to “Shabak”) is responsible for counter-interference and IO work. While they, alongside other Israeli agencies, are known for being tight-lipped, they do occasionally publish and expose interference and IO activity.
They recently exposed some Iranian activity targeting Israel in light of the ongoing war. Most of this activity was Telegram-centric, and included some key themes. The below images are taken from a Ynet article available here in Hebrew.
The first, and most common from Iran, is the utilization of extremist rhetoric and groups (see the below fake group for the ostensibly far-right and fake “Jewish Fist” group meant to stir social dissent:
Iranian actors did the same for the other side of the political spectrum by creating fake protest groups to promote the return of Israeli hostages taken by Hamas:
Some of the exposed activity also was much more easily exposable, such as a case of a fake Hebrew-language and Israeli Instagram account that was easily exposed by the “account transparency” section as in fact being based in Iran.
OpSec is Hard
Following the recent exposure of the Triangulation operation targeting Kaspersky, there’s been much discussion (on Twitter, where else), of what REALLY constitutes an APT in light of the aforementioned Vuln Chains of Olympus, which is the new technical phrasing that I will be using going forward. Big 3 APTs are often viewed with reverence, but frankly - they often make ridiculous OpSec errors that Western operators make far less frequently.
Katie Nickels of RedCanary brought up a great example of an embarassing OpSec slip-up below:
Generally speaking, there’s a much higher degree of professionalism and capability in Western actors, which makes sense for multiple reasons. Autocracies have a hard time preventing corruption, moonlighting, enforcing rules and even hiring quality individuals, so don’t be shocked when corners are cut.
That’s it for this week!