Memetic Warfare Weekly: Decoupling in the Name
Also Featuring: Influence-Ception and The Intrusion Truth is Coming from Inside the House
Welcome to Memetic Warfare Weekly!
My name is Ari Ben Am, and I’m the founder of Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I also provide consulting, training, integration and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
Before we begin - I’m going to put in a good word here for an upcoming webinar, open to the public, hosted by Falkor - an analyst OS and investigation/fusion platform which is pivoting towards T&S. The use-case covered is child safety-oriented, but I’m always happy to help out an investigation-oriented product or platform, especially when they focus on under-reported topics.
Let’s begin now with this week’s blog!
Decoupling in the Name:
The past few weeks have been rocky, to say the least, for China.
Let’s start off with the Chinese crackdown on Capvision, an international consulting and advisory firm. Capvision provides a variety of business services to its clients in China, including most interestingly its “global expert network”, which utilizes to at least some degree Chinese experts.
Chinese police raided Capvision’s offices throughout China in recent days, with Chinese state media claiming that Capvision often reached out to Chinese government employees with access to sensitive or classified material for its network.
Other due diligence or business advisory firms active in China have also been raided recently, such as Bain and Mintz under similar claims that their work undermined Chinese national security. Much of their work could potentially be construed as such, but is also pivotal to daily business operations - vetting suppliers, researching officials for corruption and more.
The need for China to clamp down on foreign access to domestic information is quite clear at this point - be it limiting the physical presence of companies that carry out research for business purposes as above, or via online research published by think tanks that exposes other not-so-secret Chinese secrets.
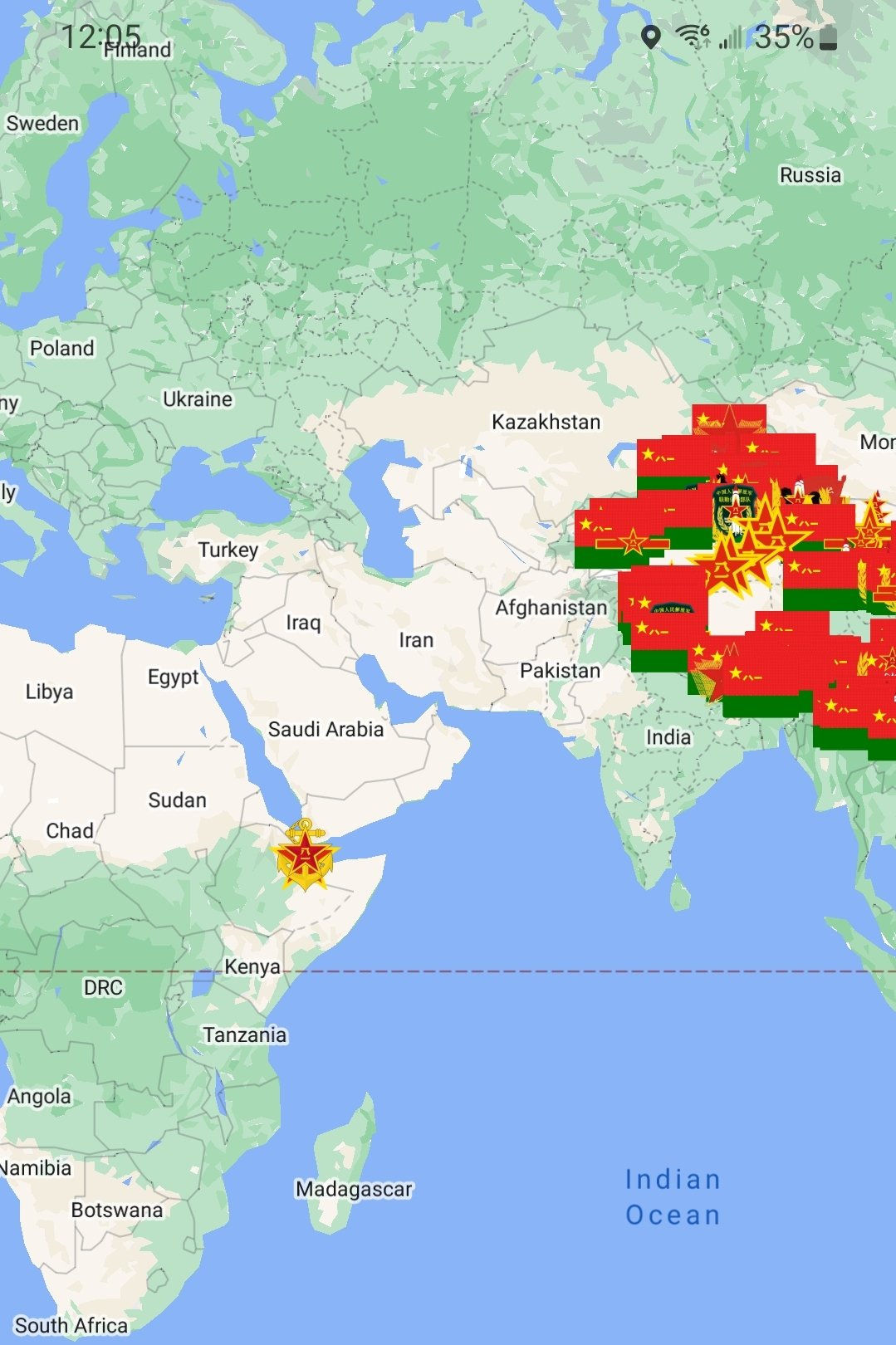
OSINT research with China is still in many ways under-utilized. Intrusion Truth’s work in general, as well as their new series on an alleged APT based in Wuhan shows the power of what one can do with even minimal information in some scenarios. A Taiwanese college student with a lot of free time created a map of over 1,000 PLA facilities identified solely via search engines - see below.
So clearly online research - and let alone the use of physical assets - is powerful and comprises a threat of some degree to China. The costs of limiting it, however, are manifold: reducing international e-commerce and potential new business ties, knowledge sharing and collaboration on various topics, people to people exchanges and more.
The business implications of limiting both online and physical research and due diligence are also clear: full decoupling in the name of national security. Multinationals will not be able to operate or expand, long-term in China for a variety of reasons without access to due diligence services.
While I personally think that these moves will harm China more than they will harm American capabilities to investigate China, these developments augur what may well come: further limitations on business, potential travel bans, inability to access even basic data via the internet and more.
The Intrusion Truth is Coming from Inside the House
Intrusion Truth, the most active Chinese APT-doxxer out there (covered in-depth here by Kim Zetter), has posted a 3-part investigation into Chinese front companies used as cover for cyber activity, links here: parts 1,2,3. Firstly - hats off to them for using humorous titles for their investigations - hopefully the industry can learn to take itself a little bit less seriously sometimes.
Their recent investigation has some key factors in it that are useful for anyone interested in investigating cyber/IO activity. Firstly - investigating APTs well requires not only technical CTI skillz, but also strong OSINT capabilities as well as as healthy analytical rigor.
These are some of the reasons why I so enjoy IO and CTI investigations in particular. IO/CTI investigations necessitate having the ability to investigate domains technically, dig into global corporate records, exploit social media and much, much more: essentially they’re the ultimate cross-domain form of investigation.
Intrusion Truth’s series brings up a few points that we as analysts/investigators should always keep in mind:
Plan your investigations! Even when investigating “hard” targets like China, there are ways to find relevant information. Intrusion Truth’s first article identified an infosec/hacking training school in China - let’s call it a quality source here - and used the testimonials (indirect pivoting) to identify graduates who may work for APT front companies.
Look for unique identifiers! The basics are always underrated - you don’t always need to investigate a phone number or email address by using paid tools, sometimes remembering to check an identifier across search engines and in a variety of ways can yield relevant results.
Text can be a unique identifier. QQ IDs, email addresses and more are great, unique identifier to search when investigating activity in China, but by thinking creatively other content can be unique as well. Intrusion Truth was able to identify identical job postings as a potential indication of coordination between companies simply by searching for exact matches of the posting itself.
Identical Job Postings - Translated from Intrusion Truth
Keep an eye out for anomalies: Intrusion Truth's blog posts mention how they’re quite adept at this stage at identifying fishy front companies. There’s only one way to truly develop this analytical spider-sense: develop domain expertise and knowledge in your given field, and investigate frequently. If you analyze it, the anomalies will come.
Don’t neglect corporate registrations when it comes to China. Despite the difficulties of investigating China as we’ve discussed ad-nauseum, investing time and effort in investigating companies - both via registries (and by using tools like AsiaVerify) and other methods such as domain investigation or even breached data - is well worth it. Looking at review sections or even forums for some companies and industries can also be incredibly useful.
Most importantly - don’t take reports and their findings for granted. While Intrusion Truth does a good job, and the majority of what they do can be reverse-engineered and verified, the conclusions they draw from their findings should not necessarily be the conclusions that you should draw from their investigation! In any investigation, logic and assumptions will have to be made at some point, but our job is to ensure that we’re productively skeptical as to their underpinnings and conclusions - this goes twofold for any organization not operating under their true identity (with or without good reason).
Influence-ception
The Intercept - an outlet that I usually don’t usually recommend due their strong editorial bias - recently came out with some interesting findings on the development of the US government’s counter-malign influence/disinformation (whatever you want to call it) efforts, available here.
The article focuses on the ODNI’s new counter-malign influence office, the “Foreign Malign Influence Center”, mentioned by director Avril Haines recently and founded officially late last year. The FMIC is one of a bevy of counter-malign influence offices now active in the US government, ranging from the State Department’s Global Engagement Center, the FBI’s Foreign Influence Task Force and the DHS’ Countering Foreign Influence Task Force, a Foreign Influence and Interference Branch and the Disinformation Governance Board to the DoD’s Influence and Perception Management Office - and all of these in the past few years alone.
Far be it from me to say that forming all of the above offices isn’t warranted - most of them probably are. Having said that, I do tend to agree with the point of the author of the Intercept piece: this is being handled “disjointedly” and almost certainly with a high degree of overlap and waste. Additionally - there really isn’t a lot of IO/interference expertise out there, so staffing is a problem, and automated solutions are lacking to say the least. The ODNI office, meant to coordinate all of the above efforts, may help, but personally - I wouldn’t hold my breath considering past attempts.
CTRL-V Sites:
Pastes are a great site for a number of reasons - they can be used to post breached data, extremist content and even play a role in cyberattacks. Unfortunately, most ways that involve searching paste sites involve using expensive 3rd party software.
Up until recently, analysts could’ve used pastebin.ga which unfortunately has stopped working recently - it may be too popular for its own good. I had a few free minutes recently so I decided to create a Google CSE to search paste sites - available here. Feel free to try it out and let me know what you think!
That’s it for this week’s post - I’ll be taking next week off from the blog, so finally MWW will live up to its bi-weekly tag. As always, with any questions - feel free to email me at ari@glowstickintel.com or message me on LinkedIn.