Memetic Warfare Weekly: Cry “Hamas” and Let Slip the APKs of (mal)War(e)
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - available at Telemetryapp.io - and Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I provide consulting, training and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
I know I said last week that there wouldn’t be a blog post this week, but I couldn’t hold myself back.
This week will focus on cyber activity in context of the recent Israel-Hamas war.
Cry “Al-Qassam” and Let Slip the APKs of War
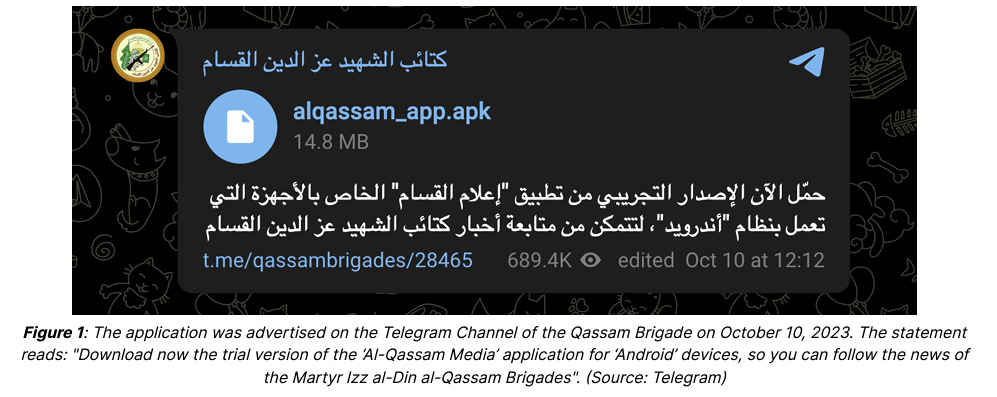
Recorded Future has put out a new report on a Hamas news application, titled إعلام القسام (Al-Qassam Media), being promoted by Hamas’ flagship media site, alqassam(.)ps, as well as its official Telegram channel:
Prior to RF’s report, I had come across the application being promoted by a number of other Hamas-related channels in rapid fashion, which may be indicative of an attempt to promote the application in a coordinated fashion. See translated (one of the many upsides of using Telemetry!) telemetryapp.io results below:
The application, unsurprisingly, connects to alqassam(.)ps - hosted via a Russian service. Despite being a key site for Hamas, they seem to have utilized poor operational security (surprise) and not used a proxy registration service. The domain is registered under the “Maktab” (office in Arabic) registrar, with two real email addresses (someone alert Google and MSN that Hamas is using their email services).
Exposed, personal email addresses are a huge OpSec risk - they can be pivoted upon in a number of ways: checking data breaches for additional PII, including passwords, past IP addresses and more for pivoting, using email resolution tools such as OSINT Industries or Epieos, converting them to usernames for username enumeration, are vulnerable to social engineering/phishing and more.
Just looking at the results quickly in Dehashed shows the vulnerability:
Doing a reverse WHOIS query shows that just one of the above has in fact registered a number of affiliated domains:
But let’s leave that aside for now, as this isn’t all about basic email investigation.
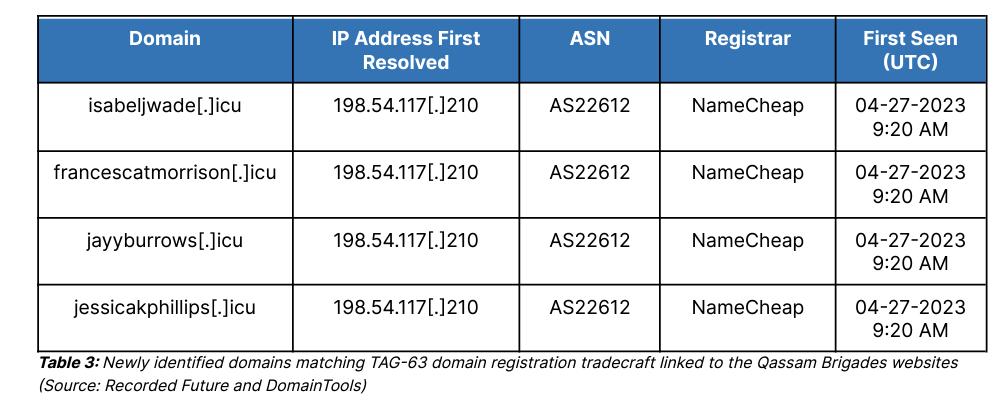
Recorded Future’s look at the Al-Qassam domain included a look at sites that both redirected to the Al-Qassam domain, including sharing the same UA Code: UA53251638.
These domains all appear to be malign, serving as potential phishing or C2 domains and do, in fact, use Cloudflare as a proxy.
However, as I always say, OpSec is hard and people make mistakes, such as the massive oversight of burning their domains by accidentally reusing the same UA code. Recorded Future also points out the similarity in naming convention, utilization of the same proxy and ASN, registration timestamp and more to tie them together and attribute these domains to Hamas.
One of the domains identified appears to share potential ties to Iran, see below:
I will just add that “modir” is the farsi loanword for “mudir” from Arabic, meaning manager, but it could be potentially misspelled. I’m less familiar with the word hamrah, but may find some time for that later.
Back to the domains - I’m unable to dedicate the time required to carry out an even deeper investigation of these due to the ongoing war, but I will make one additional point below.
I’ve said it before, I’ll say it again and I am sure that I will say it in the future: CTI vendors, please utilize source-code searching tools! It’s one of the easiest and most affordable ways, and often one of the only ways, to identify possible shared infrastructure, or in this case - victims.
PublicWWW query of just Al-Qassam’s domain shows a number of sites worth looking at - including an Iranian domain, and some unusual domains: a broadcasting group, and two domains for a Kansas City radio station:
Looking up the UA code shows that the code appears in source code on these domains:
Odd, no? Let’s archive the page and check it out:
So it appears that the site has been hacked by “ShadowTeam” via the AnonymousFox vulnerability. The reference to alqassam(.)ps and the UA code may be the result of the defaced sites linking directly to the Al-Qassam domain to host content or for other purposes. I currently am not at home and don’t have access to my workspace, so I won’t be able to securely access the site directly and investigate further.
I’ll conclude this section with RF’ss findings, with which I agree:
韜光養晦
Twitter user Cyberknow20 has reported on a new Chinese hacktivist organization, "黑暗中的灯火" - meaning "light in the dark".
This hacktivist organization has - for the first time to Cyberknow20's and my own knowledge - targeted Israel in the context of ongoing geopolitical affairs, as shown by the below screenshot, leaking #data on 38,000 Israeli citizens.
There have been some past historical events in which Chinese hacktivists have gotten involved, but not in the middle east or Israel - anyone who knows otherwise, please correct me.
Some interesting points - also discussed by Cyberknow20:
- #Telegram is increasingly important for China-oriented research of all kinds, including but not limited to #infosec, as Chinese-language Telegram groups and channels become more and more popular.
- The leak is fairly modest in size and may not indicate comparatively high skills or operational tempo.
- The channel has shared content from the Iran-aligned CyberAv3ngers group. This could be meaningless or perhaps be indicative of an attempt to situate themselves in the broader hacktivist community and to capitalize on the moment.
That’s it for this week. As always, feel free to reach out and let me know what you think at ari@glowstickintel.com or on LinkedIn!