Memetic Warfare Weekly: CIBerpunk 2023
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io - and Glowstick Intelligence Enablement.
Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
This week we’ll take a long, hard look at Meta’s Q3 Integrity Report, available here.
The report kicks off with a #throwbackthursday reference to Meta’s first, and landmark, online CIB (coordinated inauthentic behavior) report on Russian IO published about six years ago.
This is an important reminder to anyone in this space: online IO investigation is a new field and still very much coming into its own. The barriers to entry are still low, much reporting is still low-quality and low-depth, focusing on spammy social media activity on Twitter - there’s still incredible potential out there to be fulfilled in every aspect.
After that, we get a brief explanation as to the purpose of this specific report, which I can only hope doesn’t reflect the future of Meta’s reporting in regards to its emphasis on high-level trend reporting, and lesser detail on threats.
There’s already plenty of high-level reporting provided by various vendors; platforms have the unique capability of providing internal, proprietary data and context that only they can provide.
Having that be more limited than it is currently isn’t a good sign for the industry.
The report moves on to discuss the 3 operations it will cover: 2 of which “originated” in China and one in Russia.
Meta presents the networks in a nutshell:
There’s a bit more on each one of these (about 1-2 pages each) in sparse detail.
No information on specific content, screenshots, in-depth discussion of TTPs or so on, which overall shouldn’t be surprising considering the stated purpose of this report.
Meta also has decided to tone down their language on attribution, referring to the networks as “originating in” China and Russia and not say, tied to a Chinese or Russian business or government entity. This is especially disappointing in light of alleged ties to an RT employee in the Russia network.
This may be warranted due to available evidence, but we as the reader have no real way to determine if so because of the paucity of information provided.
I hope that this trend does not continue going forward, and that Meta chooses to share more information openly with the public and research community.
Meta also discusses the threat landscape in a broad sense for quite a few pages, which is useful and interesting for many, but lacks, in my opinion, “punch”, and most importantly - context.
Let me explain what I mean. Platforms, as I stated above, have unlimited access to data in their own platform, but limited access to data from other platforms, even with data-sharing agreements in place.
Additionally, platforms are naturally focused on policing their own environment, and often lack the tooling and knowledge on how to investigate well across other ecosystems.
For broader context and cross-platform investigation, we have independent firms that specialize in this that provide us with in-depth reports (check out last week’s post for an example).
As such, they are best situated to provide us with deep, specific information and findings based on activity on their own platform, which is always limited and siloed.
This is fine, but it means that any general findings or broad conclusions are going to be limited greatly by the data available across all platforms, with a specific bias given to the reporting platform’s ecosystem.
Meta has one of the largest, best and most well-known teams investigating IO, but at the end of the day they’re focused on what they know best: Meta platforms.
The community would probably be better served if in-depth reporting were provided by each platform, for independent researchers to then synthesize.
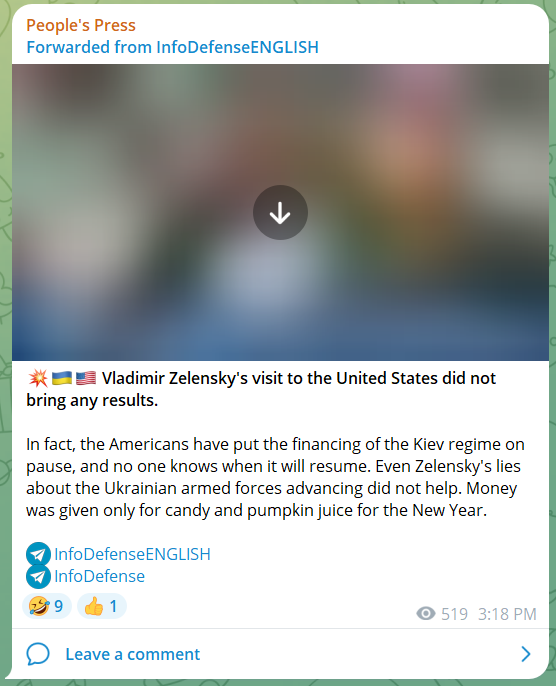
Leaving the above consternation aside, this is a great chance to check out the mentioned Telegram channels in the Russian network:
Unsurprisingly, the channel promotes other known Russian IO channels, such as the InfoDefense network, constantly.
We can also use Telegram’s “similar channel” feature to find relevant other Russian IO channels:
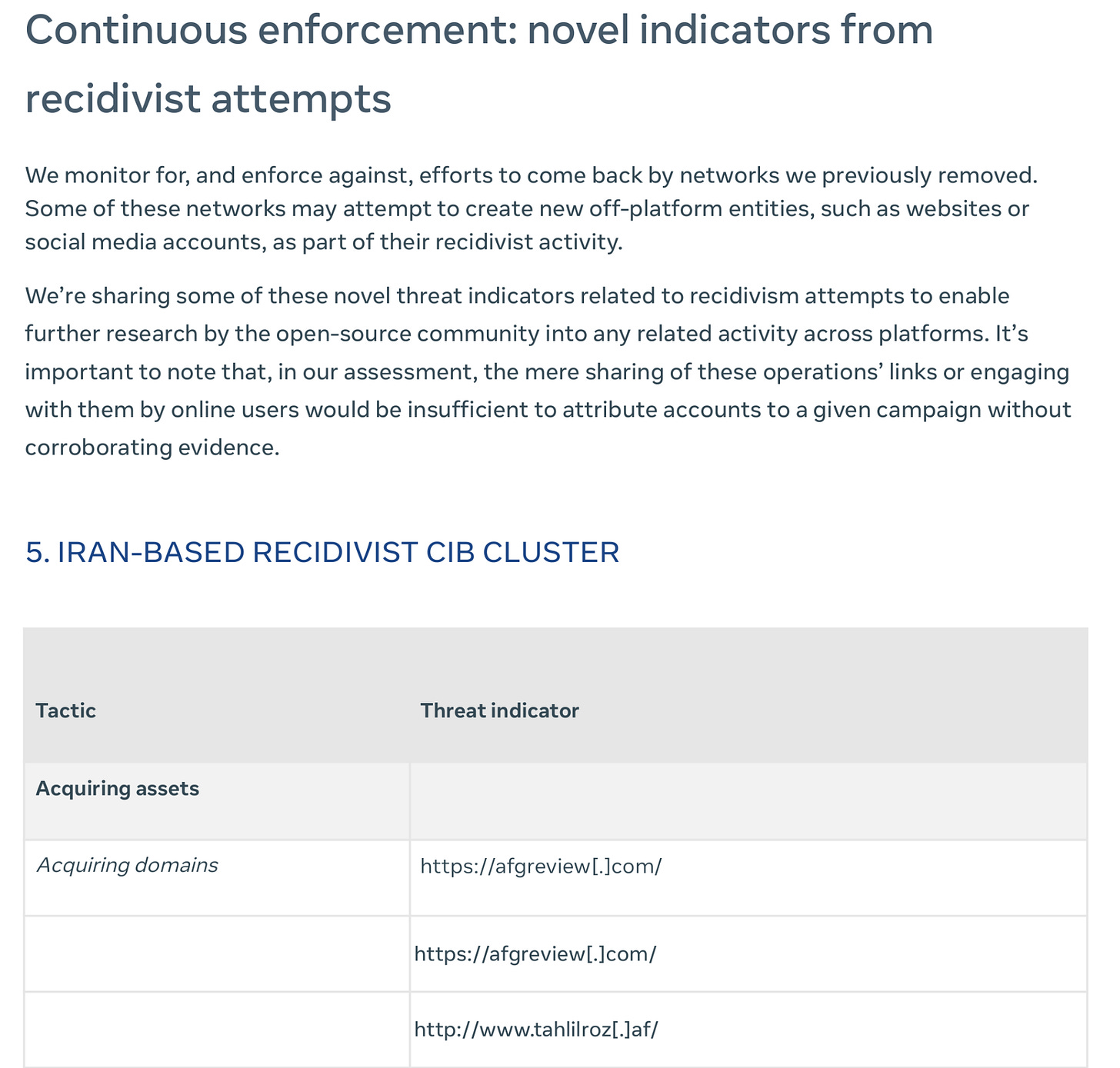
Not all is portends poorly, however. The new section on recidivism is great and needed to track massive, ongoing networks effectively:
That’s it for this week!