Memetic Warfare Weekly: Axis-2-Axis Encryption
Welcome to Memetic Warfare Weekly.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io - and Glowstick Intelligence Enablement. Memetic Warfare Weekly is where I share my opinions on the influence/CTI industry, as well as share the occasional contrarian opinion or practical investigation tip.
I provide consulting, training and research services, so if relevant - feel free to reach out via LinkedIn or ari@glowstickintel.com.
This week we’ll review some interesting phenomena that I came across while monitoring online activity in the context of the ongoing Israel-Gaza war.
Axis of Encryption
Messaging applications have been the leading method of communication in the “rest” of the world for a while now. We in the West, however, are only now waking up to them in a context broader than cyber threat intelligence due to the centrality of applications such as WhatsApp, Telegram, Viber, Line and more in conflict, geopolitics, financial markets and other newsworthy affairs.
Messaging applications pose a unique challenge to investigators and analysts in any field. Messaging applications:
Serve as echo-chambers, with built-in and highly effective forwarding mechanisms that make content go viral even faster than traditional social media.
Are primarily closed, with most activity happening in private conversations and closed groups.
Are often E2E (but not always by default - i.e. Telegram) encrypted, which is a challenge not only for law enforcement but also for platforms themselves, which are often practically unable to investigate suspicious entities due to privacy, regulation and technical limitations.
Often include minimal publicly-available user information, limiting potential avenues of investigation when required.
All of the above make messaging platforms an ideal platform for IO activity, as well as any other malign or otherwise covert actions.
These unique attributes make messaging applications a fantastic platform for malign activity to be seeded or otherwise created or promoted - making them critical for analysts, investigators and others who wish to gain advanced warning of threats or risk vectors, protect their organizations, employees/colleagues and assets and exploit potential opportunities created.
Much ado has been said about nation-state activity on messaging applications, but less so in the context of sub-state actors such as Hamas, Hezbollah and others in the “Axis of Resistance” and beyond.
Hamas and pro-Hamas actors in Gaza and beyond have, unsurprisingly, begun to utilize these applications in their IO, propaganda and other messaging activity. See a list of Telegram channels that I’ve collated here.
Pro-Hamas and directly affiliated IO activity is also available on WhatsApp and other platforms. Let’s take a look at a few examples below - note that I’ve used Google Translate on most entities for the convenience of readers:
Some Hamas-related “Fedayi” networks for domestic and regional messaging in Arabic on both Telegram and WhatsApp.
The more interesting phenomena, of course, is external messaging and IO. Hamas groups and channels have actively promoted files and guides to enable their audiences to easily share content on Twitter, alongside creating new accounts and other relevant infrastructure.
These guides are overall pretty well-done, with some basic production values - see the screenshots below.
IO and psychological warfare activity doesn’t end at having the wider public create new accounts and promote hashtags or content. Some Hamas-affiliated Mujahideen groups have actively doxxed, harassed and mass-reported Israelis:
Some groups have also begun promoting media and text content, along with relevant hashtags, to be shared across-platforms.
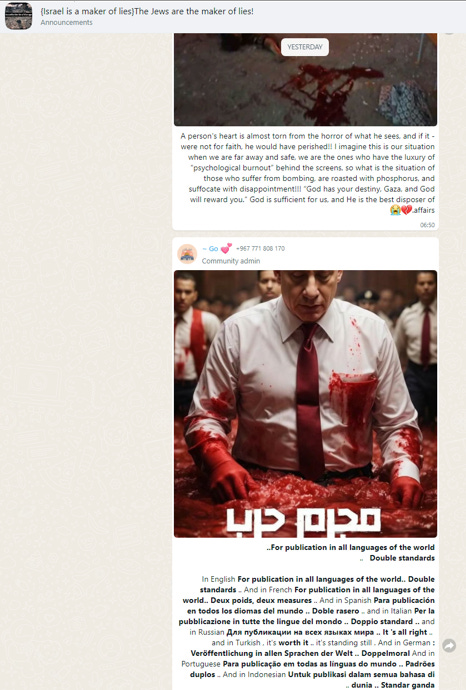
The below group is a prominent one, which also shares AI-generated imagery with accompanying text in a number of languages, ranging from English to French to Bahasa and Russian.
This content, of course, spreads verbatim to Telegram and other platforms:
The utility of artificial or low-level IO to Hamas is increasingly clear as Hamas-related entities get the banhammer across platforms, with some platforms even being forced by app stores (see below) to limit access to official Hamas entities.
That’s it for this week. There’s much, much more to look at - Hezbollah activity, Iran-affiliated militias in Iraq and Yemen and beyond. Have any questions or comments? Reach out at ari@glowstickintel.com or via LinkedIn.