Many Such Frameworks
Welcome to Memetic Warfare.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
There’s quite a bit to cover this week, so let’s cover some highlights. Then, we’ll take a look at some open questions regarding exposing Western cyber operations, and finally at Viginum’s latest report.
First order of business: an inside look at Doppelganger courtesy of Paul Bouchaud (a great resource to follow on DG in general as well).
Paul came across an OpSec slip in a DG-uploaded photo, funnily enough uploaded as an ad on Facebook, which in this case showing their VK Teams UI in the background:
Paul enhanced the image, giving us some insight into the various channels the DG operators have open:
We get some further great insight here:
Microsoft’s Threat Intelligence team has done some interesting work on jailbreaking generative AI models, available here.
The exploit, called “Skeleton Key”, enables users to force LLMs to carry out instructions contrary to their safeguards:
Also great to see that Microsoft is testing out what it works on:
This sort of exploit will be critical going forward for threat actors to be able to maliciously utilize Western LLMs, so expect to see more invested in GenAI security soon.
If you’re interested in trying to jailbreak an LLM yourself, check out Lakera’s “Gandalf” game.
Let’s move on. Sentinel One and Recorded Future published a great report on the use of ransomware as a final stage in their espionage/financial crime activities.
When will we see ransomware used as a front for hack and leaks or general IO? It’d be a great pretext for sure, especially for seeding forged documents.
Recorded Future is back at it again with a new report on CopyCop. I’m always a fan of seeing long-term research done on persistent operations, so always fun to see it here.
Some key findings:
I’ll share my highlights below. The first is the use of file paths for domain identification:
This is hard without URLScan, and I assume that with URLScan Pro it’s easier, especially if done programmatically via the API. URLScan is still somehow the most underrated tool in domain analysis, and more people need to get on it.
Look at the below example:
10/10 stuff. Note also that URLScan supports wildcards in this search query, so you can really go nuts.
Great to see how the broader ecosystem of other persistent operations (Infodefense and DG) pitch in:
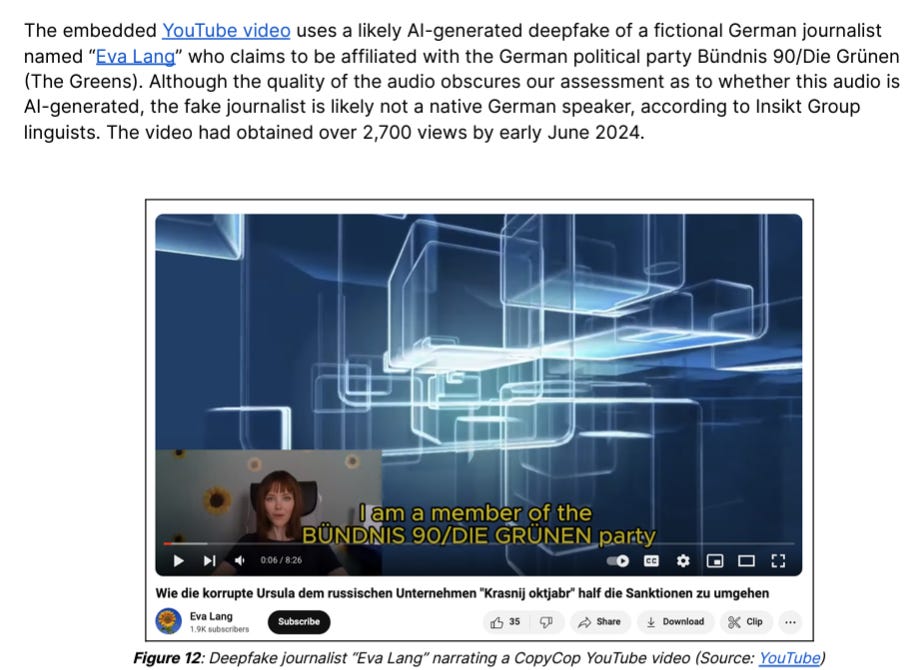
It wouldn’t be an operation in 2024 without an AI-generated anchor:
Also - tip of le fedora for doing audio file analysis. I’ve done some image/video analysis but have never really dived into audio before, so this is fantastic to see, and shows how accessible it could be:
My final kudos is the threat indicators list. Look at how clear, understandable, and most importantly, copy and paste-able it is! This is how to do it folks. The only thing I’d change here is to make it a structured table already alongside this list to make it more easily copyable into a structured table.
If you ever need to defang the URLs, just use CyberChef. To conclude - amazing stuff as usual from RF, and great to see that they’re continuing to raise the roof and their operational tempo of reporting.
They simply can’t stop/won’t stop, and that includes a new report on Russian and Iranian activity targeting the French elections, see the link here. I’ll cover this report more in-depth later on.
Let’s keep it moving. After giving Google TAG a bit of a hard time for not doing more in-depth publishing, they went and wrote a slightly more in-depth view at Spamouflauge/Dragonbridge, available here.
There are insights to be gleaned here.
Firstly, Dragonbridge is the “most prolific” IO actor that Google tracks. Guess they can out-volume Doppelganger!
The second is the news-tracking. Google claims here that they’ve seen cases of Dragonbridge reacting to breaking news within a few weeks and adapting their narratives (nothing new in of itself), but that they also create content in advance to seed massively.
This is something that we could tell anecdotally but it’s nice to have it be supported by Google’s telemetry.
There are some more things that are worth reading, so check it out yourself!
We’ll conclude this lightning round with an interesting thought piece written by Michael Coppola, available here.
In short, Coppola refers to a case in which Google TAG exposed and took down a long-running counterterrorism operation by a Western government.
This piece comes out against an overly zealous blue-team approach, stating that Google TAG went too far in exposing this operation and related exploits, infrastructure and methodology.
This piece has sparked a lot of discussion on security/vuln research Twitter and frankly raises some really interesting questions:
What responsibility does Google have towards any government? Does it change based on what they’re doing?
How does Google’s responsibility towards having secure products affect this activity?
Should Western/Western-allied cyber operations be exposed? If so, how?
What role do vendors (in this case, a vendor is suspected to be the provider of the exploit chain) play in this and how should they be treated?
I don’t usually delve into this sort of discussion, but I couldn’t help but think of this in the context of influence operations following the Reuters investigation into US influence operations.
In this specific case, Facebook and Twitter came across an ongoing American influence operation (like the above operation, done apparently with poor operational security). Both firms contacted the US government to lodge their complaints, and the US government requested that they keep the operation going.
The right answer to what should’ve been done by the firms there, like the vuln case, is debatable.
Having said that, this ethical and legal conundrum will rear its head again. Western platforms are and will continue to be the main vector for the foreseeable future, especially as the US presumably increases its operational tempo for IO online.
How platforms choose to cooperate with government operations remains to be seen, but it may well become more prominent than the hard cyber case.
It’s one thing to rent a C2 server from an American provider (or internationally) anonymously, but another thing to set up thousands to tens of thousands of inauthentic accounts to amplify a given claim, datapoint or otherwise in terms of maintaining a mitigated OpSec attack surface.
Additionally, many more people are capable of looking at IO, which is by definition public-facing, making it much easier to identify and potentially expose. Compare that to the highly-skilled in-house teams at Mandiant, TAG, Recorded Future, CrowdStrike, Meta and a few others that have the skills AND internal telemetry needed to actually investigate and attribute in-the-wild covert operations. Overall, maybe a few hundred people tops?
At the end of the day, Western states will presumably increasing utilize below-threshold hybrid warfare, influence operations among them. These operations will require commercial infrastructure, be it domain hosting and servers, online accounts and otherwise - essentially, the utilization/exploitation of Western platforms and firms. How platforms and civil society responds to this remains to be seen, and the complexity is certainly present.
These are all open questions, and I’m not quite sure how I feel about them yet. As time goes on, we’ll have better data upon which to base potential answers.
Many Such Frameworks
Viginum has also jumped on the Matryoshka train after having been scooped by Antibot4Navalny, CheckFirst and Reset.Tech, publishing a report available here:
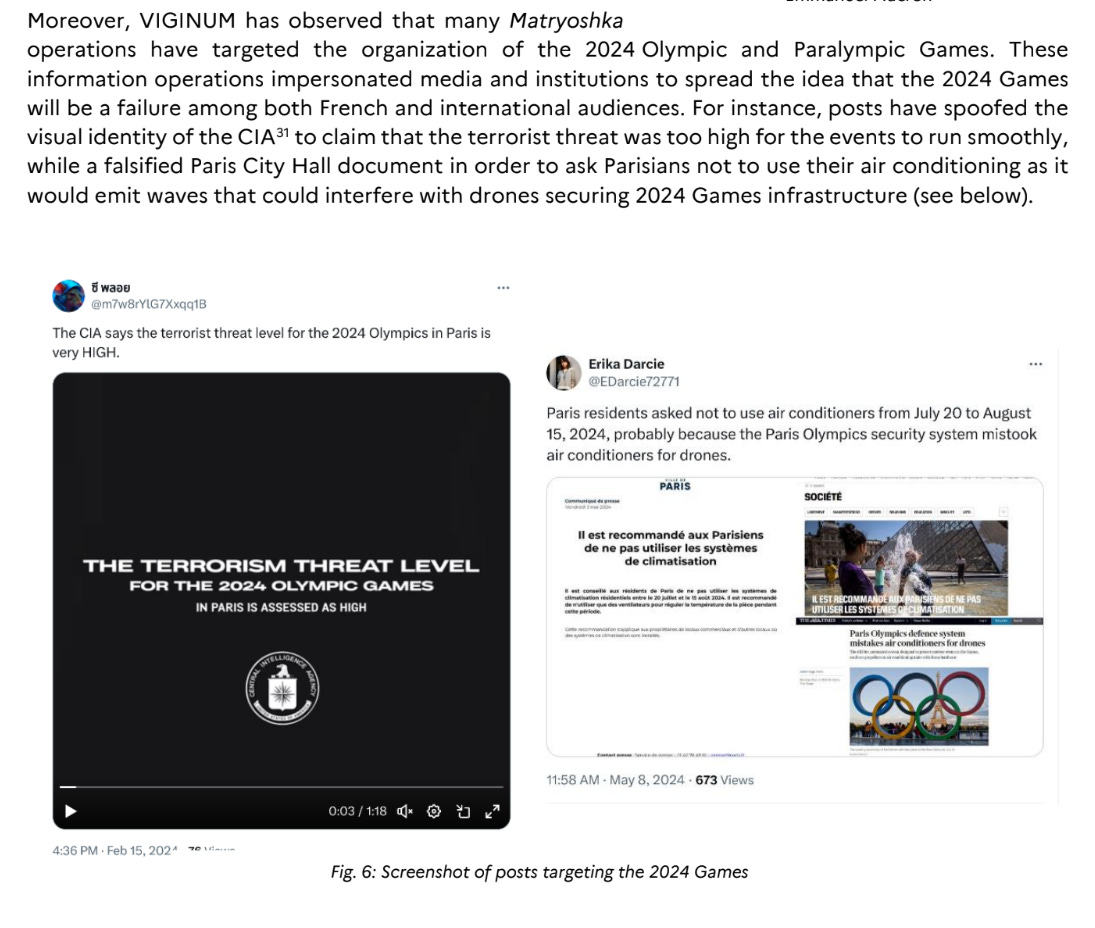
There’s operational overlap between Matryoshka and the Microsoft reporting, in this case referring to the same falsified CFIA threat assessment:
Promoting a bank run is also an interesting TTP.
The Telegram to rest of the Internet pipeline is also alive and well here.
Viginum also came across interesting evidence of potential coordinated promotion on Telegram:
There are multiple online digital marketing services available for Telegram, run by Russians and other people in eastern Europe and Central Asia. The below post shows evidence that vigilant found of the same individual Promoting network groups and channels and offering paid partnerships.
The report also provides DISARM TTPs:
Let's be real for a moment, shall we? How many of these really are that unique or impactful?
Maybe 15 to 20 percent of those above would be considered notable at the operational level. The majority of these would be, for the most part, comparatively universal. Were we to tag hundreds or thousands of reports on influence operations, there would be a very high degree of overlap.
Look at post comment or comment or reply on content. The same goes with reframe context or generate information pollution, identifying media system vulnerabilities, creating inauthentic and anonymous accounts, impersonating organizations, plagiarizing content. These are all essentially the foundational elements that we see in a very large number of influence operations.
All one needs to do is take a look at a below sample of red TTPs to see what I’m talking about:
While I'm not theoretically opposed to frameworks in the influence operation space, I feel that we're still not quite there yet.
This isn’t unique to just DISARM, there’s a lot of criticism of other frameworks out there with which I agree. Funnily enough, I believe that there’s arguably much more potential for DISARM compared to say other cyber frameworks as it develops in the long run due to the sheer potential diversity of the IO space, but that’s not the case currently.
DISARM TTPS are still underdeveloped and need to be both much more specific and simultaneously broader reaching than what we currently have.
Some directions could include integrating less traditional types of influence operation activity such as cyber enabled influence operations and perhaps physical IO as well on that spectrum. Further splitting the red and blue tags by activity or network type as well could be useful to then avoid the redundancy of each having the same functional baseline.
It’ll take time, but eventually I’m sure that we’ll get there.
That’s it for this week! As always, if you’ve made it this far, I salute you and thank you for putting up with my writing style. Check out Telemetryapp.io and see you next week!