Lil Milad IX
I’m Ari, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
I hope to have some published research come out soon so keep an eye out for that as well for some hands-on guides here, it’s been a while since the last guide and it’s time for a new one.
Let’s begin with what else but Iranian activity as it’s apparently that time of the year. CISA has put out yet another Iran-related advisory, available here.
The advisory focuses on Iranian government-affiliated actors (Pioneer Kitten) deploying ransomware alongside routine espionage and data collection. There’s a lot of interesting technical information, inlcuding of course IoCs (and BTC wallets used for the actual ransomware), so if you’re interested in trying out tools like VirusTotal and others, this would be a good place to start.
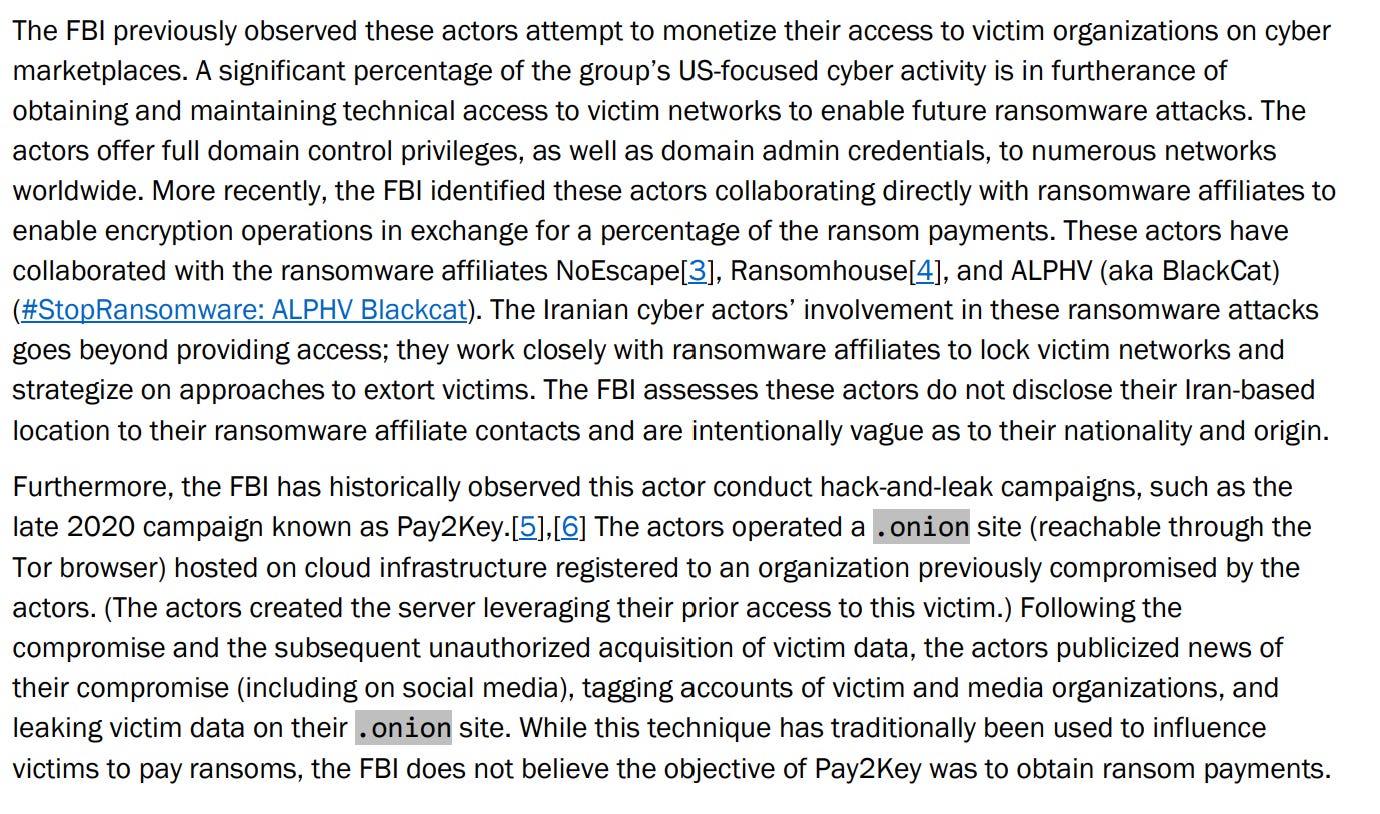
I normally don’t discuss ransomware actors on this blog, but it’s a relevant case. Pioneer Kitten not only cares out ransomware attacks, but also has collaborated with past ransomware affiliate groups for financial gain. Additionally, the FBI claims here that Pioneer Kitten doesn’t share any information on their nationality or origin as well.
The most relevant part though is that this group has historically been involved in cyber-enabled IO. The FBI brings up the previous Pay2Key campaign as a key example, in which Pioneer Kitten set up an onion site hosted on compromised cloud infrastructure owned by a previous victim. Pioneer Kitten operators then would then amplify their successful intrusion on that site as well as on social media, including by tagging accounts of victims and leaking their data for the psychological effect, and not to actually receive payment.
To summarize - this group would carry out ransomware attacks on victims for the influence and psychological impact of carrying them out, not for financial gain (alone, at least). This is a reminder that essentially any cyber operation can have a psychological/IO component to it. Ransomware as IO (essentially it’s own variety of hack and leak) is a fascinating topic that I hope to see more research on going forward.
The final note and a common TTP used by Iranian actors is the use of a front company:
Googling the company registration number or the full name leads to some results for it, including the CEO and other owners. At least one of them is involved with an additional company, so there’s some pivoting to be done.
In other Iran-related news, Mandiant published a fascinating look at an Iranian counter intelligence operation, available here. We’ll look at this shortly (as there’s a lot of information to pivot on) but this case is especially noteworthy as Adam Rawnsley first exposed this back in 2022.
The network itself is fairly straightforward, but it’s a comparatively rare to see Iranian CI operations exposed in-depth. Let’s look at the summary first:
Quite an operation, huh? Ongoing since 2017 and into at LEAST March of 2024, this kind of operation fascinates me precisely because it requires very little technical acumen (and may be tied to APT 42, but that’s not confirmed).
All we’re talking about is setting up domains ostensibly representing HR firms targeting those who’d be interested in apparently betraying Iran with a background in the country’s government agencies (I imagine there are many of them), offering them some form form of financial reward and forms to fill in, and then amplifying them with social media accounts.
Quite literally any layman could pull this off, and I have to wonder how effective it was. Let’s assume that it was at least somewhat effective in weeding out the less intelligent of Iran’s ex-military/government operators as they kept it running for so long, although even the length of the operation is not necessarily an indication of success.
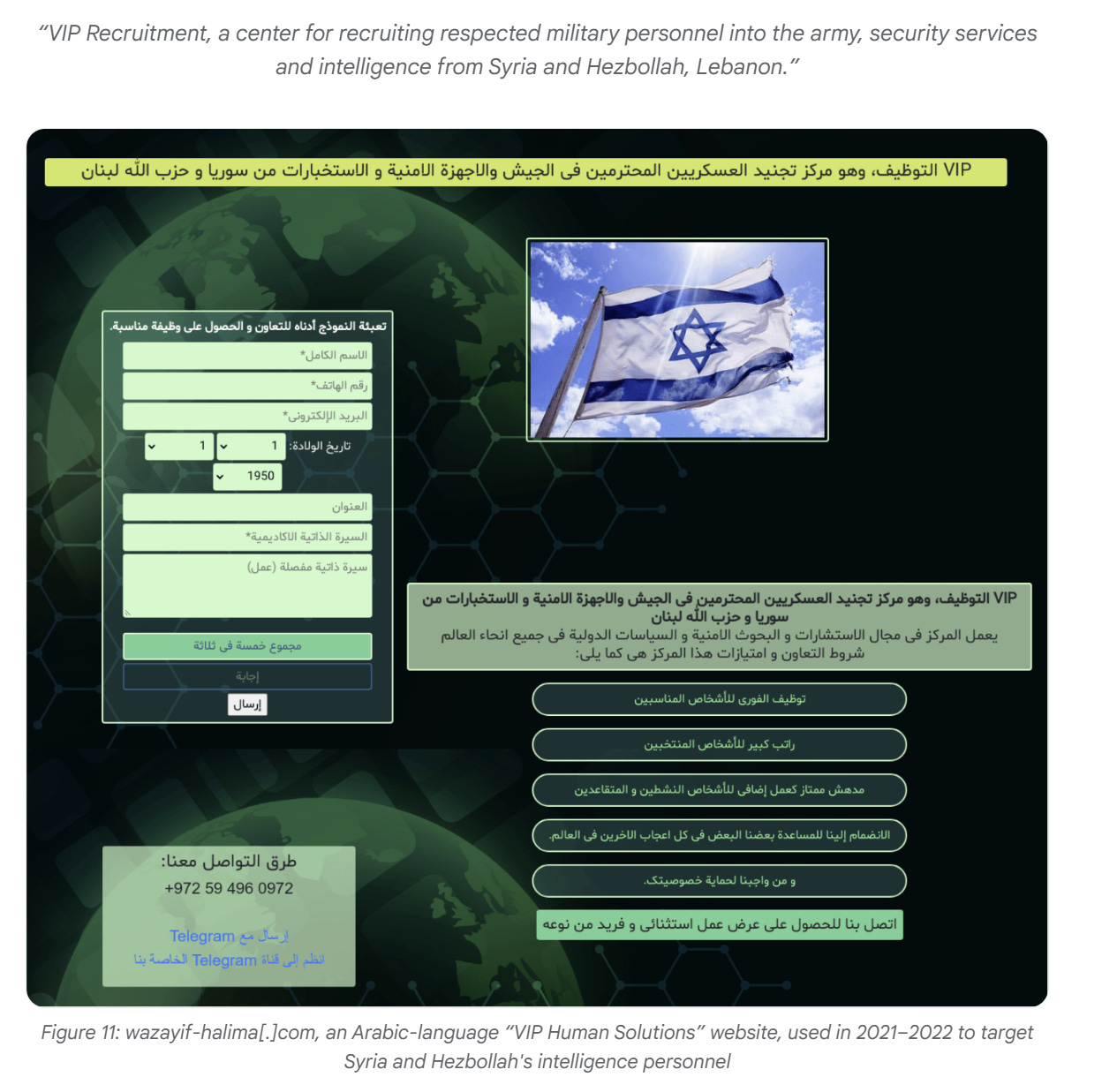
The content manages to be both cringe and highly suspicious to anyone - just look at the below seemingly generative-AI content on the right and the Israeli flag and tag line on the image:
The domains all shared similar layouts:
Truly normal things here on these domains. It’s hard to imagine anyone actually falling for these:
Mandiant also uses WordPress JSON analysis (as we’ve done here in the past on many occasions) to find that at least one of the domains has an exposed Gravatar account:
We get two hits for Miladix on PublicWWW, including at least one that’s Iranian - would be curious to see these if I had a paid membership.
The network targeted Syrian and Hezbollah personnel as well:
The final part is the conclusion, which is pretty straightforward:
Overall an interesting operation and not the kind we usually see, so good on Mandiant for getting this out.
We’ll conclude with a resource for readers. SentinelOne recently published a fairly in-depth guide for VirusTotal for analysis, you can check it out here. I only scratch the surface of what VT can offer for infrastructure mapping, there’s a lot more that it’s capable of doing.
Next week there may well not be a post, but who knows! I said that last week, and here we are. Thanks for reading.